How I decided to protect documents from falsification and “invented” an electronic digital signature
What is it about
The idea to create your own small Internet project to protect documents from forgery, I was prompted by the discussion on the forum of flaw detectors dedicated to the mass-scale forgery of the quality control reports issued by them.
During the implementation of my project, I realized that I had come to the concept of an electronic digital signature, that is, a bicycle, I, of course, did not invent it, but the story about my path can be instructive.
The urgency of the task of protection against fakes
The fact is that in our century of paperless information, not a single capital construction, be it a gas pipeline or a shopping center, can be done without preparing a complete set of as-built executive documentation, part of which includes non-destructive testing findings (visual, radiographic, ultrasound).

')
This conclusion is a document drawn up on a certain form with a conclusion about the suitability or unsuitability of, for example, a weld. Non-destructive testing services cost money and often quite considerable ones. A dishonest customer / intermediary may hire an accredited laboratory, obtain several conclusions from it and terminate or suspend work.
What surprise can there be for a defectoscopist or laboratory chief when they learn that after the work has been stopped, conclusions are issued on their behalf, fake seals are put on them and signatures are forged. The reputation of the laboratory suffers, and indeed the law is violated. Just in some cases, no one will know about it.
As part of the discussion on how to protect your documents, the idea was put to put a QR code on the document, in which the conclusion number, date and conclusion of the validity or non-validity of the object of control will be recorded. What is so good about this method - the QR code will remain well distinguishable when scanning, copying a document.
However, fraudsters will be able to just generate a QR code with the necessary content.
The birth of an idea
And then a thought struck me: why not encrypt the contents of such a QR code with a reliable algorithm. If so - you need to think of a way to decrypt it when scanning, for example, through the camera of a smartphone. Here was born the idea to do decryption on the side of the web-service, which will store the decryption key.
The last time I did a site in 2000 was in notepad and I’m not very familiar with modern site-building technologies, so I chose Wix, thinking that with the help of the service I would get a nice picture and minimal possibilities of working with the database, and with the help of Wix code I would encode what I need.
I will say right away that I did it without much difficulty, and in a few evenings, as an amateur, I was able to assemble the solution I needed from more or less ready-made blocks.
Encryption
I took a ready -made AES 128-bit encryption algorithm with a Java Script implementation on Github and placed it in the backend section of the site.
This was probably the easiest part of the job. How encryption works itself was not at all interesting for me. I was worried about the grandeur of the plan.
The main thing to remember to translate the encoded text in Bytes, and the result of encryption in HEX.
// Convert text to bytes var textBytes = aesjs.utils.utf8.toBytes(text); // The counter is optional, and if omitted will begin at 1 var aesCtr = new aesjs.ModeOfOperation.ctr(key, new aesjs.Counter(5)); var encryptedBytes = aesCtr.encrypt(textBytes); // To print or store the binary data, you may convert it to hex var encryptedHex = aesjs.utils.hex.fromBytes(encryptedBytes); QR code generation
I used ready API .
To work, it is enough to create an html1 object - to display an arbitrary html code and call the API function
let val = “ " $w("#html1").src = "https://api.qrserver.com/v1/create-qr-code/?size=100x100&data=" + val.toString(); $w("#html1").show(); Work with users
Wix supports basic user registration and profile editing features. A tool that is somewhat buggy, but workable.
I just needed to add a field that describes the name of the organization that the registered user represents, but this field is read only and the service administrator fills it when he receives confirmation that the registered user really represents the specified organization.
It was also necessary to fasten the simplest logic associated with paid / free access to functions (up to 20 documents per month can be protected for free) and the term of payment for services.
Principle of operation
A unique encryption private key is tied to a user account.
A logged in user fills out a form with information on the conclusion (number, date, result):
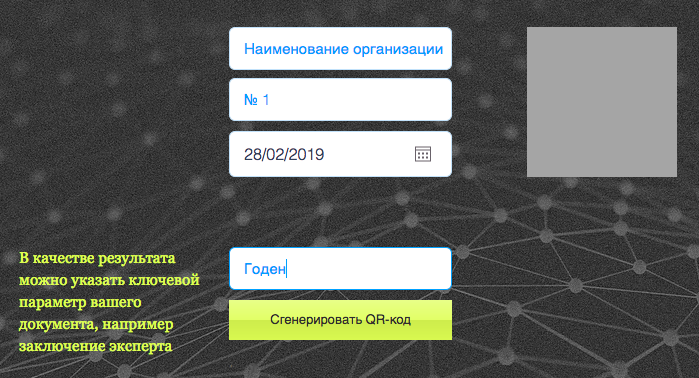
The algorithm then returns a URL containing the TEXT ciphertext and acting as the public key USER_ID, as in the example below:
https:// * * /checkqr?user=3b01b0aa-68a0-4521-ab12-f17b86d3eabc&v=1.0&text=8a026594c26be959f4280e28fe8402c1acef233e369a31613d654d3b0a5bbaca206f3058d27d2fde66b65cb64a5a6caecb69b07ad39c0015e923dad89eb723The URL turns into a QR code that the user already puts on his document by copying it to the clipboard (you can include it in the source file or stick it as a sticker on the finished printed document).

What is important here is that - as such, the information does not fall into the database of the site, but remains only in the form of this link and a QR code containing this link. Thus, no information about the contents of the protected document is stored on the server.
Code verification is performed by the site when linking.
For parsing when the website recognized the link, I used Wix code help.
www.wix.com/code/reference/wix-http-functions.html
If something went wrong during the decoding, but it could be if they tried to make some changes to the original QR code
“The document code has been decrypted with an error. Fake is possible. Contact the organization that prepared the document for clarification. ”If the decoding is completed successfully, the decrypted text containing the laboratory name, document number, date of issue and result is issued, and the user is asked to compare the result of the decryption with what he sees on the real document.
Conclusion
From the birth of the idea, I came to a working implementation with the help of a number of ready-made bricks.
I invite you to discuss the idea invented by me, trying to test / hack my service.
What is left to finish
Write on habr implementation- Understand how to reset a query, if the link has already been checked once
- Think up how to squeeze the cipher text, because when a long URL is encoded, the size of the QR code is too big
- Add the ability to copy the code to the clipboard or send to the mail by clicking on the button (until I figured out how to do it in javascript)
- Improve the work with the mobile version
Preliminary response to possible criticism:
Is it not easier for the laboratory to keep a register of conclusions on its website, but will a similar QR tag lead to this register or even display a copy of the conclusion?This can be done, but it will take considerable manual work or the introduction of its own IT solution like the one developed by me, but it will obviously cost more than take the ready-made solution.
It is impossible to make such a register fully public, because the information is not open, but can only be considered by the contractor, the customer and Rostechnadzor.
Source: https://habr.com/ru/post/442210/
All Articles