Extract the master password from the locked password manager SafeInCloud
After reading this article, I wanted to study another password manager for similar vulnerabilities.
In the comments to the article, the user Dark_Angel asked:

The study was conducted on the free Windows version of SafeInCloud v.19.0.2
When I first met the product, he made a very good impression on me.
However, further research revealed exactly the same vulnerability.
')
Unlike 1Password, SafeInCloud stores all your passwords in the clear even in the locked state (after the first unlock).
To obtain a password from the database, simply read the application memory. Obfuscation of data is completely absent! The master password (and all other passwords and records) is never overwritten after the first successful unlock of the database, even if the user locks it.
Your passwords may leak in the following cases:
+ Sending a bug report in any software. Very often, developers make memory dumps of all applications for debugging purposes.
+ If you use a computer, not only you.
+ When gaining physical access to a computer intruders.
+ When launching malware.
+ Anything else ...
The Windows application is written in .net, which greatly simplifies the analysis of the source code.

The application is written on .net
After successful decryption of the database (XDatabase), the decrypted database and master password are saved as class fields in the Singleton instanc of the DatabaseModel class.
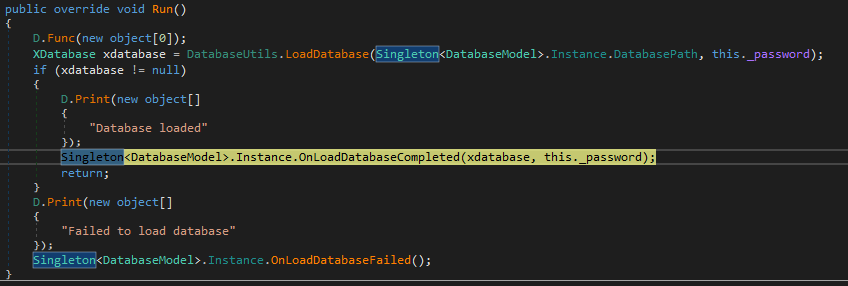
Setting fields with database and master password from it
All records and passwords are stored in memory in clear text even after the application is locked by the user. Master password is in clear view next.
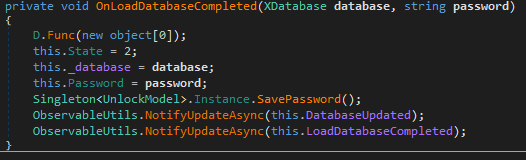
The password is stored in the Password property, _database is the field of the XDatabase class containing the decrypted database.
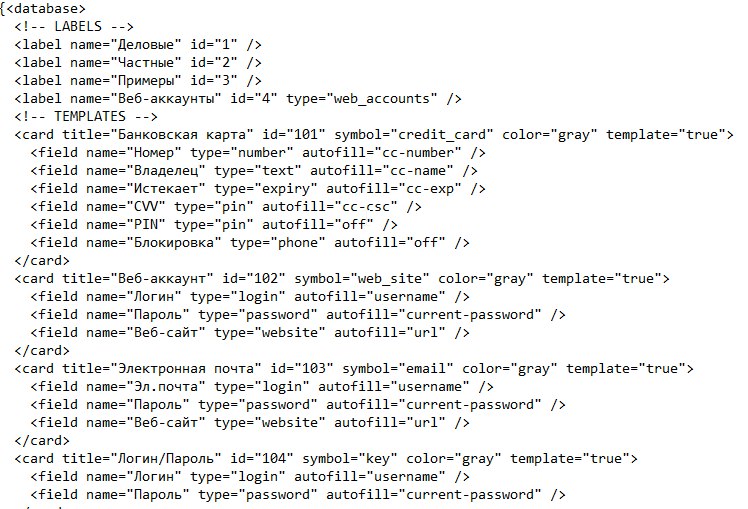
Database in XML format.
When you unlock again, the application performs an elementary check:
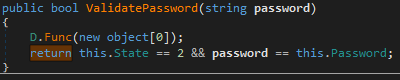
If the password entered by the user coincides with the stored in memory - unlocking is completed.
A simple utility SafeInCloudExtractor was written to automate the extraction of the master password.
The utility performs the extraction of the master password and the local path to the database file.
And which password manager do you use? Write in the comments!
In the comments to the article, the user Dark_Angel asked:
And what about SafeInCloud?

The study was conducted on the free Windows version of SafeInCloud v.19.0.2
When I first met the product, he made a very good impression on me.
However, further research revealed exactly the same vulnerability.
')
Unlike 1Password, SafeInCloud stores all your passwords in the clear even in the locked state (after the first unlock).
To obtain a password from the database, simply read the application memory. Obfuscation of data is completely absent! The master password (and all other passwords and records) is never overwritten after the first successful unlock of the database, even if the user locks it.
Your passwords may leak in the following cases:
+ Sending a bug report in any software. Very often, developers make memory dumps of all applications for debugging purposes.
+ If you use a computer, not only you.
+ When gaining physical access to a computer intruders.
+ When launching malware.
+ Anything else ...
The Windows application is written in .net, which greatly simplifies the analysis of the source code.

The application is written on .net
After successful decryption of the database (XDatabase), the decrypted database and master password are saved as class fields in the Singleton instanc of the DatabaseModel class.

Setting fields with database and master password from it
All records and passwords are stored in memory in clear text even after the application is locked by the user. Master password is in clear view next.

The password is stored in the Password property, _database is the field of the XDatabase class containing the decrypted database.

Database in XML format.
When you unlock again, the application performs an elementary check:

If the password entered by the user coincides with the stored in memory - unlocking is completed.
A simple utility SafeInCloudExtractor was written to automate the extraction of the master password.
The utility performs the extraction of the master password and the local path to the database file.
And which password manager do you use? Write in the comments!
Source: https://habr.com/ru/post/444904/
All Articles