MIT course "Computer Systems Security". Lecture 23: "The Economics of Security", part 3
Massachusetts Institute of Technology. Lecture course # 6.858. "Security of computer systems". Nikolai Zeldovich, James Mykens. year 2014
Computer Systems Security is a course on the development and implementation of secure computer systems. Lectures cover threat models, attacks that compromise security, and security methods based on the latest scientific work. Topics include operating system (OS) security, capabilities, information flow control, language security, network protocols, hardware protection and security in web applications.
Lecture 1: "Introduction: threat models" Part 1 / Part 2 / Part 3
Lecture 2: "Control of hacker attacks" Part 1 / Part 2 / Part 3
Lecture 3: "Buffer overflow: exploits and protection" Part 1 / Part 2 / Part 3
Lecture 4: "Separation of privileges" Part 1 / Part 2 / Part 3
Lecture 5: "Where Security Errors Come From" Part 1 / Part 2
Lecture 6: "Opportunities" Part 1 / Part 2 / Part 3
Lecture 7: "Sandbox Native Client" Part 1 / Part 2 / Part 3
Lecture 8: "Model of network security" Part 1 / Part 2 / Part 3
Lecture 9: "Web Application Security" Part 1 / Part 2 / Part 3
Lecture 10: "Symbolic execution" Part 1 / Part 2 / Part 3
Lecture 11: "Ur / Web programming language" Part 1 / Part 2 / Part 3
Lecture 12: "Network Security" Part 1 / Part 2 / Part 3
Lecture 13: "Network Protocols" Part 1 / Part 2 / Part 3
Lecture 14: "SSL and HTTPS" Part 1 / Part 2 / Part 3
Lecture 15: "Medical Software" Part 1 / Part 2 / Part 3
Lecture 16: "Attacks through the side channel" Part 1 / Part 2 / Part 3
Lecture 17: "User Authentication" Part 1 / Part 2 / Part 3
Lecture 18: "Private Internet browsing" Part 1 / Part 2 / Part 3
Lecture 19: "Anonymous Networks" Part 1 / Part 2 / Part 3
Lecture 20: “Mobile Phone Security” Part 1 / Part 2 / Part 3
Lecture 21: “Data Tracking” Part 1 / Part 2 / Part 3
Lecture 22: MIT Information Security Part 1 / Part 2 / Part 3
Lecture 23: "Security Economics" Part 1 / Part 2
The lecture article talks about various retaliation strategies that can stop a spammer. The authors noticed that there is a limited number of domain name registrars for affiliate programs. This means that the majority of affiliate partners are individually associated with the registrar who deals with their domain names and infrastructure. It is very rare when one domain name registrar is associated with a bunch of different affiliate programs.
')
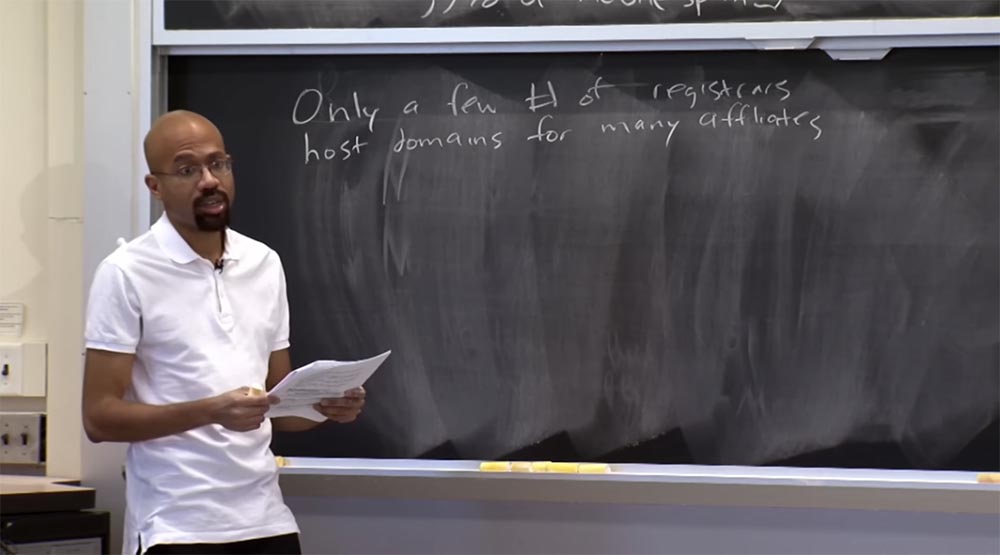
This means that there is no common center, a common registrar, striking a blow at which one could disable the entire spam infrastructure. A similar scheme applies to such things as web servers. It’s rare for one ISP provider to own a bunch of web servers with a bunch of affiliate programs. This business has a distributed nature, so it is very difficult to say that if we “take” these 3 providers, the entire spam ecosystem will be destroyed.
Therefore, it is a pity that there is no single server that could be hit to stop spamming. Later we will see that this may work in relation to some shadow banking schemes, so maybe we can still put pressure on the spammer.
Let's go back to reviewing the spam implementation stage and see what happens after you, the user, decide to buy something. The implementation phase consists of two parts.
The user pays for any goods that he buys or wants to buy, and then, I hope, receives these goods either by mail, as in the case of buying counterfeit drugs, or downloads from the Internet if he wants to get a pirated Photoshop or something like that.

Cash flow looks like this. The customer turns to the seller and tells him that he wants to buy something. He sends the credit card information, after which the seller communicates with the payment processor Payment processor. This is an important mediator who helps the seller, the spammer, deal with some of the subtleties of interaction with the credit card system. The payment processor is associated with the service bank.
The servicing bank performs all operations related to the execution of settlements and payments by bank cards. He is associated with what is called the “associated network” in the article, but we will think of it simply as the Visa or MasterCard payment system, so these are just credit card networks.
Finally, these Association networks, or card networks, communicate with the issuing bank of the buyer. In fact, they ask for information whether the transaction is legal, that is, it happens with the consent of the cardholder. If so, the money goes through the whole system and goes to the seller. This is what the end-to-end financial workflow looks like. This workflow can handle big bucks. One of the articles mentioned in the lecture material says that one partner may receive more than $ 10 million dollars as a result of such a transaction. The question arises why the acquiring bank or the issuing bank will not report that there is something wrong here? As it turns out, in many cases they don’t really report anything.

I wonder why the financial system tolerates such processes. For example, why do spammers classify their deals correctly? When you want to send something through this system, you must correctly identify the type of transaction being conducted, indicating that you are selling pharmaceuticals, software, anything, it does not matter. It can be assumed that a spammer selling fake vitamins will not want to indicate that he is in the pharmaceutical business. However, it is interesting that spammers in most cases correctly classify transactions. The reason is that for a wrong classification can be awarded a high fine.
Therefore, associated networks such as Visa or Mastercard consider that everything is in order with such transactions, even if they look a bit suspicious. But they do not want to be accused of money laundering or trying to deceive the authorities. As long as you properly classify what you are doing, then you are in a certain sense defending yourself. Because you can always tell the authorities that you did not understand the law a bit, but at least you did not try to hide the purpose of this transaction. Thus, spammers often classify their transactions correctly, that is, they play a certain measure within the system.
Another question I mentioned earlier is why should a spammer send something to customers? Presumably, if you're a spammer, then you're a criminal, right? So why not just collect money from the people and not run away with them? It turns out that they actually send things to customers because they do not want to run into high fines. This is a very interesting system in which spammers want to do something legally, and while they still cannot use bitcoins, they actually have to work within the constraints of an already existing system.
High penalties are also awarded if the spammer has a lot of chargebacks. Refundable payment means that the client declares to the financial company that he did not receive the paid goods or the quality of the goods received does not suit him. Therefore, if a spammer has too many clients demanding a return of payments, very, very high fines are levied on him. Therefore, the percentage of chargeback for spam deals is quite small. The fact is that the conversion rates of their profits are super low, so even one or two fines can destroy the entire monthly profit. So spammers are really interested in avoiding fines in both of the above cases.

Audience: Does PayPal use a more hidden bank relationship?
Professor: both yes and no. PayPal is in many ways very similar to Visa or MasterCard. Its activity is governed by similar rules, because these payment systems have the same types of risks. I think that some things Visa has more stringent restrictions, which we will discuss in a second. But as a payment system, Paypal has similar goals.
Audience: is there an idea to organize a group in which you create an account, and then intentionally go to the spammer's website, buy a bunch of things, and then make repayments to collect a fine from it? Or report that spammers misclassify transactions so that they are fined?
Professor: interesting idea, just like vigilantes!
Audience: yes, spam spammers.
Professor: yes, exactly, but I have never heard of it. I know that spammers are trying to find people who troll them. The article says how the authors identified spammers. They received a bunch of spam messages, went through a bunch of links, issued a special Visa card that they used to buy these things, and so on. They call it "test purchases." However, spammers tend to prevent test purchases of people trying to figure out what is going on. Therefore, some spammers require you to confirm your identity before you sell something. They may ask you to send a photo of your ID card or something like that. Some people began to do this after Visa tightened the rules regarding spam. Now spammers have problems, because people who click on spam links do not want to send a scan of their ID to some random person. The article contains excerpts from the correspondence of spammers on the forum, where they complain that Visa got them - they have to ask people to send them a personal identification, but they don’t want to do that. It is strange that people are afraid of sending scans of documents to spammers, but they are not afraid to tell them their credit card numbers. In any case, spammers are interested in detecting people in time trying to bring them to clean water.
Audience: with regard to chargebacks - perhaps if people do not want their bank to know that they are buying illegal items, then they will hesitate to demand a refund, even if they have not received the goods?
Professor: good question. I do not know how many people who bought all sorts of dietary supplements were disappointed by them and reported this to their bank. Interestingly, the bank must first of all know where it directs the money, but I think you do not need to disclose any additional information about the transaction to it in order to issue a refund.
Audience: What percentage of chargebacks make a spammer anxious?
Professor: call the numbers on the order of 1% of all transactions. In other words, if you are a spammer and you have more than 1% of transactions require a refund, this is a cause for concern. I would not be surprised at the lower numbers, but I heard exactly about one percent.
As I have already said, for me it was one of the most interesting parts of the article, because I always considered that open fraud was a mandatory feature of spam. That is, people followed the links, sent the money and got nothing. But as it turned out, spammers have to go through this entire network, which has mechanisms to prevent fraud, and ultimately they have to send things to customers.
Another reason spammers choose to act carefully, classify transactions correctly and actually send things to customers is that only a few banks are willing to cooperate with spammers. This means that if a spammer receives a lot of chargebacks, or creates problems with banking operations and credit cards, then some bank can break off relations with it. At the same time there are not so many other banks that agree to meet the spammer, so that he continues to deal with his "pranks".
Research on this topic has shown that there are only about 30 acquiring banks, whose services spammers have used for more than two years. In fact, this is a very small number of banks. So, the shortage of banks serves as an incentive not to fool with the financial system, because the spammer simply has no one to turn to if he breaks the established partnership.
Thus, it seems that the requirements of strictly adhering to financial rules can reduce spam. We discussed that things like a botnet provide a lot of IP addresses to spammers, there are enough providers ready to run web servers for them and so on, but the number of servicing banks actually seems small. So maybe we can really attack spam here.
But, as I have already said, this is difficult to do due to the fact that it is difficult to prove the very fact of the illegality of spam activities. For example, if you use spam messages to sell, say, sugar, there is nothing illegal in it, because selling sugar does not violate any laws. You can somehow deceive the buyer in the sale process, but the sale of sugar itself is not illegal.
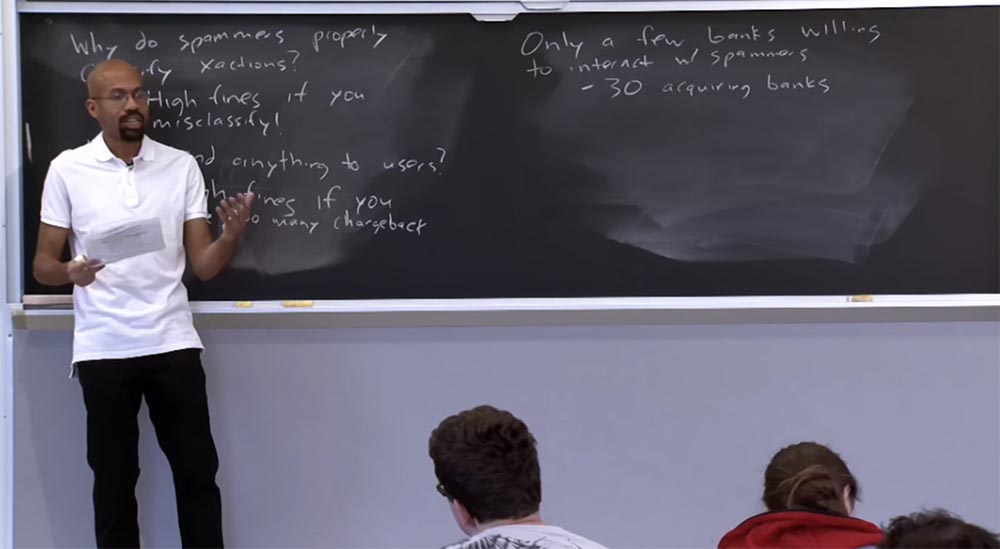
As it turns out, a lot of spam gets into this “gray area”, where the things that spammers do can be unpleasant, but they don't have to break the law. For things like pirated software, legislation more clearly delineates the legal framework. However, you cannot simply point out one of these banks and say “hello, your customers are criminals!” Because this is not always true, especially if there is no clear paper evidence that links the financial transaction to the URL of the spammer, which is the origin of this transaction. It is often very difficult to prove the connection of these links in the spamming chain.
Since the article that we are considering was published, the credit card industry has taken some response, because this article created quite a buzz at the time of its release. After that, the associations of payment systems Visa and MasterCard wondered what they could do to cut off some of the spam. Interestingly, after the article was published, some pharmaceutical companies and software vendors filed complaints against Visa.
If you remember from the article, Visa was an associated network through which spam researchers made trial or bogus purchases, so some companies felt that Visa could be used as a system for financing spammers and decided to complain about it.
In response to these complaints, Visa has made some changes in its payment policy. For example, now all transactions with pharmaceutical products Visa marks as high-risk sales. This means that if the bank acts as an acquirer for these transactions, then Visa will set more stringent transaction conditions for it, for example, it will require the bank to participate in the risk management program or will check it more often.
Visa also changed its internal regulations. Now they have unequivocally defined the list and banned the illegal sale of medicines and goods that are under the protection of registered trademarks.

This helps introduce more aggressive fines against banks and merchants who, in the opinion of this payment system, are involved in the illegal sale of drugs, watches of counterfeit brands and so on. I repeat once again - there is still a lot of spam in the “gray area”, and this is not necessarily illegal. It is just that customers are required to use certain techniques. But now Visa can have a greater impact on people.
To avoid fake purchases, which are not only for spam researchers, but also for associated networks, spammers began to require identity scans from buyers, and this is usually not very good.
At least several years after the payment systems made changes to the rules for conducting transactions, this had an impact. Nice to see that this article has had a big impact on real life.
Another interesting thing that is mentioned in the article is the ethical aspects of conducting security research, in particular, spam chain research. In order to understand how some of the banking mechanisms work, researchers actually had to make purchases. They had to pay the spammer for these goods. The authors write that they destroyed everything they bought without using anything, and talked with development companies about buying pirated versions of their software before buying it.

In fact, the origin of such things is of great importance, especially in a university environment. Because if you want to do something that includes personality research, everything that may have ethical aspects, you must get permission from lawyers from the Ethical Assessment Commission of IRB research projects and the like. It is very important for researchers to be sure that by their actions they will not support intruders in some remote corner of the world. This is also an interesting part of the lecture materials, because we have already discussed how ethical it is to develop zero-day exploits if you know that they cannot be corrected by someone? So this is a really interesting aspect of security research.
Audience: Is there any security ethics oversight? Because the article says that the IRB is not interested in this.
Professor: yes, it was very interesting. , IRB , , . , , - -. , . , . , IRB , , , .
: , 350 -, 28 , , 28 , ?
: , , , . , , 5 , , .
, , , . , , , . , - , , , , – , , .
, , 35 , , , 35 2 — . .
: 350 ? , 350 -.
: . , . , , - . , , , , -.
: , , , .
: , , . , , , , hackback, « ». , - , .

, , , . , . – , , . , 2013 , Microsoft, American Express, Paypal, . , , . , Command & Control. , , , «» .
, . , Microsoft , Microsoft.
, Windows , Windows, , , Microsoft . , . .
, . , , .
, , , , , .
, , .
.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/435948/
All Articles