Reverse engineering applications after obfuscation
Introduction
This publication aims to explore some of the techniques of reverse engineering. All materials are presented for informational purposes only and are not intended to be used for mercenary purposes.
Subject of study
As an example, we will study the code Atomineer Pro Documentation (hereinafter referred to as APD). This is a Visual Studio plugin designed to automatically generate comments in source codes. First, install this plugin and check its work. The free version has a trial period and a number of restrictions of use during this time. So when you add comments to the file, the user is notified that during the day only 10 files can be processed
Post 1

When you try to process the entire project, the utility displays a dialog warning that this command is not available.
Post 2

Let's get started
To begin with, we will look into the directory of the installed extension and find only one dynamic library there. We need it. The first thing we do is load it into the dotPeek decompiler from JetBrains.
')
dotPeek

As you can see in the screenshot, the library was scanned with an obfuscator, the variables and methods are renamed and have names like a, b, c, d ... this is what we need. We were looking for exactly that. Let's see what can be done.
Part 1
The first thing that comes to mind is to find the line, but since the search functionality is not in dotPeek, let's go the other way. We decompile the library with regular ildasm.exe from the Microsoft SDKs. At the output we get only one text file. In it we will look for the text of the message “ Trial Mode. Please note that your ... "
text file

Found a method
.method family hidebysig static bool e () cil managedWhich belongs to the CmdDocThisScope class. Now go back to dotPeek.
Spoiler header

So what we have. We found a method that displays an APD triality message and, depending on the condition, returns true or false. Find all the places from which this method is called.
call search

There were only 2 places to call and these are the CmdDocThisFile :: c and CmdDocThisScope :: c methods.
found

By the name of the classes and the constructors code, it is obvious that the classes are responsible for the menu items, and the virtuality of the “c” method indicates that this is the event handler for the selection of the corresponding menu item by the user (This information will be useful later). It is easy to guess that if the method returns true, the command will be executed though it will show a dialog with a warning.
At the beginning of the CmdDocThisScope :: e method, the variable f is incremented. Open the “IL View” window and find the command code:
IL View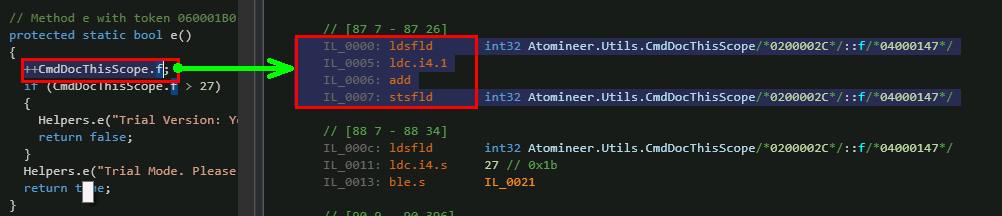

Wikipedia has an article describing these instructions .
Next, we will find this method in the APD library file. We will do this using the IDA tool. In the window with functions, we will find our method, and see the already familiar code.
IDA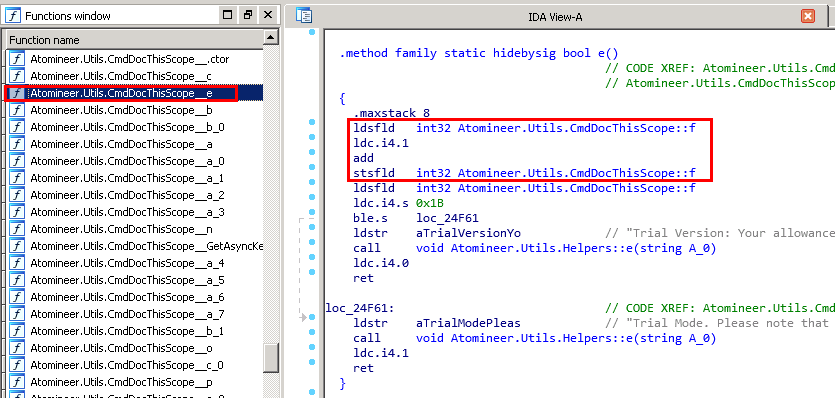

Select the ldsfld instruction and find its binary representation in the Hex View window
Hex view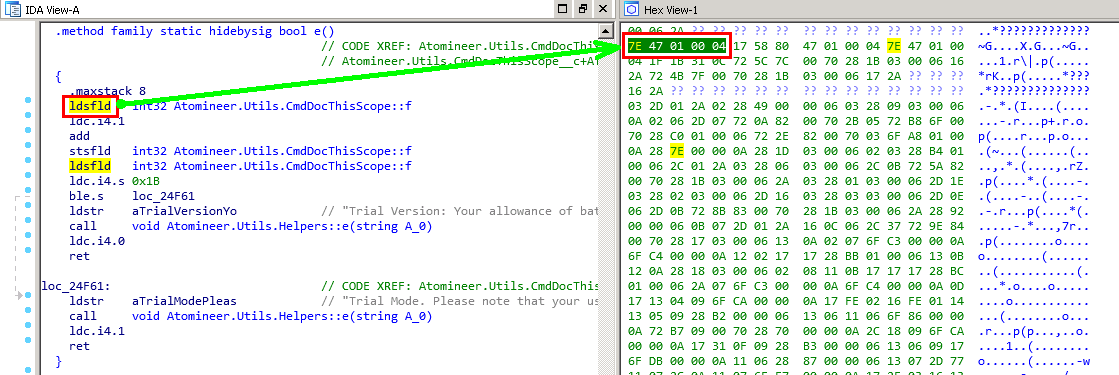

The team description confirms that we have found the right place.
Wiki

Further analysis of the code of this method and subsequent steps are beyond the scope of this article.
Part 2
Now, as already experienced researchers, we find the call of the dialogue with the message “ The document all in the project. ” This is the CmdDocThisProject :: c method
CmdDocThisProject :: c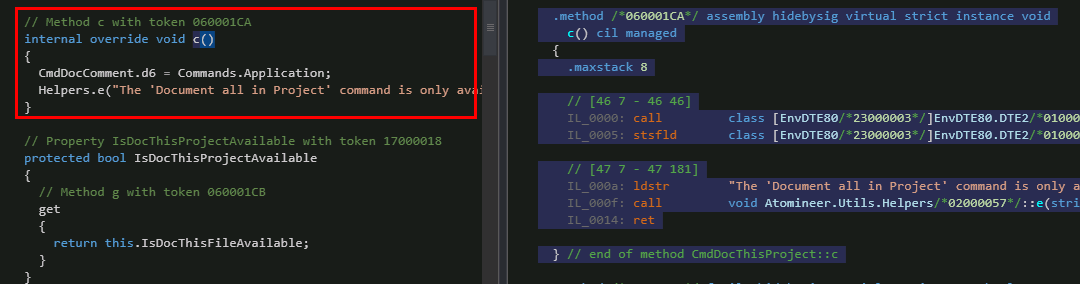

The CmdDocThisProject class is responsible for the “Process Project” command, the “c” method is virtual. And it contains only one thing - it is a dialogue call with a message. Neither conditions nor checks. Searching the source code leads us to the CmdDocThisProject :: i method, which has what we expect in CmdDocThisProject :: c. Now in IDA we can easily find the necessary methods and be able to learn the CIL instructions.
Conclusion
It remains to say that the article intentionally left white spots for their own study.
Source: https://habr.com/ru/post/444886/
All Articles