Security Week 10: NVIDIA driver vulnerabilities
One thing we have never discussed in the digest format is the vulnerability in the drivers for video cards. NVIDIA published on February 28 information about eight vulnerabilities: almost all allow you to elevate privileges or execute arbitrary code. One flaw relates to the now fashionable type of attack on a third-party channel - the fact that this problem is “closed” with the help of a simple driver update is remarkable in itself.
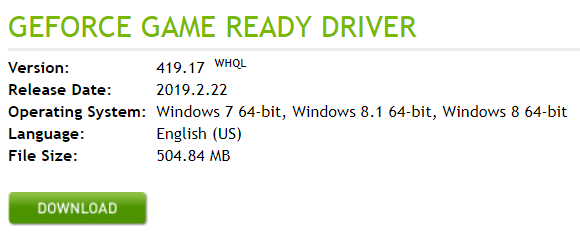
It seems that the problems in the drivers for the video cards took the information security community unawares: in fact, we deal only with information from the manufacturer, and it’s unclear how these vulnerabilities are applicable in real attacks. Anyway, it is recommended to update the drivers to the latest version - this is 419.17 for GeForce video cards. Updates for drivers on Unix-like systems are available separately - only the side channel vulnerability is closed there.
Driver packages with a capacity of hundreds of megabytes haven't surprised anyone for a long time. In the case of NVIDIA, this is rather a full-fledged set of programs for working with a video card, ensuring compatibility in games, supporting virtual reality devices, streaming capabilities, and more. The latest driver version (with patches) weighs a little more than 500 megabytes. However, NVIDIA services and additional software are responsible only for one of the eight vulnerabilities, all others are found in the system part.

The only exception is in the software for processing three-dimensional video, for which it is theoretically possible to execute arbitrary code, privilege escalation or denial of service when opening a “prepared” file.
')
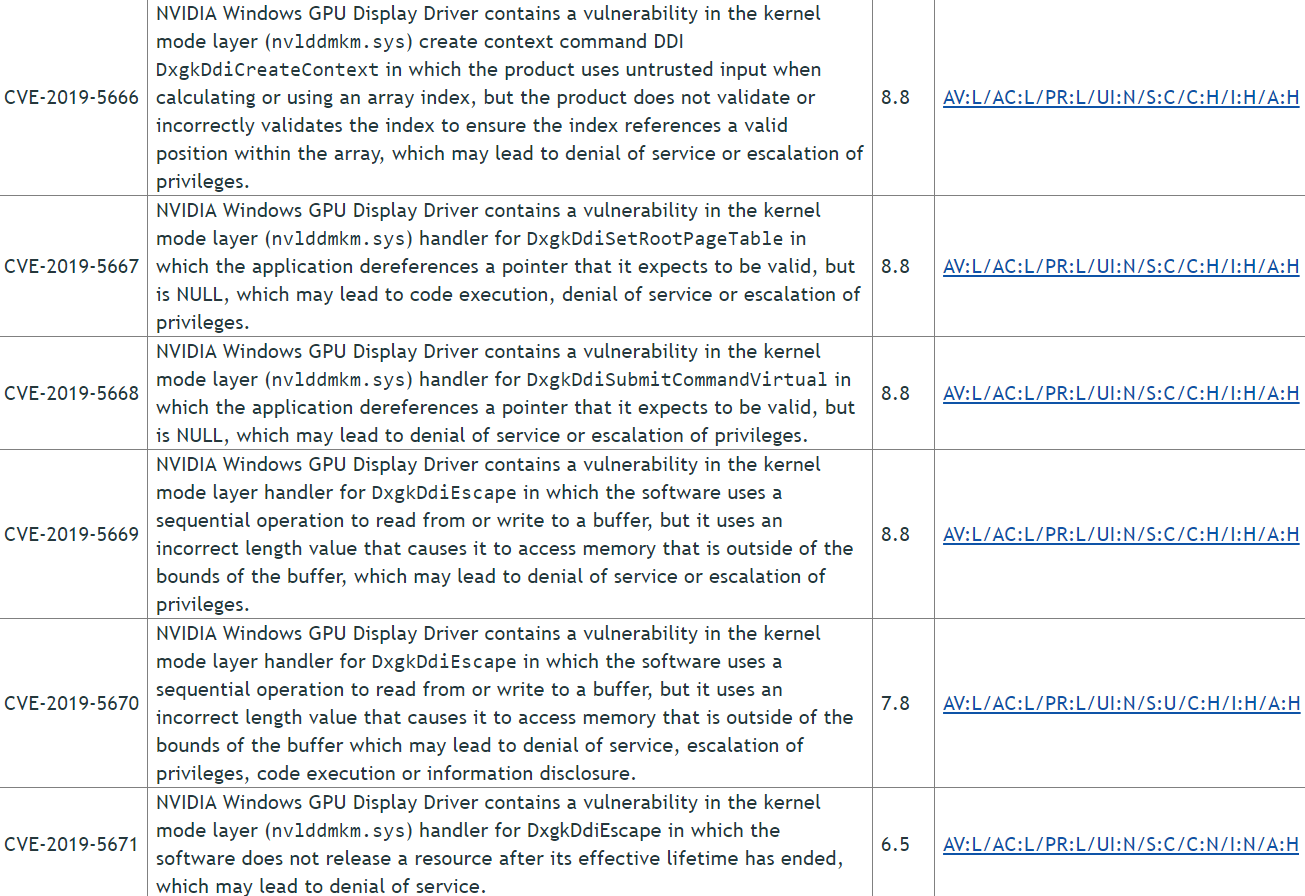
Another six vulnerabilities somehow lead to DoS, privilege escalation, and in two cases to the execution of arbitrary code. There is no data on how such attacks are realizable in practice, but it can be assumed that the most “bad” scenario is when a vulnerability in a video driver can be caused, for example, via a browser that uses a video accelerator.

Finally, another gap theoretically allows for an attack on a third-party channel. The danger level according to the CVSS V3 assessment method is rather low, the attack must be carried out locally, and there is no possibility of remote operation of the bug. This vulnerability and its exploitation scenarios were described by the University of California at Riverside in November 2018.
The research paper provides several examples of practical attacks through third-party channels, and in each case, the attacker gains access to the information of the process that is performed using video card resources. But before that, experts define three general categories of attacks, depending on the application of the video card:
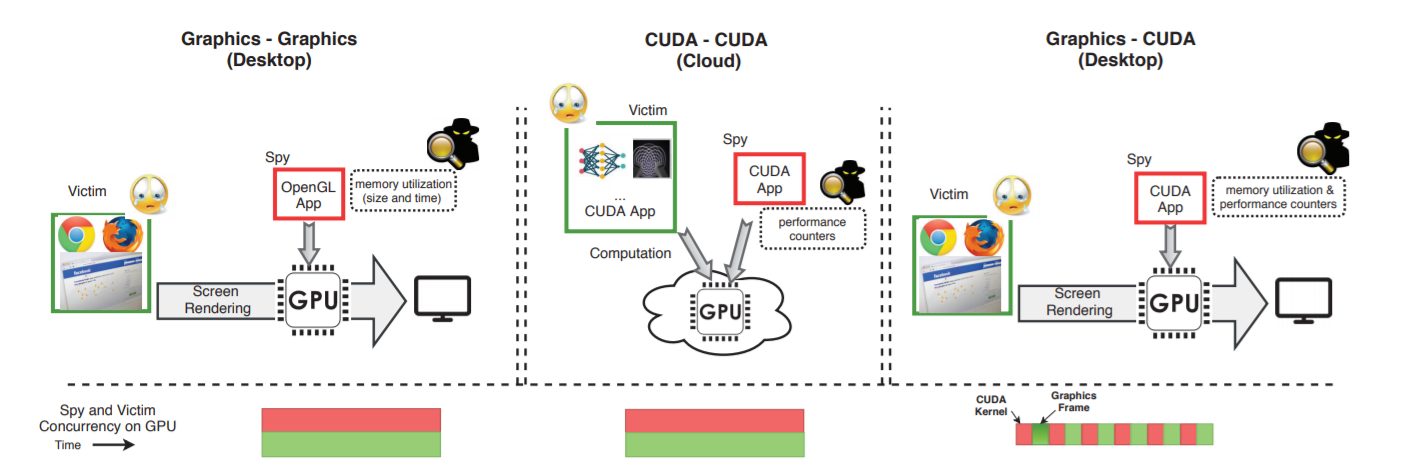
The most obvious option is using an OpenGL application to attack another application accessing a video card using the same programming interface. This method applies only to the desktop. But theoretically, you can attack and applications that use a video card for computing. This direction is generally more “interesting”, as it affects the server infrastructure.
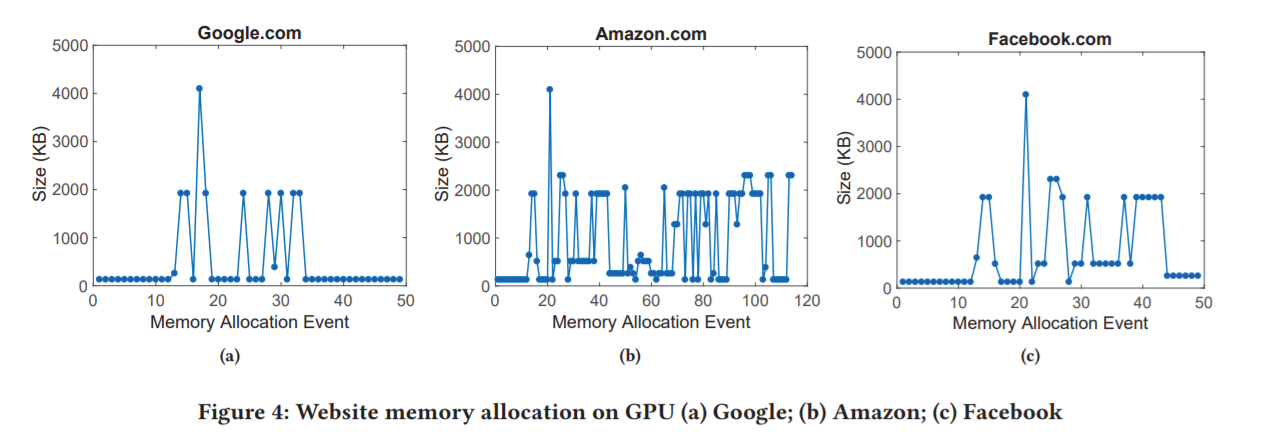
Example of a practical attack: a third-party application measures delays when accessing a video card and receives information about the amount of allocated memory in the attacked application (in this case, the browser). Since websites use video memory in different ways, the analysis of this information over time makes it possible to determine which website a user is accessing with a fairly high probability. In the following example, this idea is developed to determine the moment when a user enters a password on a specific website. The password itself cannot be intercepted, but the information on such an operation theoretically has value for the attacker.
An attack on an application using the CUDA SDK allowed researchers to restore the parameters of a neural network, something that neural network developers usually try to keep secret. The researchers noted that it is possible to reduce the information content of information “leaks” by modifying the API, which, apparently, was done in updating drivers for Windows, Linux and BSD systems.
An attack on system software and utilities for devices is hardly a serious danger if there are much simpler methods of stealing user data and gaining control over the system. There is even less potential for an attack via third-party channels, but theoretically the ability to access private data is of interest - for example, when using video card resources for encryption. In the context of NVIDIA drivers, pay attention to support for older devices. There is a list of NVIDIA video cards recognized by the developer to be outdated, but it’s easier to see for which video cards the latest driver version is available, covering the latest vulnerabilities. It turns out that all video cards are supported starting with GeForce 6XX. This series was released in 2012, and according to the manufacturer, for her it was the last patch. Not the most unexpected news, but old hardware, no longer supported by the manufacturer at the software level, can add system vulnerabilities even with modern software.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.

It seems that the problems in the drivers for the video cards took the information security community unawares: in fact, we deal only with information from the manufacturer, and it’s unclear how these vulnerabilities are applicable in real attacks. Anyway, it is recommended to update the drivers to the latest version - this is 419.17 for GeForce video cards. Updates for drivers on Unix-like systems are available separately - only the side channel vulnerability is closed there.
Driver packages with a capacity of hundreds of megabytes haven't surprised anyone for a long time. In the case of NVIDIA, this is rather a full-fledged set of programs for working with a video card, ensuring compatibility in games, supporting virtual reality devices, streaming capabilities, and more. The latest driver version (with patches) weighs a little more than 500 megabytes. However, NVIDIA services and additional software are responsible only for one of the eight vulnerabilities, all others are found in the system part.

The only exception is in the software for processing three-dimensional video, for which it is theoretically possible to execute arbitrary code, privilege escalation or denial of service when opening a “prepared” file.
')

Another six vulnerabilities somehow lead to DoS, privilege escalation, and in two cases to the execution of arbitrary code. There is no data on how such attacks are realizable in practice, but it can be assumed that the most “bad” scenario is when a vulnerability in a video driver can be caused, for example, via a browser that uses a video accelerator.

Finally, another gap theoretically allows for an attack on a third-party channel. The danger level according to the CVSS V3 assessment method is rather low, the attack must be carried out locally, and there is no possibility of remote operation of the bug. This vulnerability and its exploitation scenarios were described by the University of California at Riverside in November 2018.
The research paper provides several examples of practical attacks through third-party channels, and in each case, the attacker gains access to the information of the process that is performed using video card resources. But before that, experts define three general categories of attacks, depending on the application of the video card:

The most obvious option is using an OpenGL application to attack another application accessing a video card using the same programming interface. This method applies only to the desktop. But theoretically, you can attack and applications that use a video card for computing. This direction is generally more “interesting”, as it affects the server infrastructure.

Example of a practical attack: a third-party application measures delays when accessing a video card and receives information about the amount of allocated memory in the attacked application (in this case, the browser). Since websites use video memory in different ways, the analysis of this information over time makes it possible to determine which website a user is accessing with a fairly high probability. In the following example, this idea is developed to determine the moment when a user enters a password on a specific website. The password itself cannot be intercepted, but the information on such an operation theoretically has value for the attacker.
An attack on an application using the CUDA SDK allowed researchers to restore the parameters of a neural network, something that neural network developers usually try to keep secret. The researchers noted that it is possible to reduce the information content of information “leaks” by modifying the API, which, apparently, was done in updating drivers for Windows, Linux and BSD systems.
An attack on system software and utilities for devices is hardly a serious danger if there are much simpler methods of stealing user data and gaining control over the system. There is even less potential for an attack via third-party channels, but theoretically the ability to access private data is of interest - for example, when using video card resources for encryption. In the context of NVIDIA drivers, pay attention to support for older devices. There is a list of NVIDIA video cards recognized by the developer to be outdated, but it’s easier to see for which video cards the latest driver version is available, covering the latest vulnerabilities. It turns out that all video cards are supported starting with GeForce 6XX. This series was released in 2012, and according to the manufacturer, for her it was the last patch. Not the most unexpected news, but old hardware, no longer supported by the manufacturer at the software level, can add system vulnerabilities even with modern software.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/442568/
All Articles