SITIS CTF: how a seal helped CTF win

On January 27, 2019, the SITIS CTF event was held - a competition in information security for schoolchildren and students of technical colleges. The tournament was attended by about 80 young professionals and one seal. The game was held in the office of Jet Infosystems, the organizer of the tasks and the technical platform was made by the young team of SITIS .
CTF
The event format is task-based CTF (jeopardy), in which players solve tasks (tasks) of various levels of complexity. The answer may be a character set or an arbitrary phrase. For each correct answer (capture of the flag), participants receive a certain number of points. Access to part of the task is opened only after the decision of the previous ones.
The participants of the CTF-game managed to solve almost all the tasks, but two of them did not succumb: the fatigue most likely affected - the hackers and brains were broken by young hackers and hackers from morning to evening.
Tasks
PPC
Chain (200 points)
The participants were provided with a set of pixels specially translated into hex, among which was a chain of key pixels. By translating hex into a picture, you could get an image with a flag.
Painting (200 points)
The participants were provided with an archive containing about 1600 monochrome images with the image of 75 byte digits. The way to get the flag is to add the numbers in the pictures using zeros as separators and translate the resulting list into a string representation.
Kotorova (250 points)
See the Vraytaps section.
Music (300 points)
See the Vraytaps section.
REVERSE
Razminka (75 points)
Participants needed initial reversing skills, the password was stored as char variables in the main class.
My creation! (250 points)
See the Vraytaps section.
CRYPTO
Strange dream (100 points)
See the Vraytaps section.
Hmmmmmmm (150 points)
See the Vraytaps section.
JOY
a (25 points)
Participants had to find a flag written in small print on one of the frames in the gif with cats.
Snowflakes (75 points)
Participants were provided with an html file with obfuscated javascript code. It was necessary to compose a flag from characters slowly falling on the page.
Flag Among Us (100 points)
A picture was attached to the task.

First of all, everyone rushed to look for the flag in the image. Having rummaged in it and making sure that the flag is not there, it was worth returning to the description and name of the task and carefully read them again. The fact is that at the very competition, on the doors of the premises where the event was held, there were unusual stickers with QR codes.

')
By collecting all the pieces, you could get the phrase HRGRH {9I3371M95_7i4e3o3i}. Here the flag is obviously traced, but it is encrypted. They were given not so many points for the task, so it would be logical that the cipher should not be complicated. Looking through the main options one could come to the conclusion that Atbash was here. SITIS flag {9R3371N95_7r4v3l3r}.
STEGO
Bug or feature? (50 points)
A text document was attached to the task, in which, at first glance, there were only 2 lines. However, after looking and highlighting the text, you could see a lot of spaces and tabs on 39 lines. Those who have already encountered this, should not have made it difficult to get a flag.
Poetry (75 points)
Participants were given a picture depicting a frame from the movie "Imitation Game". It was necessary to find the original picture and compare them, and from the different pixels to create a new picture with the verses of Byron, whose surname was the flag.
STORY
Welcome (50 points)
Droids are everywhere (100 points)
It's time to air (105 points)
Help is not superfluous (125 points)
It is necessary to play stag (150 points)
First Field Test (175 points)
The fun begins p1 (200 points)
The fun begins p2 (205 points)
Final Boss (300 points)
Within the framework of the block, participants had to unravel several related tasks.
The point was to provide the participants with an archive of various files, but they needed to find coordinates in the meta-information. The tip was told that the author has topographical cretinism, so you need to swap latitude and longitude and get a flag in the form of the name of the lake.
In the second task, it was necessary to find a file with a flag in the file system. There was also a link that opened access to task 3. Next, the flag had to be found on the saved page in the web archive. In the following tasks, participants had to figure out a popular hacker from a video on Youtube (the flag was his name and surname), to find his account on some hacker forum, where the flag and hint on the site hacking were located. Then it was necessary to conduct an attack on the CTfOS website (find the hash password in the cookie md5 and get the original password using any service, the flag was the admin + password pair).
Next, it was necessary to connect via ssh, see the archive, download it via sftp, find the password, find out that instead of the image there was actually an archive, and get the flag. At the end, the port number was “65530”, it was necessary to pick up a password (rockyou dictionary), then format the system and provide evidence to the organizers.
Sitis
- INSTA (100 points)
For successful passing it was necessary to make an Instagram post with a photo of CTF and thematic hashtags. - MINI-POLL (125 points)
As part of the task, participants underwent a mini-survey.
Vrytapy
Here are a few analyzes of interesting tasks from the participants of CTF.
Kotorova

Kotorova, emphasis on the third "o". Task for 250 points out of 300 possible. The player is given a picture (see above) and a strange text consisting of the words “Miu”, “Meow”, “FRD” and “Face”.

By visual analysis of the picture (and curiosity in the past), we understand that the source text is nothing but the COW language with replaced operators. Having made the following replacements, you can get the "cow" message: Miu => MOo, Meow => MoO, FRR => OOO, Lik => Moo. We run the resulting code through an online interpreter and get the coveted token:

Weird dream…
Oddly enough, but the idea of this task really came to mind of one of the organizers after waking up one cold January morning. Description of task:
I then dreamed of a task, check for decisiveness pzh: 3
It is easy to guess from the title and description that the reference goes to Dmitriy Ivanovich, namely Mendeleev. Now let's see what we have in the file:
0x53 0x49 0x54 0x49 0x53 0x7b 0x6d 0x65 Mx3c 0x65 0x6c 0x65 0x65 Mx17 0x5f 0x65 Mx21 Mx27 0x5f Mx4b Mxf Mx39 Mx3a 0x6d 0x65 Mx7 Mx75 0x7d Hex, but with strange prefixes "M" in some places.
We translate HEX to ASCII and immediately get, at first glance, a broken flag:

Transferring only Hex with the prefix “M” to the decimal number system, we get the following sequence:
60 23 33 39 75 15 57 58 7 117 Remember about the description.
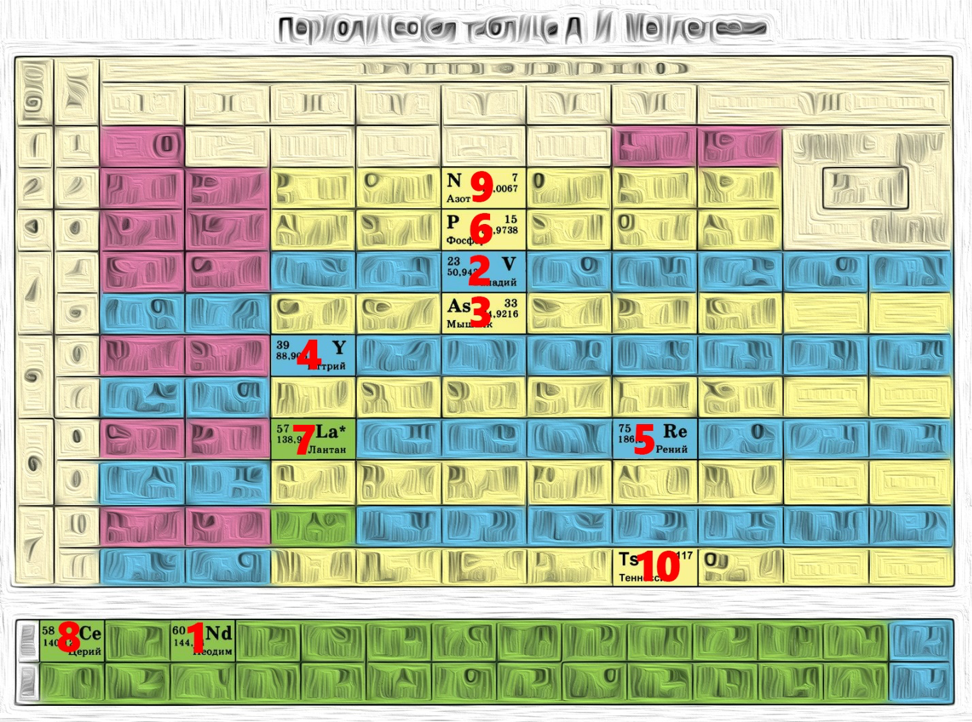
Combine ASCII HEX with Mendeleev's and get the flag.
Music
We thought about how to translate text into notes for a long time, and finally the idea was implemented:
First of all, it was decided to translate the text into a numeric representation using ord ()
awsm_msic
The space is left intentionally at first, so that the last bits do not spoil the last character.
ord(): [97, 119, 115, 109, 95, 109, 115, 105, 99, 32] Then translate it into bytes:
>>bin(): ['01100001', '01110111', '01110011', '01101101', '01011111', '01101101', '01110011', '01101001', '01100011', '00100000'] Concatenate:
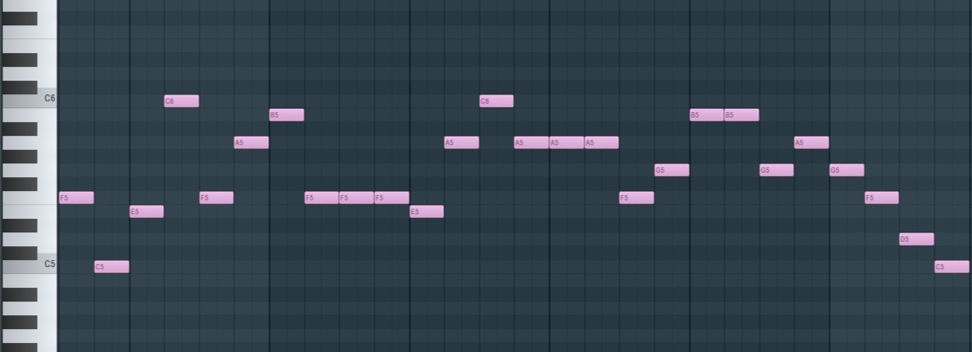
concatenate:01100001011101110111001101101101010111110110110101110011011010010110001100100000 Break the resulting text into symbols of three (triplets). Since we can encode 8 numbers in the range from 000 to 111, we will use the set of octaves C5 and C6, consisting of 8 notes:
['011', '000', '010', '111', '011', …] ["C5","D5","E5","F5","G5","A5","B5","C6"] It remains quite a bit, we translate the triplets back into the decimal number system and compile a new list based on the indices of the notes:
['F5', 'C5', 'E5', 'C6', 'F5', 'A5', 'B5', 'F5', 'F5', 'F5', 'E5', 'A5', 'C6', 'A5', 'A5', 'A5', 'F5', 'G5', 'B5', 'B5', 'G5', 'A5', 'G5', 'F5', 'D5', 'C5'] We write a MIDI file, if you wish, you can use any instrument to make the notes sound.
Reverse 250
First of all, we disassemble the program (using IDA), convert to C and look for suspicious lines:
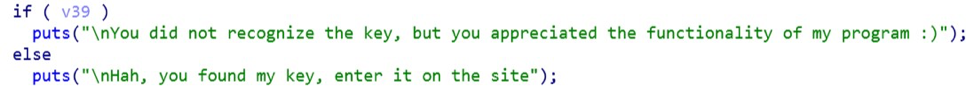
It can be concluded that v39 is a flag that in the “false” state will give us the desired string.
We look, where there is a change of a flag:
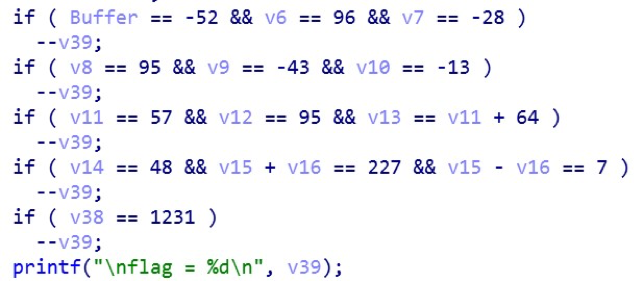
Looking at this code, it is difficult to determine with which variables we need to make changes in order for the flag to be decremented. Clicking twice on the variable Buffer, we get into the program's stack viewing window. We have to understand that Buffer is a string (since we can enter anything into the program), which means we will set such a size that all the var_xxx variables are in it:
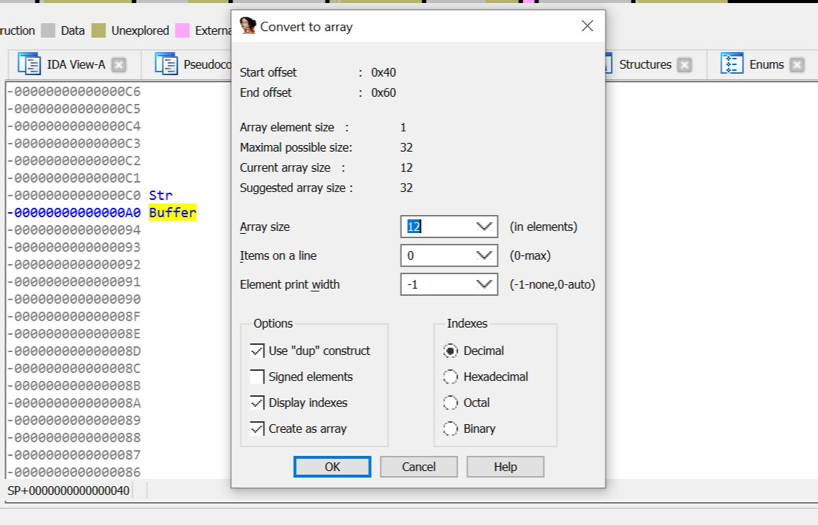
Read the code has become much easier:
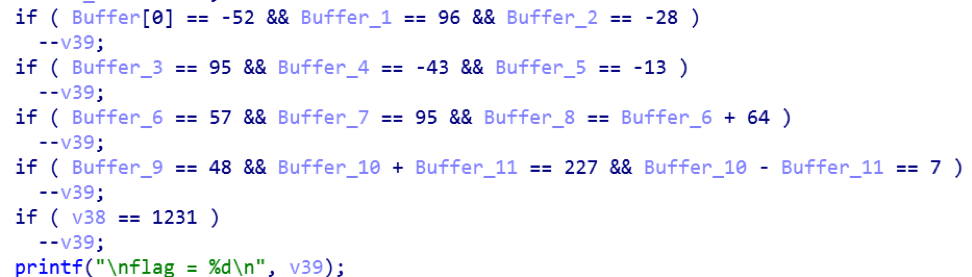
Now we will consider the block of change of characters of our line.
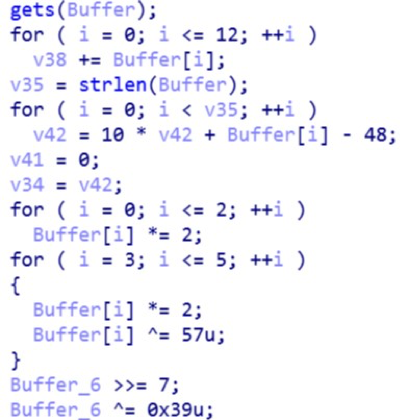
Analyzing:
- v38 - the sum of the values of character variables (according to condition 1231).
- 7 line element (Buffer_6) is shifted by 7 bits, i.e. it is impossible to perform the inverse transformation (whatever number is converted here, the result will be 0).
- The loop with v35, v41, v34 variables is used to divert attention (copies the value of one string to another to preserve the correct translation from the binary to the hexadecimal system, since we change the source string).
- The loop with the first three characters is a simple multiplication by 2.
- From fourth to sixth - a little harder. It is necessary to solve the equation (for the fourth character it will look like this: (x * 2) ^ 57 = 95). Although XOR is an irreversible operation, it is quite possible to select a value using brute force, and even with initial skills, this can be done in a few seconds.
- The changes are over, we return to the block of conditions and compose simple equations for the remaining elements.
We have (x - unknown, 0 - known): 000000x00000x. The sum of the values = 1231. We subtract the known ones from this number and get the sum of the unknown numbers = 164. So, we take any two characters whose sum will be equal to 164. Based on the meaning of the first word, let it be 'R' and 'R'.

After the introduction of the key we get our desired phrase.
Hmmmmm
When opening a task, we get two files: data.txt and Hmmmm.png:

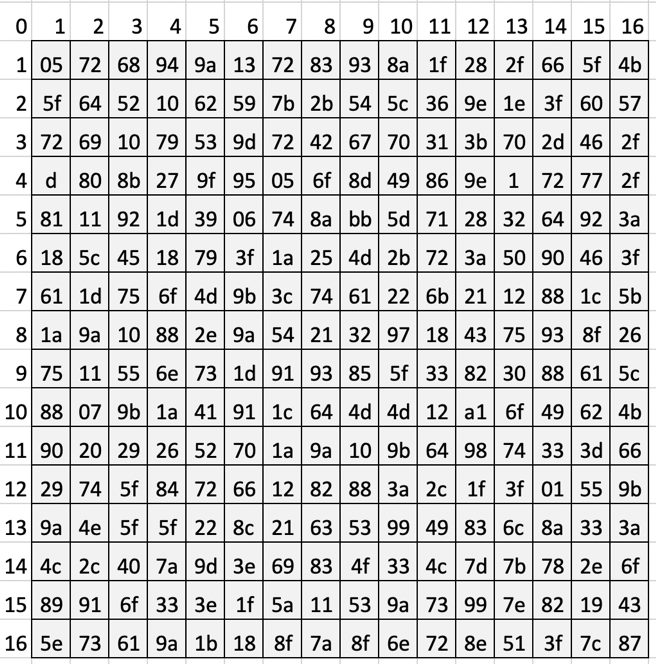
Obviously, the first line in a text file is some kind of encoding. Indeed, this is an ordinary Base64, albeit without its “=” sign at the end.
Having decoded, we see the numbers suspiciously similar to degrees:
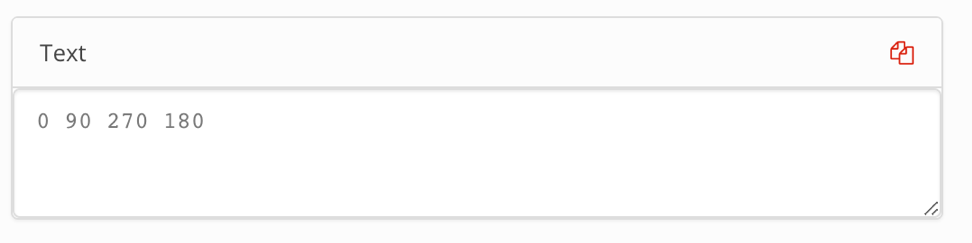
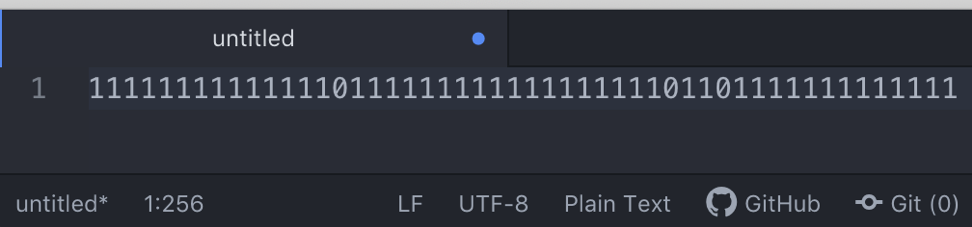
Already at this point, you can guess that we are talking about a certain lattice and its angle of inclination. But where is the stencil itself? Of course, we still have a binary set of numbers, in which the overwhelming number is 1 and only 8 zeros.
Test the hypothesis is very simple. The atom says we have 256 characters. Just as much as in the table in the photo, and from this we can also guess that the lattice is square.
Probably the most convenient way to use Excel is to draw a grid. So do.
Actually, here it is:
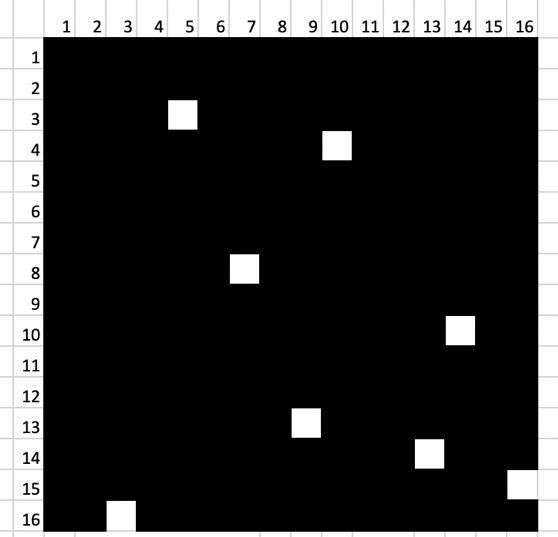
Suppose, and for good reason, that this is a given position of the lattice with respect to 0 degrees. Then with the help of manipulations in Excel or Photoshop, write down the numbers from the windows:
What could it be for numbers? Hexadecimal system ... Hex, of course!
Hooray, we are on the right track, it remains to turn the lattice and write out the remaining numbers:
It turns out that the desired sequence is in blue cells, that is:
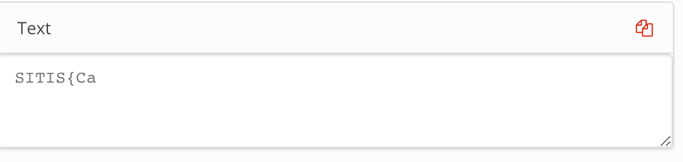
53 49 54 49 53 7b 43 61 72 64 61 6e 6f 5f 69 73 5f 70 72 6f 75 64 5f 6f 66 5f 79 6f 75 5f 21 7d 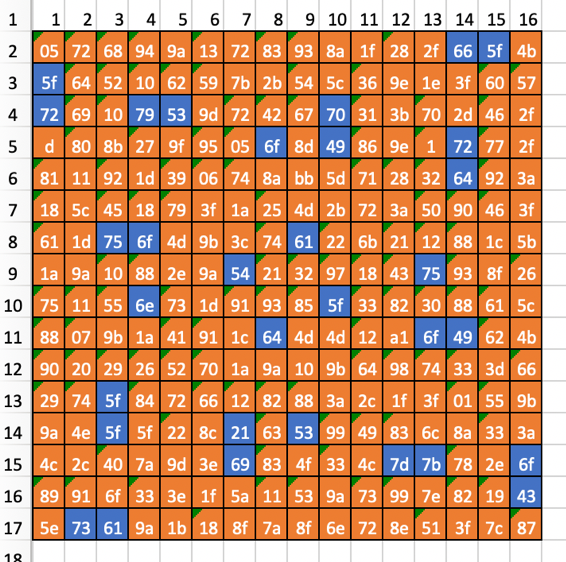
As a result, we get: SITIS {Cardano_is_proud_of you !}
Yes, yes, this is only the Cardano lattice, proposed by him in the 16th century. One of the simplest cryptographic algorithms.
Nevertheless, despite the seeming simplicity and obviousness of the task, only one team, “10x”, was able to solve it, even despite these hints:


Members
The participants of the competition were both hardened CTFs and beginners.
1st place, MLPWN:
My team liked. As for the assignments, we, as a fairly experienced team, were not very difficult to solve them, it was noticeable that the assignments were designed for beginners, they didn’t meet the idea of a complex cruel task, how many messages to interest, which is very cool. As for the organization, everything was at the highest level, which, frankly, is not always found on school courses. Good luck to the SITIS team in organizing the following SITIS CTF!
2 place, 10x
3rd place, Inview:
This was my first exit CTF, as I had previously participated only in CTF within SPB. Tasks were quite interesting and difficult, but the only problem that was often simple was the fall of the Internet. I would love to come next year and hope that SITIS CTF will only improve. I wish the organizers success both in competitions and in organizing such events.

The winner was the team MLPWN - My Little Pony (Pwnie).
There were quite a few girls among the participants =)

The struggle was serious, sometimes the help of the organizers was needed:

The organizers
The organizer of the event is a young SITIS team. CTF partners were Jet Infosystems (general partner of SITIS CTF ), Group-IB, Elefus, BCS, and FSBI Voskhod.

For those who came for the seal. He was spotted in the winning team. I think it was a sign.
LV: tell a few words about your mascot - seal =)
lithium: in fact, this is not quite our mascot c: We gathered this team relatively recently, before that everyone (well, almost all) were in different teams or had no team at all. Theodore was on the SEAL team, whose seal was the mascot. Theodore dragged him. We actually expected him to bring his pony, which he won in Sirius as Pwnie Award)

Seal says: don't be a seal, play CTF, swing your skills!
The publication retains punctuation and spelling of CTF members.
Source: https://habr.com/ru/post/437996/
All Articles