And you will monitor everything for me? Aha
Usually Habr is used as an informational solution - someone shares information that has been accumulated and structured, and someone absorbs this information (I wanted to write “consumes”, but marketers have already fucked up this word). I, as an old-timer, and considering the light relaxation between February 23 and March 8, wanted to appeal to the very collective intelligence that makes any article more interesting. And since writing a simple question - like on the forum - is boring, I will try to dilute my question with interesting facts.
I'll start from afar: I have one favorite study, dating back to 2014. It says that from 22% to 43% of the subjects are ready to download and run an unknown executable file, if they pay in the range from 1 cent to 10 dollars. I already wrote about him in a text dedicated to the offices of the future .
')
Since one of my main jobs is related to virtualization, this aspect of security is very interesting to me. Ok, the problem with the same distributions and batch update of users is quite simple to solve with the help of a hypervisor and a thin client, however - we live in reality - there will always be a part of users who do not go there, start the wrong thing and do not. I have a simple question: who uses which security system in virtualization and why?
Wagging on the interesting side number 1
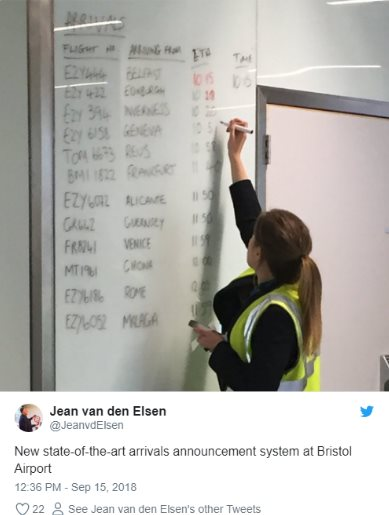
As a rule, in such articles that are published in corporate blogs, they write about ten examples of how a virus ciphers something. Most often, again, remember Petya. It is much more interesting for me to recall a bit of a curious incident that happened at the airport of Bristol.
There, too, the system was
- Where is my flight?
- And we just erased it.
- And what is my gate?
“And the devil knows, Jo has bad handwriting.”
We return to the problem for the sake of which, in fact, this post was started. On one of the projects where I participate, we use Citrix, and we chose it in comparison from this topic . So, recently we were offered to connect Citrix Analytics. According to the sellers, this thing will monitor user activity and isolate users / processes that create something wrong.
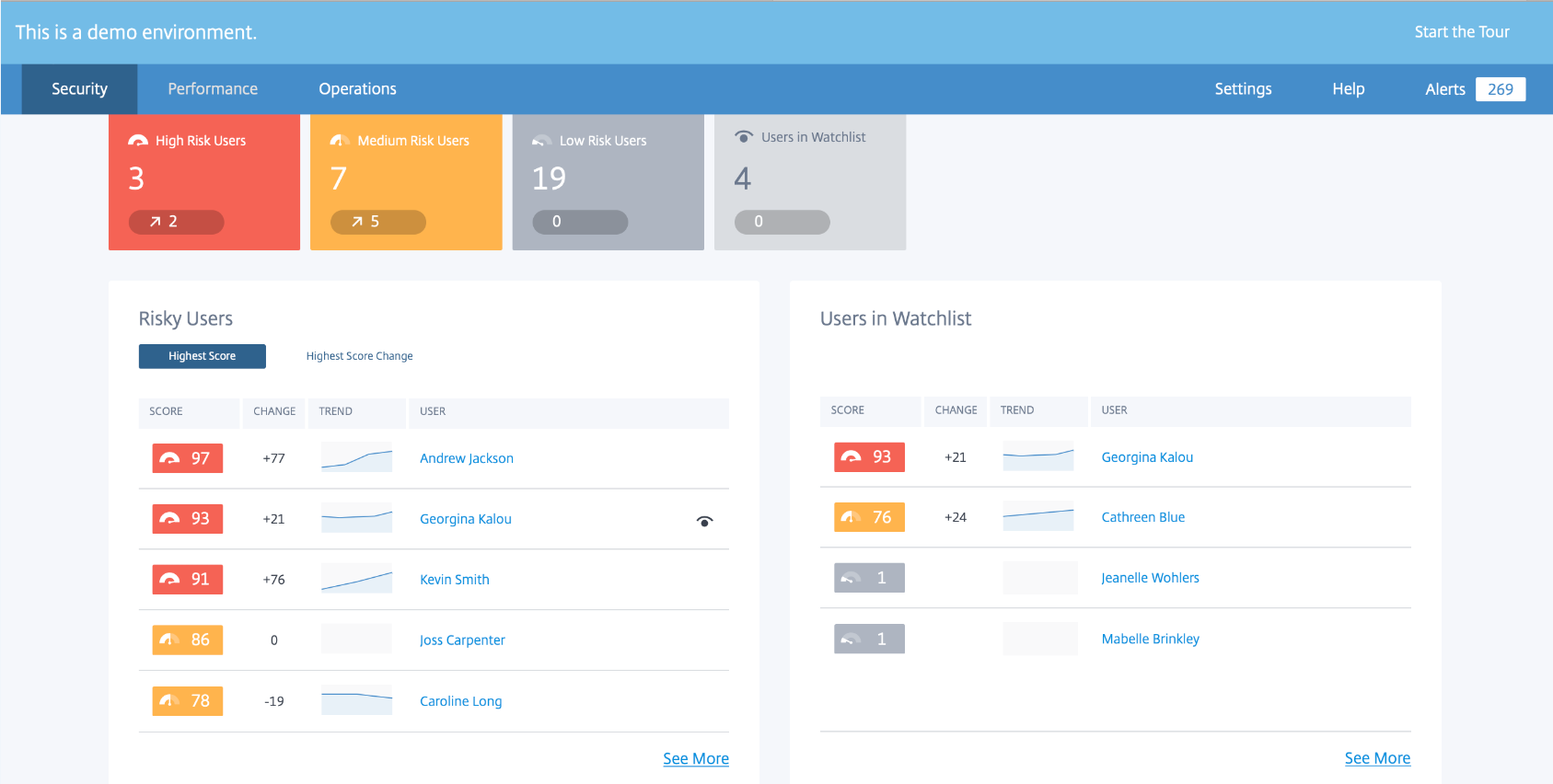
As usual, they promise machine learning, blacklists, and security breach patterns. Since, in theory, a piece is useful, we have a logical question - who actually used and are there other options?
Wagging on the interesting side number 2
Again, when they talk about various leaks, they recall the theft of passwords and other information (for example, the very cool and technically competent edition of The Bell in digital totals of the year mentioned leaks 4 times, if you count Google+ for 2 leaks - all 5). Me the question of long copying of source codes and documentation interests.
For example, Panama Plum (Panamagate). The volume of documents was 2.6 terabytes. Copying and accumulation of such a volume of information could not be unnoticed. Do large companies know now that one of the outgoing employees is not copying their data “for memory”?
What happens? It turns out that we need some kind of system that “chocks” when someone massively rubs something (cryptographers) and eats resources for encryption as if not to themselves (well, or other patterns of behavior of cryptographers). Still, when someone massively copies something to his corner. And when this someone, radish such, walks on potentially dangerous sites. And here, too, need patterns, because the sites from the black list, he will not go, but on similar - easily. Just banning by keywords is also a half decision.
We were given a chance to play around with the Citrix admin panel and if you look at the description and dig deeper, it looks fine.
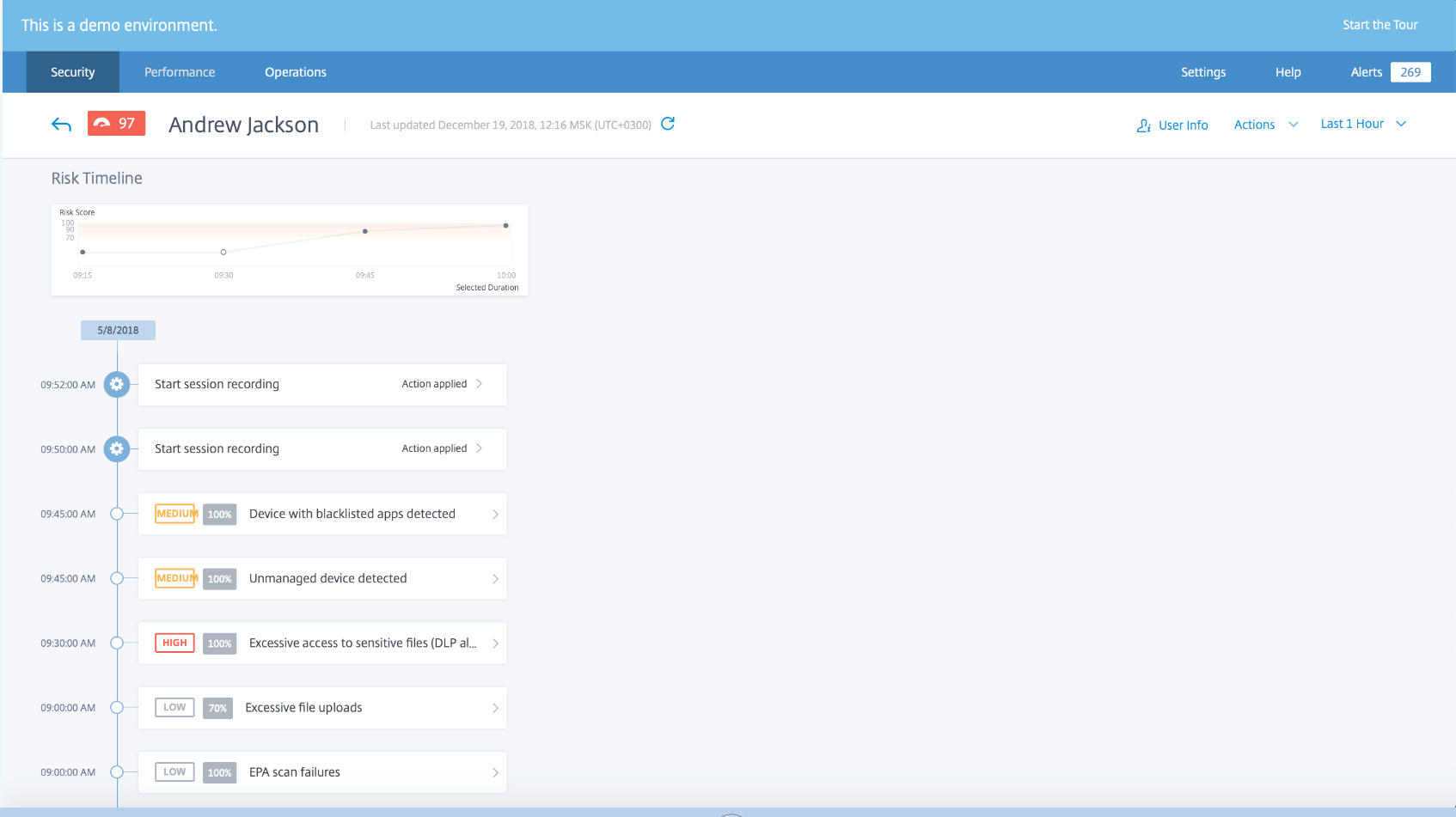
What-what did you do there, Andrew?
But we are literate people. Experience shows that when you choose from only one option, then, as a rule, this option turns out to be wrong :). Therefore, I have a simple question - did someone use a similar or similar solution? Is there something better, cheaper or better and cheaper at the same time?
Superficial googling (and not superficial too) shows that the big players have something similar, but there is very little information. At first, we looked at WMWare - it’s always interesting, and did you make the right choice two years ago when choosing virtualization? Something close is called AppDefense . There, too, the “intelligent processing algorithm” within applications is triggered. But how it works is a very interesting question.
Judging by this hour-long video, protection against encryption and other software nastiness works well there — such an antivirus on steroids — but there is no automatic user surveillance. Therefore, there is also the issue of real use - what is there really and how it works.
Let's go further. In fact, virtualization is just a bunch of jobs. Are there any solutions designed for a bunch of physical machines? For example, Cisco has a certain Cisco DNA Center where they promise to “quickly detect and react to threats before hackers can steal data or disrupt their work.” It sounds cool. Another catch: “DNA Center collects data about devices, applications, and users from multiple sources, and then applies advanced analysis algorithms to detect correlations and suggests remediation measures.”
The video also promises something close to the requested functionality.
But again, experience suggests that Cisco is more about networking solutions. And in order to tie it to virtualization, you have to somehow make this service friends with DHCP.
It seems to me that this thing is exclusively for heaps of network connections and is hardly useful in our simple and virtual conditions.
And what do you say, dear colleagues?
Source: https://habr.com/ru/post/442594/
All Articles