How the personal data of patients and doctors could be affected due to the open ClickHouse database (updated)
I write a lot about the detection of freely accessible databases in almost all countries of the world, but there is almost no news about Russian databases left in the public domain. Although recently he wrote about the “hand of the Kremlin”, which the Dutch researcher found in fright in more than 2,000 open databases.
There may be a misconception that everything is fine in Russia and the owners of large Russian online projects are responsible for storing user data. I hasten to debunk this myth in this example.
The Russian medical online service DOC + seems to have managed to keep the ClickHouse database open for access with access logs. Unfortunately, the logs look so detailed that the personal data of employees, partners and customers of the service could be subject to a possible leak.

First things first ...
: . . , .
With me, as with the owner of the Leaked Telegram channel, the reader of the channel got in touch, who wished to remain anonymous and literally said the following:
An open ClickHouse server, which is owned by doc +, was discovered on the Internet. The IP address of the server is the same as the IP address on which the docplus.ru domain is configured.
From Wikipedia: DOC + (LLC New Medicine) is a Russian medical company that provides services in the field of telemedicine, a call to the doctor at home, storage and processing of personal medical data . The company received investments from Yandex.
Judging by the information gathered, the ClickHouse database was really freely accessible, and anyone knowing the IP address could get data from it. These data were supposed to be the logs of access to the service.
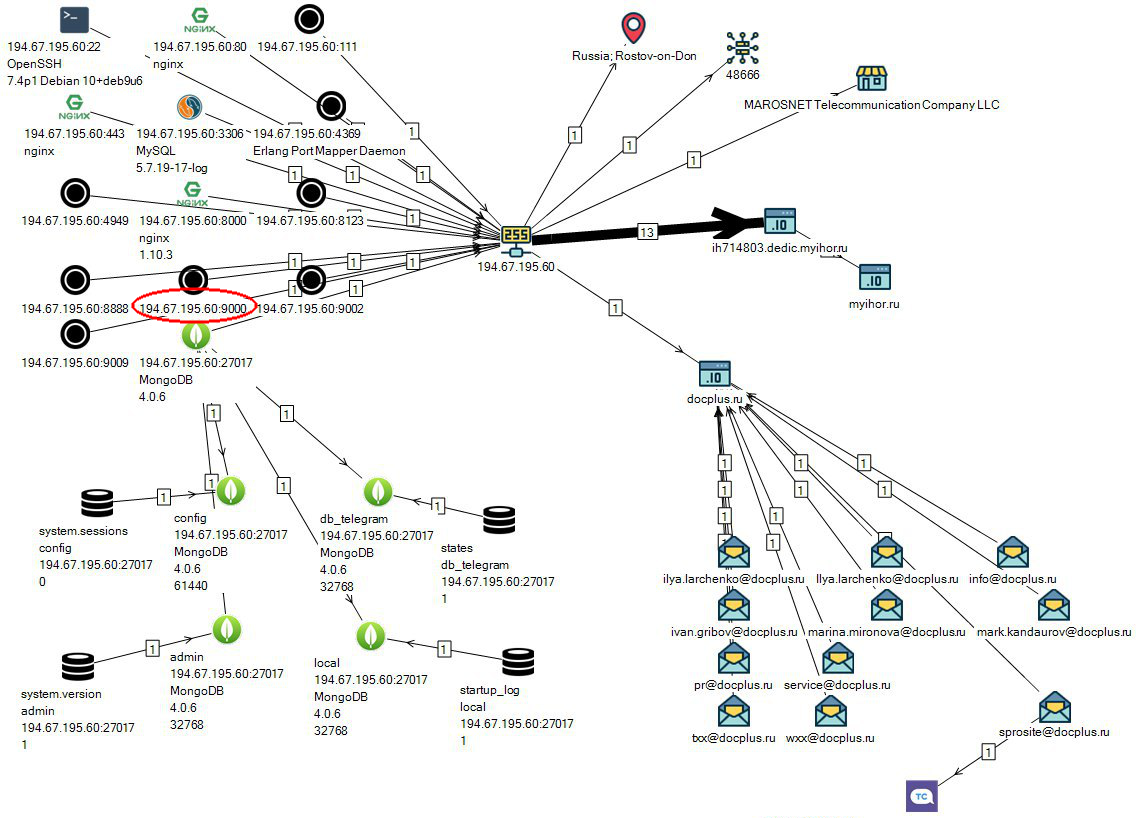
As can be seen from the picture above, in addition to the web server www.docplus.ru and the server ClickHouse (port 9000), the MongoDB database is open on the same IP address (in which, apparently, there is nothing interesting).
As far as I know, to locate the ClickHouse server, the search engine Shodan.io was used (about how the researchers discovered the open databases I wrote separately) in conjunction with a special ClickDown script that checked the found database for lack of authentication and listed all its tables. At that time, they seemed to be 474.
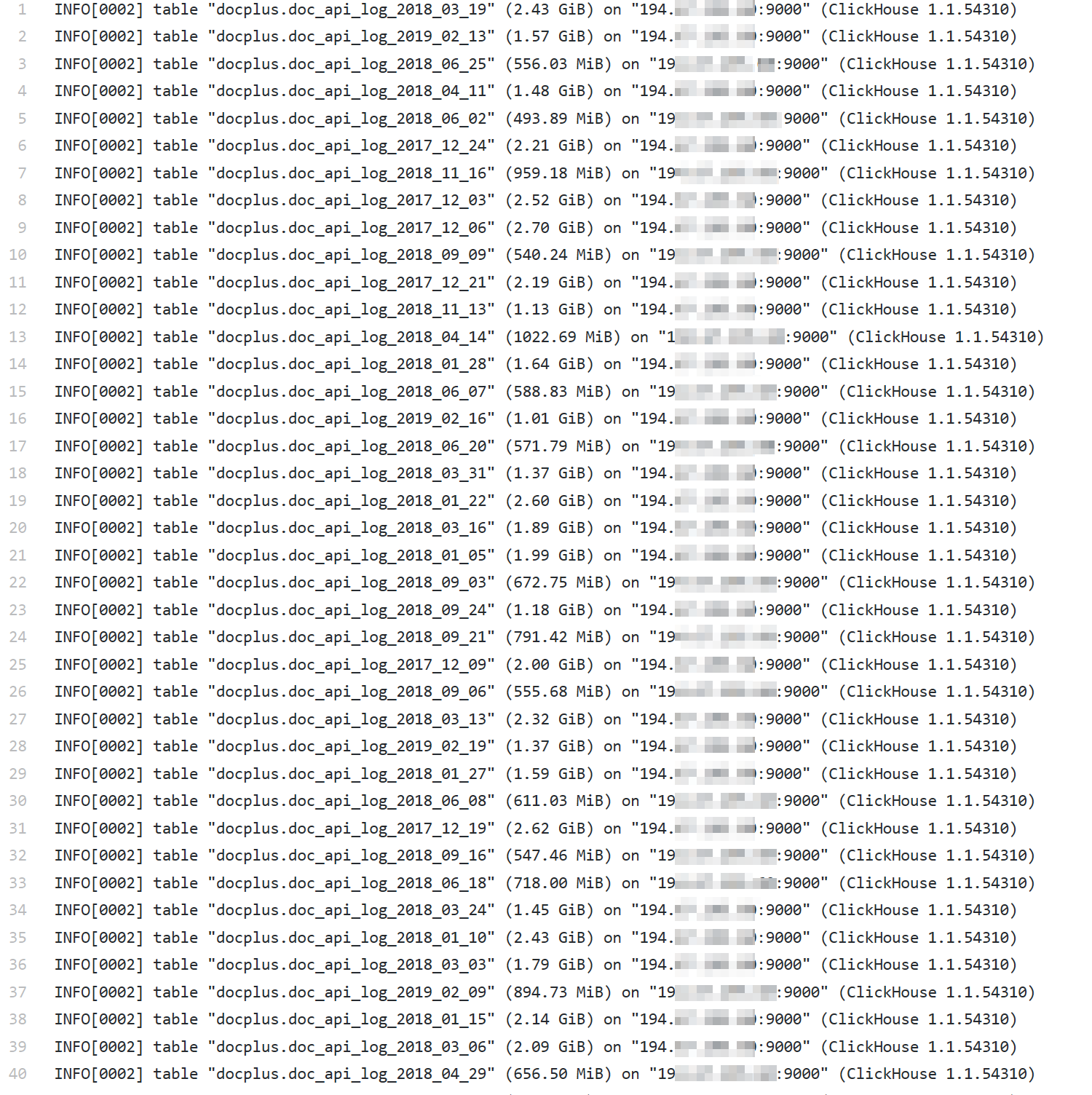
From the documentation it is known that by default, the ClickHouse server listens to HTTP on port 8123. Therefore, to see what is contained in the tables, it is enough to execute approximately the following SQL query:
http://[IP-]:8123?query=SELECT * FROM [ ] As a result of the request, it is likely that what is shown in the screenshot below could return:

It is clear from the screenshot that the information in the HEADERS field contains data about the location (latitude and longitude) of the user, his IP address, information about the device from which he connected to the service, the OS version, etc.
If it occurred to someone to slightly modify the SQL query, for example, like this:
http://[IP-]:8123?query=SELECT * FROM [ ] WHERE REQUEST LIKE '%25Profiles%25' Something similar to the personal data of the employees could be returned, namely: full name, date of birth, gender, TIN, registration and actual address, phone numbers, positions, email addresses and much more:
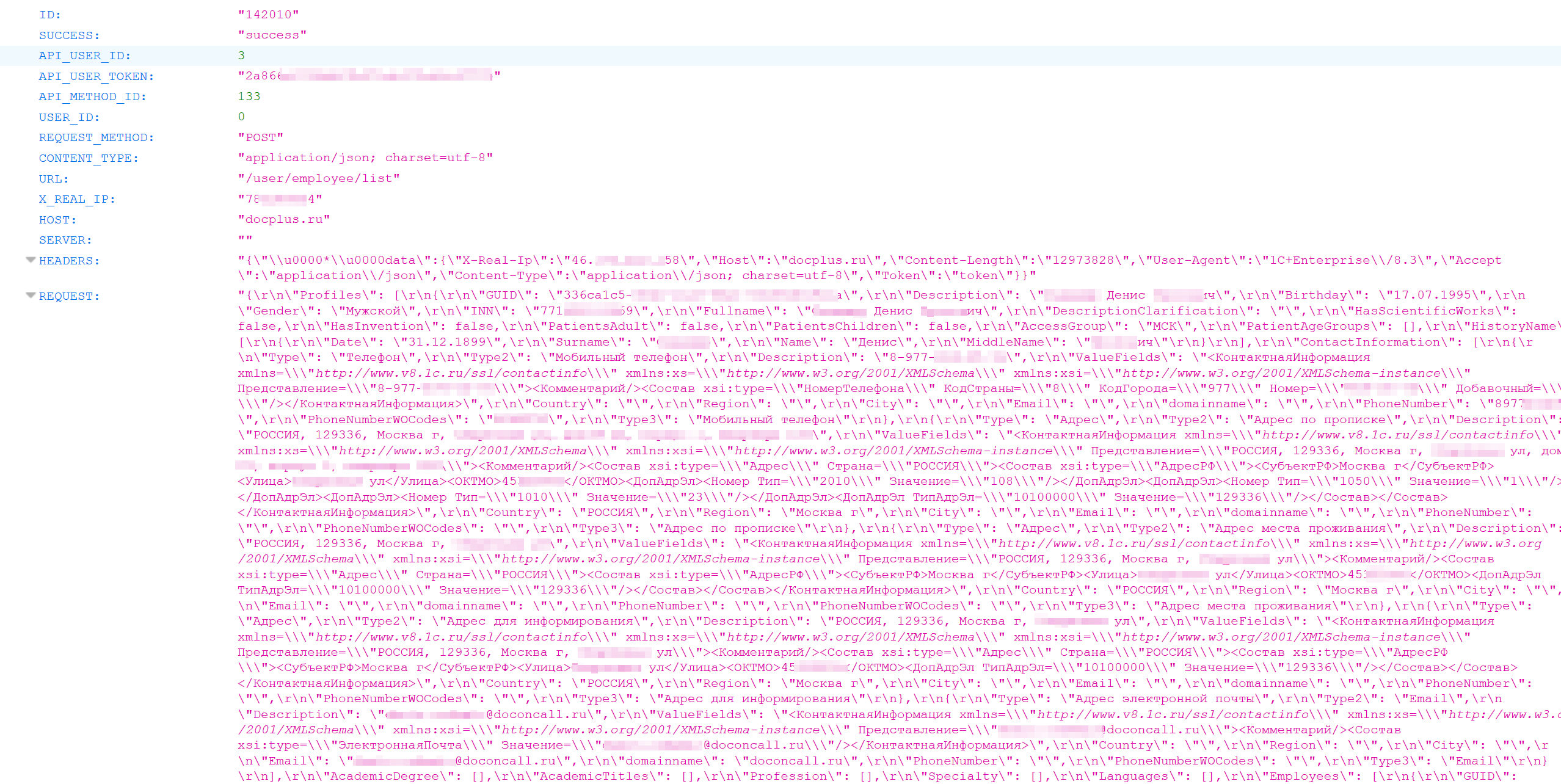
All this information from the screenshot above is very similar to the personnel department data from 1C: Enterprise 8.3.
Looking closely at the API_USER_TOKEN parameter , you might think that this is a “working” token with which you can perform various actions on behalf of the user - including receiving his personal data. But I certainly can not say this.
At the moment there is no information that the ClickHouse server is still freely accessible at the same IP address.
New Medicine LLC issued an official statement on the incident. In a statement, there are a lot of letters, summarizing briefly: “Minor leak. Human factor. Less than 1%. Test environment (on the main IP!) ”. To whom not too lazy to read I bring the statement entirely:
The company "New Medicine" (DOC +) is the operator of personal data, in connection with which it takes all the protective measures required by law. The company introduced modern means of protection that have passed the necessary certification procedures by the FSC, FSTEC. Internal processes of management and control over the state of security of information systems, in which personal data are processed, are lined up. The policy of protection and processing of personal data is available to study on our website.
DOC + uses the ClickHouse service to debug the functionality of client product improvements. ClickHouse loads data from a test and production environment. The ClickHouse service operates on the company's servers, access to which is strictly regulated and limited. The emergence of data from ClickHouse in the public domain was due to an error due to human factors. Access to data was promptly closed on 03/17/19 immediately after publication of the vulnerability. The company regularly analyzes the vulnerabilities of the personal data protection system, and this error would necessarily be detected and corrected. Unfortunately, we did not have time to do this before the error was discovered by other specialists.
In the public domain, there was temporarily a small amount of data that could not lead to negative consequences for the staff and users of the DOC + service. At the time of the incident, ClickHouse had data mainly from the test environment. The medical data of clients that have become publicly available are impersonal, it would be possible to identify the subject of personal data by it only upon receipt of the entire database. An analysis of the history of database access and outgoing traffic from our servers suggests that a leak could affect <1% of all information.
')
On the fact of the incident internal proceedings are conducted. We are developing and have already begun to introduce additional measures that further tighten data protection. We regret the incident, but once again emphasize the absence of negative consequences for our clients. Your security and privacy is a priority for the entire DOC + team from the early days of the company.
Source: https://habr.com/ru/post/444114/
All Articles