No more than 80 TLS certificates have been extended due to the US government's shutdown.
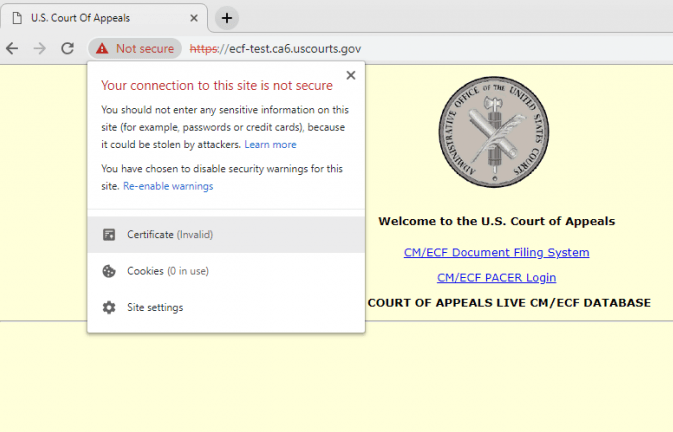
The DigiCert certificate used by the US Court of Appeals website expired on January 5, 2019 and was not renewed. The site contains links to the filing system and PACER (system of public access to judicial electronic records)
According to a Netcraft survey , dozens of US government sites have become either insecure or unavailable during the ongoing federal shutdown. These include important payment portals and remote access services used by NASA, the US Department of Justice and the Court of Appeals.
About 400,000 federal employees are currently on forced leave. It is therefore not too surprising that no one bothered to extend more than 80 TLS certificates on government sites in the .gov zone. The situation is aggravated by the fact that some of these abandoned sites have become inaccessible due to the strict HSTS security policy, which was implemented before the shutdown.
One example is https://ows2.usdoj.gov , the website of the US Department of Justice. His certificate expired a week before the Shatdaun. The certificate was signed by a trusted certification authority GoDaddy, but has not been updated since its expiration on December 17, 2018.
')
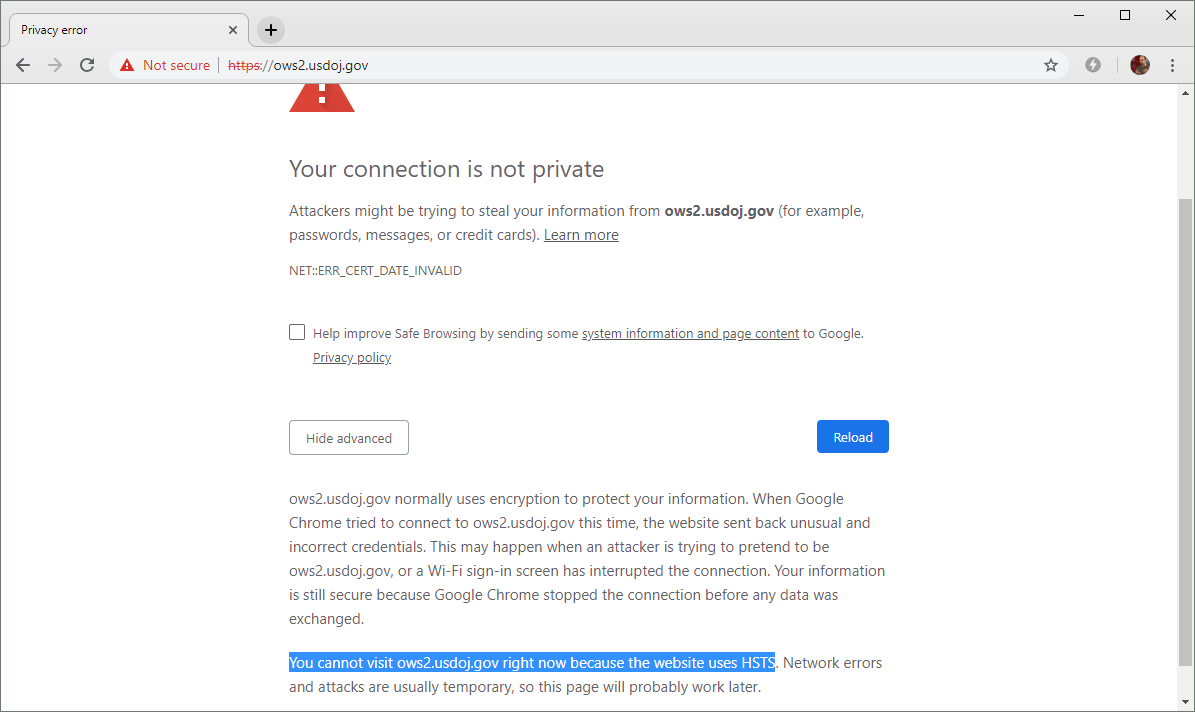
All sub-domains of the US Department of Justice are covered by the HSTS policy. In combination with the expired TLS certificate, this currently prevents users from ignoring warnings and entering the site.
The domain usdoj.gov and all its subdomains are included in the HSTS Chromium preloading list . This is a reasonable security measure that forces modern browsers to use only secure, encrypted protocols when accessing the websites of the Ministry of Justice. At the same time, access is blocked when an expired certificate is detected. In these cases, modern browsers, such as Google Chrome and Mozilla Firefox, deliberately hide an advanced option that will allow the user to bypass the warning and go to the site.
Recognizing the deplorable situation, experts Netcraft believe that after all, between the usability and security should choose the second, if you can not get one or the other. If users had the opportunity to ignore such warnings, they would be vulnerable to attacks like MiTM, which TLS certificates are designed to combat.
However, the correct HSTS policy is configured only on a few .gov sites. They appear in the HSTS preload list, and the rest try to set the policy via the HTTP Strict-Transport-Security header. This policy will not be executed with expired certificate, it is effective only if the user has already visited sites before.
Thus, most of the affected sites will display a security warning that the user can bypass, writes Netcraft: "This creates some security problems, as users are more likely to ignore these security warnings and become vulnerable to attacks like MiTM."

This NASA site still uses an expired certificate, but the domain is not on the preliminary list of HSTS. Thus, users can ignore browser warnings and go to the site.
For example, the domain https://rockettest.nasa.gov/ is not included in the HSTS preloading list, and the certificate expired on January 5, 2019.
Another example clearly demonstrates the potential danger of ignoring browser security warnings. The Berkeley lab site certificate https://d2l.lbl.gov expired on January 8, 2019 (although the Berkeley Lab is not affected by the shutdown) and has not been replaced. Since there is no effective HSTS policy, users can ignore browser warnings and go to the login form. In this example, clicking next to the address bar of the browser will explicitly advise the user not to leave any confidential information on the page.
The government shatdaun occurred because of the stubborn position of two parties on the American political scene. President Donald Trump does not want to compromise on the wall with Mexico, and Democrats refuse to approve a budget containing $ 5.7 billion to build a wall. If the shatdaun lasts, and federal employees remain on vacation, in the near future even more government sites may be inaccessible due to overdue TLS certificates.
Source: https://habr.com/ru/post/435934/
All Articles