Palo Alto Networks NGFW Security Policy Optimizer
How to evaluate the effectiveness of tuning NGFW
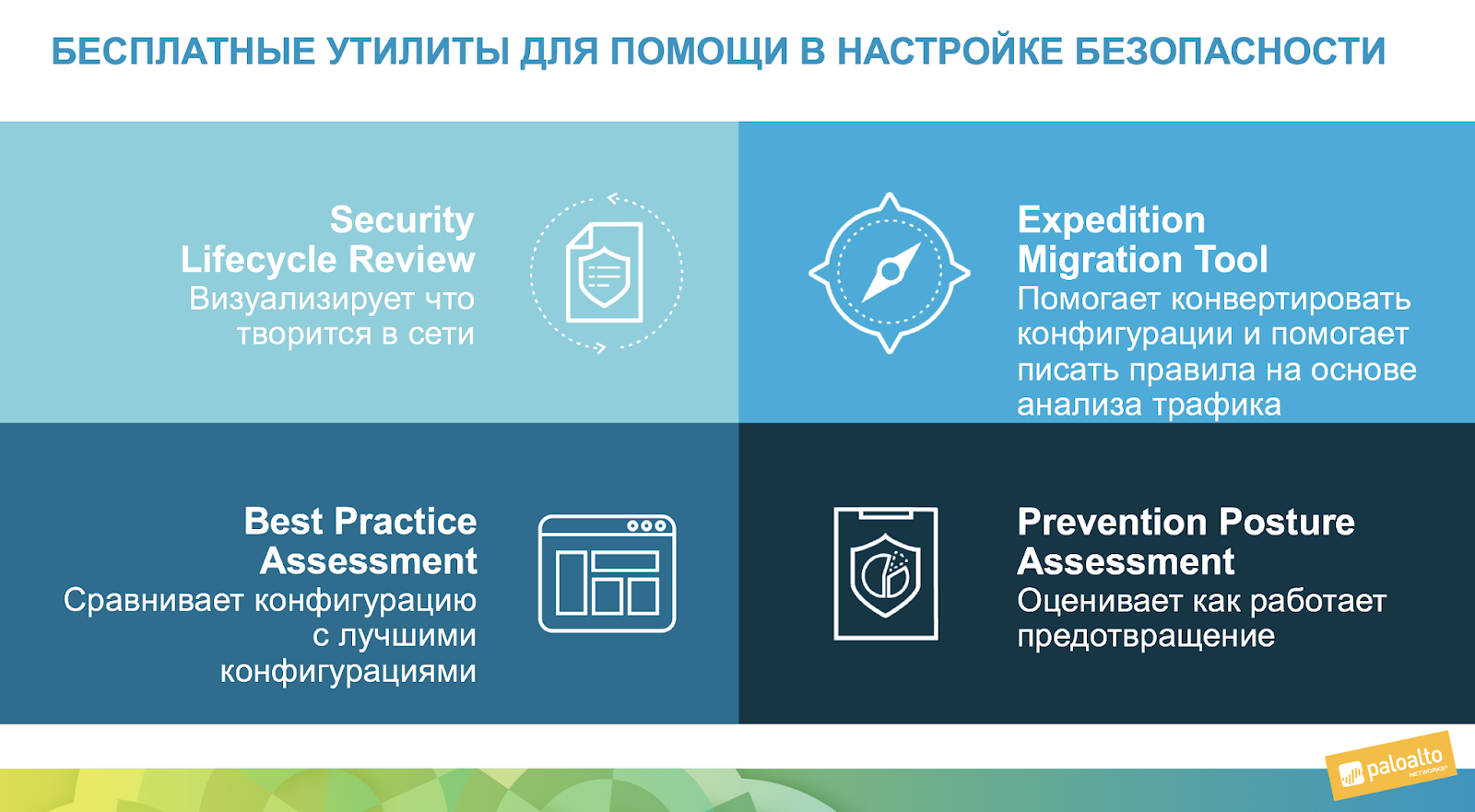
The most common task is to check how efficiently your firewall is configured. To do this, there are free utilities and services from companies that are engaged in NGFW.
For example, it can be seen below that Palo Alto Networks has the opportunity directly from the support portal to launch an analysis of firewall statistics — an SLR report or a best-practice analysis — a BPA report. These are free online utilities that you can use without installing anything.
')
Content
Expedition (Migration Tool)
Policy optimizer
Zero trust
Click on Unused
Click on Unused App
Click No Apps Specified
But what about machine learning
UTD
Expedition (Migration Tool)
A more complicated way to check your settings is to download the free Expedition utility (formerly the Migration Tool). It is downloaded as a Virtual Appliance under VMware, with no settings required - you need to download an image and deploy it under the VMware hypervisor, launch it and access the web interface. This utility requires a separate story, only the course on it takes 5 days, so many functions are there now, including Machine Learning and migration of different policy configurations, NAT and objects for different Firewall vendors. About Machine Learning, I will write more below.
Policy optimizer
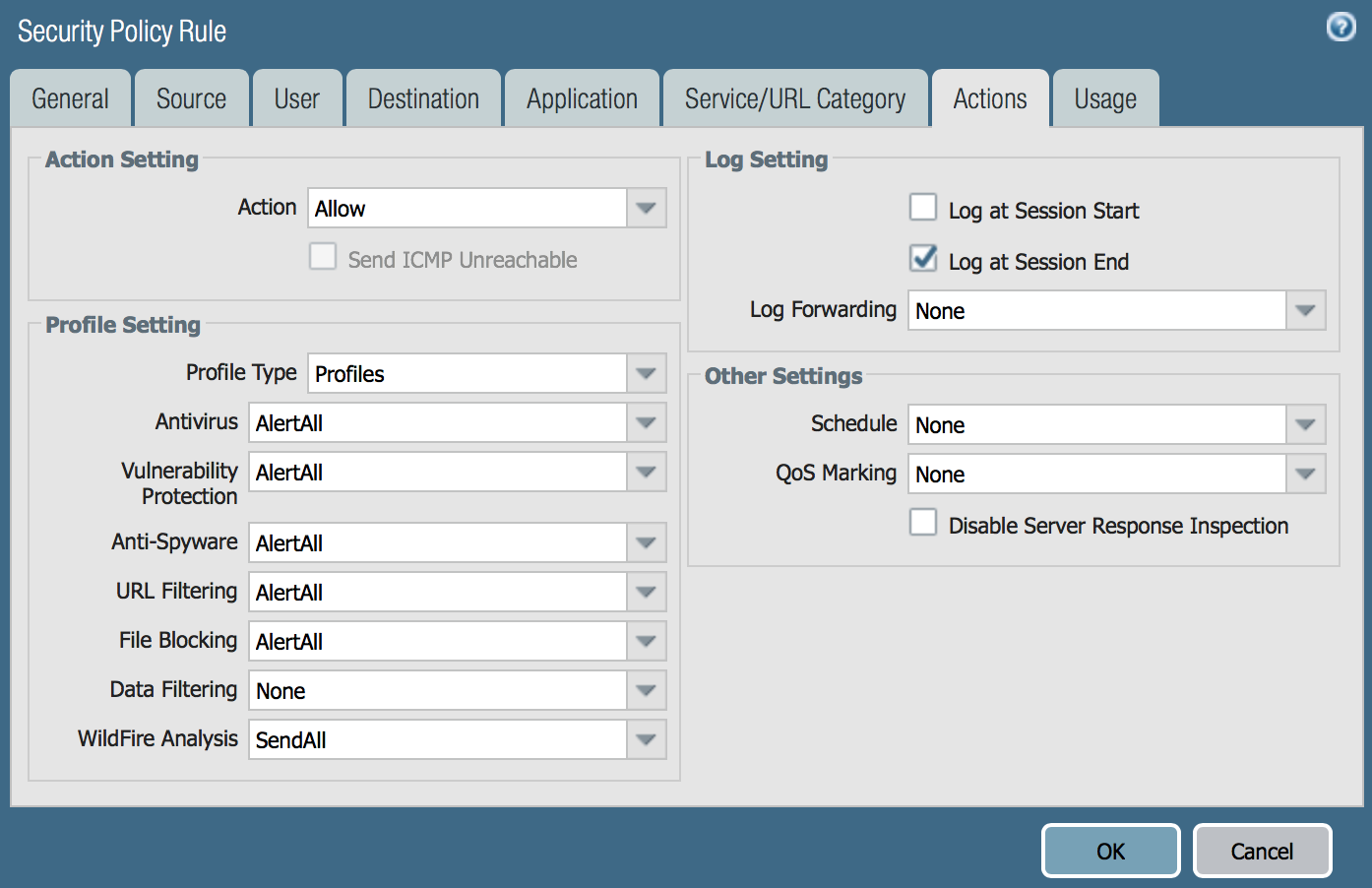
And the most convenient option (IMHO), about which, today I will tell you in more detail - the policy optimizer built into the Palo Alto Networks interface itself. To demonstrate it, I installed an internetwork screen at home and wrote a simple rule: permit any to any. In principle, I sometimes see such rules even in corporate networks. Naturally, I included all the NGFW security profiles, as seen in the screenshot:
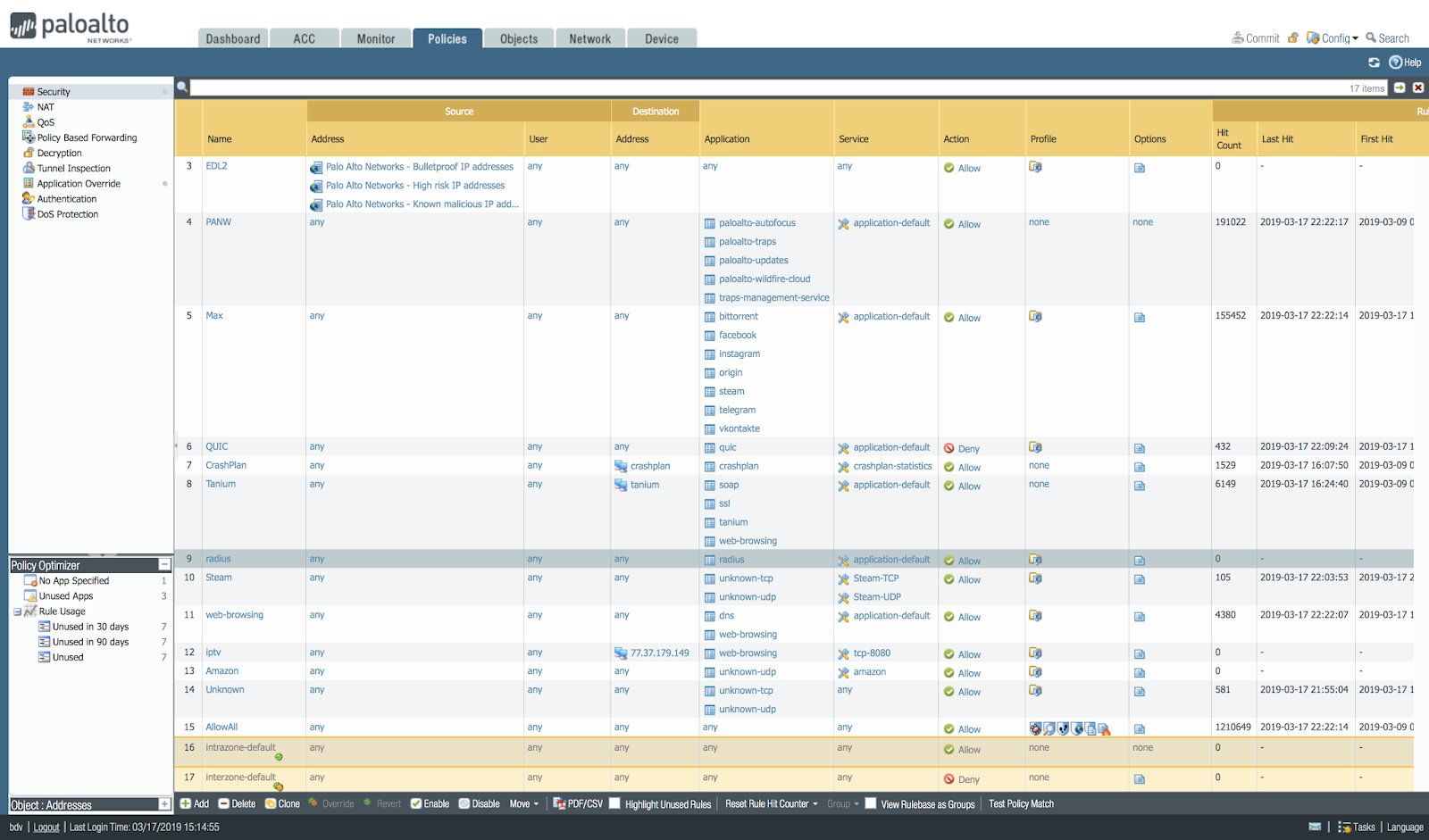
The screenshot below shows an example of my home unconfigured firewall, where almost all connections fall into the last rule: AllowAll, as seen in the statistics in the Hit Count column.
Zero trust
There is an approach to security called Zero Trust . What this means: we have to allow exactly the connections that they need and prohibit everything else to people within the network. That is, we need to add clear rules on applications, users, URL categories, file types; enable all IPS and antivirus signatures, enable sandbox, DNS protection, use IoC from the available Threat Intelligence databases. In general, the tasks when setting up a firewall are a decent amount.
By the way, the minimum set of required settings for Palo Alto Networks NGFW is described in one of the SANS documents: Palo Alto Networks Security Configuration Benchmark - I recommend starting with it. And of course there is a set of best practices for setting up a firewall at the manufacturing company: Best Practice .
So, I had a firewall at home for a week. Let's see what traffic in my network is:
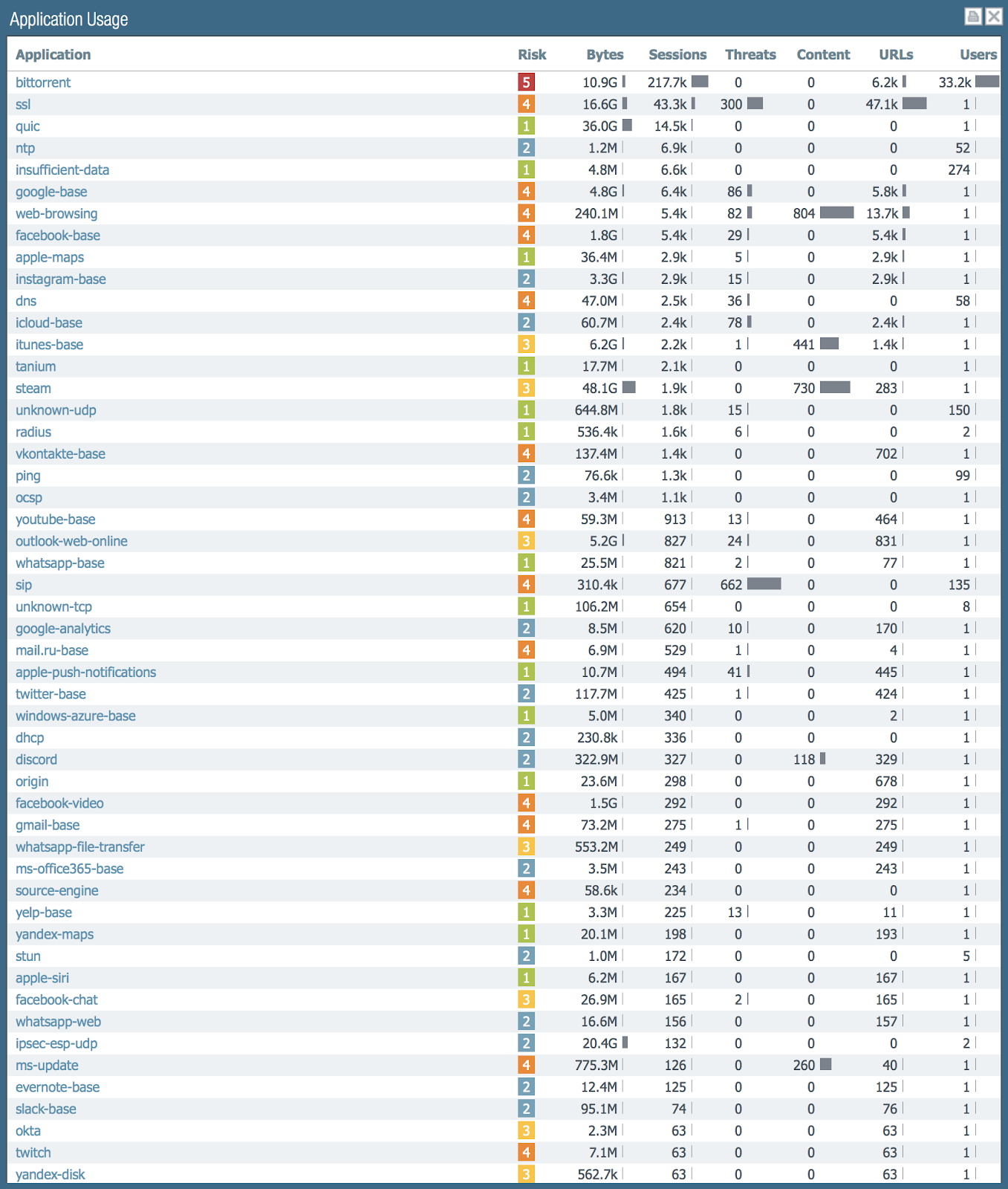
If you sort by the number of sessions, then bittorent creates them most, then comes SSL, then QUIC. This is a statistic for both incoming and outgoing traffic: there are a lot of external scans of my router. There are 150 different applications on my network.
So, all this was omitted by one rule. Now let's see what the Policy Optimizer says about this. If you looked above at the screenshot of the interface with the security rules, then at the bottom left you saw a small window, which hints to me that there are rules that can be optimized. Let's go there click.
What Policy Optimizer shows:
- What policies were not used at all, 30 days, 90 days. It helps to decide to remove them altogether.
- What applications were specified in the policies, but such applications were not detected in the traffic. This allows you to remove unnecessary applications in permissive rules.
- What politicians allowed everything, but there really were applications that it would be nice to indicate explicitly according to the Zero Trust methodology.
Click on Unused
To show how it works, I added a few rules and they have so far never missed a single package today. Here is a list of them:
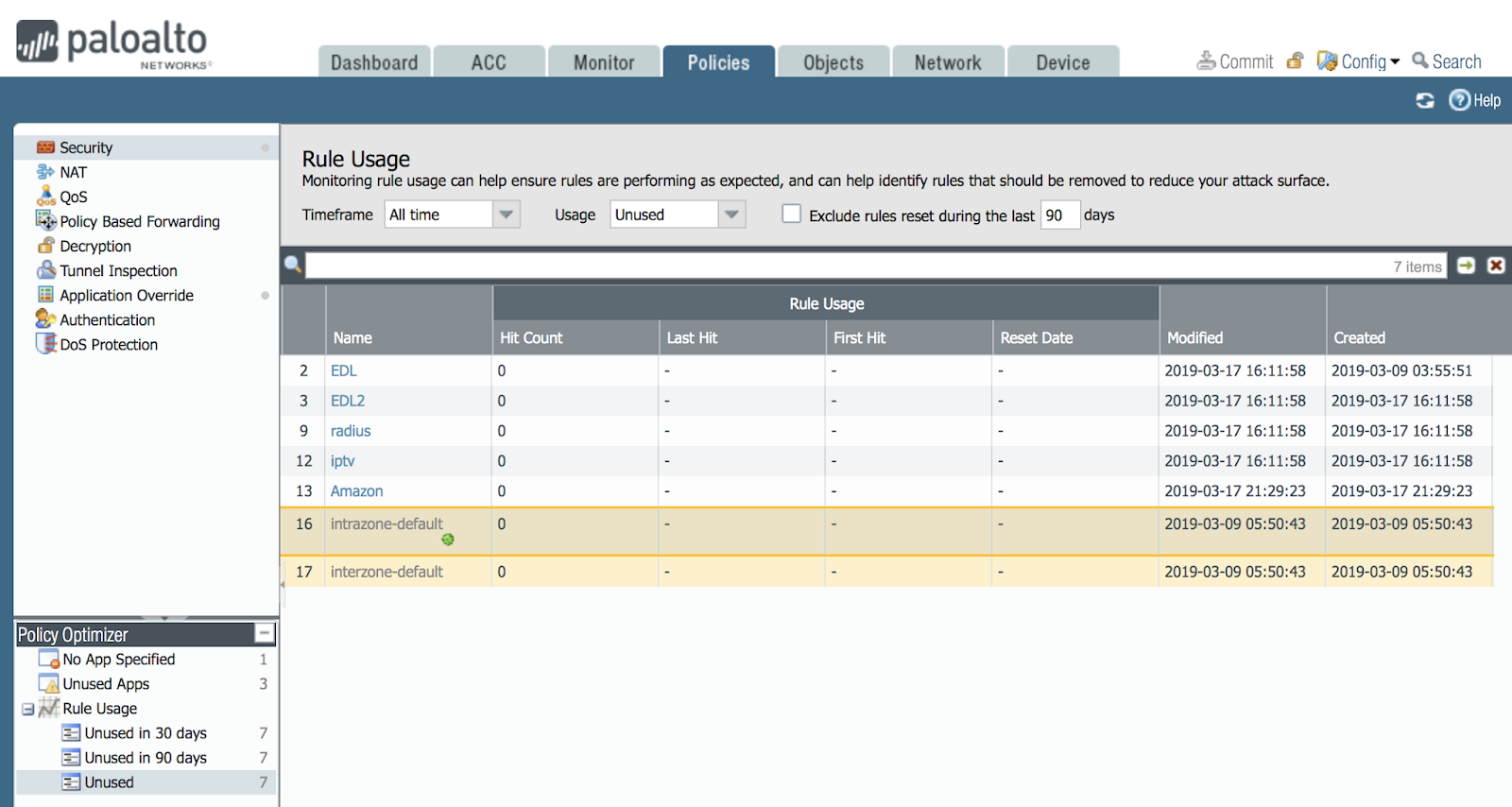
Perhaps over time there will be traffic and then they will disappear from this list. And if they are on this list for 90 days, then you can decide to delete these rules. After all, every rule makes it possible for a hacker.
There is a real problem in configuring the firewall: a new employee comes, looks at the firewall rules, if they have no comments and he does not know why this rule is created, whether it is really necessary, whether it can be removed: suddenly a person is on vacation and after 30 days traffic will go again from the service he needs. And just this function helps him to make a decision - no one uses - to delete!
Click on Unused App
We click on the Unused App in the optimizer and see that interesting information opens in the main window.
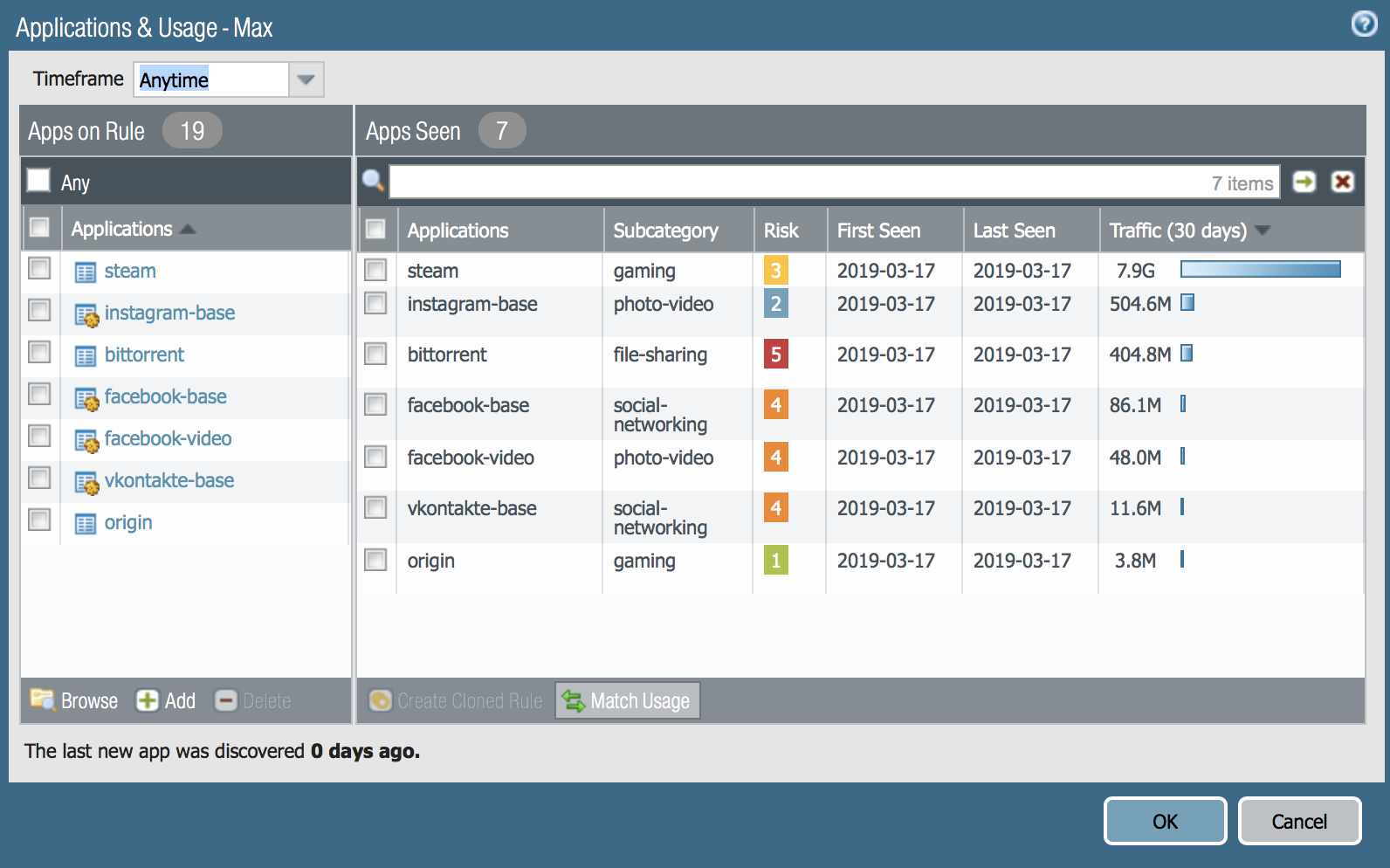
We see that there are three rules, where the number of allowed applications and the number of applications actually under this rule differ.
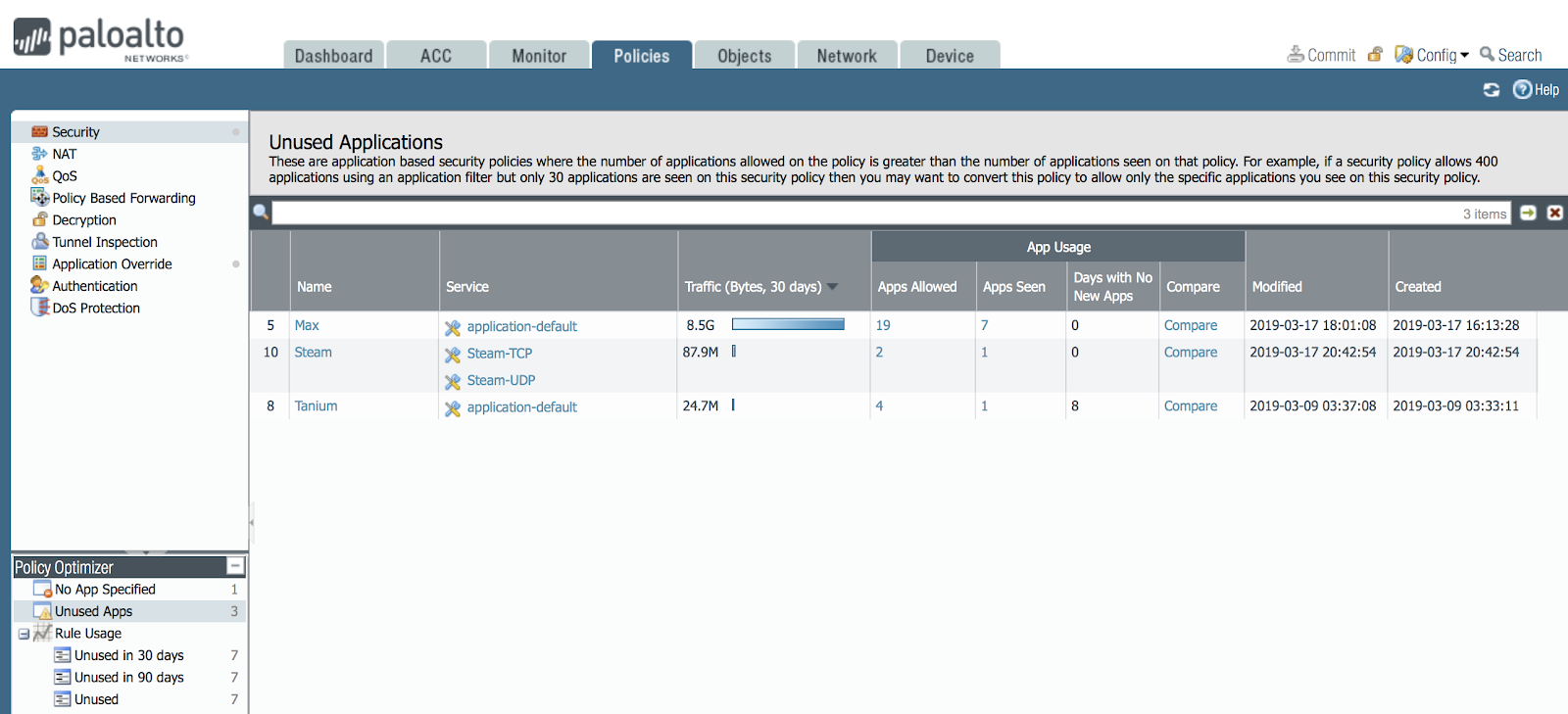
We can click and see the list of these applications and compare these lists.
For example, click on the Compare button for the Max.

Here you can see that facebook, instagram, telegram, vkontakte applications were enabled. But the actual traffic went only in terms of sub-applications. Here you need to understand that the facebook application contains several sub-applications.
The entire list of NGFW applications can be seen on the applipedia.paloaltonetworks.com portal and in the Firewall interface itself in the Objects-> Applications section and in the search type the application name: facebook, you’ll get the following result:
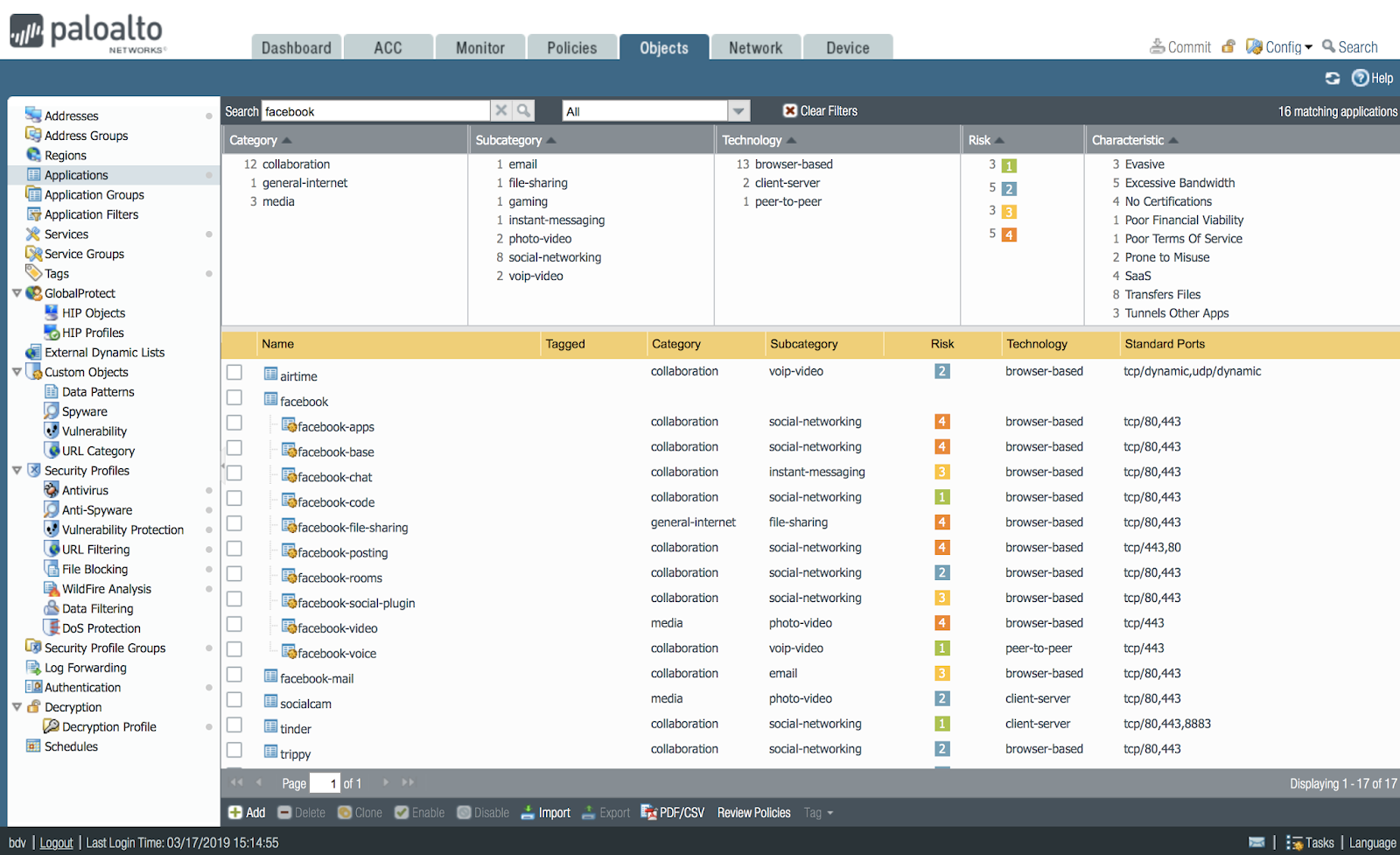
So, some of these sub-applications NGFW saw, and some did not. In fact, you can separately prohibit and allow various subfunctions of Facebook. For example, allow watching messages, but prohibit chat or file transfer. Accordingly, the Policy Optimizer talks about this and you can make a decision: not to allow all Facebook applications, but only the main ones.
So, we realized that the lists are different. You can make the rules allow exactly those applications that actually went over the network. To do this, you click the button MatchUsage. It turns out like this:
And also you can add applications that you consider necessary - the Add button in the left part of the window:
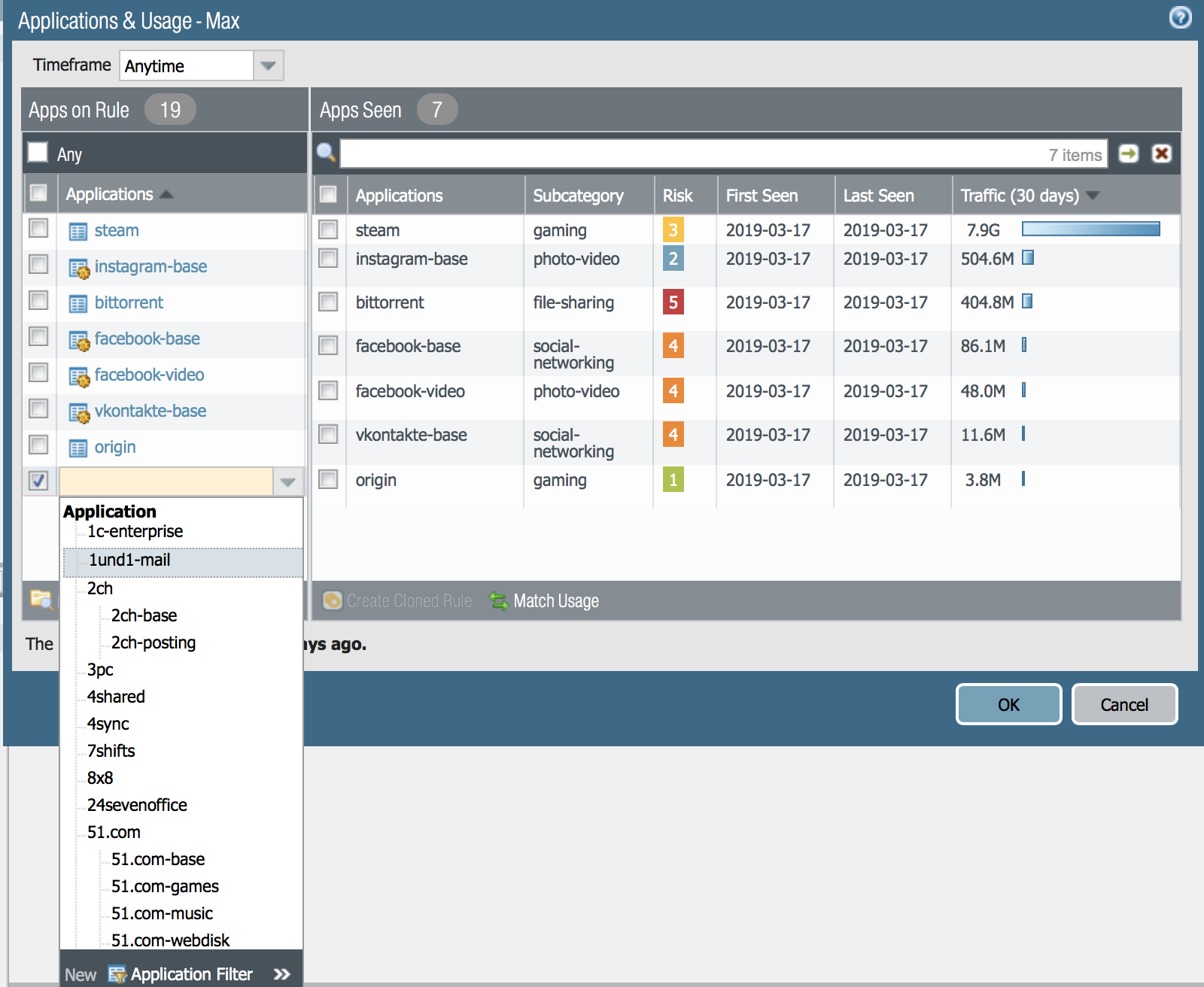
And then this rule can be applied and tested. Congratulations!
Click No Apps Specified
In this case, the important security window will open.
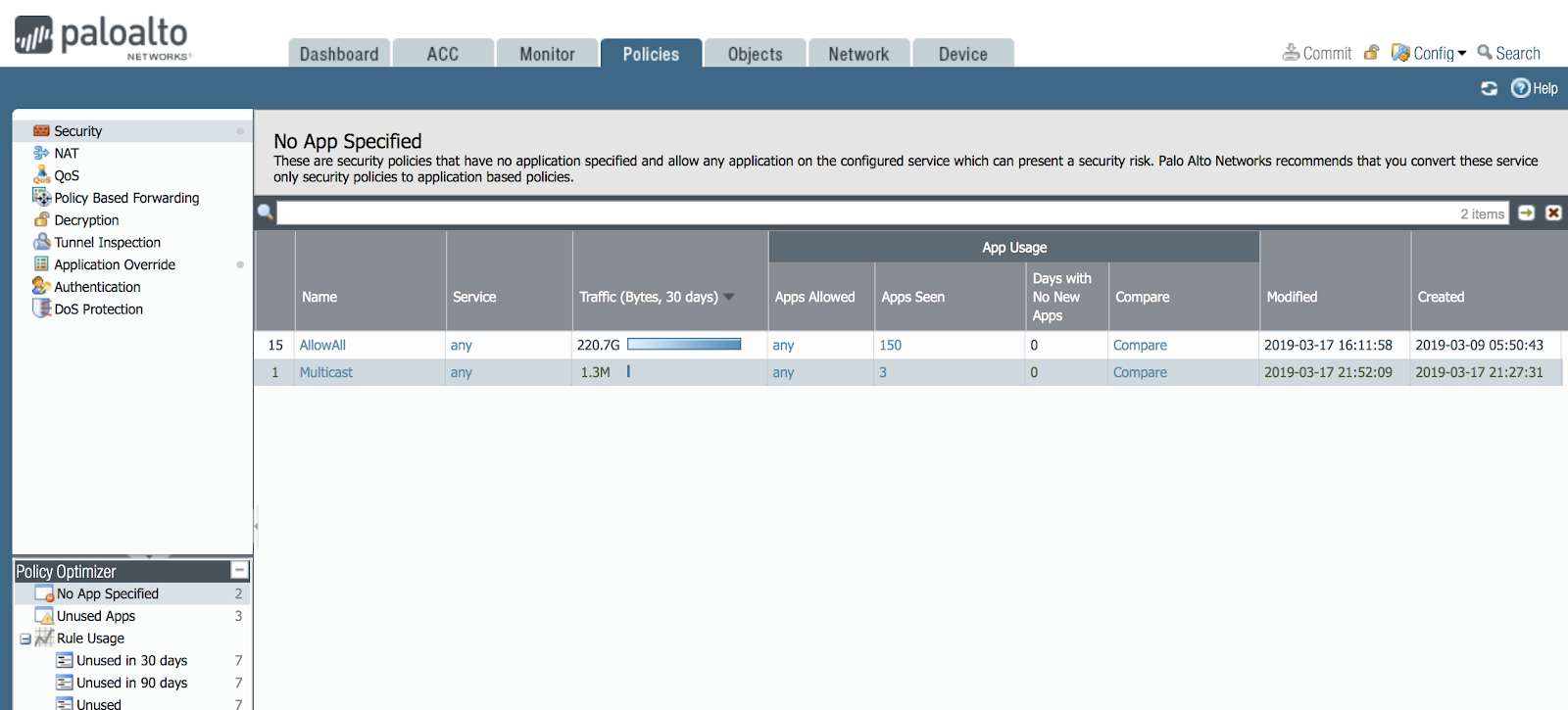
There are obviously no such rules where an application of the L7 level is not indicated, most likely there are a lot of them on your network. And in my network there is such a rule - let me remind you that I made it during the initial configuration, specifically to show how the Policy Optimizer works.
In the picture you can see that the AllowAll rule missed 220 gigabytes of traffic over the period from March 9 to March 17, which means that there are 150 different applications in my network. And this is not enough. Typically, a medium-sized corporate network has 200-300 different applications.So, one rule skips as many as 150 applications. As a rule, this means that the firewall is configured incorrectly, because usually in one rule 1-10 applications are skipped for different purposes. Let's see what these applications are: click the button
Compare:
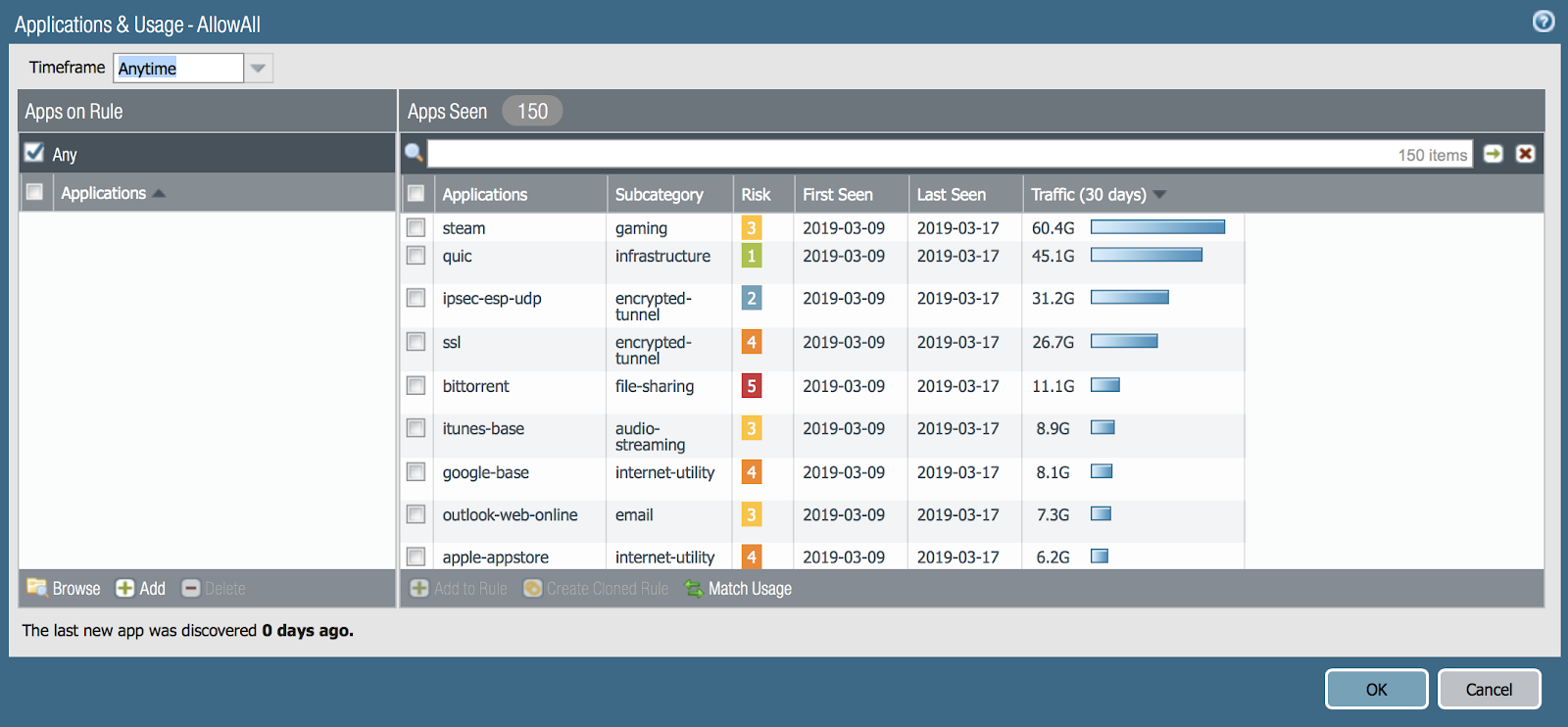
The most wonderful thing for the administrator in the Policy Optimizer function is the Match Usage button - you can create a rule with one click, where you will enter all 150 applications into the rule. Manually, it would be long enough. The number of tasks for the administrator to work even in my network of 10 devices is huge.
I have 150 different applications running at home that transmit gigabytes of traffic! And how much do you have?And what is happening in the network of 100 devices or 1000 or 10,000? I saw firewalls with 8000 rules and I am very glad that now administrators have such convenient automation tools.
Some of the applications that you saw and showed the L7 application analysis module in NGFW you will not need on the network, so you simply remove them from the list of allowing rules, or do the cloning of the rules with the Clone button (in the main interface) and in one application rule you allow, other applications will block as definitely not needed in your network. Such applications often become bittorent, steam, ultrasurf, tor, hidden tunnels such as tcp-over-dns and others.
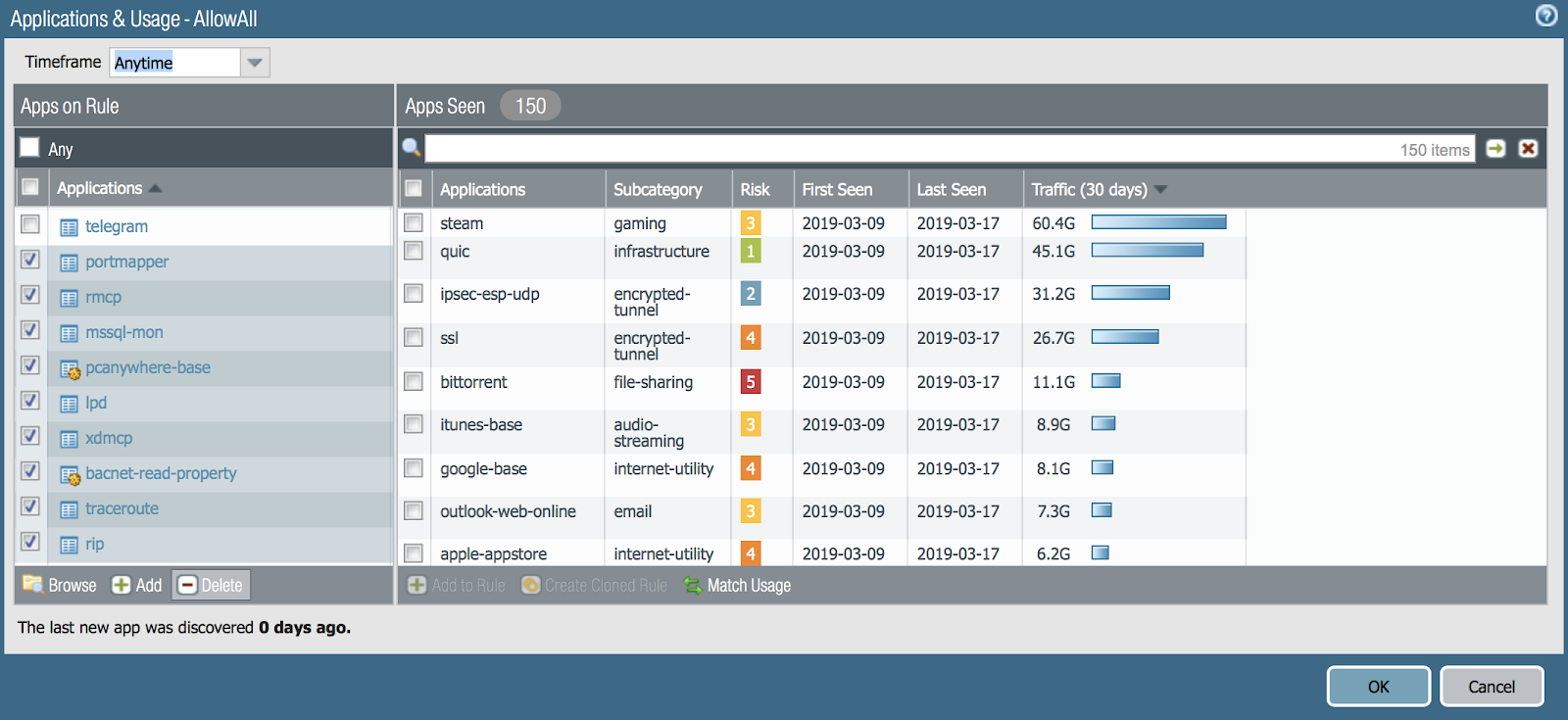
Well, click in another rule - what you see there:
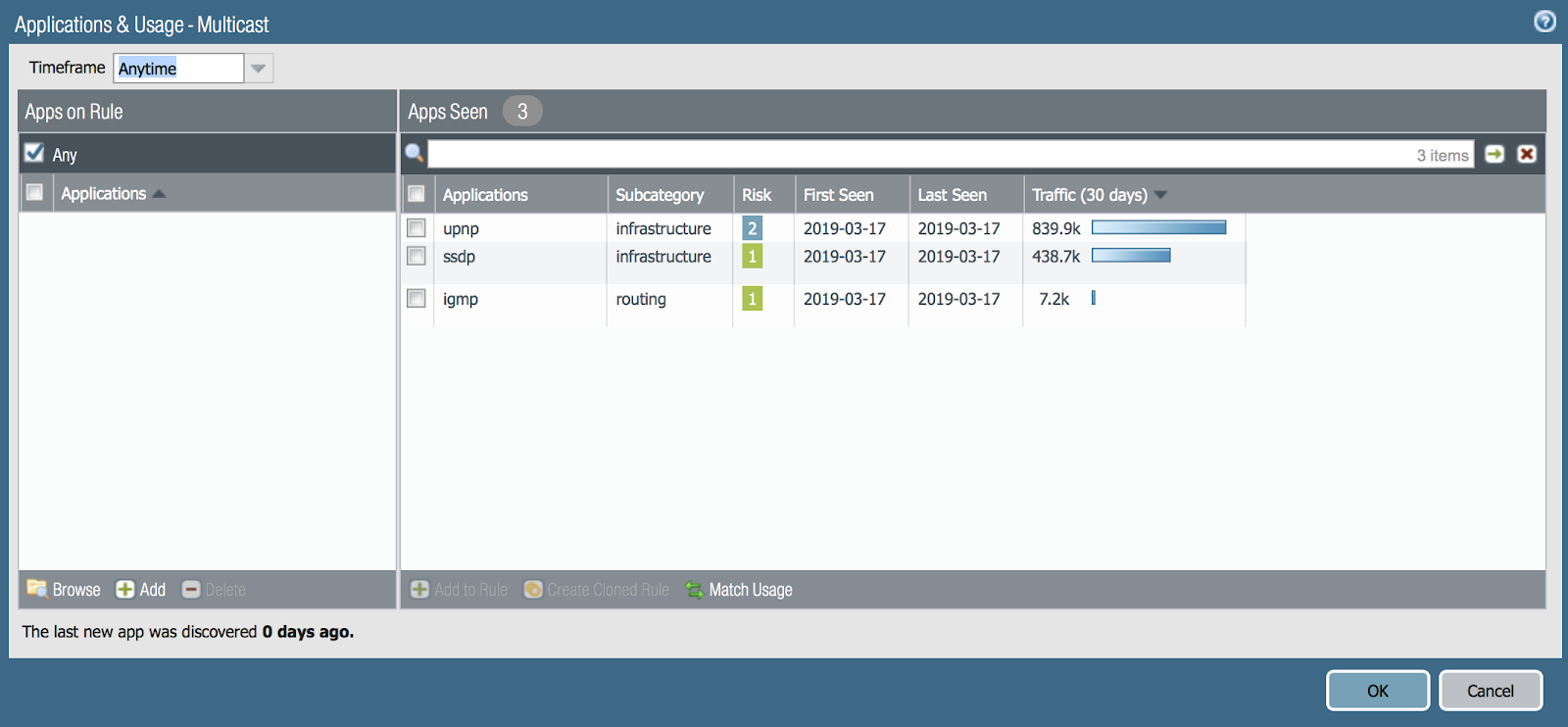
Yes, there are applications typical for multicast. We must allow them to view the video over the network. Click Match Usage. Fine! Thank you Policy Optimizer.
But what about machine learning
Now it is fashionable to talk about automation. What I described came out - it helps a lot. There is another opportunity that I have to talk about. This is the Machine Learning functionality built into the Expedition utility, which has already been mentioned above. In this utility, it is possible to transfer rules from your old firewall from another manufacturer. And it is also possible to analyze the existing traffic logs of Palo Alto Networks and suggest which rules to write. This is similar to the functionality of the Policy Optimizer, but in Expedition this is even more expanded and you are offered a list of ready-made rules — you just need to approve them.
To test this functionality there is a laboratory work - we call it a test drive. This test can be done by accessing the virtual firewalls that the staff of the Palo Alto Networks office in Moscow will launch at your request.
You can send the request to Russia@paloaltonetworks.com and write in the request: “I want to make a UTD via the Migration Process”.
In fact, the lab works called Unified Test Drive (UTD) are several options and they are all available remotely upon request.
Source: https://habr.com/ru/post/444582/
All Articles