Industrial wireless networks: which one to choose?
We are accustomed to the fact that data can easily be transmitted through the air. Wireless data transmission is used everywhere - WiFi, Bluetooth, 3G, 4G and others. And the main criterion for evaluating a particular technology was the speed and data transfer and their volume. But is it always that important?
For example, in the industry, wireless technologies are also actively gaining momentum, but in addition to the usual WiFi, Bluetooth and other modern technologies, it is often possible to find, at first glance, exotic protocols at industrial sites. For example, WirelessHART or Trusted Wireless 2.0, transmitting data at a maximum speed of 250 kbps. First you start to think that these are some outdated technologies and you need to switch to WiFi and other “fast” protocols. But is this fair for industry? Let's see.
Compare the four technologies - WiFi, Bluetooth, Trusted Wireless 2.0 and WirelessHART. All technologies will be considered at 2.4 GHz. Other frequencies for the Russian Federation are not very relevant (well, except 5 GHz, but this frequency range only supports WiFi).
')
We will compare according to several criteria:
The comparison is theoretical.
The first thing that questions arise when thinking about network organization using wireless technologies is the reliability of data transfer. By reliability of data transfer, I propose to understand data transfer with a permanent connection and without data loss.
Data loss and connection failure can be caused by two main factors:
Electromagnetic interference
Electromagnetic interference at an industrial facility is generated, first of all, by frequency converters, electric drives and other primary equipment. Such interference has a frequency range that is a multiple of kHz or MHz. And all the technologies that we have taken for comparison, operate at a frequency of 2.4 GHz. Interference from primary equipment simply does not reach this range. Thus, other wireless systems transmitting data at 2.4 GHz become a source of interference. There are two completely different approaches to ensure the electromagnetic compatibility of these systems:
When using DSSS, a useful signal passes through a spreading code generator, where one bit of useful information is replaced with N bits, which increases the clock frequency by N times. This affects the spread of the spectrum also N times. At the receiver, this signal passes through the same generator and decoding information occurs. The advantage of this approach is the ability to transfer data at very high speeds. The signal occupies a certain frequency band and narrowband interference distorts only certain frequencies of the spectrum, but there is enough information to reliably decode the signal. But after a certain threshold of the frequency spectrum of the interference frequency, the signal will be impossible to decode. The generator simply does not understand where the useful signal is, and where is the superimposed one.

DSSS
When using FHSS, the data transmission frequency changes in a pseudo-random order. In this case, the resulting interference will affect only one of the random frequencies, regardless of the width of the spectrum.

Fhss
Thus, if serious electromagnetic interference occurs in the FHSS system, some data will be lost, and in the DSSS system, data transmission will stop completely.
WiFi uses DSSS. The width of one channel is 22 MHz and, accordingly, 14 WiFi channels are available on the 2.4 GHz band. Only 13 are available in Russia. At the same time, 3 non-overlapping channels are available for use. Surely, many of you have watched a picture of WiFi at home completely. This can happen just because a neighbor has an access point operating on the same channel as your point, or on an overlapping channel.
Bluetooth uses FHSS technology. The width of one channel is 1 MHz. 79 channels are available for rebuilding and access. As with WiFi, a different number of channels may be available in different countries.
Wireless HART uses a combination of FHSS and DSSS. The width of one channel is 2 MHz and all channels are located on a width of 5 MHz, i.e. 16 channels are available, and they are all non-overlapping.
Trusted Wireless 2.0 uses FHSS technology. Devices are available 127 channels for adjustment. The number of frequencies available for selection by a specific device depends on the “blacklist of frequencies”, which is configured in order to ensure compatibility with other wireless systems, and whether special frequency bands (RF band) are used to optimize the wireless network.
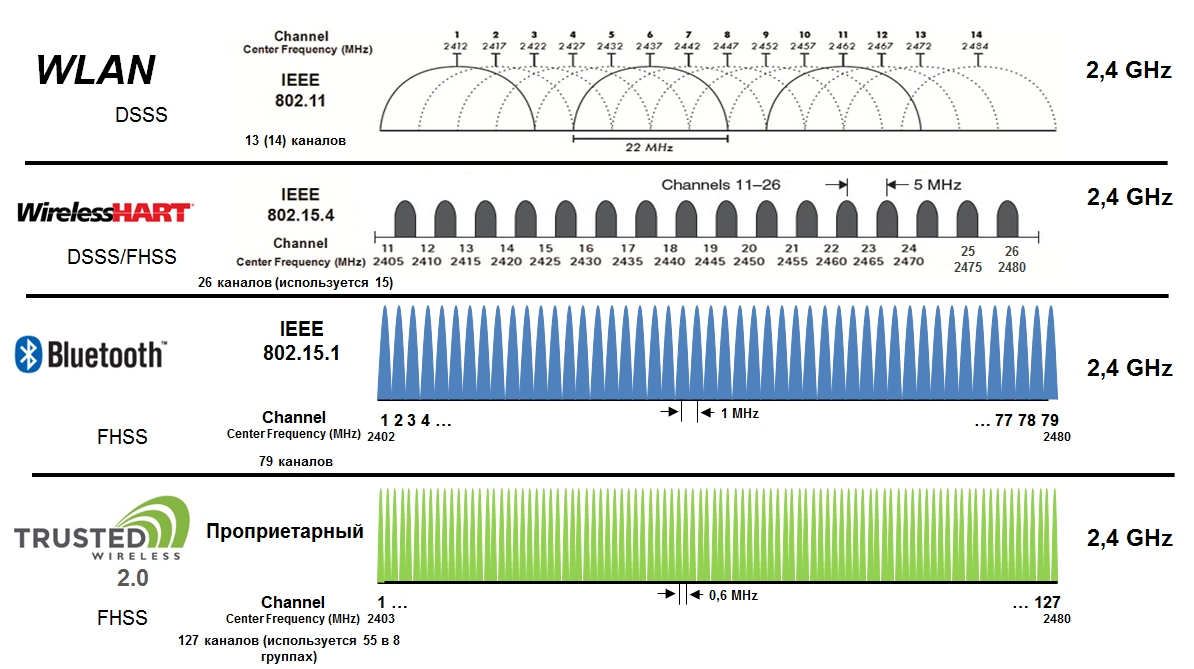
Fig. Signal attenuation due to propagation of radio waves in free space and the occurrence of reflections
In the process of propagation in the transmission medium, the signal weakens due to various external influences. The main factor is the reflections arising during the propagation of radio waves. The signal from the transmitter to the receiver propagates in several directions. In this connection, several waves reach the receiver, which contain the same information, but due to different propagation paths they may have different phases. This can either weaken the signal (when the incoming radio waves are in antiphase), or strengthen (when the phases coincide). Against the background of this problem, FHSS gets an additional advantage - the frequency at which data is transmitted is constantly changing, which automatically solves the physical problem described above. If during the propagation of radio waves in several directions data transmission is impossible on one frequency, then the signal on the next frequency will be strong enough for reception.

Fig. Signal attenuation due to propagation of radio waves in free space and the occurrence of reflections
As mentioned above, interference can only be generated by other systems operating at 2.4 GHz. Due to the fact that wireless networks in the industry are gaining more and more popularity, more and more such systems appear on the sites. Therefore, the issue of ensuring compatibility of wireless networks is very important for the organization of reliable and uninterrupted data transmission.
Worst of all is compatibility with WiFi technology. Due to the fact that WiFi uses only DSSS as a modulation, and the channel has a fairly large width, it is quite problematic to use it simultaneously with other wireless technologies. At the same time, as mentioned above, we can create only three WiFi networks, but this happens only in a perfect world. In reality, in any residential house or shopping center, much more WiFi networks get along, and we get networks that work on overlapping channels, which significantly degrades the quality of communication, and sometimes it also makes it impossible to connect to WiFi.
In top compatibility is Trusted Wireless. This protocol offers a blacklist mechanism in addition to FHSS. This mechanism allows you to put the range of frequencies that are used by other networks in the "black list". The frequencies from this list are not used by Trusted Wireless 2.0 devices, and rebuilding to these frequencies is not performed.
Wireless HART with compatibility matters is also quite good - FHSS is also used, and there is the possibility of using “black lists of channels”, but a small number of channels for frequency tuning prevents it from being as flexible as Bluetooth or Trusted Wireless. In the last two protocols, if there was interference at some frequency, it is possible to switch to many other channels.
Information security is now a very active trend in industrial automation, and this issue cannot be ignored, especially when talking about wireless networks, since information is transmitted via an unprotected interface - in fact, air. It is important to take into account and prevent unauthorized access and transmit data in encrypted form.
Data transmitted over WiFi can be protected using various methods of authentication and encryption (WEP, TKIP, WPA, WPA-2), but there are quite a few different information security threats when using WiFi. And because of the popularity of the protocol, all these methods are very easy to watch, not to mention the multiple video reviews on YouTube. (usually all vulnerabilities are discussed and a large community is always gathered around WiFi hacking)
The Bluetooth connection is protected with a PIN code and encryption. But Bluetooth is sick of the same thing as WiFi. This is a very popular open protocol, and there is a lot of information on how to hack it.
Thanks to the closed technology, the wireless channel based on Trusted Wireless 2.0 is much better protected against possible attacks compared to open protocols.
In addition, Trusted Wireless 2.0 has two security mechanisms: encrypting all transmitted data using the AES-128 protocol and a proprietary authentication protocol that ensures that the message has been received by an authorized recipient due to the fact that this message has a special code that cannot be repeated.
WirelessHART is protected by an AES encryption algorithm with a 128-bit key.
Technologies that use FHSS also receive an additional bonus, since the transition from frequency to frequency occurs by a pseudo-random algorithm, which is determined individually for each connection.
For wireless data transmission, especially for outdoor applications, data transmission distance plays a decisive role. But even in applications where there is no need for data transmission over long distances, a high sensitivity level of the receiver creates a system reserve for data transmission in harsh conditions, for example, data transmission in the absence of direct visibility.
The level of sensitivity affects the speed of data transmission. Each bit is transmitted with a certain transmission power P. The energy per bit is defined by the formula Ebit = P * tbit, where tbit is the transmission time of this bit.
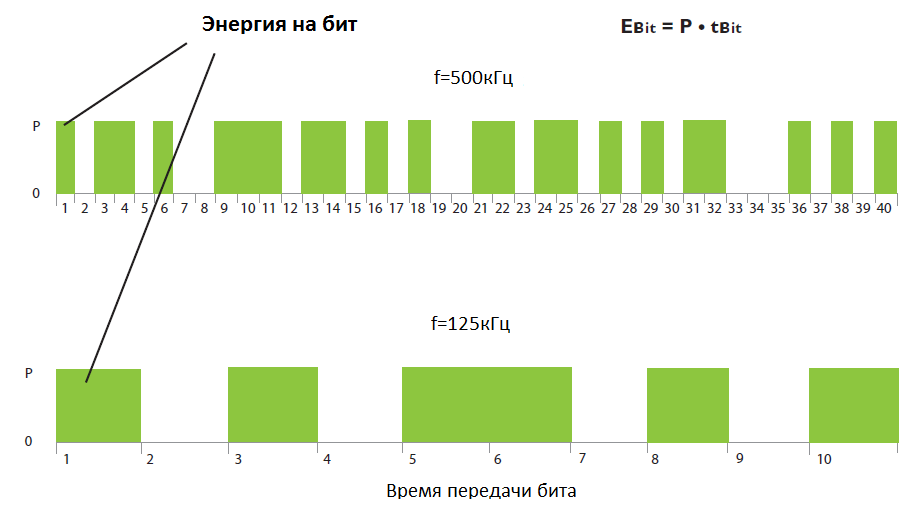
When reducing the data transfer rate - the transmission time of each bit increases, which gives an increase in energy per bit, due to which we get a significant signal gain.
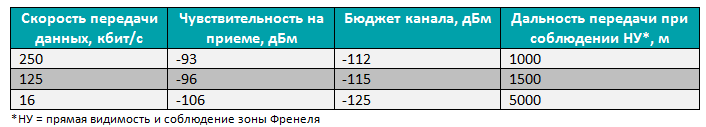
In Trusted Wireless 2.0, the following data transfer rates can be selected:
WiFi, with a data transfer rate of 54 Mbit / s over a wireless network, allows you to transfer data over distances up to 1 km, using a powerful, narrowly focused antenna. If you reduce the speed to 6 Mbps, you can achieve a data transfer distance of 1 km to 2 km.
Bluetooth has more modest speeds compared to WiFi (about 1 Mbit / s), and at the same time data can be transmitted over distances up to 1.5 km.
WirelessHART operates at a data rate of 250 kbps. The average distance is considered to be 255 m. With a directional antenna, distances of about 2 km can also be achieved, but, as a rule, not very powerful non-directional antennas are installed on field sensors or WirelessHART adapters, which give an average distance of 255 m.
The topologies used also have a significant difference.
If we talk about Bluetooth, you can use two topologies: point-to-point and star. Up to 7 devices can be connected to the star.
WiFi offers a richer selection. Traditionally, you can organize a star topology - we all repeatedly created it at home, connecting several devices to a home access point. But you can also create more complex topologies. Some devices can be used in the "bridge" mode, which allows the device to act as a repeater for WiFi. Also now become available devices that allow you to create mesh-networks (about them later) based on WiFi. (e.g. FL WLAN 1100 - 2702534). And WiFi allows you to organize the so-called roaming. Roaming is a network when several access points are set up with the same SSID, and the client can move from one access point to another (adequate WiFi coverage should be provided), while remaining in the same wireless network.
Trusted Wireless 2.0 also allows you to use devices as repeaters and, moreover, to restore communication in the event of a signal break. Those. if the device loses connection, then it searches for another nearest repeater through which data can be transmitted. Thus, the connection is restored, and data begins to be transmitted through the backup channel. Connection recovery takes from milliseconds to seconds - depending on the selected data transfer rate. A similar topology, where communication channels are lined up through randomly selected repeaters, is called a mesh topology.

In addition to mesh topology, devices with Trusted Wireless 2.0 support support point-to-point, star, line topologies.
Due to the high sensitivity level of the receivers of Trusted Wireless 2.0 devices, sometimes the nodes are connected not with the nearest repeaters, but with more distant ones. To avoid such situations, Trusted Wireless 2.0 provides a “blacklist of repeaters” (English parent-black-listing), which identifies the sites with which the connection should not be established. There is also a “white list of repeaters” (English parent-white-listing), which specifies the nodes that are preferred for connection. By default, all repeaters are allowed to connect.
WirelessHART also uses a mesh network to which 254 end sensors can be connected.
Internal data exchange between individual nodes is necessary to support the operation of the wireless network, regardless of the amount of information transmitted. Thus, the process of adding a new node to the network, as well as managing already existing nodes, plays an important role from the point of view of ensuring the reliability of the network and optimizing the transmitted traffic.
WirelessHART uses a centralized node management approach. The network has a "manager" who sends all requests to the nodes and receives responses. Accordingly, this approach creates a large amount of traffic passing through a single network node - the manager.
The same will be true for WiFi and Bluetooth. Here, too, all data exchange goes through access points, and if the access point fails, the devices will no longer be able to exchange data.
Trusted Wireless 2.0, in turn, uses a distributed approach. Network management is divided into zones parent / child (English parent / child, P / C). The parent is the repeater (or the central node of the network), through which other repeaters or heir end devices are connected to the network. Thus, parents and heirs form a tree structure. The parent is responsible for all direct heirs and is responsible for connecting the new heir. All this information is not sent to the central device, but remains within the parent / heir zone, which significantly reduces network traffic.
For example, if it is necessary to connect a new device to the network, this will occur in several stages:
And all these actions are performed within the same P / C zone. For comparison, in WirelessHART, due to the use of a centralized approach, joining a new node to the network requires 6-7 commands. For the simplest point-to-point network, the join operation will take about 2 seconds, and data exchange will begin in 10 seconds. The network, consisting of 100 nodes, will require about 600-700 commands for connection and data exchange, and it will be able to start only after 25 minutes!
Also, within the framework of one P / S zone, the parent device collects diagnostic information from devices of this zone and stores all this information.

Fig. Parent / child partitioning (parent / child - P / C)
Also, this approach significantly reduces the time of network convergence.
If the network with the central control de-energizes the network manager, all information about the connections in this network will be lost, and the network will be restored for quite a long time.
In a network based on Trusted Wireless 2.0, management processes run in parallel in different branches of the tree, which gives significant acceleration when the network is restored.
What do we have in the end? Trusted Wireless and WirelessHART are much slower in speed, but for industrial networks this is not always the most important criterion. Often, wireless technology is needed to expand the cable, which is not possible to lay. In such cases, often the task is to transmit discrete and analog signals, and this does not require high speeds. Or, it is necessary to collect data from some remote installation that communicates via PROFIBUS DP or Modbus RTU — these protocols are also not demanding for data rates in most applications, but the station itself can be far enough. WiFi and Bluetooth do not provide data transmission over long distances. Yes, and setting up WiFi and Bluetooth at distances from 1 km is quite a laborious task. Trusted Wireless, on the contrary, at the expense of low speed, is excellent for long-distance transmissions.
But what is really important for the industry is the reliability of data transfer and its compatibility with existing wireless systems. This is exactly what Trusted Wireless and WirelessHART can boast of — by using FHSS and “blacklists” they are very reliable and allow for very high compatibility with other technologies.
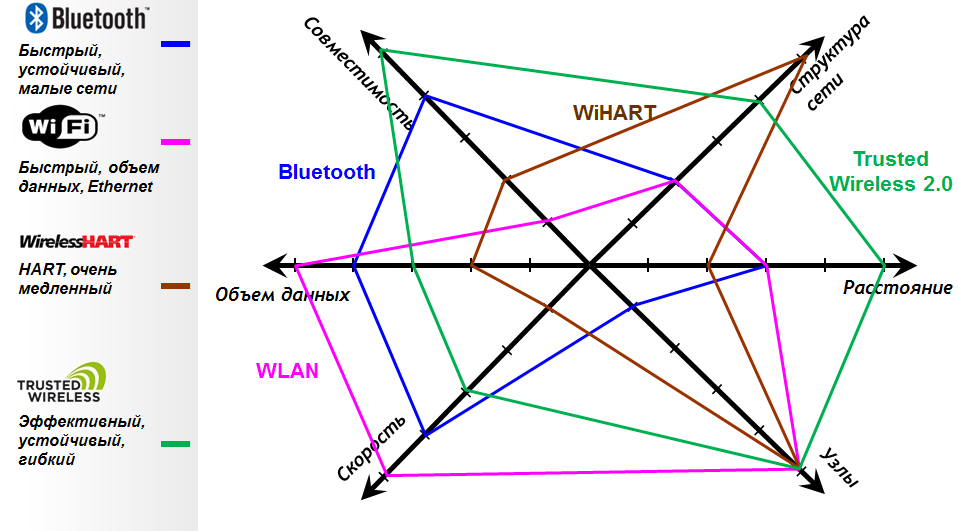
But this does not mean that WiFi or Bluetooth are not used at industrial sites. They are also quite often used, but slightly for other tasks. They allow you to organize data transfer with high speed over short distances, for example: automation of a large warehouse or machine room.
Therefore, it is impossible to give preference to any one technology - each is suitable for its task and most often, they are used together in the framework of a single process control system.
Need help building an industrial network? Come to our site .
For example, in the industry, wireless technologies are also actively gaining momentum, but in addition to the usual WiFi, Bluetooth and other modern technologies, it is often possible to find, at first glance, exotic protocols at industrial sites. For example, WirelessHART or Trusted Wireless 2.0, transmitting data at a maximum speed of 250 kbps. First you start to think that these are some outdated technologies and you need to switch to WiFi and other “fast” protocols. But is this fair for industry? Let's see.
Compare the four technologies - WiFi, Bluetooth, Trusted Wireless 2.0 and WirelessHART. All technologies will be considered at 2.4 GHz. Other frequencies for the Russian Federation are not very relevant (well, except 5 GHz, but this frequency range only supports WiFi).
')
We will compare according to several criteria:
- reliability of data transmission;
- compatibility with other wireless networks;
- data transmission security;
- data transmission distance;
- network structure;
- the nature of the interaction of network nodes.
The comparison is theoretical.
Reliability of data transmission
The first thing that questions arise when thinking about network organization using wireless technologies is the reliability of data transfer. By reliability of data transfer, I propose to understand data transfer with a permanent connection and without data loss.
Data loss and connection failure can be caused by two main factors:
- electromagnetic interference;
- attenuation due to the propagation of radio waves in free space and the occurrence of reflections.
Electromagnetic interference
Electromagnetic interference at an industrial facility is generated, first of all, by frequency converters, electric drives and other primary equipment. Such interference has a frequency range that is a multiple of kHz or MHz. And all the technologies that we have taken for comparison, operate at a frequency of 2.4 GHz. Interference from primary equipment simply does not reach this range. Thus, other wireless systems transmitting data at 2.4 GHz become a source of interference. There are two completely different approaches to ensure the electromagnetic compatibility of these systems:
- use of broadband modulation with direct spread spectrum (Direct Sequence Spread Spectrum - DSSS);
- the use of pseudo-random adjustment of the operating frequency (Frequency Hopping Spread Spectrum - FHSS).
When using DSSS, a useful signal passes through a spreading code generator, where one bit of useful information is replaced with N bits, which increases the clock frequency by N times. This affects the spread of the spectrum also N times. At the receiver, this signal passes through the same generator and decoding information occurs. The advantage of this approach is the ability to transfer data at very high speeds. The signal occupies a certain frequency band and narrowband interference distorts only certain frequencies of the spectrum, but there is enough information to reliably decode the signal. But after a certain threshold of the frequency spectrum of the interference frequency, the signal will be impossible to decode. The generator simply does not understand where the useful signal is, and where is the superimposed one.

DSSS
When using FHSS, the data transmission frequency changes in a pseudo-random order. In this case, the resulting interference will affect only one of the random frequencies, regardless of the width of the spectrum.

Fhss
Thus, if serious electromagnetic interference occurs in the FHSS system, some data will be lost, and in the DSSS system, data transmission will stop completely.
WiFi uses DSSS. The width of one channel is 22 MHz and, accordingly, 14 WiFi channels are available on the 2.4 GHz band. Only 13 are available in Russia. At the same time, 3 non-overlapping channels are available for use. Surely, many of you have watched a picture of WiFi at home completely. This can happen just because a neighbor has an access point operating on the same channel as your point, or on an overlapping channel.
Bluetooth uses FHSS technology. The width of one channel is 1 MHz. 79 channels are available for rebuilding and access. As with WiFi, a different number of channels may be available in different countries.
Wireless HART uses a combination of FHSS and DSSS. The width of one channel is 2 MHz and all channels are located on a width of 5 MHz, i.e. 16 channels are available, and they are all non-overlapping.
Trusted Wireless 2.0 uses FHSS technology. Devices are available 127 channels for adjustment. The number of frequencies available for selection by a specific device depends on the “blacklist of frequencies”, which is configured in order to ensure compatibility with other wireless systems, and whether special frequency bands (RF band) are used to optimize the wireless network.

Fig. Signal attenuation due to propagation of radio waves in free space and the occurrence of reflections
In the process of propagation in the transmission medium, the signal weakens due to various external influences. The main factor is the reflections arising during the propagation of radio waves. The signal from the transmitter to the receiver propagates in several directions. In this connection, several waves reach the receiver, which contain the same information, but due to different propagation paths they may have different phases. This can either weaken the signal (when the incoming radio waves are in antiphase), or strengthen (when the phases coincide). Against the background of this problem, FHSS gets an additional advantage - the frequency at which data is transmitted is constantly changing, which automatically solves the physical problem described above. If during the propagation of radio waves in several directions data transmission is impossible on one frequency, then the signal on the next frequency will be strong enough for reception.

Fig. Signal attenuation due to propagation of radio waves in free space and the occurrence of reflections
Compatible with other wireless networks
As mentioned above, interference can only be generated by other systems operating at 2.4 GHz. Due to the fact that wireless networks in the industry are gaining more and more popularity, more and more such systems appear on the sites. Therefore, the issue of ensuring compatibility of wireless networks is very important for the organization of reliable and uninterrupted data transmission.
Worst of all is compatibility with WiFi technology. Due to the fact that WiFi uses only DSSS as a modulation, and the channel has a fairly large width, it is quite problematic to use it simultaneously with other wireless technologies. At the same time, as mentioned above, we can create only three WiFi networks, but this happens only in a perfect world. In reality, in any residential house or shopping center, much more WiFi networks get along, and we get networks that work on overlapping channels, which significantly degrades the quality of communication, and sometimes it also makes it impossible to connect to WiFi.
In top compatibility is Trusted Wireless. This protocol offers a blacklist mechanism in addition to FHSS. This mechanism allows you to put the range of frequencies that are used by other networks in the "black list". The frequencies from this list are not used by Trusted Wireless 2.0 devices, and rebuilding to these frequencies is not performed.
Wireless HART with compatibility matters is also quite good - FHSS is also used, and there is the possibility of using “black lists of channels”, but a small number of channels for frequency tuning prevents it from being as flexible as Bluetooth or Trusted Wireless. In the last two protocols, if there was interference at some frequency, it is possible to switch to many other channels.
Data transfer security
Information security is now a very active trend in industrial automation, and this issue cannot be ignored, especially when talking about wireless networks, since information is transmitted via an unprotected interface - in fact, air. It is important to take into account and prevent unauthorized access and transmit data in encrypted form.
Data transmitted over WiFi can be protected using various methods of authentication and encryption (WEP, TKIP, WPA, WPA-2), but there are quite a few different information security threats when using WiFi. And because of the popularity of the protocol, all these methods are very easy to watch, not to mention the multiple video reviews on YouTube. (usually all vulnerabilities are discussed and a large community is always gathered around WiFi hacking)
The Bluetooth connection is protected with a PIN code and encryption. But Bluetooth is sick of the same thing as WiFi. This is a very popular open protocol, and there is a lot of information on how to hack it.
Thanks to the closed technology, the wireless channel based on Trusted Wireless 2.0 is much better protected against possible attacks compared to open protocols.
In addition, Trusted Wireless 2.0 has two security mechanisms: encrypting all transmitted data using the AES-128 protocol and a proprietary authentication protocol that ensures that the message has been received by an authorized recipient due to the fact that this message has a special code that cannot be repeated.
WirelessHART is protected by an AES encryption algorithm with a 128-bit key.
Technologies that use FHSS also receive an additional bonus, since the transition from frequency to frequency occurs by a pseudo-random algorithm, which is determined individually for each connection.
Data transmission range
For wireless data transmission, especially for outdoor applications, data transmission distance plays a decisive role. But even in applications where there is no need for data transmission over long distances, a high sensitivity level of the receiver creates a system reserve for data transmission in harsh conditions, for example, data transmission in the absence of direct visibility.
The level of sensitivity affects the speed of data transmission. Each bit is transmitted with a certain transmission power P. The energy per bit is defined by the formula Ebit = P * tbit, where tbit is the transmission time of this bit.

When reducing the data transfer rate - the transmission time of each bit increases, which gives an increase in energy per bit, due to which we get a significant signal gain.
In Trusted Wireless 2.0, the following data transfer rates can be selected:

WiFi, with a data transfer rate of 54 Mbit / s over a wireless network, allows you to transfer data over distances up to 1 km, using a powerful, narrowly focused antenna. If you reduce the speed to 6 Mbps, you can achieve a data transfer distance of 1 km to 2 km.
Bluetooth has more modest speeds compared to WiFi (about 1 Mbit / s), and at the same time data can be transmitted over distances up to 1.5 km.
WirelessHART operates at a data rate of 250 kbps. The average distance is considered to be 255 m. With a directional antenna, distances of about 2 km can also be achieved, but, as a rule, not very powerful non-directional antennas are installed on field sensors or WirelessHART adapters, which give an average distance of 255 m.
Network structure
The topologies used also have a significant difference.
If we talk about Bluetooth, you can use two topologies: point-to-point and star. Up to 7 devices can be connected to the star.
WiFi offers a richer selection. Traditionally, you can organize a star topology - we all repeatedly created it at home, connecting several devices to a home access point. But you can also create more complex topologies. Some devices can be used in the "bridge" mode, which allows the device to act as a repeater for WiFi. Also now become available devices that allow you to create mesh-networks (about them later) based on WiFi. (e.g. FL WLAN 1100 - 2702534). And WiFi allows you to organize the so-called roaming. Roaming is a network when several access points are set up with the same SSID, and the client can move from one access point to another (adequate WiFi coverage should be provided), while remaining in the same wireless network.
Trusted Wireless 2.0 also allows you to use devices as repeaters and, moreover, to restore communication in the event of a signal break. Those. if the device loses connection, then it searches for another nearest repeater through which data can be transmitted. Thus, the connection is restored, and data begins to be transmitted through the backup channel. Connection recovery takes from milliseconds to seconds - depending on the selected data transfer rate. A similar topology, where communication channels are lined up through randomly selected repeaters, is called a mesh topology.

In addition to mesh topology, devices with Trusted Wireless 2.0 support support point-to-point, star, line topologies.
Due to the high sensitivity level of the receivers of Trusted Wireless 2.0 devices, sometimes the nodes are connected not with the nearest repeaters, but with more distant ones. To avoid such situations, Trusted Wireless 2.0 provides a “blacklist of repeaters” (English parent-black-listing), which identifies the sites with which the connection should not be established. There is also a “white list of repeaters” (English parent-white-listing), which specifies the nodes that are preferred for connection. By default, all repeaters are allowed to connect.
WirelessHART also uses a mesh network to which 254 end sensors can be connected.
The nature of the interaction of network nodes
Internal data exchange between individual nodes is necessary to support the operation of the wireless network, regardless of the amount of information transmitted. Thus, the process of adding a new node to the network, as well as managing already existing nodes, plays an important role from the point of view of ensuring the reliability of the network and optimizing the transmitted traffic.
WirelessHART uses a centralized node management approach. The network has a "manager" who sends all requests to the nodes and receives responses. Accordingly, this approach creates a large amount of traffic passing through a single network node - the manager.
The same will be true for WiFi and Bluetooth. Here, too, all data exchange goes through access points, and if the access point fails, the devices will no longer be able to exchange data.
Trusted Wireless 2.0, in turn, uses a distributed approach. Network management is divided into zones parent / child (English parent / child, P / C). The parent is the repeater (or the central node of the network), through which other repeaters or heir end devices are connected to the network. Thus, parents and heirs form a tree structure. The parent is responsible for all direct heirs and is responsible for connecting the new heir. All this information is not sent to the central device, but remains within the parent / heir zone, which significantly reduces network traffic.
For example, if it is necessary to connect a new device to the network, this will occur in several stages:
- device search for the nearest station, i.e. the device will "listen" to the broadcast;
- synchronization with the station selected for data transmission;
- transition to the FHSS algorithm used by this device;
- sending a connection request (English join-request);
- receipt of connection confirmation (English join-acknowledge).
And all these actions are performed within the same P / C zone. For comparison, in WirelessHART, due to the use of a centralized approach, joining a new node to the network requires 6-7 commands. For the simplest point-to-point network, the join operation will take about 2 seconds, and data exchange will begin in 10 seconds. The network, consisting of 100 nodes, will require about 600-700 commands for connection and data exchange, and it will be able to start only after 25 minutes!
Also, within the framework of one P / S zone, the parent device collects diagnostic information from devices of this zone and stores all this information.

Fig. Parent / child partitioning (parent / child - P / C)
Also, this approach significantly reduces the time of network convergence.
If the network with the central control de-energizes the network manager, all information about the connections in this network will be lost, and the network will be restored for quite a long time.
In a network based on Trusted Wireless 2.0, management processes run in parallel in different branches of the tree, which gives significant acceleration when the network is restored.
Conclusion
What do we have in the end? Trusted Wireless and WirelessHART are much slower in speed, but for industrial networks this is not always the most important criterion. Often, wireless technology is needed to expand the cable, which is not possible to lay. In such cases, often the task is to transmit discrete and analog signals, and this does not require high speeds. Or, it is necessary to collect data from some remote installation that communicates via PROFIBUS DP or Modbus RTU — these protocols are also not demanding for data rates in most applications, but the station itself can be far enough. WiFi and Bluetooth do not provide data transmission over long distances. Yes, and setting up WiFi and Bluetooth at distances from 1 km is quite a laborious task. Trusted Wireless, on the contrary, at the expense of low speed, is excellent for long-distance transmissions.
But what is really important for the industry is the reliability of data transfer and its compatibility with existing wireless systems. This is exactly what Trusted Wireless and WirelessHART can boast of — by using FHSS and “blacklists” they are very reliable and allow for very high compatibility with other technologies.

But this does not mean that WiFi or Bluetooth are not used at industrial sites. They are also quite often used, but slightly for other tasks. They allow you to organize data transfer with high speed over short distances, for example: automation of a large warehouse or machine room.
Therefore, it is impossible to give preference to any one technology - each is suitable for its task and most often, they are used together in the framework of a single process control system.
Need help building an industrial network? Come to our site .
Source: https://habr.com/ru/post/441146/
All Articles