How to disable standard passwords and make everyone hate you
Man, as is known, is a lazy creature. And even more so when it comes to choosing a sustainable password.
I think each administrator has ever encountered the problem of using light and standard passwords. This phenomenon is often found among the top echelons of the company's management. Yes, it is among those who have access to secret or commercial information and it would be highly undesirable to eliminate the consequences of a password leak / hack and further incidents.
In my practice, there was a case when, in an Active Directory domain with password policy enabled, accountants on their own got the idea that a password like “Pas $ w0rd1234” perfectly rolls up to the requirements of the policy. The consequence was the widespread use of this password anywhere and everywhere. Sometimes he differed only in a set of numbers.
I really wanted to be able to not only include the password policy and determine the set of characters, but also filter by dictionary. To exclude the possibility of using such passwords.
')
Microsoft kindly informs us by reference that anyone who knows how to hold the compiler in their hands, the IDE, and who can correctly pronounce C ++, is able to compile and use the library itself according to its own understanding. Your humble servant is not capable of this, so I had to look for a ready-made solution.
After along hour of searching, two solutions to the problem were revealed. I, of course, speak about OpenSource solution. After all, paid options - from and to.
Option number 1. OpenPasswordFilter
There are no kommites like 2 years ago. The native installer works one time, you have to tinker with your hands. Creates its own separate service. When updating the password file, the DLL does not automatically pick up the changed content, you need to stop the service, wait for a timeout, edit the file, start the service.
Not ice!
Option number 2. PassFiltEx
The project is active, alive and you don’t even have to kick a cold body.
Setting the filter consists of copying two files and creating several registry entries. The password file is not in lock, that is, it is editable and, according to the idea of the author of the project, it is simply read once a minute. Also, with the help of additional registry entries, you can configure additional settings for both the filter itself and even the nuances of the password policy.
So.
Given: Active Directory domain test.local
Windows 8.1 test workstation (irrelevant for the task condition)
PassFiltEx password filter
You can also add the following registry entries, which gives you more flexibility in using this filter:
Section: HKLM \ SOFTWARE \ PassFiltEx - created automatically.
A number of rules when creating a template file:
For debugging in the archive there are batch files that allow you to create a log and then parse it using, for example, Microsoft Message Analyzer.
This password filter uses Event Tracing for Windows.
The ETW provider for this password filter is 07d83223-7594-4852-babc-784803fdf6c5 . For example, you can configure the event tracing after the next reload:
Tracing will start after the next system reboot. To stop:
All these commands are listed in the StartTracingAtBoot.cmd and StopTracingAtBoot.cmd scripts .
For one-time testing of the filter operation, you can use StartTracing.cmd and StopTracing.cmd .
In order to conveniently read the exhaust debug of this filter in Microsoft Message Analyzer, it is recommended to use the following settings:
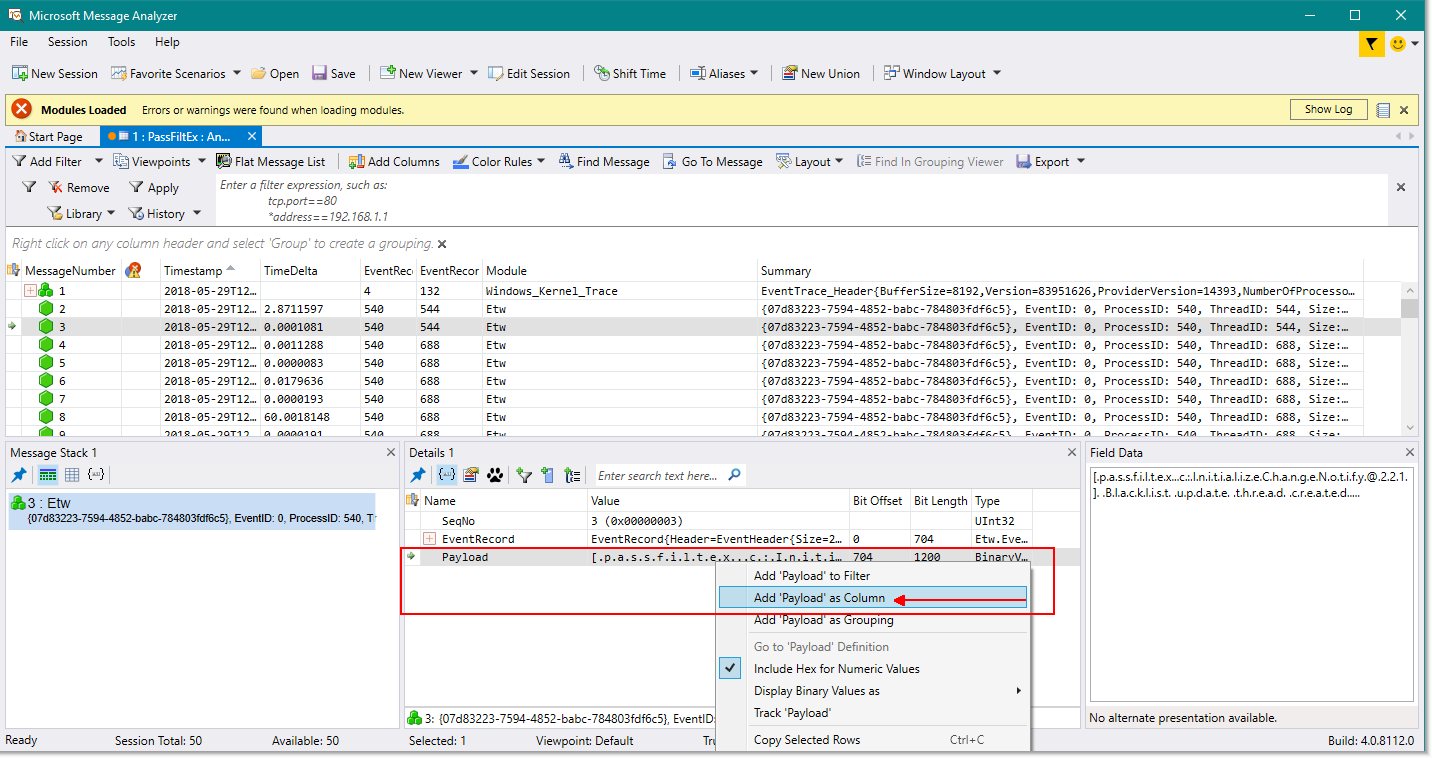

When you stop the log and parse in Microsoft Message Analyzer , everything looks like this:

Here you can see that there was an attempt to set a password for the user - the magic word SET in debug tells us about it. And the password was rejected due to its presence in the template file and more than 30% compliance in the input text.
When a successful attempt to change the password, we see the following:

There is some inconvenience for the end user. When trying to change a password that falls into the list of a template file, the message on the screen is not different inintelligence and wit from the standard message when the password policy does not pass.
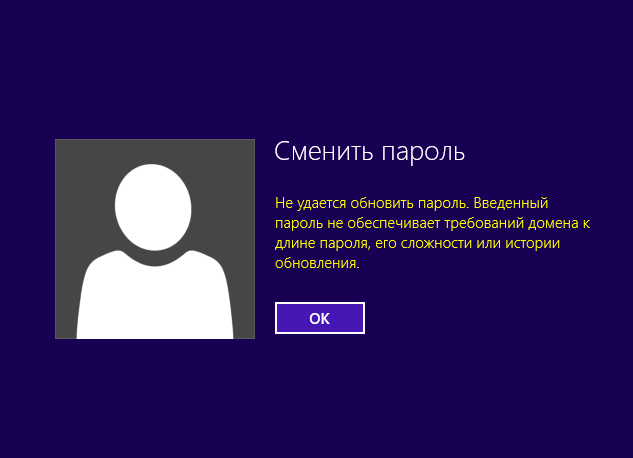
Therefore, be prepared for calls and shouts: "I entered the password as it should, but it does not work."
This library allows you to prohibit the use of simple or standard passwords in the Active Directory domain. Say "No!" To passwords of the form: "P @ ssw0rd", "Qwerty123", "ADm1n098".
Yes, of course, users will love you even more for such concern about their security and the need to invent furious passwords. And, perhaps, the number of calls and requests to help with the password you add. But you have to pay for security.
Links to used resources:
An article on Microsoft regarding the custom password filter library: Password Filters
PassFiltEx: PassFiltEx
Release Link: Latest Release
Password Lists:
DanielMiessler lists: Link.
Wordlist from weakpass.com: Link.
Wordlist from berzerk0 repo: Link.
Microsoft Message Analyzer: Microsoft Message Analyzer.
I think each administrator has ever encountered the problem of using light and standard passwords. This phenomenon is often found among the top echelons of the company's management. Yes, it is among those who have access to secret or commercial information and it would be highly undesirable to eliminate the consequences of a password leak / hack and further incidents.
In my practice, there was a case when, in an Active Directory domain with password policy enabled, accountants on their own got the idea that a password like “Pas $ w0rd1234” perfectly rolls up to the requirements of the policy. The consequence was the widespread use of this password anywhere and everywhere. Sometimes he differed only in a set of numbers.
I really wanted to be able to not only include the password policy and determine the set of characters, but also filter by dictionary. To exclude the possibility of using such passwords.
')
Microsoft kindly informs us by reference that anyone who knows how to hold the compiler in their hands, the IDE, and who can correctly pronounce C ++, is able to compile and use the library itself according to its own understanding. Your humble servant is not capable of this, so I had to look for a ready-made solution.
After a
Option number 1. OpenPasswordFilter
There are no kommites like 2 years ago. The native installer works one time, you have to tinker with your hands. Creates its own separate service. When updating the password file, the DLL does not automatically pick up the changed content, you need to stop the service, wait for a timeout, edit the file, start the service.
Not ice!
Option number 2. PassFiltEx
The project is active, alive and you don’t even have to kick a cold body.
Setting the filter consists of copying two files and creating several registry entries. The password file is not in lock, that is, it is editable and, according to the idea of the author of the project, it is simply read once a minute. Also, with the help of additional registry entries, you can configure additional settings for both the filter itself and even the nuances of the password policy.
So.
Given: Active Directory domain test.local
Windows 8.1 test workstation (irrelevant for the task condition)
PassFiltEx password filter
- Download the latest PassFiltEx release link.
- Copy PassFiltEx.dll to C: \ Windows \ System32 (or % SystemRoot% \ System32 ).
Copy PassFiltExBlacklist.txt to C: \ Windows \ System32 (or % SystemRoot% \ System32 ). If necessary, we supplement it with our own templates.
- Edit the registry branch: HKLM \ SYSTEM \ CurrentControlSet \ Control \ Lsa => Notification Packages
Add PassFiltEx to the end of the list. (You do not need to specify the extension.) The full list of packages used for checking will look like this " rassfm scecli PassFiltEx ".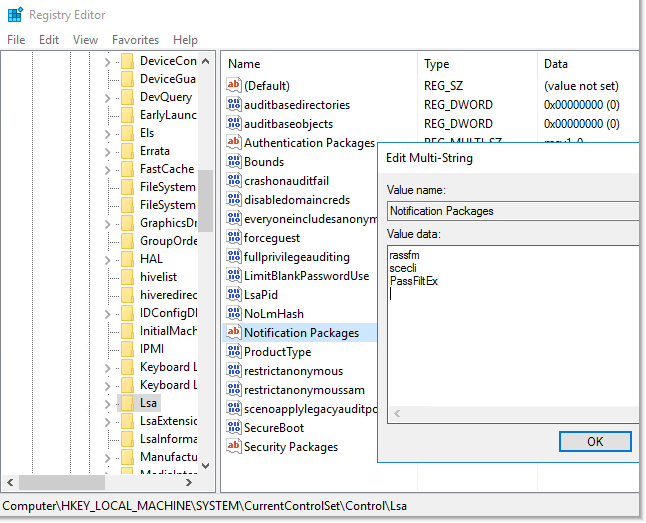
- Reboot the domain controller.
- Repeat the above procedure for all domain controllers.
You can also add the following registry entries, which gives you more flexibility in using this filter:
Section: HKLM \ SOFTWARE \ PassFiltEx - created automatically.
- HKLM \ SOFTWARE \ PassFiltEx \ BlacklistFileName , REG_SZ, Default: PassFiltExBlacklist.txt
BlacklistFileName - allows you to specify a custom path to the file with password templates. If this registry entry has a blank value or does not exist, then the default path is used, namely % SystemRoot% \ System32 . You can even specify the network path, but you need to remember that the template file must have clear permissions to read, write, delete, modify. - HKLM \ SOFTWARE \ PassFiltEx \ TokenPercentageOfPassword , REG_DWORD, Default: 60
TokenPercentageOfPassword - allows you to specify the percentage occurrence of the mask in the new password. The default value is 60%. For example, if a percentage entry of 60 is specified and the starwars string is in the template file, then the password is Starwars1! will be rejected, while the password starwars1! DarthVader88 will be accepted, because the percentage entry string in the password is less than 60% - HKLM \ SOFTWARE \ PassFiltEx \ RequireCharClasses , REG_DWORD, Default: 0
RequireCharClasses - allows you to expand the requirements for passwords compared to the standard complexity requirements of ActiveDirectory passwords. The built-in complexity requirements require 3 of 5 possible different kinds of characters: Upper case, Lower case, Number, Special, and Unicode. Using this registry entry, you can set your own password complexity requirements. The value that can be specified is a set of bits, each of which is a corresponding power of two.
That is - 1 = lower case, 2 = upper case, 4 = number, 8 = special character, and 16 = Unicode character.
Thus, with a value of 7, the requirements will be “Upper case AND lower case AND number,” and with value 31, “Upper case AND lower case AND number AND special AND symbol Unicode character”.
You can even combine - 19 = “Uppercase AND lowercase AND Unicode character”. 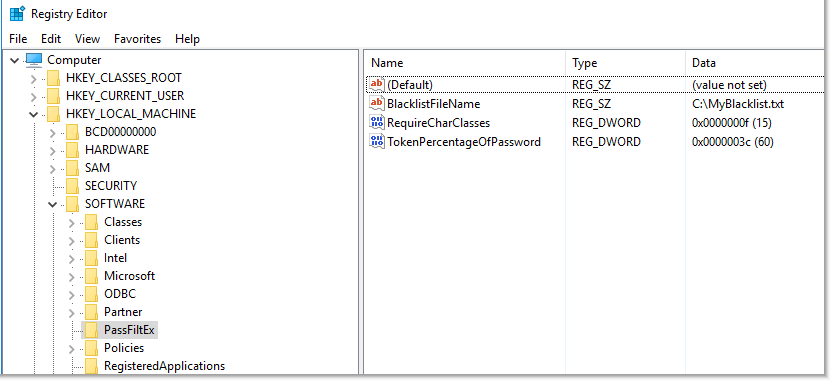
A number of rules when creating a template file:
- Patterns are case-insensitive. Therefore, the entry in the starwars file and StarWarS will be defined as the same value.
- The blacklist file is reread every 60 seconds, so you can safely edit it, in a minute the new data will already be used by the filter.
- There is currently no Unicode support for pattern checking. That is, you can use Unicode characters in passwords, but the filter will not work. This is not critical, because I have not seen users who use Unicode passwords.
- It is advisable to avoid blank lines in the template file. In the debug, then you see an error when loading data from the file. The filter works, but why unnecessary exceptions?
For debugging in the archive there are batch files that allow you to create a log and then parse it using, for example, Microsoft Message Analyzer.
This password filter uses Event Tracing for Windows.
The ETW provider for this password filter is 07d83223-7594-4852-babc-784803fdf6c5 . For example, you can configure the event tracing after the next reload:
logman create trace autosession\PassFiltEx -o %SystemRoot%\Debug\PassFiltEx.etl -p "{07d83223-7594-4852-babc-784803fdf6c5}" 0xFFFFFFFF -ets Tracing will start after the next system reboot. To stop:
logman stop PassFiltEx -ets && logman delete autosession\PassFiltEx -etsAll these commands are listed in the StartTracingAtBoot.cmd and StopTracingAtBoot.cmd scripts .
For one-time testing of the filter operation, you can use StartTracing.cmd and StopTracing.cmd .
In order to conveniently read the exhaust debug of this filter in Microsoft Message Analyzer, it is recommended to use the following settings:


When you stop the log and parse in Microsoft Message Analyzer , everything looks like this:

Here you can see that there was an attempt to set a password for the user - the magic word SET in debug tells us about it. And the password was rejected due to its presence in the template file and more than 30% compliance in the input text.
When a successful attempt to change the password, we see the following:

There is some inconvenience for the end user. When trying to change a password that falls into the list of a template file, the message on the screen is not different in

Therefore, be prepared for calls and shouts: "I entered the password as it should, but it does not work."
Total
This library allows you to prohibit the use of simple or standard passwords in the Active Directory domain. Say "No!" To passwords of the form: "P @ ssw0rd", "Qwerty123", "ADm1n098".
Yes, of course, users will love you even more for such concern about their security and the need to invent furious passwords. And, perhaps, the number of calls and requests to help with the password you add. But you have to pay for security.
Links to used resources:
An article on Microsoft regarding the custom password filter library: Password Filters
PassFiltEx: PassFiltEx
Release Link: Latest Release
Password Lists:
DanielMiessler lists: Link.
Wordlist from weakpass.com: Link.
Wordlist from berzerk0 repo: Link.
Microsoft Message Analyzer: Microsoft Message Analyzer.
Source: https://habr.com/ru/post/446336/
All Articles