Data leakage (which could have occurred, but did not occur) from the telemedicine company
Just a couple of days ago, I wrote on Habré about how the Russian medical online service DOC + managed to leave in the public domain a database with detailed access logs from which it was possible to get data from patients and service staff. And here is a new incident, with another Russian service providing patients with online consultations of doctors - “Doctor is near” (www.drclinics.ru).
I’ll write right away that, due to the adequacy of the Doctor beside employees, the vulnerability was quickly (2 hours from the notice at night!) Eliminated and most likely the leakage of personal and medical data did not happen. Unlike the DOC + incident, where I know for sure that at least one json file with 3.5 GB data got into the “open world”, and the official position looks like this: “ In the public domain, a small amount of data was temporarily which cannot lead to negative consequences for employees and users of the DOC + service. ".

I, as the owner of the Leaked Telegram channel, were contacted by an anonymous subscriber and reported a potential vulnerability on www.drclinics.ru.
The essence of the vulnerability was that, knowing the URL and being in the system under your account, you could view data from other patients.
To register a new account in the Doctor beside system, in fact, only a mobile phone number is required, which receives confirming SMS, so no one could have problems accessing the personal account.
After the user logged into his personal account, he could immediately change the URL in the address bar of his browser to view reports containing patient personal data and even medical diagnoses.
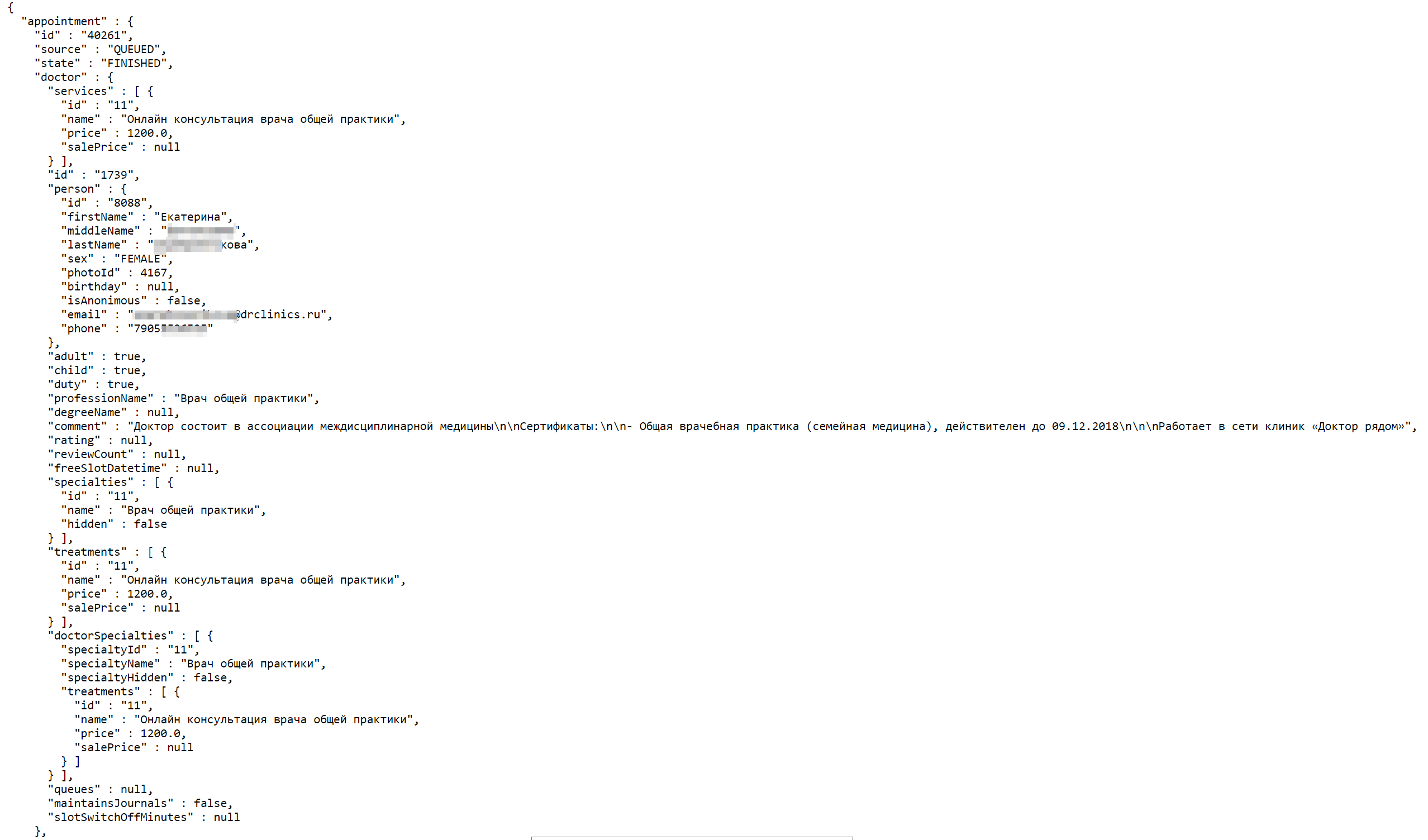
The main problem was that the service uses the end-to-end numbering of reports and from these numbers already forms a URL:
https://[ ]/…/…/40261/…
Therefore, it was enough to set the minimum allowable number (7911) and maximum (42926 - at the moment of the presence of the vulnerability) to calculate the total number (35015) of reports in the system and even (if there is malicious intent) to extort them all with a simple script.

Among the data available for viewing were: doctor’s and patient’s full names, doctor’s and patient’s birth dates, doctor’s and patient’s telephones, doctor’s and patient’s gender, doctor’s and patient’s e-mail addresses, doctor’s specialization, consultation date, consultation cost, and in some cases even a diagnosis ( as a comment to the report).
This vulnerability is in fact very similar to the one that was discovered in December 2017 on the server of the microfinance organization “Zaymograd”. Then, through the search, it was possible to obtain 36763 contracts containing full passport data of the organization’s clients.
As I indicated from the very beginning, the Doctor beside employees showed real professionalism and despite the fact that I reported them about the vulnerability at 23:00 (Moscow time), access to the personal account was immediately closed for everyone, and by 1:00 ( Moscow time) this vulnerability was eliminated.
I can not help but kick again the PR department of the same DOC + (LLC "New Medicine"). Declaring “ in the public domain temporarily turned out to be a small amount of data ”, they overlook the fact that we have “objective control” data, namely the search engine Shodan. As correctly noted in the comments to that article, according to Shodan, the date of the first fixing of the open ClickHouse server on the IP address is DOC +: 02/15/2019 03:08:00, the last fix date: 03/17/2019 09:52:00. Database size is about 40 GB.
And there were a total of 15 fixations:
15.02.2019 03:08:00 16.02.2019 07:29:00 24.02.2019 02:03:00 24.02.2019 02:50:00 25.02.2019 20:39:00 27.02.2019 07:37:00 02.03.2019 14:08:00 06.03.2019 22:30:00 08.03.2019 00:23:00 08.03.2019 14:07:00 09.03.2019 05:27:00 09.03.2019 22:08:00 13.03.2019 03:58:00 15.03.2019 08:45:00 17.03.2019 09:52:00 From the statement it turns out that temporarily it is just over a month, and a small amount of data is about 40 gigabytes. Well I do not know...
But back to the "Doctor is near."
At the moment, my professional paranoia is haunted only by one remaining minor problem - by the server's response, you can find out the number of reports in the system. When you try to get a report using a URL that you don’t have access to (but the report itself is available), the server returns ACCESS_DENIED , and when you try to get a report that does not exist, NOT_FOUND is returned. By monitoring the increase in the number of reports in the system over time (once a week, month, etc.), it is possible to estimate the workload of the service and the volume of services provided. This of course does not violate the personal data of patients and doctors, but may be a violation of the company's commercial secrets.
')
Source: https://habr.com/ru/post/444590/
All Articles