Leisure thoughts of cryptography and data protection
 Why about cryptography? I myself have enough superficial knowledge about her. Yes, I read the classic work of Bruce Schneier , but a long time ago; Yes, I understand the difference between symmetric and asymmetric encryption, I understand what elliptic curves are, but that’s all. Moreover, the existing cryptographic libraries, with their sweet custom, include the full name of the algorithm in the name of each function and a bunch of initializers jutting out, causing me as a programmer to have a terrible batthyrth.
Why about cryptography? I myself have enough superficial knowledge about her. Yes, I read the classic work of Bruce Schneier , but a long time ago; Yes, I understand the difference between symmetric and asymmetric encryption, I understand what elliptic curves are, but that’s all. Moreover, the existing cryptographic libraries, with their sweet custom, include the full name of the algorithm in the name of each function and a bunch of initializers jutting out, causing me as a programmer to have a terrible batthyrth. 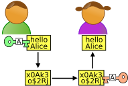
So why? Probably because when reading the current tree of publications on data protection, confidential information, etc., I have a feeling that we are digging somewhere not there, or more specifically, we are trying to solve social problems with the help of technical means (cryptography) . Let us talk about this, epoch-making discoveries, as well as concrete proposals, I do not promise, leisure thoughts they are leisure.
A little bit of history, just a bit
In 1976, the United States adopted a federal standard for symmetric encryption algorithms - DES. It was the first public and standardized cryptographic algorithm created in response to growing business demands for data protection.
The algorithm was published by mistake. It was optimized for hardware implementation and was considered too complicated and inefficient for software. However, Moore's Law quickly put everything in its place.
It would seem - the end of the story, take, encrypt, decipher, if necessary, increase the key length. Perhaps you absolutely know for sure that the Americans have bookmarked in it, then for you there is a Russian equivalent - GOST 28147-89 , which you probably trust even less. Then use both, one on top of the other. If you believe that the FBI and the FSB have joined together and exchanged their bookmarks for you, then I have good news for you - you are not paranoid, you have a banal delusions of grandeur.
How does symmetric encryption work? Both participants know the same key, it is the password, what is encrypted by it, it can also be decrypted. The scheme works fine for spies, but it is completely unsuitable for the modern Internet, since this key must be passed in advance to each of the interlocutors. For some time, while relatively few companies defended their data when communicating with a previously known partner, the problem was solved with the help of couriers and secure mail, but then the Internet became widespread and came on the scene
Asymmetric cryptography
where two keys are involved: public , which is not kept secret and is communicated to anyone who wishes; and private , who knows only its owner. What is encrypted with the public key can only be decrypted private, and vice versa. Thus, anyone can find out the recipient’s public key and send him a message, only the addressee will read it. It would seem the problem is solved?
But the Internet does not work that way , the problem of authentication and, especially, initial authentication arises in its full height, and in some sense the opposite problem of anonymity . In short, how can I be sure that the one with whom I speak is really the one with whom I was going to speak? and the public key that I use really belongs to the one with whom I was going to talk? Especially if I communicate with him for the first time? And how to instill trust in a partner, while maintaining anonymity? Already here, if you look closely, you can notice an internal contradiction.
Let's consider in general terms what schemes of interaction between the participants exist and are applied in practice:
- server - server (or business - business, in this context it’s the same): this is the simplest classical scheme for which quite symmetric cryptography is enough, participants know everything about each other, including off-network contacts. However, pay attention - there is not even any talk of anonymity here, and the number of participants is strictly limited to two. That is, it is almost an ideal scheme for an extremely limited number of communications and, in general, is obviously of little use.
- server - anonymous (or business client): here there is some asymmetry, which is successfully maintained by asymmetric cryptography. The key point here is the lack of client authentication, it does not matter to the server with whom it is communicating; if it is necessary, the server performs secondary authentication using a pre-negotiated password, and then it all comes down to the previous case. On the other hand, the client is extremely important to authenticate the server, he wants to be sure that his data goes exactly to the one to whom he sent them, this side is based in practice on the system of certificates. In general, such a scheme is quite convenient and transparently covered by the https: // protocol, however, a couple of interesting points arise at the interface of cryptography and sociology.
- server trust: even if I transferred some information to the north in an absolutely safe way, outsiders have access to it in a purely technical manner. This problem is completely outside the area of responsibility of encryption, but I ask you to remember this moment, it will pop up later.
- Server Certificate Trust: The certificate hierarchy is based on the fact that there is a certain root certificate that is absolutely trustworthy. Technically, quite an influential attacker
[I ask to consider the word intruder a technical term, not slander or insult to the existing power]It can replace a certificate of any lower level, but it is assumed that the certification system is needed by everyone equally, i.e. this certificate authority will be immediately ostracized and all its certificates will be revoked. So it is so, but still note that the system is not based on technical means, but on some kind of social contract.Speaking of hotAs part of the expecteddoomsdaypupation of the RuNet, has anyone analyzed the possible pupation of the Russian root certificate and the consequences? If someone read / wrote on this topic, send links, I will insert, it seems to me an interesting topic - indirect de-anonymization on the server: also a sore subject, even if the north does not have a formal registration / authentication, there are many ways to collect information about the client and ultimately identify it. It seems to me that the root of the problem is in the existing http: // protocol and the like, which, as expected, could not have foreseen such an outrage; and that it would be entirely possible to create a parallel protocol without these punctures. However, this goes against all existing monetization practices and is therefore unlikely. Still interesting, did anyone try?
- anonymous is anonymous: two meet on the network, (option - just met), (option - not two but two thousand), and they want to rattle about their own, but so that Big Brother does not hear (option - mom did not recognize each their priorities). Perhaps you can hear the irony in my voice, well, it is because this is it. Let's apply to the task of Schneier's postulate ( any algorithm can be hacked if you invest enough resources , that is, money and time). From this point of view, penetration into such a group by social methods is not difficult, not to mention money, that is, the cryptographic strength of the algorithm is zero with the most sophisticated encryption methods.
However, in this case we have a second bastion - anonymity , and we place all our hopes on it, let everyone know us, but no one can find. However, with the most modern technical methods of protection, do you seriously think that you have a chance? I remind you that I’m talking only about anonymization now, we seem to have already convincingly done away with data protection. Let us, for definiteness, agree that if your name or home address or ip-address became known, the turnout was completely failed.
Speaking of ip, here comes the aforementioned trust in the server to its full height, he knows your ip without a doubt. And then everything plays against you - from simple human curiosity and vanity, to corporate policies and the same monetization. Just keep in mind that VPS and VPN are also servers; to theorists from cryptography, these abbreviations are somehow sideways; Yes, and the server’s jurisdiction does not matter when there is a great need. This also includes end-to-end encryption - it sounds nice and solid, but the server still has to believe the word.
What is the general role of the server in this messenger? First, the postman is trivial, if the recipient is not at home, come back later. But also, and this is much more significant, this is a meeting point, you cannot send a letter directly to the addressee, you send it to the server for onward transmission. And most importantly, the server conducts the necessary authentication , certifying for all that you are you, and for you that your interlocutor is really the one you need. And he does it with the help of your phone.
Do not you think that your messenger knows too much about you? No, no, we certainly believe him (and by the way, and his phone at the same time, um), but here the cryptographers claim that it’s in vain that no one can believe at all.
Not convinced? But there is still the same social engineering, if you have a hundred interlocutors in the group, you simply have to mean that 50% of them are enemies, 49% are either vain, or stupid, or simply careless. Yes, and the remaining one percent, no matter how strong you are in the methods of protecting information, you probably cannot resist a good psychologist in a chat.
The only seemingly defensive strategy is to get lost among millions of such groups, but this is no longer about us, again about some terrorist spies who have no network fame or monetization.
Well, it seems to me that I somehow substantiated (no, did not prove, just substantiated) my harsh thoughts about data protection in the modern model of society. The conclusions are simple but sad - we should not expect help from data encryption more than we already have, cryptography did everything it could, and did it well, but our Internet model completely contradicts our desire for privacy and negates all our efforts. In fact, I have never been a pessimist and would really like to say something bright now, but I just don’t know what.
Try to look into the next section, but I warn you - there are completely pink unscientific fantasies, but then you can be encouraged by someone, and you can even cheer on someone.
Can you do anything at all?
Well, for example, to reflect on this topic, it is desirable to liberate consciousness and discard prejudices. For example, let's temporarily completely sacrifice anonymity , however terrible it may sound. Let everyone from birth be given a unique personal public key, and of course, the corresponding private key is natural. No need to shout at me and stomp your feet, in an ideal world it is extremely convenient - here you have your passport and TIN, and even a phone number in one bottle. Moreover, if we add an individual certificate to this, we get a universal authenticator / login; and also a pocket notary with the ability to certify any documents. You can make the system multilevel - in the public domain only the public key and certificate, for friends (the list of keys is attached here) you can make the phone available and whatever else friends trust, there may be even deeper levels, but this already implies unnecessary trust in the server .
With such a scheme, the privacy of the information sent is achieved automatically (although on the other hand, why, in an ideal world?), Alice writes something to Bob, but no one will ever read it except for Bob himself. All instant messengers automatically receive end-to-end encryption, their role is reduced to mailboxes and in principle there can be no complaints about the content. Yes, and the servers themselves become interchangeable, you can send through one, you can through the other, but you can even through a chain of servers, like email. And you can also send to the addressee directly, if his ip is known, without contacting any intermediaries at all. Really cool? The only pity is that I will not have to live in this beautiful time - neither I nor you © H-yes, again I am sad.
Further, where is it all stored? Well, offhand, to make an open hierarchical system, something like the current DNS, only more powerful and branched. In order not to load root DNS admins with add-modifications, one can make free registration, the only necessary check is for uniqueness. Type >> " Hello, there are five of us, the Ivanov family. Here are our names / nicknames, here are the public keys. If you ask, please send to us. And here is a list of hundred-grandmothers from our district with their keys, if they are asked send to us too. "
It is only necessary to make the installation and configuration of such a home server extremely simple and convenient, so that anyone can figure it out if desired, again, no one will once again load all official state servers.
Stop! , and what have then the state in general?
But now you can and carefully restore anonymity. If anyone can generate a private key and confirm it with an individual certificate and install a low-level CA server, or ask a neighbor, or which public server, why do we need all this official membership? Yes, and become attached to the real character then there is no need, complete privacy, security and anonymity. It is enough that at the beginning of the hierarchy there was someone trustworthy, well, we believe in TM or Let's Encrypt, and well-known public DNS'y still did not seem to send anyone to the steppe. On the part of the bureaucracy, too, there seems to be no complaints, that is, there will certainly be complaints, but why?
Perhaps someday such a system, or something like that, will be created. And of course, we have no one to rely on except for ourselves, not one of the states known to me will build such a system. Fortunately, the already existing Telegrams, i2p, Tor, and probably someone else forgot, show that there is nothing fundamentally impossible. This is our network, and we will equip it if we are not satisfied with the status quo.
Brrr, accidentally it turned out to finish on a pretentious note. In fact, I do not like it, somehow I feel closer to sarcasm.
PS: it's all about pink snot and girlish dreams.
PPS: but if someone ever wants to try it - reserve for me nickname degs, please, I'm used to it.
PPPS: and the implementation seems quite simple by the way.
')
Source: https://habr.com/ru/post/446126/
All Articles