What is the Mirai botnet, and how can I protect my devices?

First discovered in 2016, the Mirai botnet captured an unprecedented number of devices and caused enormous damage to the Internet. Now he is back and more dangerous than ever.
New and improved Mirai infects more devices
On March 18, 2019, security researchers at Palo Alto Networks announced that Mirai was modified and updated to achieve the same goal on a larger scale. The researchers found that Mirai uses 11 new types of exports, bringing the total to 27, and the new list of administrator credentials by default, for the sample. Some changes are aimed at business equipment, including LG Supersign TVs and Wipg-1000 wireless presentation systems.
Mirai can be even more powerful if he can take over business equipment and command business networks. As Ruhna Nigam, senior threat investigator at Palo Alto networks, says :
These new features provide the botnet with a large attack surface. In particular, the guidance of industrial units also gives him access to greater bandwidth, which ultimately will lead to greater power of the botnet for DDoS attacks.
This option Mirai continues to attack client routers, cameras and other devices connected to the network. For destructive purposes, the more devices are infected, the better. Ironically, the malicious virus was posted on a website promoting a business that dealt with “e-security, implementation and monitoring of alarms.”
Mirai is a botnet that attacks IOT devices
If you don’t remember, in 2016 the Mirai botnet seemed to be everywhere. He aimed at routers, DVR systems, IP cameras and more. These are often called Internet of Things (IoT) devices and include simple devices, such as thermostats that connect to the Internet . Botnets work by infecting groups of computers and other devices connected to the Internet , and then force these infected machines to attack systems or work on other targets in a coordinated manner.
Mirai went for the device with the default administrator credentials, either because no one changed them, or because the manufacturer hardcoded them. Botnet captured a huge number of devices. Even if most systems were not very powerful, a large number of handlers could work together to achieve more than a powerful zombie computer could do on their own.
Mirai captured nearly 500,000 devices. Using this group botnet of IoT devices, Mirai damaged services such as Xbox Live and Spotify and websites such as BBC and Github , focusing directly on DNS providers . With so many infected machines, the Dyn (DNS provider) was stopped by a DDOS attack of 1.1-terabyte traffic. DDoS-attack works, flooding the target with a huge amount of Internet traffic, more than the target can handle. This leads the victim’s website or service to slow down or completely disconnect from the Internet.
The original creators of the Marai botnet software were arrested, pleaded guilty and received a suspended sentence . For a while, Mirai was turned off. But enough code survived for other criminals who adopted Mirai and changed it according to their needs. Now there is another option Mirai.
How to protect yourself from Mirai
Mirai, like other botnets, uses known exploits to attack devices and compromise them. He also tries to use known credentials to default to work in the device and take it over. So your three best lines of defense are simple.
Always update the firmware and software of everything that you have in your home or workplace and that can connect to the Internet. Hacking is a cat-and-mouse game, and as soon as a researcher discovers a new exploit, patches will follow to fix the problem. Botnets like this thrive on unpatched devices, and this version of Mirai is no different. The exploits aimed at business equipment were identified last September and in 2017.

Fig. 1. Upgrade the firmware of the router.
Change your device administrator credentials, username and password as soon as possible. For routers, this can be done in the web interface of your router or in the mobile application (if any). For other devices that you log in with a default username or password, refer to the device manual.
If you can log in using admin , password, or an empty field, you need to change this. Remember to change the default credentials when setting up a new device. If you have already set up devices and forgot to change your password, do it now. This new version of Mirai is aimed at new default username and password combinations.
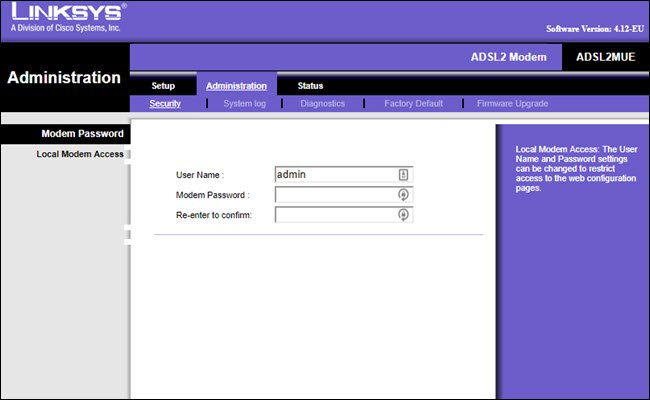
Fig. 2. Bad username example.
If the device manufacturer has stopped releasing new firmware updates or has hard-coded administrator credentials and cannot change them, consider replacing the device.
The best way to check is to start with your manufacturer’s website. Find your device’s support page and find any firmware update notifications. Check when the last one was released. If many years have passed since the firmware update, the manufacturer probably no longer supports the device.
Instructions for changing administrative credentials can also be found on the device manufacturer’s support website. If you cannot find the latest firmware updates or a way to change the device password, it is probably time to replace the device itself. You should not leave something vulnerable and permanently connected to your network.
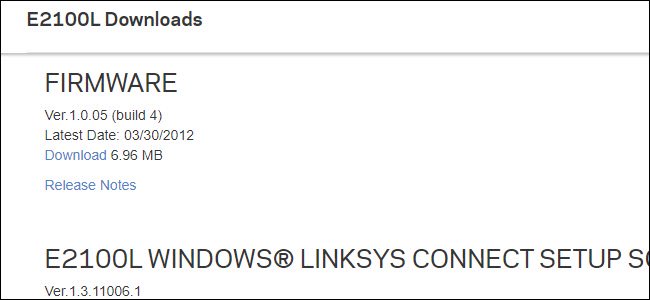
Fig. 3. If the latest firmware you can find is from 2012, you must replace your device.
Replacing devices may seem like a radical measure, but if it is vulnerable, then this is your best option. Botnets like Mirai are not going anywhere. You must protect your devices. And by protecting your own devices, you will protect the rest of the Internet.
')
Source: https://habr.com/ru/post/444436/
All Articles