New HTTPS Interception Detection Tools
As the use of HTTPS grows, there is a growing desire for outsiders to infiltrate secure traffic. A 2017 study by The Security Impact of HTTPS Interception has shown that this is becoming an increasingly common practice. An analysis of the traffic on the Firefox update servers showed that in some countries the percentage of introducing extraneous agents in HTTPS reaches 15%.
Since the study, the situation is unlikely to have improved. Now even the latest model of Sennheiser wireless headphones requires installing a root certificate in the system (with insecure parameters).
Most often, the protection is compromised by the antivirus or the corporate middlebox (see the list below), but it can be worse. In any case, it's best to know for sure when your HTTPS channel is not really end-to-end secure. Even when a third-party system intercepts traffic from the best intentions, it often does not support modern ciphers or does not validate certificates, thus reducing the overall protection of the connection. But intercept SSL-traffic can not only for good purposes, but also malicious, for example, for censorship at the state level.
')
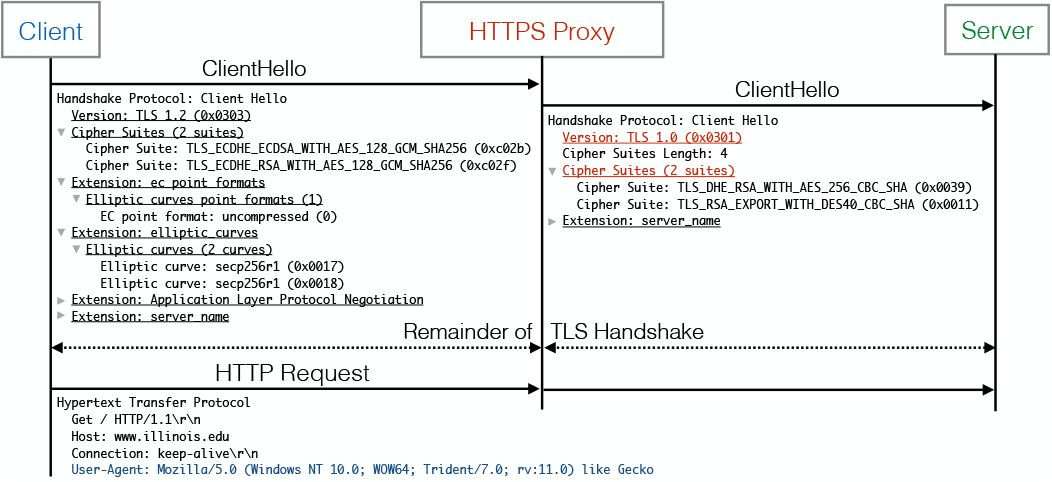
HTTPS monitoring programs work as transparent proxies that terminate the TLS session, inspect the content, and then establish a new session with the destination server. They use different versions of TLS libraries than popular browsers, which allows them to be detected on the server side due to the mismatch between the HTTP User-Agent and the TLS Client Hello of the real browser and proxy.
To begin with, we present some practical conclusions from a 2017 study in which Mozilla, Google, GlobalSign participated, as well as academic researchers from the University of Michigan, the University of Illinois at Urbana-Champaign and the University of California at Berkeley.
The practical harm of HTTPS interception is the degradation of encryption and the additional vulnerabilities of the transparent proxy. The authors of the study rated a number of popular middleboxes by these parameters. As we see, in 2017, almost half of them did not support modern cipher suites, and five registered serious vulnerabilities. Only 1 out of 12 was able to fully mirror all user cipher suites.
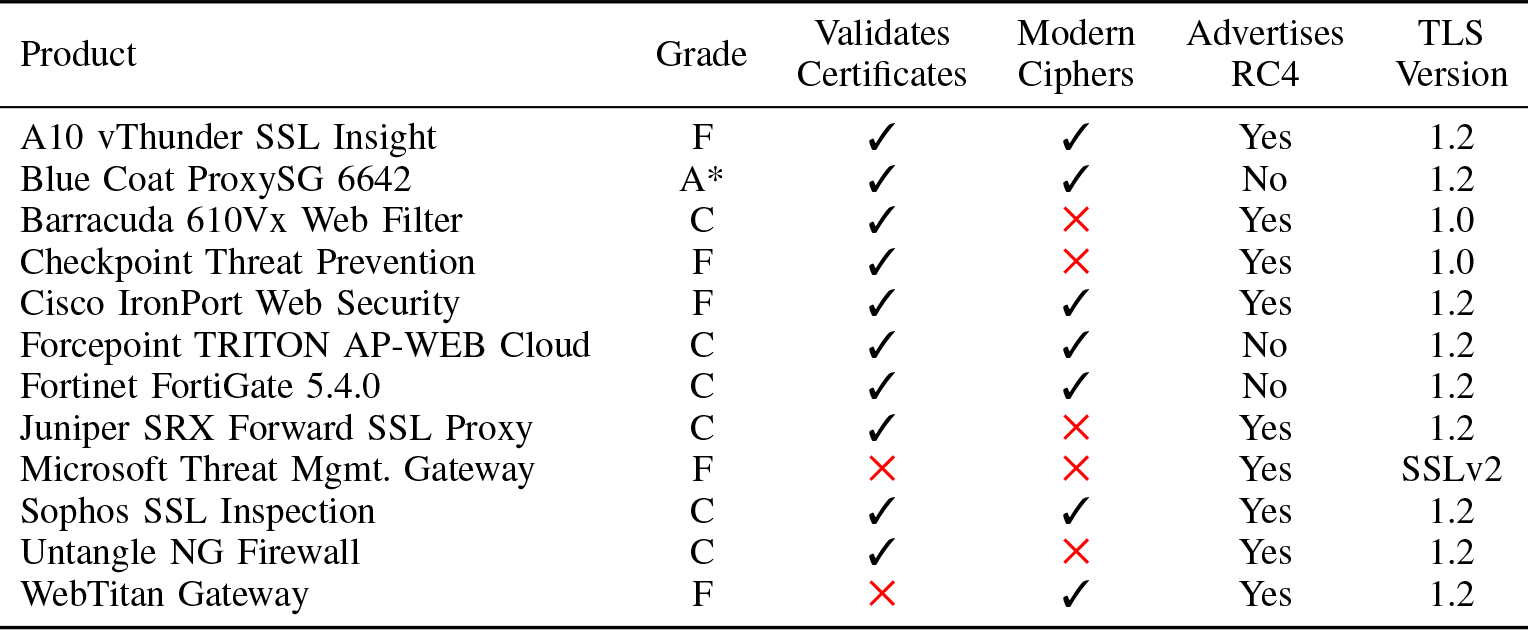
Antivirus activity on users' computers is also usually detected on the server side. The study showed that only two antiviruses completely mirror user ciphers; in other cases, encryption is degraded.
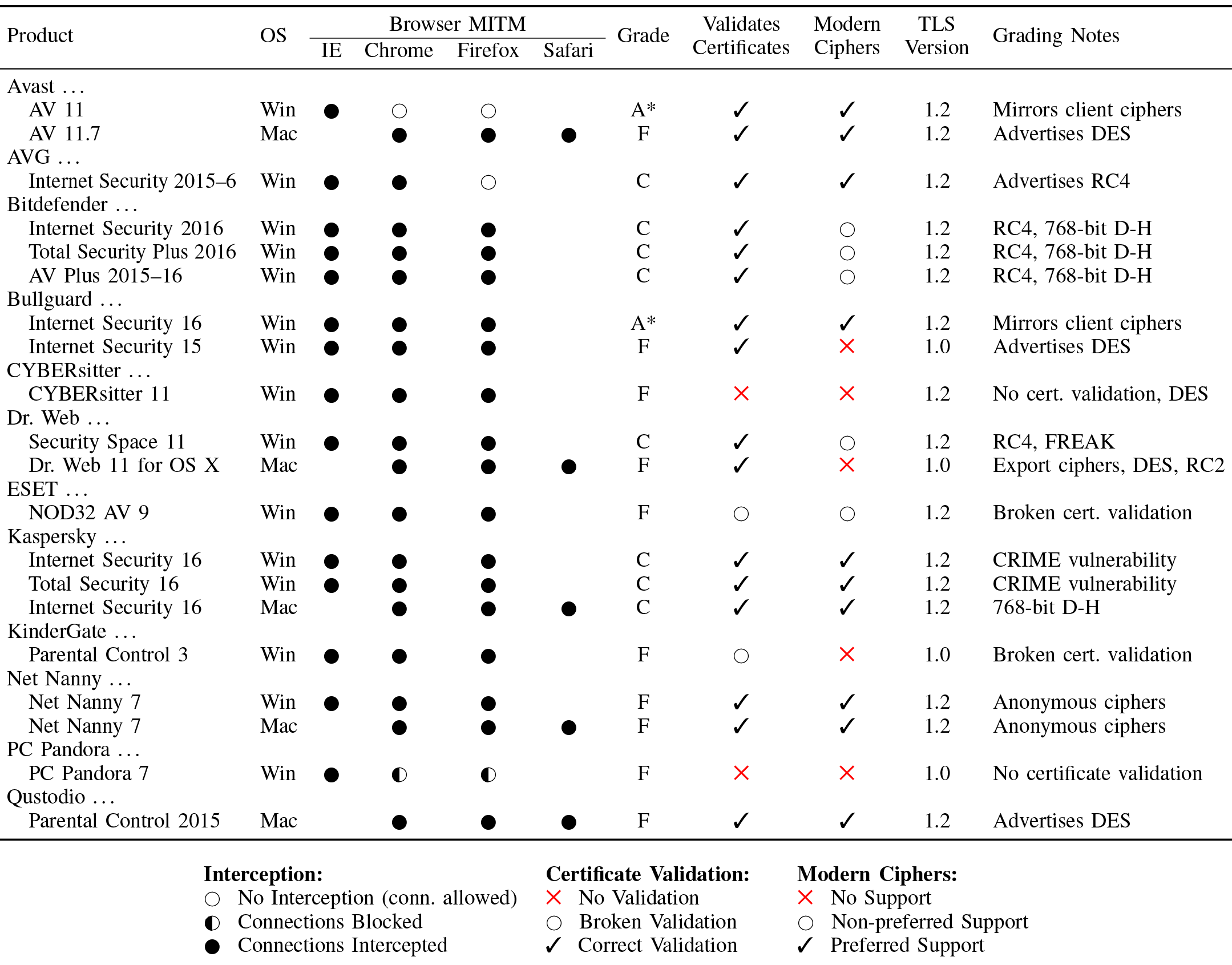
By protecting against some threats, antiviruses reduce encryption and add their own vulnerabilities. In general, installing third-party anti-virus often significantly impairs the overall security of the system. Some experts advise users to always remove third-party antiviruses from the system , because their invasive and poorly written code makes it difficult for browsers and other programs to ensure their own security.
Other transparent proxies can work on the path between the client and the server. To better detect these agents, Cloudflare recently released two new tools:
- MITMEngine , a free library for determining HTTPS interception.
- MALCOLM , dashboard for displaying HTTPS intercept metrics on the Cloudflare network.
The main interest is the library MITMEngine. Developers write that they took as an example the popular Caddy Server MITM Detection tool. It supports a set of popular browsers and recognizes HTTPS interception using specific fingerprints of TLS Client Hello and User Agent messages, as described above.
The developers have tried to provide extensibility, simplifying the future of adding new versions of browsers to the detector, as well as improved performance and expanded detector functionality, compared to Caddy Server MITM Detection. It analyzes the following TLS Client Hello parameters by comparing real data with fingerprints of known browsers:
- TLS version;
- cipher suites;
- extensions and their meanings;
- supported groups of elliptic curves;
- formats of points of an elliptic curve.
In fact, MITMEngine performs partial fingerprinting of a user without de-anonymizing it, but with a reliable determination that the connection is established by a real browser, and not by an intermediary.
Work example
Suppose MITMEngine sees the following User Agent from the user:
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/47.0.2526.111 Safari/537.36This User Agent corresponds to Chrome 47 for Windows 7. It is accompanied by a TLS Client Hello message that indicates the following cipher suites in hex:
0000 c0 2b c0 2f 00 9e c0 0a c0 14 00 39 c0 09 c0 13 .+./.... ...9....
0010 00 33 00 9c 00 35 00 2f 00 0a .3...5./ ..This message corresponds to these cipher suites:
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b)
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f)
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (0x009e)
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (0xc00a)
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014)
TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039)
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (0xc009)
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013)
TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x0033)
TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c)
TLS_RSA_WITH_AES_256_CBC_SHA (0x0035)
TLS_RSA_WITH_AES_128_CBC_SHA (0x002f)
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0x000a)The default cipher suites for Chrome 47 are as follows:
0000 c0 2b c0 2f 00 9e cc 14 cc 13 c0 0a c0 14 00 39 .+./.... .......9
0010 c0 09 c0 13 00 33 00 9c 00 35 00 2f 00 0a .....3.. .5./..If you look closely, you can see: in real traffic, the cipher list is slightly shorter than it should be in a real browser. Although the others are arranged in the same order, but two sets are missing:
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (0xcc14)
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (0xcc13)It can be assumed that the traffic from the user's browser passes through a transparent proxy, which does not support the ChaCha ciphers. This reduces the security of the user, because the list of AES-CBC cipher suites that follow ChaCha are vulnerable to padding oracle attacks.
In some cases, MITMEngine even allows you to determine which program causes the degradation of an HTTPS connection (in the example above, this is Sophos antivirus). The server may alert the user about this threat.

Source: https://habr.com/ru/post/444496/
All Articles