92.7% make backups, data loss increased by 30%. What's wrong?
In 2006, at a major Russian conference, the doctor of technical sciences made a report on the growing information space. In beautiful schemes and examples, the scientist told that in 5-10 years in developed countries, information will be given to each person in an amount that he cannot fully perceive. He talked about the wireless networks available at every step of the Internet and wearable electronics, and especially that the information will need protection, but it will be impossible to provide this protection 100%. Well, this is what we are now formulating, and then the audience accepted him as a crazy professor who lives in the world of science fiction.
13 years have passed, and a new study by Acronis has shown that science fiction has long become a reality. International backup day is the best time to share your results and give some important tips on how to stay protected in dozens of networks, gigabytes of incoming information and a lot of gadgets at hand. And yes, companies are also concerned.
For the coolest IT people - competition inside.
')

Just made a backup? Exactly?
If you are a system administrator who is tired of corporate life, has a security guard exhausted by users, and you know exactly where your legs have problems with data security, you can immediately go to the end of the article - there are 4 cool tasks that, having solved, can win valuable prizes from Acronis and make your information more secure nowhere (in fact, there is always where).
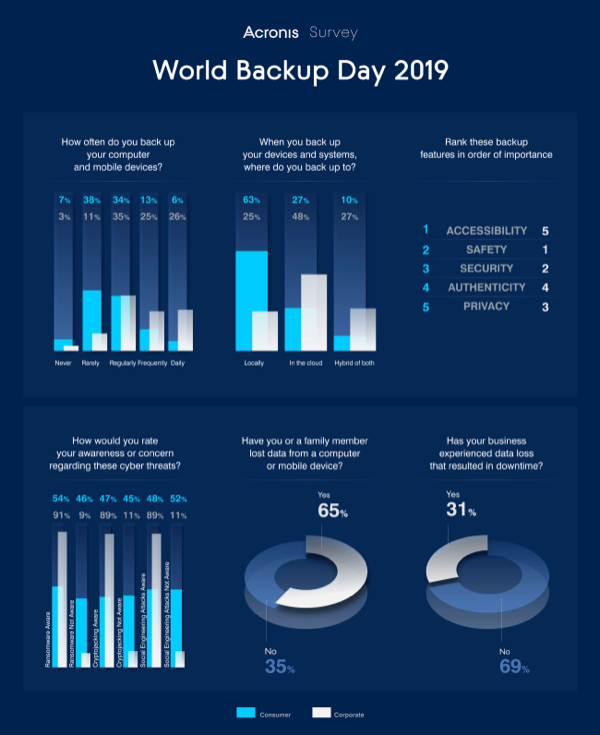
The first unexpected, but quite explainable result of the survey: 65% of respondents reported that last year either they themselves or one of their relatives faced data loss as a result of accidental deletion of files or hardware or software failures. This figure increased by 29.4% compared with the previous year.
At the same time, for the first time in a five-year history of research conducted by Acronis, almost all surveyed consumers (92.7%) back up data from their own computers. The growth of this indicator was 24%.
Here’s how the contradiction is explained by Acronis President and Chief Operating Officer Stanislav Protasov:
Users from the USA, Great Britain, Germany, Spain, France, Japan, Singapore, Bulgaria and Switzerland took part in the survey.
This year the survey was first conducted among business users. Due to the increasing number of cases of loss of work by CEOs, IT managers and other executives as a result of data hacking, online attacks and computer technology errors, Acronis decided to include relevant data protection issues in the study. The inclusion of business users revealed several differences in how and why users and companies protect their digital assets.
There are a lot of devices
The number of devices used by consumers continues to grow, with 68.9% of households claiming to use three or more devices such as computers, smartphones and tablets. This figure increased by 7.6% compared with last year.
Users are aware of the value of information.
Given the growth of natural and man-made disasters, resonant acts of extortion, as well as cases of data leakage, with increased data volumes, the growth in the data backup rate indicates that consumers are still trying to protect their data. This year, only 7% of users said they had never backed up data, while last year almost a third of respondents provided such an answer (31.4%).
Users began to value their own data more, as evidenced by the fact that 69.9% are willing to spend more than $ 50 to restore lost files, photos, videos and other information. Last year, only 15% were willing to pay that amount.
To protect your own data, 62.7% of users keep it at hand, keeping backups on a local external hard disk (48.1%) or in a separate hard disk partition (14.6%). Only 37.4% use cloud technologies or a hybrid cloud and local backup format.
Clouds are not for everyone
Another obvious problem is the lack of active adoption of cloud technologies. More and more consumers are saying that the basic value of backing up data is to provide access to it - many say they want to have “fast and easy access to backup data from any location.” But at the same time, only a third of them use cloud technologies for backup, allowing them to extract data regardless of their location.
Master data
The main data of value to consumers are contacts, passwords and other personal information (45.8%), as well as multimedia files, including photos, videos, music and games (38.1%).
Users still need educational program
Less than half of consumers have information about data threats such as ransomware (46%), malware for mining cryptocurrency (53%), and social engineering attacks (52%) used to distribute malware. Knowledge of these dangers is spreading slowly, as evidenced by the fact that the number of users who are aware of the extortion programs has increased by only 4% compared to last year.
Acronis infographics about data protection
Losses from one hour of downtime are estimated at about 300 thousand US dollars, so users from the business environment, of course, are well aware of the value of their company's data. Since CEOs and senior executives are increasingly responsible for data protection, they are taking an increasingly active interest in security issues, especially given the increasing number of high-profile cases involving data attacks.
This explains why business users who participated in the survey were already prepared to protect their own data, applications, and systems, and stated that the most important aspects for them are security in terms of preventing unintended incidents and security in terms of preventing malicious users. actions regarding their data.
Business users were included in the annual survey 2019 for the first time, with responses from companies of all sizes, including 32.7% of small businesses with up to 100 employees, 41% of medium-sized companies with 101 to 999 employees and 26, 3% of large enterprises with more than 1,000 employees.
For most companies, data protection becomes one of the most important priorities: for example, companies make data backup monthly (25.1%), weekly (24.8%) or daily (25.9%). As a result of such measures, 68.7% said they had no downtime due to data loss last year.
Such companies are well aware of the latest risks to their data, with the result that they expressed concern or extreme concern regarding ransomware programs (60.6%), cryptodikeking (60.1%) and social engineering (61%).
Today, companies of all sizes rely on cloud backups, with 48.3% using only cloud backups, and 26.8% using a combination of cloud and local backups.
Considering their security and data protection requirements, it is possible to understand their interest in cloud technologies. From a security point of view, in the context of unintentional data loss (“reliable backups so that data can always be recovered”), external cloud backups ensure data availability even in the event of the destruction of office space as a result of fire, flood or other natural disasters. From a security point of view, in the context of malicious acts (“data protected from online threats and cybercriminals”), the cloud is an obstacle to the deployment of malware.
To protect personal files or ensure company continuity, Acronis recommends performing four simple steps to help protect data. However, these tips will be clearly useful for private users.
 Today, March 31 - International Day of backup. This is at least a reason to make a backup on the eve of April Fools ’draws, and as a maximum - to win prizes from Acronis. Especially Sunday evening to this has.
Today, March 31 - International Day of backup. This is at least a reason to make a backup on the eve of April Fools ’draws, and as a maximum - to win prizes from Acronis. Especially Sunday evening to this has.
This time, the annual Acronis True Image 2019 Cyber Protection license with 1 TB in the cloud storage is at stake - 5 winners will receive it.
The first three, we additionally give:
To participate you need to solve difficult (as always), but interesting puzzles. The first is simple, the second and third are average, and the fourth is for real hardcore people.
Proud of love Pasha loves to encrypt texts, what did he encrypt this time? Ciphertext:
What kind of plugins for popular CMS (WordPress, Drupal and others) do you recommend for backup and migration. Than they are worse / better than normal backups and Application Aware backups.
How to work with the registry data of your application starting with Windows 8. It is desirable to give an example of correct updating of two values in the registry key. Why backup is not able to solve the problem of logical consistency of the registry?
Vasya wants to load the dll into the child process (created with the SUSPENDED flag), the dll name was copied using VirtualAllocEx / WriteProcessMemory
CreateRemoteThread (hChildProcess, nullptr, 0, LoadLibraryA, remoteDllName, 0, nullptr);
But because of the ASLR in the child process, the kernelbase.dll is located at a different address.
On 64-bit Windows at this moment EnumModulesEx does not work. Suggest 3 methods for finding the address of a kernelbase.dll in a child frozen process.
It is desirable to implement one of the methods.
Well, the rest of Habr's readers have one important and necessary wish: I made backups - sleep well!

13 years have passed, and a new study by Acronis has shown that science fiction has long become a reality. International backup day is the best time to share your results and give some important tips on how to stay protected in dozens of networks, gigabytes of incoming information and a lot of gadgets at hand. And yes, companies are also concerned.
For the coolest IT people - competition inside.
')

Just made a backup? Exactly?
Disclaimer
If you are a system administrator who is tired of corporate life, has a security guard exhausted by users, and you know exactly where your legs have problems with data security, you can immediately go to the end of the article - there are 4 cool tasks that, having solved, can win valuable prizes from Acronis and make your information more secure nowhere (in fact, there is always where).
Contradiction of contradictions
The first unexpected, but quite explainable result of the survey: 65% of respondents reported that last year either they themselves or one of their relatives faced data loss as a result of accidental deletion of files or hardware or software failures. This figure increased by 29.4% compared with the previous year.
At the same time, for the first time in a five-year history of research conducted by Acronis, almost all surveyed consumers (92.7%) back up data from their own computers. The growth of this indicator was 24%.
Here’s how the contradiction is explained by Acronis President and Chief Operating Officer Stanislav Protasov:
“At first glance, these two findings seem contradictory, because how can a loss of a larger amount of data occur if almost all users began to make backup copies of them? However, there are reasons why these survey figures look that way. People use more devices and work with data from more points than ever before, which creates more reasons for their loss. For example, users can back up data stored on a laptop, but if they accidentally forget a smartphone in a taxi, the backup of which they do not create, the data will still be lost. ”That is, the reason was the same our reality, where we do not just get tired of information, but do not have time to control all sources of danger, and therefore, quickly and adequately respond to them. It turns out that against the background of automation and informatization, the human factor begins to play a particularly important and even critical role.
Briefly about the survey
Users from the USA, Great Britain, Germany, Spain, France, Japan, Singapore, Bulgaria and Switzerland took part in the survey.
This year the survey was first conducted among business users. Due to the increasing number of cases of loss of work by CEOs, IT managers and other executives as a result of data hacking, online attacks and computer technology errors, Acronis decided to include relevant data protection issues in the study. The inclusion of business users revealed several differences in how and why users and companies protect their digital assets.
Survey results: let's learn from the mistakes of others
Only 7% of users make no effort to protect their own data.
There are a lot of devices
The number of devices used by consumers continues to grow, with 68.9% of households claiming to use three or more devices such as computers, smartphones and tablets. This figure increased by 7.6% compared with last year.
Users are aware of the value of information.
Given the growth of natural and man-made disasters, resonant acts of extortion, as well as cases of data leakage, with increased data volumes, the growth in the data backup rate indicates that consumers are still trying to protect their data. This year, only 7% of users said they had never backed up data, while last year almost a third of respondents provided such an answer (31.4%).
Users began to value their own data more, as evidenced by the fact that 69.9% are willing to spend more than $ 50 to restore lost files, photos, videos and other information. Last year, only 15% were willing to pay that amount.
To protect your own data, 62.7% of users keep it at hand, keeping backups on a local external hard disk (48.1%) or in a separate hard disk partition (14.6%). Only 37.4% use cloud technologies or a hybrid cloud and local backup format.
Clouds are not for everyone
Another obvious problem is the lack of active adoption of cloud technologies. More and more consumers are saying that the basic value of backing up data is to provide access to it - many say they want to have “fast and easy access to backup data from any location.” But at the same time, only a third of them use cloud technologies for backup, allowing them to extract data regardless of their location.
Master data
The main data of value to consumers are contacts, passwords and other personal information (45.8%), as well as multimedia files, including photos, videos, music and games (38.1%).
Users still need educational program
Less than half of consumers have information about data threats such as ransomware (46%), malware for mining cryptocurrency (53%), and social engineering attacks (52%) used to distribute malware. Knowledge of these dangers is spreading slowly, as evidenced by the fact that the number of users who are aware of the extortion programs has increased by only 4% compared to last year.

Acronis infographics about data protection
Companies actively protect cloud data
Losses from one hour of downtime are estimated at about 300 thousand US dollars, so users from the business environment, of course, are well aware of the value of their company's data. Since CEOs and senior executives are increasingly responsible for data protection, they are taking an increasingly active interest in security issues, especially given the increasing number of high-profile cases involving data attacks.
This explains why business users who participated in the survey were already prepared to protect their own data, applications, and systems, and stated that the most important aspects for them are security in terms of preventing unintended incidents and security in terms of preventing malicious users. actions regarding their data.
Business users were included in the annual survey 2019 for the first time, with responses from companies of all sizes, including 32.7% of small businesses with up to 100 employees, 41% of medium-sized companies with 101 to 999 employees and 26, 3% of large enterprises with more than 1,000 employees.
For most companies, data protection becomes one of the most important priorities: for example, companies make data backup monthly (25.1%), weekly (24.8%) or daily (25.9%). As a result of such measures, 68.7% said they had no downtime due to data loss last year.
Such companies are well aware of the latest risks to their data, with the result that they expressed concern or extreme concern regarding ransomware programs (60.6%), cryptodikeking (60.1%) and social engineering (61%).
Today, companies of all sizes rely on cloud backups, with 48.3% using only cloud backups, and 26.8% using a combination of cloud and local backups.
Considering their security and data protection requirements, it is possible to understand their interest in cloud technologies. From a security point of view, in the context of unintentional data loss (“reliable backups so that data can always be recovered”), external cloud backups ensure data availability even in the event of the destruction of office space as a result of fire, flood or other natural disasters. From a security point of view, in the context of malicious acts (“data protected from online threats and cybercriminals”), the cloud is an obstacle to the deployment of malware.
4 useful tips for everyone
To protect personal files or ensure company continuity, Acronis recommends performing four simple steps to help protect data. However, these tips will be clearly useful for private users.
- Always back up your important data. Store backups both locally (to ensure quick access to them and the possibility of any frequent restoration), and in the cloud (to ensure the safety of all data in the event of office destruction as a result of theft, fire, flood or other natural disasters).
- Regularly update the operating system and software. The use of outdated versions of the OS or applications means that the errors remain uncorrected, and the security fixes that help block the access of cybercriminals to the corresponding system are not installed.
- Pay attention to suspicious emails, links and attachments. Most cases of infection of the system with viruses or the launch of extortion programs occur as a result of the use of social engineering methods, under the influence of which users open fraudulently infected e-mail attachments or click on links leading to malware websites.
- Install anti-virus software and run automatic system updates to protect it from the latest known threats. Windows users must confirm the activation and relevance of Windows Defender.
How can Acronis help you?
Due to the incredibly rapid evolution of modern threats to data, companies and users are seeking to find data protection solutions that provide maximum protection, including flexible local, hybrid and cloud backup and powerful antivirus software.
Only Acronis backup solutions ( Acronis Backup for companies and Acronis True Image for individual users) imply active protection against ransomware and cryptodikeking, based on artificial intelligence, able to detect and block malicious programs in real time and automatically repair any damaged ones. files. The technology is so effective that last year it managed to prevent 400 thousand such attacks.
A new version of such an integrated protection called Acronis Active Protection recently received a new feature for detecting and blocking malware for the extraction of cryptocurrency. Released in the autumn of 2018, the Acronis Active Protection update blocked tens of thousands of malware attacks for the extraction of cryptocurrency during the first months of operation.
Only Acronis backup solutions ( Acronis Backup for companies and Acronis True Image for individual users) imply active protection against ransomware and cryptodikeking, based on artificial intelligence, able to detect and block malicious programs in real time and automatically repair any damaged ones. files. The technology is so effective that last year it managed to prevent 400 thousand such attacks.
A new version of such an integrated protection called Acronis Active Protection recently received a new feature for detecting and blocking malware for the extraction of cryptocurrency. Released in the autumn of 2018, the Acronis Active Protection update blocked tens of thousands of malware attacks for the extraction of cryptocurrency during the first months of operation.
→ Acronis Competition on Habr to the international backup day - tasks for labor IT specialists
 Today, March 31 - International Day of backup. This is at least a reason to make a backup on the eve of April Fools ’draws, and as a maximum - to win prizes from Acronis. Especially Sunday evening to this has.
Today, March 31 - International Day of backup. This is at least a reason to make a backup on the eve of April Fools ’draws, and as a maximum - to win prizes from Acronis. Especially Sunday evening to this has.This time, the annual Acronis True Image 2019 Cyber Protection license with 1 TB in the cloud storage is at stake - 5 winners will receive it.
The first three, we additionally give:
- for 1 place - portable acoustics
- 2nd place - power bank
- for 3rd place - Acronis mug
To participate you need to solve difficult (as always), but interesting puzzles. The first is simple, the second and third are average, and the fourth is for real hardcore people.
→ Task 1
Proud of love Pasha loves to encrypt texts, what did he encrypt this time? Ciphertext:
tnuyyet sud qaurue → Task 2
What kind of plugins for popular CMS (WordPress, Drupal and others) do you recommend for backup and migration. Than they are worse / better than normal backups and Application Aware backups.
→ Task 3
How to work with the registry data of your application starting with Windows 8. It is desirable to give an example of correct updating of two values in the registry key. Why backup is not able to solve the problem of logical consistency of the registry?
→ Task 4
Vasya wants to load the dll into the child process (created with the SUSPENDED flag), the dll name was copied using VirtualAllocEx / WriteProcessMemory
CreateRemoteThread (hChildProcess, nullptr, 0, LoadLibraryA, remoteDllName, 0, nullptr);
But because of the ASLR in the child process, the kernelbase.dll is located at a different address.
On 64-bit Windows at this moment EnumModulesEx does not work. Suggest 3 methods for finding the address of a kernelbase.dll in a child frozen process.
It is desirable to implement one of the methods.
The decision is given 2 weeks - until April 13. On April 14, an Acronis jury will select and announce the winners.
UPD:
Dear friends, our challenge competition has ended.
The only winner who solved all the problems correctly was StasPo.
Congratulations! Portable acoustics and a one-year license of Acronis True Image 2019 with 1TB of cloud storage are sent to you :)
→ To participate in the contest and send answers, register here.
Well, the rest of Habr's readers have one important and necessary wish: I made backups - sleep well!

Source: https://habr.com/ru/post/446132/
All Articles