New cybersecurity threats: everything is much bigger than you thought
The world and society are changing rapidly, becoming more and more computerized, technology-dependent. In some ways this creates the illusion of freedom. If before the employees were tied to the office, then now they have the opportunity to work anywhere: opened the laptop, started the mail, connected to the company's server, and off. Mobility and teleworking is a global trend. Millennials and the so-called "generation Z" flatly refuse to sit in the office. And by 2025 they will be 75% of the workforce .

Moreover, modern technologies make it possible to work from home, and this is not only a higher level of flexibility, but also greater efficiency of employees. This approach offers an increasing number of enterprises, which gives employees the opportunity to perform their work in more comfortable conditions. According to Eurostat , 35% of businesses in Europe currently offer their employees the opportunity to work from home. But there is a downside.
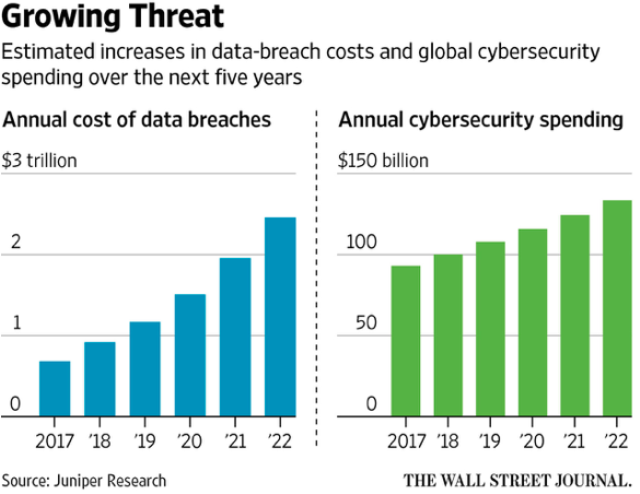
The growing number of employees working outside the office poses difficult security problems for IT departments. Total costs in this area are growing year by year, and gaps in the IT security system are becoming more expensive.
')
The IT security market is one of the fastest growing, but still immature. As an example, you can tell an interesting story that happened to one of the casinos in Las Vegas. Needless to say, the casinos are very carefully monitoring the security of their data, but trouble has come from no one expected. In the lobby of the casino there was an aquarium with exotic sea fishes, and the casino installed a “smart” thermostat to make it more convenient to control the state of the water. The attackers managed to break the thermostat, through it got access to the casino's internal network and downloaded from there everything they needed. About what happened in the casino only found out a few months later.
In fact, the existing risks are quite varied and extensive, and the future seems even more frightening. Data loss can occur in various forms, such as stealing a password or even a computer itself. According to statistics, about 70% of all security incidents in the world are linked to “ identity theft ”. Such a cybercrime occurs every two seconds. And in more than 80% of cases, the cause is weak passwords .
All this can lead to the fact that criminals can get their hands on confidential personal or corporate information. For this reason, many enterprises do not take full advantage of the possibility of branchless work of employees. On the whole, sometimes a paradoxical situation sometimes arises: innovative solutions that should protect users sometimes carry risks for themselves. And new technologies mean new risks and threats.
According to researchers , in the coming years, the world will see an unprecedented "flowering of cybercrime." The development of technology and the erasing of the lines between personal and work devices, mainly smartphones, laptops and tablet computers (most of them will have a permanent connection to the Internet) will lead to the fact that intruders have access to personal data, corporate confidential and secret information, much easier.
The role of PCs is changing, new form factors are emerging, for example, folding devices. Molecular, optical and quantum devices are being developed, new types of interfaces are being developed.

Gadgets and smart devices collect a wide variety of information about their owners. It seems that “smart houses” will know everything about their tenants. Danger conceals everything that connects to the Internet. Even in Tesla electric vehicles found vulnerability , and remote exposure can lead to death. All this increases the number of vectors of digital attacks.
Information security threats are taking on a completely new look. This applies to all three types of tasks that must address the remedies, including threats to accessibility, integrity, and confidentiality:
Almost everyone faces information security threats. Significant risks are malware (viruses, worms, Trojans, ransomware), phishing (gaining access to user logins and passwords) and identity theft (using other people's personal data). The subject of hunting can be accounts in social networks and applications, passport data and credit card information.
Thus, according to the US Bureau of Labor Statistics (BJS), the annual losses from personal identity theft (Identity Theft) in the country are close to $ 25 billion. At that, the damage from all other thefts (household thefts, car thefts, robberies) does not exceed 14 million dollars
Neglect of security principles caused a number of large-scale data thefts: Equifax, Yahoo (twice), MySpace, Heartland Payment Systems, Sony PlayStation Network, CardSystems Solutions and TJ Maxx compromised a total of about a billion accounts.
One of the most high-profile data breaches in recent years has been the Equifax case - one of the three main credit reporting agencies. The victims were about 147.9 million people. Or an incident with Uber in 2016, when hackers stole data on 57 million Uber clients, and the company paid $ 100,000 to hide the fact of theft.
Meanwhile, criminals are already actively exploring such areas as robotics, artificial intelligence. There is nothing good about the hacker gaining access to confidential financial information, intellectual property, customer information and / or company employees. But in the situation of the Internet of Things (IoT), the stakes are even higher. Imagine the potentially terrible consequences for people of using a hacker’s vulnerability in autonomous cars, power grids or medical devices with remote monitoring functions.
This requires new means of protection. For example, no matter how we today rely on the antivirus installed on our PCs, any personal computer is 95% defenseless. Mark Goodman, computer security specialist and author of the book “Threats and Crimes of the Future”, compares such a situation with human immunity: if a man were not so immune from infection as today's computers, he would have died in a few hours. The antivirus era, according to the author, is over.
Today it is difficult to isolate any separate breakthrough information security technology. The “newest” areas currently being developed are mainly introduced for the first time more than ten years ago. These include, for example, machine learning, and detection technology in the cloud.

Meanwhile, companies that do not provide protection for their products will leave the market in three to four years. Cyber attacks are moving from the financial sector to industry, the transport industry, retail and other sectors of the economy, new objects of attack have appeared, for example, networks of IoT devices, and the complexity and complexity of threats is increasing. Businesses are aware of the importance of protecting their IT infrastructure and information, and are increasingly investing in “secure” IT solutions.
The rapid pace of product development and the presence of a constant threat from hackers lead to the fact that no manufacturer can guarantee one hundred percent absence of vulnerabilities in their products. However, most vendors understand that they need to protect customers from ever-changing security threats, and the products and solutions they provide must contain means to protect the confidentiality, integrity and availability of data. A team of security professionals with experience in various fields is working on this. Of course, the approaches of all vendors are different. Here is what Lenovo is doing in this area:
All of these measures help you monitor potential risks on an ongoing basis and use ways to reduce them.
Active work on the inaccessibility of devices leads to more reliable and convenient means of protection. At the same time, in a number of areas, one has to act in advance so as not to be like, according to Winston Churchill's famous maxim, “generals who are always preparing for the last war”.
Of course, you need to understand that no security strategy is absolutely perfect. However, the means, measures and security policies are intrusive and adversely affect user productivity. According to the study of the Dimensional Research: The Value of a Great Desktop Experience, 62% of users said that “unobtrusive security” is a very important factor in increasing their productivity.
Lenovo makes a lot of effort to ensure that its products are at least as competitive as the quality of security solutions. For example, it offers multi-component and multi-factor authentication systems that can work both individually and in combination. Among them there are standard ones, such as fingerprint scanners, and there are more interesting ones, such as, for example, IP-based protection and GPS tracker protection. As one of the safest options, the company offers the use of smart cards that are inserted into a laptop.

Lenovo also works in partnership with Intel, Microsoft, Absolute and other vendors to ensure security during work. For example, there is a proprietary utility from Coronet for protection when connected to public Wi-Fi networks.
In addition, Lenovo is one of the founders of the FIDO Alliance. FIDO, which includes the giants of the global IT industry (Google, Microsoft, Amazon, Intel, Infenion, NXP, Lenovo, RSA), companies from the financial sector (PayPal, MasterCard, VISA, Goldman Cachs, ING) and many smaller companies, offers secure way to register in the cloud and provides transaction protection through fingerprint verification. In this case, passwords are no longer sent to the database servers. Encryption is performed using public keys, while the keys remain on the devices. With this protection scheme, in addition, it is impossible to track the relationship between services. The FIDO paradigm is safety and usability.

The versatility and standardization of the U2F technology (Universal Second Factor), promoted by the FIDO Alliance in recent years, promise it a great future, but so far it has not gained mass distribution.
The essence of the technology is as follows. For authentication, a Google Chrome web browser that supports the U2F specification is used. During the registration process, the user presents the U2F device, which generates the cryptographic keys that will be used for authentication. Public keys are sent to web resources and stored in user accounts. For authentication, a protocol based on asymmetric cryptography is used. For authentication, the user enters a username and password, and then connects a device that performs operations without entering a PIN code.
How to ensure confidentiality, availability and integrity of information? By continuing to use traditional password authentication to access their information resources, companies actually put them at risk. This applies primarily to companies in the financial sector. Indeed, according to statistics, about 80% of information security incidents occur due to the use of weak passwords. Weak user passwords - the most vulnerable place used by hackers.
The advantages of multifactor authentication include its ability to protect information from both internal threats and external intrusions. It is based on the sharing of multiple authentication factors, which greatly increases security.
A well-known example is SMS authentication based on the use of a one-time password. The advantage of this approach, compared to a permanent password, is that this password cannot be reused. An example of the use of biometric devices and authentication methods is the use of a fingerprint scanner with confirmation of authority with a password. Other biometric authenticators can be used in a similar way: the outlines and sizes of the face; voice characteristics; the pattern of the iris and retina; voice authentication
There are also software and hardware solutions, such as autonomous keys for generating one-time passwords, readers of RFID tags, software and hardware tokens, electronic keys of various types.
As the second factor of authentication (the first is the password), biometrics can be used. For example, “Match-On-Card”, “Match-On-Chip” and similar technologies allow you to replace PIN input with fingerprint analysis, which adds ease of use, since you do not need to memorize and enter a PIN code.
Lenovo ThinkPad laptops use advanced biometric authentication, a camera that supports face recognition to log on to Windows Hello. The computer can be equipped with a built-in fingerprint recognition device. Intel Software Guard Extensions (SGX) protects user data, and the fingerprint scanner provides a high level of security through TLS 1.2 encryption.
Fingerprint scanner with Match-on-Chip technology adds another level of security. Lenovo Biometric Fingerprint Recognition with Intel Active Management (AMT) technology simplifies access control and security policies.
The fingerprint scanner only forms a bitmap image of the fingerprint pattern. Further processing of the image, formation of a template based on it, loading of the template into a smart chip. Pattern matching is performed inside a chip that supports Match-on-chip technology. Such technology of biometric control allows building reliable solutions with two- or three-factor authentication. The biometric identification method can be used both in place of the PIN code and in combination with it. Since the comparison is made exclusively inside a special chip, high security of the authentication process is ensured.
By registering your fingerprint and associating it with a password when you turn on the PC, a password to access the hard disk, or both passwords, the user can log in to the ThinkPad Setup without entering the password: fingerprint authentication will be used instead of passwords, which ensures simple and secure user access.
For additional protection, you can install the Client Security Solution. The ClientSecurity Solution program is compatible with several authentication mechanisms (for example, mechanisms that include fingerprint and smart card authentication).
Fingerprint scanner is very reliable. As already noted, it uses the technology of Match-on-chip. In this version of the fingerprint scanner, authentication data is stored immediately in the chip - this option is more difficult to circumvent.
The entered data is processed by the scanner, and the fingerprint processing module is responsible for all fingerprint images, preventing unauthorized entry into the system.
Fingerprint scanners today are used in many places. And this is not only government and commercial structures. In consumer electronics, compact fingerprint scanners are also used - these are desktops, laptops, smartphones. It may be an illusion that you are very well protected. But is it? There are a number of ways to "cheat" such systems. At Lenovo, the Match-on-Chip fingerprint scanner places fingerprint scans in a secure storage on an FPR chip, which provides additional data protection against intruders.
The laptop also has a built-in Trusted Platform Module (dTPM) that encrypts user data. The Fast Identity Online or FIDO authentication feature provides stricter authentication and three-level information protection. FIDO authentication is used to control credentials when visiting sites such as Facebook or Google, or making payments via PayPal, Visa, etc. The ThinkPad became the first corporate laptop with authentication support for PayPal authorized by FIDO. Built-in fingerprint scanner allows you to log into your PayPal account.

You can also access sites using a fingerprint scanner through the Universal Authentication Framework (UAF) or buttons on the screen through the Universal 2nd Factor (U2F). With these built-in FIDO authentication methods, websites receive fully protected security keys, which significantly increases the level of protection of personal information and prevents fraud.
The scanner can also serve as an additional protection factor besides using a standard ID and password. Unlike individual security keys or SMS codes, an additional authentication factor is built into the PC, providing greater protection for personal data and simplifying the process of logging into Google, Facebook, Dropbox and other services.
These developments were included in the set of protective equipment presented at the end of last year, called the ThinkShield. This platform comprehensively protects Lenovo devices and combats common vulnerabilities. ThinkShield was designed to protect devices, protect against identity theft on the Internet, and protect sensitive data.
To protect against such incidents, a complex of protective measures is needed. That is why Lenovo ThinkShield provides basic privacy, authentication, data protection and network vulnerability detection.
ThinkShield security tools for ThinkPad computers, Lenovo has a key role to play. It includes a whole range of protective equipment, from the simplest to the most advanced:
For example, the Lenovo ThinkShutter camera shutter allows the user to decide for himself whether someone will see it. There are thousands of videos online where the hero (or heroine) doesn’t even know that the laptop’s camera is recording. Now, so that this does not happen, you do not need to stick the cameras on laptops with tape. There is a more elegant solution to protect your privacy. You need to call via Skype - open the curtain. I want to be "invisible" - close, so as not to become a "YouTube hero". The solution is not new, but effective and convenient.

All systems with ThinkShield support FIDO — a standard for secure authentication offered by Microsoft Hello Windows, as well as Intel Authenticate with multi-factor authentication. A high level of integration with Intel Authenticate (up to seven factors) guarantees a higher degree of security and flexibility than solutions that provide fewer authentication methods.
As a founding member of FIDO , Lenovo offers FIDO certified authentication tools. This certification means that you use a secure way to register in the cloud and protect transactions using fingerprint verification. This uses encryption using public keys that remain on the device: passwords are no longer sent to database servers.
Another important point: sometimes it is necessary to disconnect the USB ports on a computer or laptop in order to limit the connection of flash drives, hard drives and other USB devices. Disabling USB ports will help prevent drives from being connected, which could potentially be used to steal sensitive information or cause a computer to become infected with a virus and spread malicious software over a local network.
BIOS-based Smart USB protection allows IT professionals to configure USB ports so that PCs respond only to keyboards and pointing devices, ensuring the safety of employees' computers. Thus, the USB ports on the PC can be blocked so that users cannot pick up malware or download data from the device.
Another source of threats is wireless networks. Sometimes connecting to a free-access wireless network can lead to negative consequences. You risk opening access to personal information, location and files. By connecting to a free Wi-Fi network, you often put your personal data "on display". , , .
, , SMS, -. « » .
Lenovo WiFi Security , . .
, ? Buffer Zone , . ThinkShield Buffer Zone — , , , .
MobileIron. Lenovo Endpoint Management MobileIron .
MobileIron . . , , , .
Lenovo , - , , , .
Absolute Persistence , , .
, ThinkShield .
, , . , «» . , .
ThinkShield Lenovo , - ThinkPad. , .

, , , Lenovo — .
, , . , . Lenovo ThinkPad ThinkShield , .
BIOS . Lenovo BIOS , .
, ThinkShield Lenovo, , , . , , – , . , .
, , , . , . , - .

Moreover, modern technologies make it possible to work from home, and this is not only a higher level of flexibility, but also greater efficiency of employees. This approach offers an increasing number of enterprises, which gives employees the opportunity to perform their work in more comfortable conditions. According to Eurostat , 35% of businesses in Europe currently offer their employees the opportunity to work from home. But there is a downside.
The growing number of employees working outside the office poses difficult security problems for IT departments. Total costs in this area are growing year by year, and gaps in the IT security system are becoming more expensive.
')

The IT security market is one of the fastest growing, but still immature. As an example, you can tell an interesting story that happened to one of the casinos in Las Vegas. Needless to say, the casinos are very carefully monitoring the security of their data, but trouble has come from no one expected. In the lobby of the casino there was an aquarium with exotic sea fishes, and the casino installed a “smart” thermostat to make it more convenient to control the state of the water. The attackers managed to break the thermostat, through it got access to the casino's internal network and downloaded from there everything they needed. About what happened in the casino only found out a few months later.
In fact, the existing risks are quite varied and extensive, and the future seems even more frightening. Data loss can occur in various forms, such as stealing a password or even a computer itself. According to statistics, about 70% of all security incidents in the world are linked to “ identity theft ”. Such a cybercrime occurs every two seconds. And in more than 80% of cases, the cause is weak passwords .
All this can lead to the fact that criminals can get their hands on confidential personal or corporate information. For this reason, many enterprises do not take full advantage of the possibility of branchless work of employees. On the whole, sometimes a paradoxical situation sometimes arises: innovative solutions that should protect users sometimes carry risks for themselves. And new technologies mean new risks and threats.
PCs of the future and new threats
According to researchers , in the coming years, the world will see an unprecedented "flowering of cybercrime." The development of technology and the erasing of the lines between personal and work devices, mainly smartphones, laptops and tablet computers (most of them will have a permanent connection to the Internet) will lead to the fact that intruders have access to personal data, corporate confidential and secret information, much easier.
The role of PCs is changing, new form factors are emerging, for example, folding devices. Molecular, optical and quantum devices are being developed, new types of interfaces are being developed.

Gadgets and smart devices collect a wide variety of information about their owners. It seems that “smart houses” will know everything about their tenants. Danger conceals everything that connects to the Internet. Even in Tesla electric vehicles found vulnerability , and remote exposure can lead to death. All this increases the number of vectors of digital attacks.
Information security threats are taking on a completely new look. This applies to all three types of tasks that must address the remedies, including threats to accessibility, integrity, and confidentiality:
- Violations of the system and their supporting infrastructure.
- Forgery and theft of information.
- The dangers posed by the unreliable protection of confidential information, whether it is corporate data or information about individuals.
Almost everyone faces information security threats. Significant risks are malware (viruses, worms, Trojans, ransomware), phishing (gaining access to user logins and passwords) and identity theft (using other people's personal data). The subject of hunting can be accounts in social networks and applications, passport data and credit card information.
Thus, according to the US Bureau of Labor Statistics (BJS), the annual losses from personal identity theft (Identity Theft) in the country are close to $ 25 billion. At that, the damage from all other thefts (household thefts, car thefts, robberies) does not exceed 14 million dollars
Neglect of security principles caused a number of large-scale data thefts: Equifax, Yahoo (twice), MySpace, Heartland Payment Systems, Sony PlayStation Network, CardSystems Solutions and TJ Maxx compromised a total of about a billion accounts.
One of the most high-profile data breaches in recent years has been the Equifax case - one of the three main credit reporting agencies. The victims were about 147.9 million people. Or an incident with Uber in 2016, when hackers stole data on 57 million Uber clients, and the company paid $ 100,000 to hide the fact of theft.
Meanwhile, criminals are already actively exploring such areas as robotics, artificial intelligence. There is nothing good about the hacker gaining access to confidential financial information, intellectual property, customer information and / or company employees. But in the situation of the Internet of Things (IoT), the stakes are even higher. Imagine the potentially terrible consequences for people of using a hacker’s vulnerability in autonomous cars, power grids or medical devices with remote monitoring functions.
How to protect against new threats?
This requires new means of protection. For example, no matter how we today rely on the antivirus installed on our PCs, any personal computer is 95% defenseless. Mark Goodman, computer security specialist and author of the book “Threats and Crimes of the Future”, compares such a situation with human immunity: if a man were not so immune from infection as today's computers, he would have died in a few hours. The antivirus era, according to the author, is over.
Today it is difficult to isolate any separate breakthrough information security technology. The “newest” areas currently being developed are mainly introduced for the first time more than ten years ago. These include, for example, machine learning, and detection technology in the cloud.

Meanwhile, companies that do not provide protection for their products will leave the market in three to four years. Cyber attacks are moving from the financial sector to industry, the transport industry, retail and other sectors of the economy, new objects of attack have appeared, for example, networks of IoT devices, and the complexity and complexity of threats is increasing. Businesses are aware of the importance of protecting their IT infrastructure and information, and are increasingly investing in “secure” IT solutions.
The rapid pace of product development and the presence of a constant threat from hackers lead to the fact that no manufacturer can guarantee one hundred percent absence of vulnerabilities in their products. However, most vendors understand that they need to protect customers from ever-changing security threats, and the products and solutions they provide must contain means to protect the confidentiality, integrity and availability of data. A team of security professionals with experience in various fields is working on this. Of course, the approaches of all vendors are different. Here is what Lenovo is doing in this area:
| Security architecture | Compliance with technical requirements for product design and development strategy |
| BIOS / firmware / application security | Code Verification and Authentication |
| Ethical hacking | White Hacker Vulnerability Testing |
| Supply chain | Careful safety assessment of each vendor providing components, assemblies, firmware, software, and user configurations |
| Support | Troubleshoot and resolve customer issues |
| Incident Response | Measures to reduce risks and eliminate identified problems |
| Project management | Contractor monitoring and program management |
| Customer awareness | Security incident reports and company strategy notifications |
All of these measures help you monitor potential risks on an ongoing basis and use ways to reduce them.
Active work on the inaccessibility of devices leads to more reliable and convenient means of protection. At the same time, in a number of areas, one has to act in advance so as not to be like, according to Winston Churchill's famous maxim, “generals who are always preparing for the last war”.
Of course, you need to understand that no security strategy is absolutely perfect. However, the means, measures and security policies are intrusive and adversely affect user productivity. According to the study of the Dimensional Research: The Value of a Great Desktop Experience, 62% of users said that “unobtrusive security” is a very important factor in increasing their productivity.
My device is my castle
Lenovo makes a lot of effort to ensure that its products are at least as competitive as the quality of security solutions. For example, it offers multi-component and multi-factor authentication systems that can work both individually and in combination. Among them there are standard ones, such as fingerprint scanners, and there are more interesting ones, such as, for example, IP-based protection and GPS tracker protection. As one of the safest options, the company offers the use of smart cards that are inserted into a laptop.

Lenovo also works in partnership with Intel, Microsoft, Absolute and other vendors to ensure security during work. For example, there is a proprietary utility from Coronet for protection when connected to public Wi-Fi networks.
In addition, Lenovo is one of the founders of the FIDO Alliance. FIDO, which includes the giants of the global IT industry (Google, Microsoft, Amazon, Intel, Infenion, NXP, Lenovo, RSA), companies from the financial sector (PayPal, MasterCard, VISA, Goldman Cachs, ING) and many smaller companies, offers secure way to register in the cloud and provides transaction protection through fingerprint verification. In this case, passwords are no longer sent to the database servers. Encryption is performed using public keys, while the keys remain on the devices. With this protection scheme, in addition, it is impossible to track the relationship between services. The FIDO paradigm is safety and usability.

The versatility and standardization of the U2F technology (Universal Second Factor), promoted by the FIDO Alliance in recent years, promise it a great future, but so far it has not gained mass distribution.
The essence of the technology is as follows. For authentication, a Google Chrome web browser that supports the U2F specification is used. During the registration process, the user presents the U2F device, which generates the cryptographic keys that will be used for authentication. Public keys are sent to web resources and stored in user accounts. For authentication, a protocol based on asymmetric cryptography is used. For authentication, the user enters a username and password, and then connects a device that performs operations without entering a PIN code.
Multifactor authentication
How to ensure confidentiality, availability and integrity of information? By continuing to use traditional password authentication to access their information resources, companies actually put them at risk. This applies primarily to companies in the financial sector. Indeed, according to statistics, about 80% of information security incidents occur due to the use of weak passwords. Weak user passwords - the most vulnerable place used by hackers.
The advantages of multifactor authentication include its ability to protect information from both internal threats and external intrusions. It is based on the sharing of multiple authentication factors, which greatly increases security.
A well-known example is SMS authentication based on the use of a one-time password. The advantage of this approach, compared to a permanent password, is that this password cannot be reused. An example of the use of biometric devices and authentication methods is the use of a fingerprint scanner with confirmation of authority with a password. Other biometric authenticators can be used in a similar way: the outlines and sizes of the face; voice characteristics; the pattern of the iris and retina; voice authentication
There are also software and hardware solutions, such as autonomous keys for generating one-time passwords, readers of RFID tags, software and hardware tokens, electronic keys of various types.
As the second factor of authentication (the first is the password), biometrics can be used. For example, “Match-On-Card”, “Match-On-Chip” and similar technologies allow you to replace PIN input with fingerprint analysis, which adds ease of use, since you do not need to memorize and enter a PIN code.
Lenovo ThinkPad laptops use advanced biometric authentication, a camera that supports face recognition to log on to Windows Hello. The computer can be equipped with a built-in fingerprint recognition device. Intel Software Guard Extensions (SGX) protects user data, and the fingerprint scanner provides a high level of security through TLS 1.2 encryption.
Fingerprint scanner with Match-on-Chip technology adds another level of security. Lenovo Biometric Fingerprint Recognition with Intel Active Management (AMT) technology simplifies access control and security policies.
The fingerprint scanner only forms a bitmap image of the fingerprint pattern. Further processing of the image, formation of a template based on it, loading of the template into a smart chip. Pattern matching is performed inside a chip that supports Match-on-chip technology. Such technology of biometric control allows building reliable solutions with two- or three-factor authentication. The biometric identification method can be used both in place of the PIN code and in combination with it. Since the comparison is made exclusively inside a special chip, high security of the authentication process is ensured.
By registering your fingerprint and associating it with a password when you turn on the PC, a password to access the hard disk, or both passwords, the user can log in to the ThinkPad Setup without entering the password: fingerprint authentication will be used instead of passwords, which ensures simple and secure user access.
For additional protection, you can install the Client Security Solution. The ClientSecurity Solution program is compatible with several authentication mechanisms (for example, mechanisms that include fingerprint and smart card authentication).
Fingerprint scanner is very reliable. As already noted, it uses the technology of Match-on-chip. In this version of the fingerprint scanner, authentication data is stored immediately in the chip - this option is more difficult to circumvent.
The entered data is processed by the scanner, and the fingerprint processing module is responsible for all fingerprint images, preventing unauthorized entry into the system.
Fingerprint scanners today are used in many places. And this is not only government and commercial structures. In consumer electronics, compact fingerprint scanners are also used - these are desktops, laptops, smartphones. It may be an illusion that you are very well protected. But is it? There are a number of ways to "cheat" such systems. At Lenovo, the Match-on-Chip fingerprint scanner places fingerprint scans in a secure storage on an FPR chip, which provides additional data protection against intruders.
The laptop also has a built-in Trusted Platform Module (dTPM) that encrypts user data. The Fast Identity Online or FIDO authentication feature provides stricter authentication and three-level information protection. FIDO authentication is used to control credentials when visiting sites such as Facebook or Google, or making payments via PayPal, Visa, etc. The ThinkPad became the first corporate laptop with authentication support for PayPal authorized by FIDO. Built-in fingerprint scanner allows you to log into your PayPal account.

You can also access sites using a fingerprint scanner through the Universal Authentication Framework (UAF) or buttons on the screen through the Universal 2nd Factor (U2F). With these built-in FIDO authentication methods, websites receive fully protected security keys, which significantly increases the level of protection of personal information and prevents fraud.
The scanner can also serve as an additional protection factor besides using a standard ID and password. Unlike individual security keys or SMS codes, an additional authentication factor is built into the PC, providing greater protection for personal data and simplifying the process of logging into Google, Facebook, Dropbox and other services.
What is the “security platform” for?
These developments were included in the set of protective equipment presented at the end of last year, called the ThinkShield. This platform comprehensively protects Lenovo devices and combats common vulnerabilities. ThinkShield was designed to protect devices, protect against identity theft on the Internet, and protect sensitive data.
To protect against such incidents, a complex of protective measures is needed. That is why Lenovo ThinkShield provides basic privacy, authentication, data protection and network vulnerability detection.
| Protective function | What is it for? |
| Identity Protection | Prevent unauthorized access through the use of biometric data, face recognition technology and other authentication procedures. |
| Internet security | Securely connect and prevent identity theft, protection against malware and phishing. |
| Data security | Preventing theft or loss of data on the device, ensuring compliance with data disclosure requirements. |
| Safe packaging | Physical protection thanks to packaging with control of the first opening, reliable and safe transportation and tracking. |
ThinkShield security tools for ThinkPad computers, Lenovo has a key role to play. It includes a whole range of protective equipment, from the simplest to the most advanced:
| Security technology | What is she doing |
| ThinkShutter | Mechanical blind on the camera protects privacy from prying eyes. |
| FIDO certification | Provides simplified and secure authentication for login and secure payments. |
| Intel Multi-factor Authentication | PIN codes, biometric data, keys and tokens of security, as well as associated certificates are encrypted and stored in a place that is reliably protected from standard hacking methods. |
| Smart USB Protection Technology | Blocks data transfer via USB ports. |
| Secure docking station | Physical locking of the docking station allows you to prevent theft. |
| Fingerprint scanner Match-on-chip | Keeping fingerprint scans in secure storage on the chip provides additional biometric data protection against intruders. |
| Absolute | Provides IT administrators with two-way communication with devices that allow them to remotely assess risks, prevent security incidents and respond to them. |
| Buffer zone | Using virtualization technologies to isolate cyber attacks on the endpoint or on the network (sandboxing). |
| "Leave the hard drive in your service" | Allows customers to save their hard disk / files after replacement under warranty. |
| Winmagic | Data protection, ensuring compliance with regulatory requirements, optimization of work, support for unified encryption throughout the enterprise. |
| Lenovo Unified Workspace | Gives IT professionals the ability to deliver the right applications and documents to the right user on any device. |
| MobileIron | Gives IT administrators the ability to manage devices of any form factor from any installed OS. |
| Online Backup (OLDB) | Allows businesses to quickly and securely store confidential information automatically in the cloud. |
| USB secure hard drive | Fully encrypted external storage device for access to which requires a numeric password. |
| Lenovo WiFi Security | Blocking the display of user data in unreliable networks. |
| ThinkPad PrivacyGuard | Enabling protection of the screen protection by pressing a button, notification when an intruder is detected who is trying to access information on the screen. |
For example, the Lenovo ThinkShutter camera shutter allows the user to decide for himself whether someone will see it. There are thousands of videos online where the hero (or heroine) doesn’t even know that the laptop’s camera is recording. Now, so that this does not happen, you do not need to stick the cameras on laptops with tape. There is a more elegant solution to protect your privacy. You need to call via Skype - open the curtain. I want to be "invisible" - close, so as not to become a "YouTube hero". The solution is not new, but effective and convenient.

All systems with ThinkShield support FIDO — a standard for secure authentication offered by Microsoft Hello Windows, as well as Intel Authenticate with multi-factor authentication. A high level of integration with Intel Authenticate (up to seven factors) guarantees a higher degree of security and flexibility than solutions that provide fewer authentication methods.
As a founding member of FIDO , Lenovo offers FIDO certified authentication tools. This certification means that you use a secure way to register in the cloud and protect transactions using fingerprint verification. This uses encryption using public keys that remain on the device: passwords are no longer sent to database servers.
Another important point: sometimes it is necessary to disconnect the USB ports on a computer or laptop in order to limit the connection of flash drives, hard drives and other USB devices. Disabling USB ports will help prevent drives from being connected, which could potentially be used to steal sensitive information or cause a computer to become infected with a virus and spread malicious software over a local network.
BIOS-based Smart USB protection allows IT professionals to configure USB ports so that PCs respond only to keyboards and pointing devices, ensuring the safety of employees' computers. Thus, the USB ports on the PC can be blocked so that users cannot pick up malware or download data from the device.
Another source of threats is wireless networks. Sometimes connecting to a free-access wireless network can lead to negative consequences. You risk opening access to personal information, location and files. By connecting to a free Wi-Fi network, you often put your personal data "on display". , , .
, , SMS, -. « » .
Lenovo WiFi Security , . .
, ? Buffer Zone , . ThinkShield Buffer Zone — , , , .
MobileIron. Lenovo Endpoint Management MobileIron .
MobileIron . . , , , .
Lenovo , - , , , .
Absolute Persistence , , .
, ThinkShield .
, , . , «» . , .
ThinkShield Lenovo , - ThinkPad. , .

, , , Lenovo — .
, , . , . Lenovo ThinkPad ThinkShield , .
BIOS . Lenovo BIOS , .
, ThinkShield Lenovo, , , . , , – , . , .
, , , . , . , - .
Source: https://habr.com/ru/post/445184/
All Articles