Security Week 14: ShadowHammer and supply chain
The main news of last week is a targeted attack on Asus device owners through the hacked Asus Live Update utility. Researchers at Kaspersky Lab discovered an attack in January of this year: an infected utility for updating drivers on laptops and computers with Asus components was signed with a legitimate certificate and distributed from the manufacturer’s servers. Modification of the utility provided hackers with full access to all affected systems, but they used this opportunity only when the MAC address of one of the network adapters of the system coincided with the list of systems of interest.

In this case, an additional malware was downloaded from a server created in March 2018 and stopped working before an attack was detected - for the time being with unknown targets. The attack is remarkable both for its complexity and secrecy. Most likely, it was preceded by more large-scale events in order to gather information and identify “promising” victims. Although it is too early to talk about the exact attribution of the attack, there are data linking it with earlier incidents with the 2017 CCleaner utility. The full attack study will be published next week and presented at the Security Analyst Summit conference at Kaspersky Lab. In this post - a brief description of the incident and some conclusions.
Original sources: news , excerpts from the Kaspersky Lab study, a detailed article on Motherboard , an official statement from Asus. You can check the MAC address of your Asus device using this online service.
From June to November 2018, an infected version of Asus Live Update was heard from Asus servers. The program is pre-installed on laptops from this manufacturer, but is also available for owners of computers based on Asus motherboards. It allows you to download the latest BIOS, firmware and device drivers and install them automatically. The malicious application was uploaded to the vendor’s servers, signed with the company's legitimate certificates, and was distributed as a software update. On Reddit there is a discussion of the strange behavior of the utility, although it has not yet been established whether the incident mentioned in the thread is related to this attack.
')
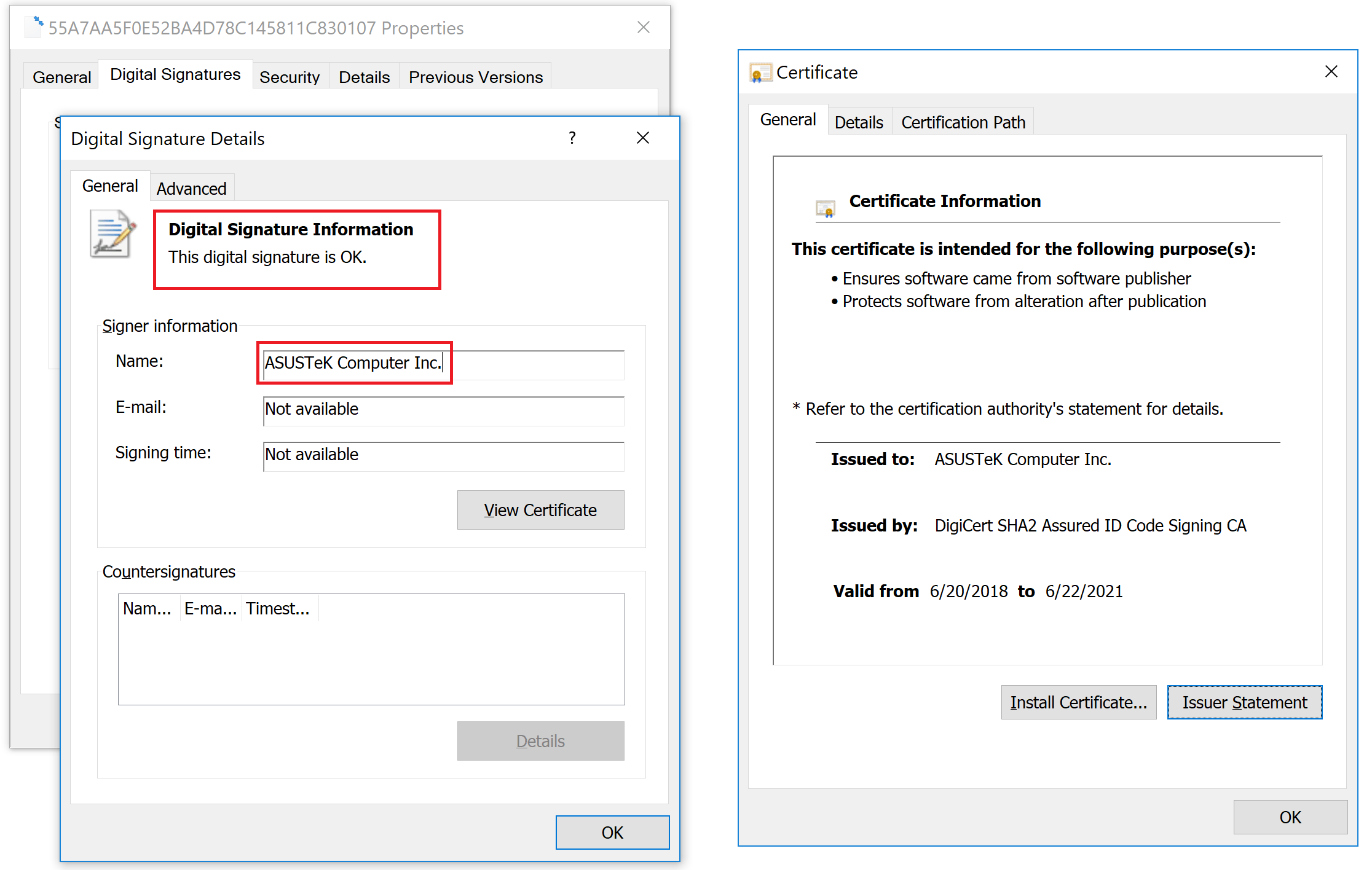
Although the utility was “updated”, in fact it was an outdated version of the program with additional malicious functionality (analysis of malicious code by an independent researcher is here ). It can be concluded that Asus’s infrastructure was partially compromised: the attackers had access to the update server and digital certificates, but not to the source code of the application and the build servers. Detection of a malicious utility has become possible thanks to tests of a new technology aimed at detecting attacks in the supply chain (in English - supply chain) - when attackers either attack software or hardware one way or another before being delivered to the end consumer-victim, or compromise service tools and device management during operation - those that are trusted.
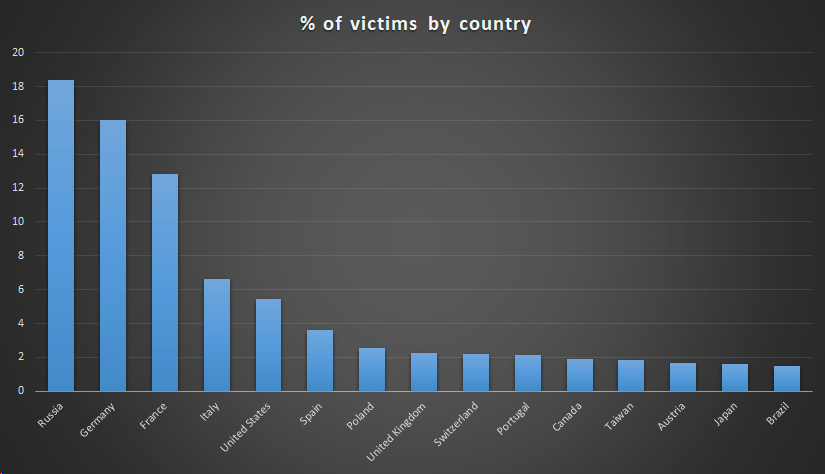
If you count all those who flew the utility "with a peg", then tens of thousands of users have suffered, most of them from Russia, Germany and France. But this is only according to Kaspersky Lab. Later, Symantec provided its own data - they counted 13 thousand infected systems, with a greater share of users from the United States. This is clearly not all affected, most likely the malware was on hundreds of thousands of systems. But on most attacked computers, the utility did nothing, it only checked the MAC addresses with its own database. In case of coincidence with the command server (for it the asushotfix [.] Com domain was registered), additional software was loaded. In some cases, the trigger was a combination of the MAC addresses of the wired and wireless network modules.
Of the two hundred samples of the infected utility, we managed to extract about 600 MAC addresses of the systems to which the ShadowHammer attack was really aimed. What was done to them later was not yet clear: the command server had stopped working until the researchers had detected the attack. The known facts end there, the conclusions begin.
The complexity of the attack is now hardly anyone can be surprised - there are examples of targeted attacks with much more serious investments in R & D. An important feature of the ShadowHammer operation is that it is a successful attack on the supply chain. Infected software is distributed from the manufacturer’s servers, signed by the manufacturer’s certificate — there is no reason for the client to trust such a scenario. In this case, we are dealing with a pre-installed utility, but previously other programs, which the user usually installs on his own, were successfully attacked. Kaspersky Lab experts have reason to believe that the latest ShadowHammer attack is related to two incidents two years ago.
In the first case, the CCleaner utility already mentioned above was modified; it was also distributed from the manufacturer’s servers. In the second case, a manufacturer of device management software in the corporate network NetSarang was attacked. It is possible that there were other attacks in which attackers collected the MAC addresses of the victims' computers of interest. In this story there is a hint at one of the real reasons for the massive infection of IoT devices - IP cameras, routers, and the like. It is not always possible to get to the data of interest through an infected device, but enough information can be collected for use in the next, more targeted operation.
Of course, the question of trust in hardware and software manufacturers arises: if a software update or driver arrives from a vendor, is it safe or not? Perhaps, it’s still necessary to be trusted, otherwise the point of vulnerability can simply move to another place. Prompt response to such incidents by the manufacturer is also welcome. In the case of Asus, according to Kaspersky Lab, almost two months passed from the first notification (end of January) to the official confirmation of the problem (March 26). I wonder what technologies will be used for the rapid detection of such attacks? There is a lot of work to do both for security vendors and vendors. The cases of using a legitimate certificate to sign malware are sporadic, but the mere presence of a digital signature can no longer serve as the sole criterion for evaluating software.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.

In this case, an additional malware was downloaded from a server created in March 2018 and stopped working before an attack was detected - for the time being with unknown targets. The attack is remarkable both for its complexity and secrecy. Most likely, it was preceded by more large-scale events in order to gather information and identify “promising” victims. Although it is too early to talk about the exact attribution of the attack, there are data linking it with earlier incidents with the 2017 CCleaner utility. The full attack study will be published next week and presented at the Security Analyst Summit conference at Kaspersky Lab. In this post - a brief description of the incident and some conclusions.
Original sources: news , excerpts from the Kaspersky Lab study, a detailed article on Motherboard , an official statement from Asus. You can check the MAC address of your Asus device using this online service.
What happened
From June to November 2018, an infected version of Asus Live Update was heard from Asus servers. The program is pre-installed on laptops from this manufacturer, but is also available for owners of computers based on Asus motherboards. It allows you to download the latest BIOS, firmware and device drivers and install them automatically. The malicious application was uploaded to the vendor’s servers, signed with the company's legitimate certificates, and was distributed as a software update. On Reddit there is a discussion of the strange behavior of the utility, although it has not yet been established whether the incident mentioned in the thread is related to this attack.
')

Although the utility was “updated”, in fact it was an outdated version of the program with additional malicious functionality (analysis of malicious code by an independent researcher is here ). It can be concluded that Asus’s infrastructure was partially compromised: the attackers had access to the update server and digital certificates, but not to the source code of the application and the build servers. Detection of a malicious utility has become possible thanks to tests of a new technology aimed at detecting attacks in the supply chain (in English - supply chain) - when attackers either attack software or hardware one way or another before being delivered to the end consumer-victim, or compromise service tools and device management during operation - those that are trusted.
Who suffered

If you count all those who flew the utility "with a peg", then tens of thousands of users have suffered, most of them from Russia, Germany and France. But this is only according to Kaspersky Lab. Later, Symantec provided its own data - they counted 13 thousand infected systems, with a greater share of users from the United States. This is clearly not all affected, most likely the malware was on hundreds of thousands of systems. But on most attacked computers, the utility did nothing, it only checked the MAC addresses with its own database. In case of coincidence with the command server (for it the asushotfix [.] Com domain was registered), additional software was loaded. In some cases, the trigger was a combination of the MAC addresses of the wired and wireless network modules.
Of the two hundred samples of the infected utility, we managed to extract about 600 MAC addresses of the systems to which the ShadowHammer attack was really aimed. What was done to them later was not yet clear: the command server had stopped working until the researchers had detected the attack. The known facts end there, the conclusions begin.
The complexity of the attack is now hardly anyone can be surprised - there are examples of targeted attacks with much more serious investments in R & D. An important feature of the ShadowHammer operation is that it is a successful attack on the supply chain. Infected software is distributed from the manufacturer’s servers, signed by the manufacturer’s certificate — there is no reason for the client to trust such a scenario. In this case, we are dealing with a pre-installed utility, but previously other programs, which the user usually installs on his own, were successfully attacked. Kaspersky Lab experts have reason to believe that the latest ShadowHammer attack is related to two incidents two years ago.
In the first case, the CCleaner utility already mentioned above was modified; it was also distributed from the manufacturer’s servers. In the second case, a manufacturer of device management software in the corporate network NetSarang was attacked. It is possible that there were other attacks in which attackers collected the MAC addresses of the victims' computers of interest. In this story there is a hint at one of the real reasons for the massive infection of IoT devices - IP cameras, routers, and the like. It is not always possible to get to the data of interest through an infected device, but enough information can be collected for use in the next, more targeted operation.
Of course, the question of trust in hardware and software manufacturers arises: if a software update or driver arrives from a vendor, is it safe or not? Perhaps, it’s still necessary to be trusted, otherwise the point of vulnerability can simply move to another place. Prompt response to such incidents by the manufacturer is also welcome. In the case of Asus, according to Kaspersky Lab, almost two months passed from the first notification (end of January) to the official confirmation of the problem (March 26). I wonder what technologies will be used for the rapid detection of such attacks? There is a lot of work to do both for security vendors and vendors. The cases of using a legitimate certificate to sign malware are sporadic, but the mere presence of a digital signature can no longer serve as the sole criterion for evaluating software.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/446354/
All Articles