Information security instances on attackdefense.com platform

... We live in an era of big events and small people.
… Winston Churchill
Today we bring to your attention the first article from the cycle on parsing and passing laboratory work from attackdedeense.com with the support of the well-known conference organizer ( Black Hat and Pentes Academy ) - a project that allows you to understand many aspects of attacks on various protocols, services, systems. For the most part, this resource is a platform with laboratory work on the most relevant topics.
')
Immediately answer some of the questions that may appear during the reading of this material:
Under the spoiler
- What did you like about this resource? (By its simplicity of use. You do not need to have a whole range of programs and services to hone your skills, there are already a lot of them.)
- This article is advertising? (This cycle of articles will be of a purely technical nature, aimed at laboratory work, and not at PR of a resource. But we do not exclude that interest in this site may increase.)
- “Immediately, by the way, the community will receive a question, how ethical is it to describe solutions of other people's tasks and did we receive an acceptance of a similar series of articles from the authors of the resource?”
(Unfortunately, but no, we are trying to get in touch with them through public email addresses. But there is no answer yet.) - How often and how many articles are expected to be released? (In plans to publish 2 more materials, with a video presentation. And further articles will be formed already from your wishes in the comments.)
- The site already has answers to labs and a description from the video. Why then this article? (Yes, everything is true. Such materials are present especially in old laboratory works. But unfortunately some of the study materials on the topics are paid. Just like video. We’ll not talk about all laboratory works. And publish our solution, with " our "materials and our video recordings. Thus, we will not compete with the site themselves and not interfere with its sales of paid subscriptions to materials)
- Questions remarks and criticism appropriate? (Of course! Always open for conversations, for this there is: Telegram: @ orion_0ri0n)
- Are there other resources with a similar theme? (Of course! There are many of them, some of which even form their TOP best, as an example: HackTheBox)
- From a legal point of view, the actions on this resource are contrary to the law? (There is no definite answer to this question, because according to the rules of this resource. While performing laboratory work, you do not violate any laws. But if you try to hack the architecture of this resource for example or other actions prohibited by the rules: attackdefense.com/policy/ pp.txt . That resource warns you that your data may be transferred to the police or other authority
Disclosure for Law Enforcement: Binary Security Inc. If you’re willing to disclose your information?
In this article we will briefly review:
- Lyrics about the possibilities and resource. And what it will give us.
- What types of "attacks" offers a resource.
- Material on the vector of attack according to the laboratory work, which we will describe.
- The decision of one of the "test" laboratories.
- Findings.
The following articles are planned:
- Complete the full line of one type of attack. (Traffic Analysis)
- Prepare materials for the course.
- Let us analyze the main errors that occur when solving laboratory work.
- Let's collect a brief theory in this direction (theses / cribs)
- Answer questions on the previous article.
Introduction
Purpose pursued by us: To develop an interest in the study of services for those who have not previously been devoted to this topic, but had a burning interest in this area.
Some people and communities have already started this topic, but no one unlocked the potential of the resource. What we will try to offer, what others do not have. These are explanations in technologies where this or that vulnerability arose, which will make it possible to understand why this vulnerability arose and how it can be closed, avoided or counteracted.
For more skilled people who have already formed their opinion and have “their own” development directions, we suggest to get acquainted with the possibility of discovering new vectors for themselves.
For professionals, we offer to discover the new “Capture the Flag”. This area will not be given a detailed overview. It will remain for self-passage. (But, if there are volunteers who want to share their achievements, results or original solutions. We’ll be happy to add your thoughts to a separate layer of articles. As an additional review. With the mention of heroes.
For more details, see here:
For those who are interested to publish their results, we suggest including them in this series of articles. Where from you will be necessary:
What we can offer you: (unfortunately, a little)
- Provide information about what layer of solved lab work you want to demonstrate. (Perhaps it has already been passed by and the material is being prepared for it)
- The solution of this laboratory itself. The solution should include:
- The code needed to solve this labs. (most often it is already on the site. And if it matches, there is no need to copy)
- Comments on the code. After all, maybe you used your original solution. Or a solution not covered by the condition. Which speeds up, reduces time and labor costs.
- Conclusions on the laboratory. What are the comments offer or your opinion.
- Materials on this course. (since there are many directions and the community (including us) can be inferior to you in knowledge)
- Video materials and / or screenshots are required.
What we can offer you: (unfortunately, a little)
- Publication of your material in the context of a general article on laboratory work. (Except, if the material is sufficient for a separate article, then it will go as a special issue.)
- Link to you, your profile or your other resources (if you wish.)
- Advertising mention of your service or resource. At the beginning of the article. In the section about the Author.
- Our respect and recognition of the community.
- In the plans: When publishing a video passing of laboratory work, where you participated. Make a link to you or your resource. (under the video in the description)
Loading
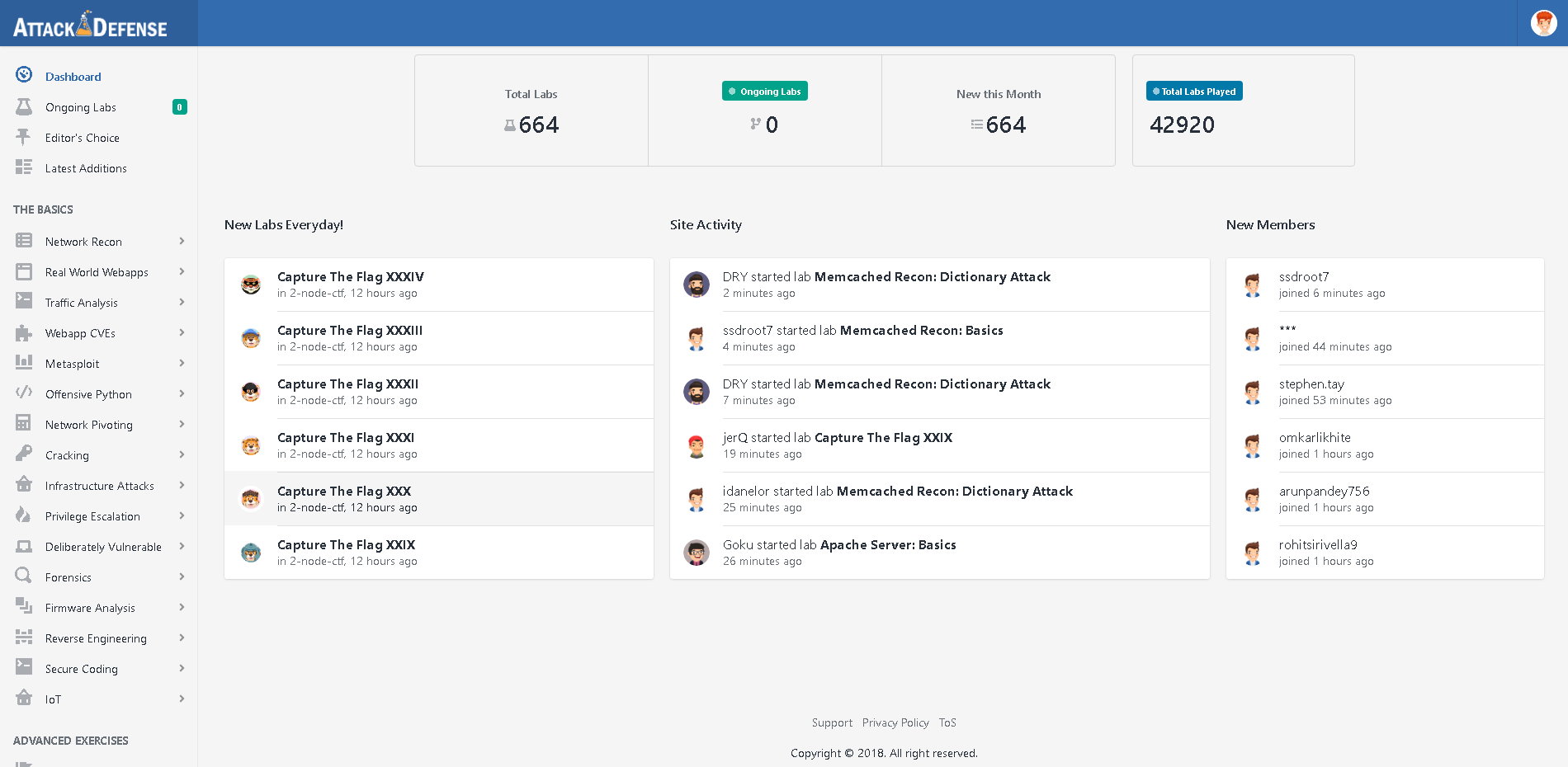
Some statistics:
At the time of this writing, the number of laboratories increased from 505 - 664 - 700 pcs.
Screenshots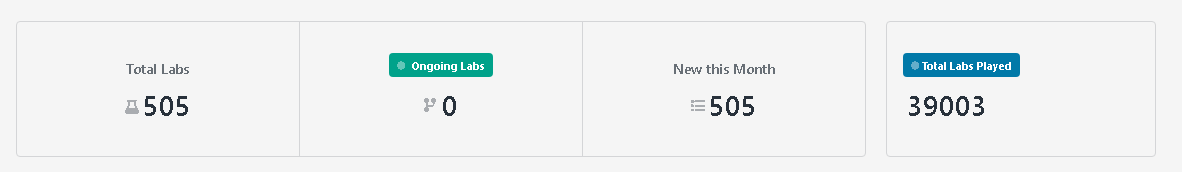



Quickly go through the menu:
| Network recon | Network intelligence: Scanning, collecting information about the most popular services (IMAP Servers, DNS, SIEM Platforms, SMB Servers, SSH Servers, Telnet Servers and others.) |
| Real world webapps | Web applications: Exploitation of vulnerabilities in the web. SQL Injection, File Upload, Stored XSS, and others |
| Traffic analysis | Traffic analysis: Learn to work with tshark and analyze traffic including Wi FI. |
| Webapp CVEs | Webapp CVEs: CVE Task Set (broken down by year, very convenient) |
| Metasploit | Metasploit attacks: instance to work with meta-sploit. Themes are different. |
| Offensive python | Python attack: |
| Network pivoting | Network Pivoting - Cannot be translated correctly |
| Cracking | Cracking *: |
| Infrastructure Attacks | Attacks on the network infrastructure: Exploiting vulnerabilities in network services |
| Privilege Escalation | Privilege escalation: instancefor elevating privileges across platforms. Linux / web |
| Deliberately Vulnerable | Intentional vulnerabilities *: ??? |
| Forensics | Forensic examination: For the most part, the analysis of logs and the ability to work with them. |
| Firmware Analysis | Analysis of firmware: Analysis of firmware of routers, search for backdoors. |
| Reverse engineering | Reverse engineering: instance with “pulling” passwords and keys. |
| Secure coding | Secure coding: A new section is still being formed. |
| Iot | IoT: A new section is still being formed |
| I really liked the last two points: (Secure Coding and IoT) for a reason. I have not seen similar laboratories for testing before. (they appeared on the resource about 02/27/2019 - fresh) We advise you to try to figure it out yourself. | |
Laboratory Analysis: Network Recon - Memcashed [Theory]
Memcached is software that implements an in-memory data caching service based on a hash table. Using the client library, it allows caching data in the RAM of many available servers (see the wiki or a little more detail on habr.com ).
What is the interest of this product, why is it given such attention?
The problem lies in the ease of use of this tool in the interests of "intruders" because the protocol used in this application is UDP. As you remember, what is the difference between TCP vs UDP protocols ( let me remind you who forgot for example: otvet.mail / Wiki or link ). Those. UDP allows you to send frame data without worrying about getting it to the destination. And most importantly, the amount of data transmitted via UDP is several times more than TCP.
But what is the attention? And the fact that when accessing this software via the network / Internet on port 11211 with the size of the incoming packet is 100 kb. The answer can be obtained 1,000–50,000 times more. Those. Sent 100 kb will return 100,000 kb. Good odds? Best!
But what is the danger then? You ask. Why do you need this information?
And the problem is this: in local area networks and telecom operators that do not control traffic, such kind of attack as ip spoofing is possible. substitution of outgoing ip. It turns out that now malicious can not only be presented by anyone, but also on behalf of him will request some information.
And here it turns out that (briefly illustrated in the image):
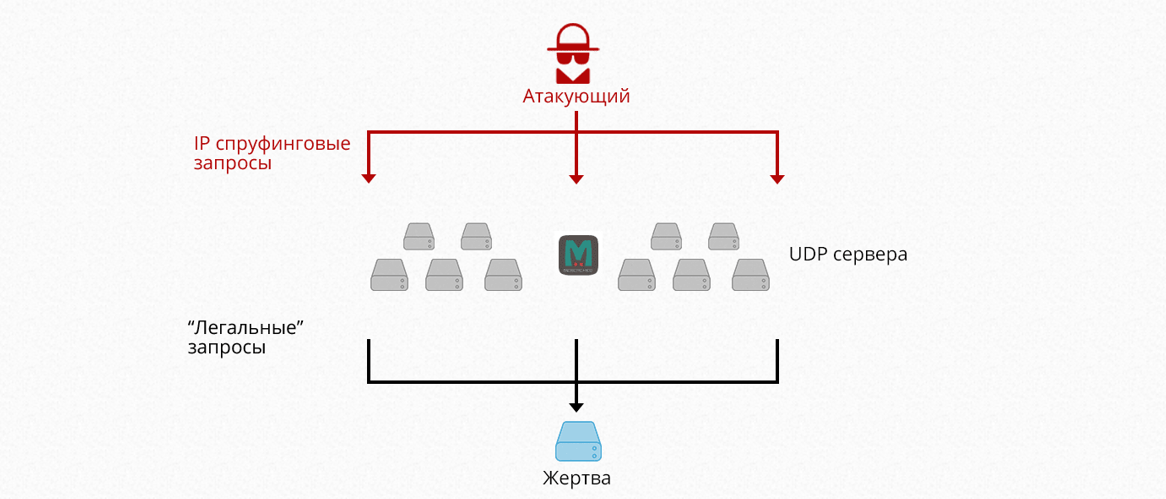
- An attacker using ip spoofing replaces his ip. On ip "victims".
- Makes a request to the Memcashed server. With a modified IP address
- The server responds to the request. But the response to the appeal already sends the "victim"
- "Victim" comes the answer 100 times the size of the request.
In consequence of the large number of such request-responses. An attack of Dos or DDos can occur depending on the number of “zombies” cars.
More details can be read here: securitylab , xakep.ru , 360totalsecurity
Or search Google.
Mitigation: How to fix the Memcached server vulnerability?
One of the easiest ways to prevent the abuse of Memcached servers as reflectors is a firewall blocking or restricting UDP speed on the source port 11211. Because Memcached uses INADDR_ANY and runs with UDP support by default, administrators are advised to disable UDP support if they do not use it. An attack through Memcached cannot be easily stopped by Internet Service Providers (ISPs) if spoofing IP is allowed on the Internet.
An example of finding a service with nmap (not the most rational way)
nmap 192.168.1.1 -p 11211 -sU -sS --script memcached-infoIn this cycle of laboratory work, it will be possible to become familiar with the simple intelligence functions of the Memcashed service. Where will the tools from the Metasploit arsenal be affected? And standard Linux system commands. Not that complicated and mediocre.
Parsing Laboratory [Practice]
[Menu]
Each laboratory work has menu items:
1. Task
2. Rules
3. Answers to the task
4. Tips for solving. (not always and not in all labs)
5. References for reading (En only)
[ The task ]
1. Find the version of memcached server using nmap.
2. Find the version information using netcat or telnet.
3. If you need to use the nmap scripts.
4. Find the number of current items on the memcached server using memcstat.
5. Find the value stored in the key “flag” from the key value of the pairs value dumped by the available metasploit module.
6. Find all the keys to the memcached server using memcdump.
[ Start ]

Click “Lad link” to open a new window with kali linux terminal.

This will be our main window. (not any virtual machines. Everything is already installed and configured for you. All lab scripts are already inside. There is nothing to download, search, invent is not necessary!) As a rule (but not always) materials, scripts and databases are in the root folder, or at home.
Task 1: Find the version of memcached server using nmap.
Hint already given earlier. Using Nmap
Nmap –p 11211 ipaddress –sV –p . 11211 -sV – 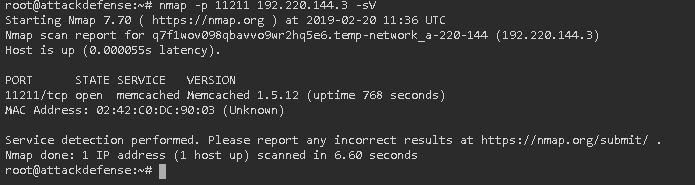
More information about nmap can be read at the end of the article. In the section Extras. materials. There we will put cribs.
Result: 1.5.12 (the answer is in the lab they write 1.5.6 - they know better)
Task 2: Find version information using netcat or telnet.
How much was not asked:
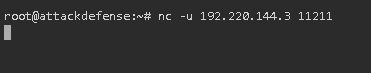
The answer never received.
Result: failed to get the result.
Task 3: Find the maximum number of simultaneous incoming connections allowed by the memcached server to use the available nmap scripts.
Hint: google search: memcached nmap
We follow the links and see that there is already a ready solution for searching for information about memcache. Since we were assured that all the scripts are already installed, we try:
Nmap –p 111211 –script memcached-info 182.220.144.3 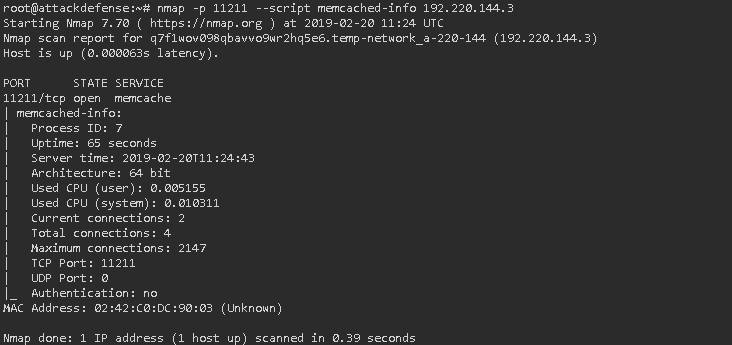
Result: 2147
Task 4: Find the number of current items on the memcached server using memcstat.
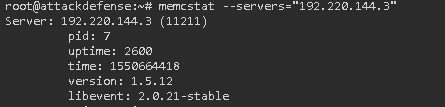
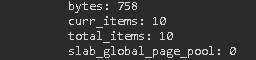
memcstat –h memcstat --servers=”IP” Result: curr_items: 10
Task 5: Find the value stored in the “flag” key from the key value pairs reset by the available metasploit module
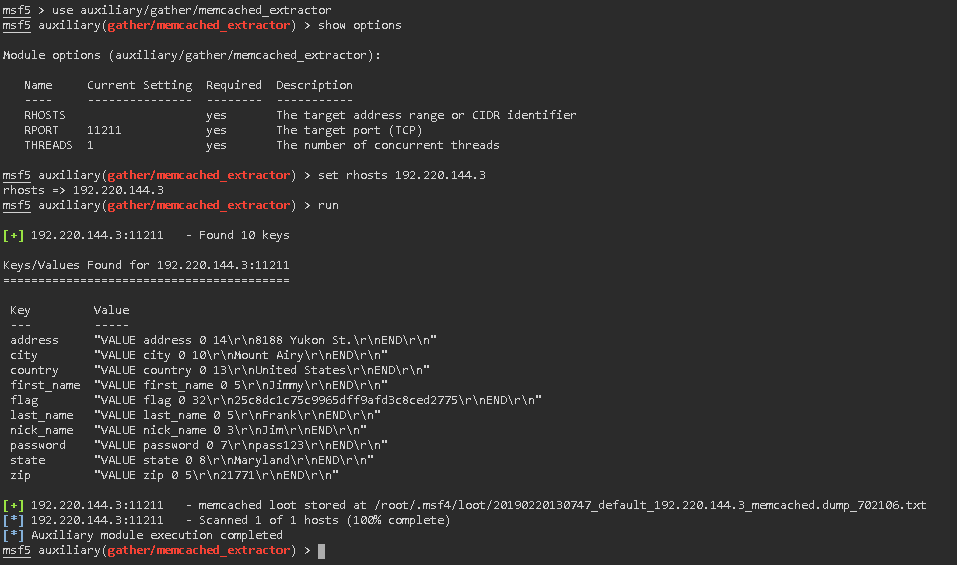
use auxiliary/gather/memcached_extractor show options set rhosts 192.220.144.3 run Script response: flag "VALUE flag 0 32 \ r \ n25c8dc1c75c9965dff9afd3c8ced2775 \ r \ nEND \ r \ n"
Result: "VALUE flag 0 32 \ r \ n25c8dc1c75c9965dff9afd3c8ced2775 \ r \ nEND \ r \ n"
(25c8dc1c75c9965dff9afd3c8ced2775) In principle, the same thing.
Task 6: Find the name of all the keys to the memcached server using memcdump.
Hint: we already know them. With the help of our metasploita in the previous task. Well, we can still see:
root@attackdefense:~# memcdump 192.220.144.3 flag, password, country, zip, state, city, address, nick_name, last_name, first_name

Result: flag, password, country, zip, state, city, address, nick_name, last_name, first_name
Task 7: Find the value stored in the key “first_name” using the memcached-tool.
Want to try it yourself with the tool "memcached-tool"
Result: But the answer will be the same: Jimmy
How did you know? We look at the screenshot with "Result 5".
Let's sum up
1. Regarding this lab
As we have seen, there are several approaches to solving the set tasks (clearly visible on question 5, 6 and 7) and, most importantly, your time spent depends on the choice of the solution.
Unfortunately, I did not understand the essence of task number 2. But alas, he did not get success (
2. Regarding the entire resource.
What we liked this resource:
Spoiler header
1. A lot of laboratory work on various topics
2. There is no need to look for various utilities for a particular attack. (everything is already in the lab)
3. There is no need to deploy virtual images / containers on your hardware. And spend time on it. (saves a lot of time)
4. Everything works through the browser. No need to have on hand putti and other utilities. Everything is already there
5. Free!
6. Constant updates (Last update + 160 laboratory works.)
7. There are answers to every lab. Even if you are not sure about the result, you can check yourself.
8. Safe! Not punishable by law. (If not to break it)
9. There are no restrictions on the execution time and the number of attempts. (I lie - is. But these are the details, see the minuses of the project)
10. And I think the most important thing that hooked me to this project. This is an opportunity to self-study new directions. There are no ready-made solutions (there are tips in the lab), but only directions with the expectation of a certain result.
11. It is possible to jointly pass part of the lab.
12. There is a CSF.
2. There is no need to look for various utilities for a particular attack. (everything is already in the lab)
3. There is no need to deploy virtual images / containers on your hardware. And spend time on it. (saves a lot of time)
4. Everything works through the browser. No need to have on hand putti and other utilities. Everything is already there
5. Free!
6. Constant updates (Last update + 160 laboratory works.)
7. There are answers to every lab. Even if you are not sure about the result, you can check yourself.
8. Safe! Not punishable by law. (If not to break it)
9. There are no restrictions on the execution time and the number of attempts. (I lie - is. But these are the details, see the minuses of the project)
10. And I think the most important thing that hooked me to this project. This is an opportunity to self-study new directions. There are no ready-made solutions (there are tips in the lab), but only directions with the expectation of a certain result.
11. It is possible to jointly pass part of the lab.
12. There is a CSF.
What did not like:
Spoiler header
1. Restriction on the number of instances launches. During the day, only 10 instances starts.
2. A pair of the result does not match the answer to the site.
3. There is no support for the Russian language.
4. Weak iron allocated to each instance. (after all, long processed commands)
5. The console breaks the connection after a certain time. Need to re-open.
2. A pair of the result does not match the answer to the site.
3. There is no support for the Russian language.
4. Weak iron allocated to each instance. (after all, long processed commands)
5. The console breaks the connection after a certain time. Need to re-open.
Add. Materials
Man nmap :
Cheat Sheet :
Man rus nmap
PS Supplement from the authors:
Sites for finding the services you need
Source: https://habr.com/ru/post/442674/
All Articles