NetBIOS in the hands of a hacker
In this article, a brief narration will go about what such a familiar-looking thing like NetBIOS can tell us. What information can it provide to a potential intruder / pentester.
The demonstrated field of application of reconnaissance techniques relates to internal, that is, isolated and externally inaccessible networks. Such networks usually have any even the smallest company.
NetBIOS itself is usually used to obtain a network name. And this will be enough to do at least 4 things.
')
Because NetBIOS can use UDP as a transport, its speed allows it to detect hosts on very large networks. So, for example, the nbtscan tool, included in the same-named packet, can in just 2 seconds (can lay the network) resolve the network addresses of the form 192.168.0.0/16, while the traditional TCP scan will take tens of minutes. This feature can be used as a host sweep on very large networks, about which nothing is known, before running nmap. Although the result does not guarantee 100% detection, since the windows-hosts and not all of them will mostly respond, it will nevertheless allow you to determine in what ranges approximately the live hosts are.
Using the results of getting names from ip-addresses:
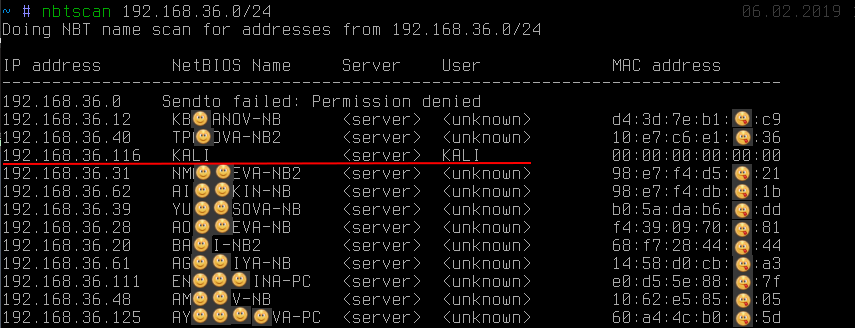
you can see: besides the fact that the name reveals the owner of the workstation (although this is by the way not always the case), one of the addresses clearly stands out from the others. We can see that the name KALI was obtained. This behavior is typical, as a rule, for the unix implementation of SMB / NetBIOS as part of the samba software package or very old Windows 2000 .
Getting the name KALI , while on other hosts, this < unknown > indicates the presence of a so-called null-session . With default settings, the SMB server on linux is prone to it. Null-session only allows you to completely anonymously (and we did not enter any passwords, as you can see on the screen) to get a lot of additional information, such as a local password policy, a list of local users, groups and a list of shared resources (ball):
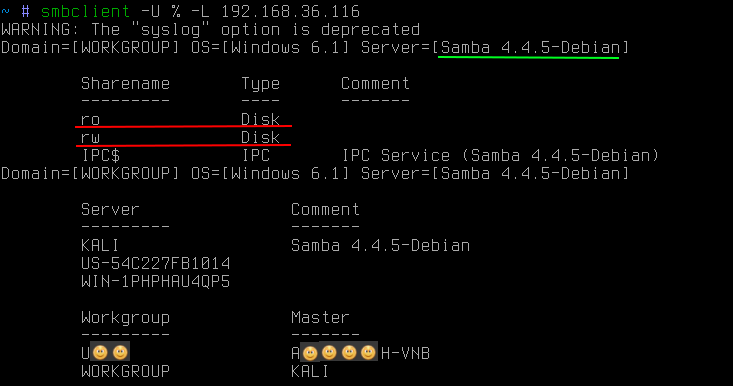
Often on linux SMB -servers there are publicly available balls, not just reading, but even writing. The presence of both of them carries various threats, the use of which is beyond the scope of this article.
NetBIOS also allows you to get the names of all types that the workstation stores:
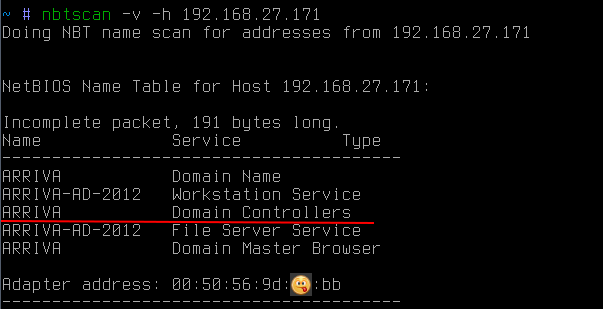
in this case, it lets you know that the host is also the ARRIVA domain controller .
It is also worthwhile to additionally note that NetBIOS allows you to get mac- address. Moreover, unlike arp requests, NetBIOS requests can go beyond the limits of a subnet. This can be useful if, for example, you need to find a laptop or specific hardware on the network, knowing its manufacturer. Since the first three octets of the mac address identify the manufacturer, you can send similar NetBIOS requests to all known subnets to try to find the device you need (http://standards-oui.ieee.org/oui.txt).
Often, when moving across internal corporate networks, it is necessary to attack the workstation included in the domain (for example, to raise privileges to the domain administrator level) or vice versa. In this case, NetBIOS can help again:
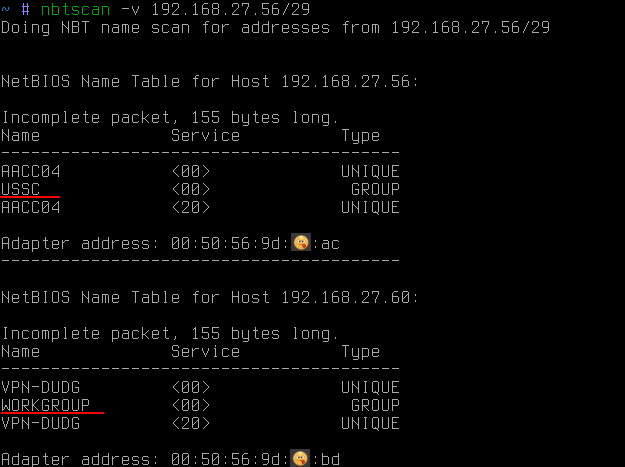
In this case, using NetBIOS all names of all types were obtained. Among them, you can see, in addition to the name of the PC (what has already been received before), and the name of the working group. By default for windows, it is usually something like WORKGROUP or IVAN-PC , but if the workstation is in the domain, then its working group is the domain name.
Thus, using NetBIOS, you can find out whether the workstation is in the domain and, if so, in which.
If you want to get a list of domain hosts within a subnet, then one broadcast request with the name of the required domain will suffice:

as a result, all hosts in this domain will respond.
And finally, another probably very little known technique that is simply indispensable for finding ways to secure, perhaps even physically isolated, networks. It can be shop networks of enterprises, stuffed with controllers. Access to this network for the attacker means the ability to influence the process, and for the enterprise the risk of incurring huge losses.
So, the point is that even if the network is isolated from the corporate network, then often some administrators, whether by their laziness, or even like that, like to put up another network card on their PCs to access this same network. At the same time, all this happens, of course, bypassing all the rules of corporate firewalls. Convenient, yes, but not very safe, if you are hacked, then you will become a bridge to this network and be responsible.
However, for the attacker, there is one problem - to find the administrator who joined the secure network in such an illegal way. Moreover, it is a difficult problem for the network security personnel themselves. In large enterprises, it is truly a difficult task, like finding a needle in a haystack.
In this situation, the obvious options for the attacker would be two:
However, everything is much simpler. There is one extremely simple technique that allows you to get a list of network interfaces from a particular host. Suppose we have a certain host:
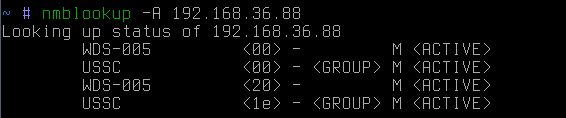
This is a reverse IP address → network name. If we now try to make a direct resolv network name → ip-address:

then we learn that this host is also a gateway (apparently) on some other network. It is worth noting that in this case the request was broadcast. In other words, it will be heard by hosts only from the attacker's subnet.
If the target host is outside the subnet, then you can send a targeted request:
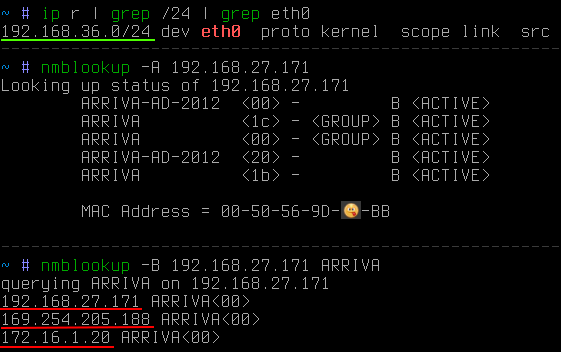
In this case, it is clear that the target is outside the attacker's subnet. Using the –B switch, it was stated that the request should be sent to a specific address, and not to a broadcast address.
Now it only remains to quickly gather information from the entire subnet of interest, and not from a single address. You can use a small python script for this:
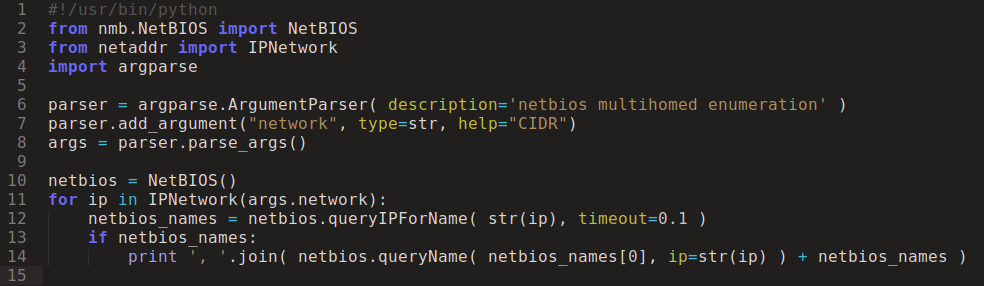
And after a few seconds:
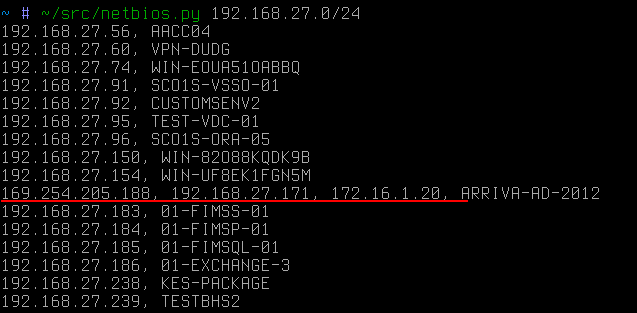
It is a dedicated host, in this improvised case, would be the first target of the attacker, if he pursued the network 172.16.1 / 24.
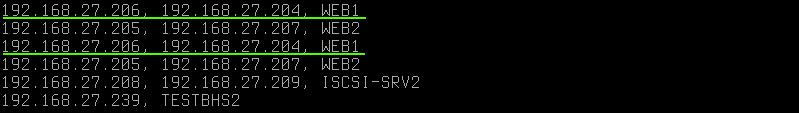
Duplicate names on different ip indicate that the host also has two network cards, but on the same subnet. It is worth noting that NetBIOS does not disclose alias (which can easily be calculated via arp requests as ip with the same mac ). In this case, ip-addresses have different mac .
Another example of using this technique is public Wi-Fi. Sometimes you can come across a situation where among the guest devices, personnel working in a closed corporate segment are connected to the public network. Then, with the help of this intelligence technique, an attacker will very quickly be able to chart his way to a closed network:
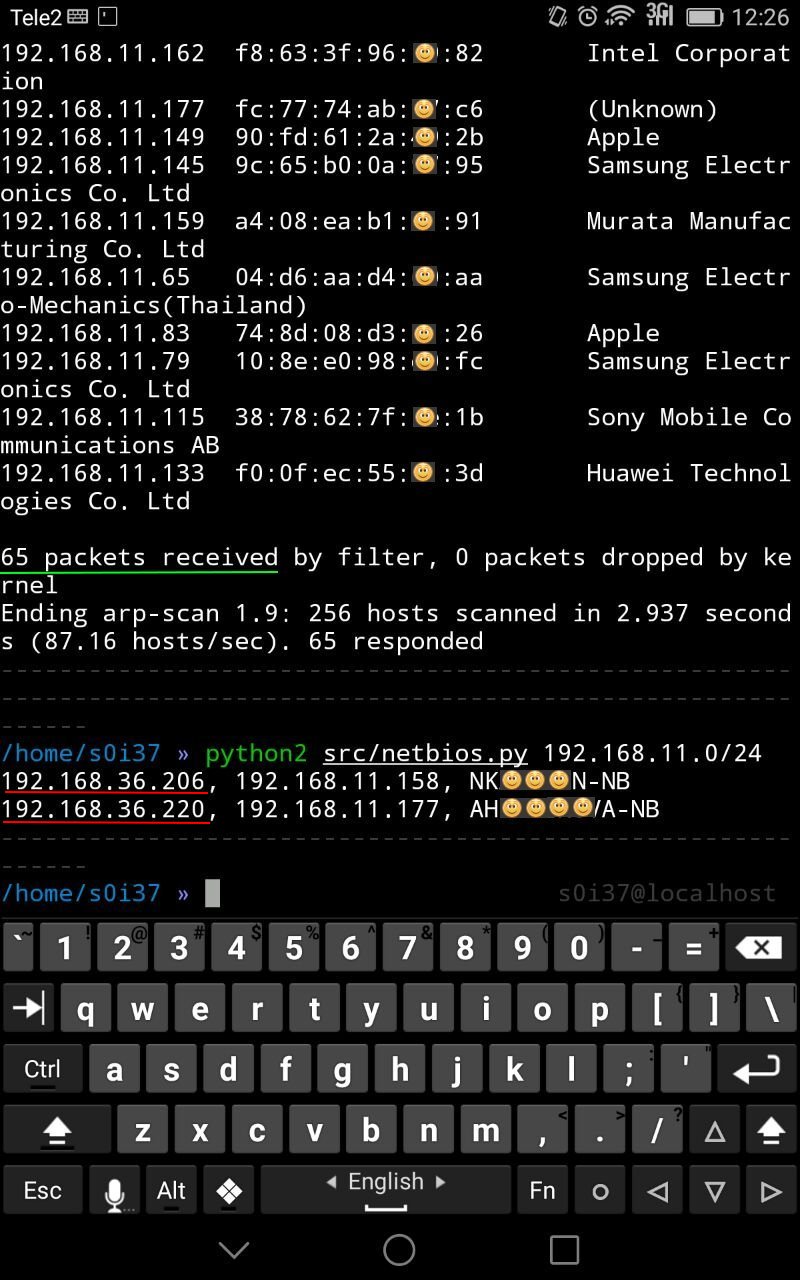
In this case, among the 65 public Wi-Fi clients were two workstations that have an additional interface, probably related to the corporate network.
If sometimes filtering traffic to the 445 / tcp port is observed between the network segments or directly at the workstations, preventing remote logging into the system (remote code execution), in this case, the 137 / udp port is used to resolve names using NetBIOS; is encountered, since the convenience of working in the network will suffer from this, for example, the network environment may disappear, etc.
As the saying goes, enumeration is the key
Is there any protection against this? It is not, because this is not a vulnerability in all. This is just the regular functionality of the little windows default (the behavior is slightly different in linux ). And if you suddenly inconsistently, bypassing the rules of network routing, are included in the closed segment, then the attacker will find you and do it very quickly.
The demonstrated field of application of reconnaissance techniques relates to internal, that is, isolated and externally inaccessible networks. Such networks usually have any even the smallest company.
NetBIOS itself is usually used to obtain a network name. And this will be enough to do at least 4 things.
')
Host Discovery
Because NetBIOS can use UDP as a transport, its speed allows it to detect hosts on very large networks. So, for example, the nbtscan tool, included in the same-named packet, can in just 2 seconds (can lay the network) resolve the network addresses of the form 192.168.0.0/16, while the traditional TCP scan will take tens of minutes. This feature can be used as a host sweep on very large networks, about which nothing is known, before running nmap. Although the result does not guarantee 100% detection, since the windows-hosts and not all of them will mostly respond, it will nevertheless allow you to determine in what ranges approximately the live hosts are.
Host Identification
Using the results of getting names from ip-addresses:

you can see: besides the fact that the name reveals the owner of the workstation (although this is by the way not always the case), one of the addresses clearly stands out from the others. We can see that the name KALI was obtained. This behavior is typical, as a rule, for the unix implementation of SMB / NetBIOS as part of the samba software package or very old Windows 2000 .
Getting the name KALI , while on other hosts, this < unknown > indicates the presence of a so-called null-session . With default settings, the SMB server on linux is prone to it. Null-session only allows you to completely anonymously (and we did not enter any passwords, as you can see on the screen) to get a lot of additional information, such as a local password policy, a list of local users, groups and a list of shared resources (ball):

Often on linux SMB -servers there are publicly available balls, not just reading, but even writing. The presence of both of them carries various threats, the use of which is beyond the scope of this article.
NetBIOS also allows you to get the names of all types that the workstation stores:

in this case, it lets you know that the host is also the ARRIVA domain controller .
It is also worthwhile to additionally note that NetBIOS allows you to get mac- address. Moreover, unlike arp requests, NetBIOS requests can go beyond the limits of a subnet. This can be useful if, for example, you need to find a laptop or specific hardware on the network, knowing its manufacturer. Since the first three octets of the mac address identify the manufacturer, you can send similar NetBIOS requests to all known subnets to try to find the device you need (http://standards-oui.ieee.org/oui.txt).
Determining Domain Membership
Often, when moving across internal corporate networks, it is necessary to attack the workstation included in the domain (for example, to raise privileges to the domain administrator level) or vice versa. In this case, NetBIOS can help again:

In this case, using NetBIOS all names of all types were obtained. Among them, you can see, in addition to the name of the PC (what has already been received before), and the name of the working group. By default for windows, it is usually something like WORKGROUP or IVAN-PC , but if the workstation is in the domain, then its working group is the domain name.
Thus, using NetBIOS, you can find out whether the workstation is in the domain and, if so, in which.
If you want to get a list of domain hosts within a subnet, then one broadcast request with the name of the required domain will suffice:

as a result, all hosts in this domain will respond.
Multihomed host detection
And finally, another probably very little known technique that is simply indispensable for finding ways to secure, perhaps even physically isolated, networks. It can be shop networks of enterprises, stuffed with controllers. Access to this network for the attacker means the ability to influence the process, and for the enterprise the risk of incurring huge losses.
So, the point is that even if the network is isolated from the corporate network, then often some administrators, whether by their laziness, or even like that, like to put up another network card on their PCs to access this same network. At the same time, all this happens, of course, bypassing all the rules of corporate firewalls. Convenient, yes, but not very safe, if you are hacked, then you will become a bridge to this network and be responsible.
However, for the attacker, there is one problem - to find the administrator who joined the secure network in such an illegal way. Moreover, it is a difficult problem for the network security personnel themselves. In large enterprises, it is truly a difficult task, like finding a needle in a haystack.
In this situation, the obvious options for the attacker would be two:
- Try to use each PC in the corporate subnet as a gateway to the desired network. It would be very convenient, but this is rare, since on windows hosts ip forwarding is almost always disabled. Moreover, such verification is possible only within its own subnet, and it also requires the attacker to know the target address from an isolated network.
- try to remotely login to each host and execute the banal ipconfig / ifconfig command. And here is not so smooth. Even if the attacker has secured the rights of the domain administrator, the firewalls and local firewalls have not been canceled. So this task is not 100% automated. As a result, it remains painful to go to each host, overcoming firewalls (often blocking exactly 445 / tcp port), hoping to finally see the desired network interface.
However, everything is much simpler. There is one extremely simple technique that allows you to get a list of network interfaces from a particular host. Suppose we have a certain host:

This is a reverse IP address → network name. If we now try to make a direct resolv network name → ip-address:

then we learn that this host is also a gateway (apparently) on some other network. It is worth noting that in this case the request was broadcast. In other words, it will be heard by hosts only from the attacker's subnet.
If the target host is outside the subnet, then you can send a targeted request:

In this case, it is clear that the target is outside the attacker's subnet. Using the –B switch, it was stated that the request should be sent to a specific address, and not to a broadcast address.
Now it only remains to quickly gather information from the entire subnet of interest, and not from a single address. You can use a small python script for this:

And after a few seconds:

It is a dedicated host, in this improvised case, would be the first target of the attacker, if he pursued the network 172.16.1 / 24.

Duplicate names on different ip indicate that the host also has two network cards, but on the same subnet. It is worth noting that NetBIOS does not disclose alias (which can easily be calculated via arp requests as ip with the same mac ). In this case, ip-addresses have different mac .
Another example of using this technique is public Wi-Fi. Sometimes you can come across a situation where among the guest devices, personnel working in a closed corporate segment are connected to the public network. Then, with the help of this intelligence technique, an attacker will very quickly be able to chart his way to a closed network:

In this case, among the 65 public Wi-Fi clients were two workstations that have an additional interface, probably related to the corporate network.
If sometimes filtering traffic to the 445 / tcp port is observed between the network segments or directly at the workstations, preventing remote logging into the system (remote code execution), in this case, the 137 / udp port is used to resolve names using NetBIOS; is encountered, since the convenience of working in the network will suffer from this, for example, the network environment may disappear, etc.
As the saying goes, enumeration is the key
Is there any protection against this? It is not, because this is not a vulnerability in all. This is just the regular functionality of the little windows default (the behavior is slightly different in linux ). And if you suddenly inconsistently, bypassing the rules of network routing, are included in the closed segment, then the attacker will find you and do it very quickly.
Source: https://habr.com/ru/post/445212/
All Articles