MIT course "Computer Systems Security". Lecture 23: Security Economics, Part 2
Massachusetts Institute of Technology. Lecture course # 6.858. "Security of computer systems". Nikolai Zeldovich, James Mykens. year 2014
Computer Systems Security is a course on the development and implementation of secure computer systems. Lectures cover threat models, attacks that compromise security, and security methods based on the latest scientific work. Topics include operating system (OS) security, capabilities, information flow control, language security, network protocols, hardware protection and security in web applications.
Lecture 1: "Introduction: threat models" Part 1 / Part 2 / Part 3
Lecture 2: "Control of hacker attacks" Part 1 / Part 2 / Part 3
Lecture 3: "Buffer overflow: exploits and protection" Part 1 / Part 2 / Part 3
Lecture 4: "Separation of privileges" Part 1 / Part 2 / Part 3
Lecture 5: "Where Security Errors Come From" Part 1 / Part 2
Lecture 6: "Opportunities" Part 1 / Part 2 / Part 3
Lecture 7: "Sandbox Native Client" Part 1 / Part 2 / Part 3
Lecture 8: "Model of network security" Part 1 / Part 2 / Part 3
Lecture 9: "Web Application Security" Part 1 / Part 2 / Part 3
Lecture 10: "Symbolic execution" Part 1 / Part 2 / Part 3
Lecture 11: "Ur / Web programming language" Part 1 / Part 2 / Part 3
Lecture 12: "Network Security" Part 1 / Part 2 / Part 3
Lecture 13: "Network Protocols" Part 1 / Part 2 / Part 3
Lecture 14: "SSL and HTTPS" Part 1 / Part 2 / Part 3
Lecture 15: "Medical Software" Part 1 / Part 2 / Part 3
Lecture 16: "Attacks through the side channel" Part 1 / Part 2 / Part 3
Lecture 17: "User Authentication" Part 1 / Part 2 / Part 3
Lecture 18: "Private Internet browsing" Part 1 / Part 2 / Part 3
Lecture 19: "Anonymous Networks" Part 1 / Part 2 / Part 3
Lecture 20: “Mobile Phone Security” Part 1 / Part 2 / Part 3
Lecture 21: “Data Tracking” Part 1 / Part 2 / Part 3
Lecture 22: MIT Information Security Part 1 / Part 2 / Part 3
Lecture 23: "Security Economics" Part 1 / Part 2
Audience: how do spammers work with mailing lists, especially with huge lists?
')

Professor: There are problems with aggregation of mailing lists, as it is very difficult to provide mass mailing. Perhaps spammers need to use heuristics, with which they scale the payment according to the size of the list. For example, it would be heuristically more reasonable to send letters to 1000, and not to 350 million people or something like that. But you are right that there are practical limitations to mailing lists.
So, what can a spammer do to circumvent the spam protection methods mentioned above? Attackers have three workarounds.
The first is a botnet network with many IP addresses that the spammer can use. Even if someone tries to create a “black list” of IP addresses, an attacker can search through a bunch of IP addresses on the network using a botnet and bypass the black list filtering.
The second is the use of hacked email accounts to send spam. This is a very profitable way, because due to the high popularity of the mail services Gmail, Yahoo or Hotmail can not be placed in the "black list". If you list the entire service in such a list, then you have closed it for tens of millions of people.

Of course, these individual services can put your mailbox on the “black list” if they use heuristic analysis, showing that you are sending letters to a lot of people with whom you have not copied, and the like. On the web server side of the postal service, there are technologies that allow you to detect your suspicious activity.
However, hacked accounts still represent great value for spammers, because even if your compromised account is not suitable for mass mailing, it can be used to send emails to people you know from your contact list. This makes it easier for an attacker to phish, since people are more likely to click on links sent to them by a familiar person. This is a very powerful tool for spamming attacks.
The third workaround is to capture the IP address from the rightful owner. As Mark mentioned in a previous lecture, there is a network protocol called BGP, which is used to control routing on the Internet. Thus, there are attacks in which the hacker claims that he is the owner of IP addresses, although in fact he does not own them. Because of this, all traffic associated with these addresses will be sent to the attacker, and he will be able to use these IP addresses to send spam. As soon as a spammer is detected, it will stop using BGP for one autonomous system and switch to another.
There is a lot of research on how to implement BGP authentication to prevent IP address capture, and a bunch of different security methods that attackers can try to work around. But all these workarounds are not free, because the attacker must somehow pay for the botnet or for getting into email accounts. So any of the protective measures will increase the cost of spam generation. Therefore, these protective measures are useful, although not perfect.
So what does a botnet network look like? In general, we have a cloud in which the Command & Control infrastructure is located, giving commands to all slave bots. So, the spammer calls C & C and says: “here are my new spam messages that I want to send”, after which the bots start acting on behalf of the command and control infrastructure and send messages to a group of people.

How are bots useful? As I already mentioned, they have IP addresses, they have bandwidth, perform computational cycles, sometimes these bots are used as a web server themselves. So these things are very, very useful for the spammer, besides they serve as a kind of indirect addressing. Indirect addressing is very useful for intruders. This means that if law enforcement or anyone else disconnects this layer without affecting the infrastructure of the C & C itself, the spammer can simply attach the command and control infrastructure to another set of bots and continue his work.
This is one of the reasons for the usefulness of bots. A botnet can scale to millions of IP addresses, so people will click on random links, all the while using malicious software. So these things can get very, very big. Since the whole companies are involved in the botnet's network, millions and millions of computers can be present in them, so these networks are rather complicated technically.
So how much does it cost to install malware for all these bots? It must be remembered that, as a rule, these are ordinary end-user computers. The cost of placing malware on one of the computers, or the price per host, is about 10 cents for American hosts and about one cent for Asian hosts. There are several reasons why the price is so different. Perhaps people tend to think that the connection established from the United States deserves more confidence. At the same time, Asian computers mostly use pirated software that is not updated with security packages, so organizing a botnet network in Asia is much cheaper.
You will see some very interesting statistics on how these costs can fluctuate, because companies such as Microsoft are trying to eradicate piracy. But in any case, this is a rough estimate. Suffice to say that it is not too expensive.
What makes this C & C center and how does it look? In its simplest form, this is a centralized computer system of one or more machines. The attacker simply works on these machines, sending commands to the network from there a botnet. Since this is a centralized system, it will be very useful for an attacker to have what is known as “bulletproof hosting”. His idea is that you place the Command & Control infrastructure on the servers of Internet providers that ignore requests from financial or law enforcement agencies to shut down such servers. "Bulletproof servers" really exist.

They are more expensive because there are risks in this case, but if you can place your C & C center there, it will be a great success. Because when the US government or Goldman Sachs bank says to such a provider: “hey, turn off this guy who is sending spam!”, He answers: “how can you make me do this? I work in another jurisdiction and am not obliged to comply with intellectual property laws. ” As I said, these types of hosts actually charge a premium for the risk of launching such services on their servers.
Another alternative to running the C & C infrastructure is the P2P peer network, which is a mini-botnet. Here, the entire management infrastructure is distributed across different computers, and at any given time there is another computer that takes on the role of C & C, giving commands to all these work nodes. This is good because it does not require access to one of these "bullet-proof hosts." You can build a C & C infrastructure using regular bots. P2P makes it difficult to guarantee the availability of hosts located in this cloud, but it has other advantages. In general, these are two approaches that attackers can use to send spam.

So what happens if the hosting is closed? There are a couple of things that a spammer can do in this case. For example, it can use DNS to redirect requests. Suppose someone starts shutting down servers by counteracting the spammer. But while the servers are still alive, the attacker creates lists of server IP addresses, which can contain hundreds or thousands of these addresses. After that, it will begin to bind each address to the host name for a very short period of time, say, 300 seconds. This allows an attacker to deal with the consequences of shutting down servers, which are considered to be spam messages distributors based on heuristics. In fact, every 300 seconds it changes the place in which spam is sent. So indirect addressing is a great prospect for a spammer. As I said, the use of indirect addressing is for the spammer the main way to evade law enforcement and heuristic protection methods.
One may wonder what will happen if we just destroy the spammer’s DNS server? How difficult is it to do? The lecture article states that there are several levels at which you can counterattack the spammer. For example, you can try to remove the attacker's domain registration. For example, you say: "hey, if you are looking for russianpharma.rx.biz.org, then go here to this DNS server and communicate through it!". That is, as soon as someone tries to get to the spammer’s DNS server, you redirect it to the top-level domain. However, the difficulty is that an attacker can use fast flow switching methods at another level. For example, it can “scroll” the servers that are used as spam DNS servers, that is, switch between the servers that it uses to send spam, and so on and so forth. Thus, we see how these people can use several machines to try to avoid detection.
As I mentioned earlier, you can use hacked email accounts to send spam. If you can get access to someone's account, then you do not even need to install malware on the user's computer. You can access someone else's account from your own computer, wherever you are. This method is optimal for carrying out phishing attacks, because you send spam on behalf of a person who is trusted by his friends.
Therefore, postal service providers are extremely interested in preventing this, because if they do not do this, they risk falling into the “black list”. In addition, the provider needs to somehow monetize its service. They really need real users who will click on the legal advertisements that appear on their email page. But the higher the proportion of users who spam, the less likely that advertisers decide to use the services of such a mail service. Therefore, webmail providers are very interested in preventing spam infiltrations.
They use heuristics to detect this type of spam. They may try to use captcha. If they suspect that you have sent 5 spam messages in a row, they may ask you to enter numbers from one of these blurry images or something similar.
However, many of these methods do not work very well. If you look at the price of a hacked account, then, as a spammer, it will seem cheap enough - from one to 5 cents per account for Yahoo, Gmail or Hotmail. It is very very cheap. So such protection is not capable of forcing spammers to refuse to purchase hacked accounts. This is a bit disappointing, because it seems that wherever we go, we have to solve a captcha if we want to buy something or send mail. So what happened to the captcha, because she had to prevent harmful things?
As it turns out, an attacker can create services to solve a captcha, and the captcha input process can be automated, like everything else. As it turned out, the cost of solving a single captcha is about $ 0.001, and this can be done with a very low latency. Therefore, captcha is not a serious barrier against spam. You might think that captchas are solved by computers, software. But in reality, this is not the case; in most cases, real people decide captchas, and an attacker can outsource this case in two ways.
First of all, a hacker can simply find a labor market with very cheap labor force and use people as captcha solvers. For example, the spammer is concerned about the Gmail captcha, in which case he sends it to where the person is sitting, he decides to send it to the spammer for a small amount of money, and then the spammer sends the answer to the legal site. You can also do this with the help of the “Mechanical Turk” Mechanical Turk. Have you heard about the "mechanical turk"?

It is rather elegant, I mean "elegant" as a way to do evil. You can post these tasks on the Mechanical Turk website and say, “hey, I’m just playing solving problems with pictures,” or something like that. Or you can openly state that you have captcha to be solved. You publish a price, after which the market brings you together with people who are ready to perform this task, they give answers and you publish them. So you can automate the spammer’s workflow, however, you need to consider that Amazon, which owns Mechanical Turk, charges a fee for using it.
The second way of outsourcing is that the spammer takes a captcha from the site he needs and copies it on the legal site to which the user is being redirected. He decides to captcha actually for the attacker, who then enters the correct answer on his website, taking advantage of the work of an unsuspecting user. In addition, if the spammer does not trust its users, he can duplicate the work using crowdsourcing.
For example, you send a captcha to solve for two or three people, and then use a majority vote and choose what is accepted by the majority of votes as a response to your captcha.
For the above reasons, captcha does not work as well as you might think. Therefore, Gmail or Yahoo providers try to use captchas as often as possible to make life difficult for spammers. However, the problem is that the frequent use of a captcha in the first place annoys respectable users.
A good example of the complexity of the spam generation process is Gmail’s two-factor authentication. Actually, this is a very good idea. If Gmail determines that you are trying to sign in to a Gmail account from a computer that it doesn’t know, it will send you a text message to your phone saying “enter this verification code before continuing to use our service”.
It's funny that this is a great idea, but at least it really annoys me. I understand that this is done for my own safety, but I am still angry. If I do not often use different computers, I agree to such conditions, otherwise it becomes very inconvenient.
Thus, there is a very interesting compromise between the security that people talk about and the security measures with which they are willing to put up. As a result, postal service providers find it very difficult to find the optimal balance between the frequency of using captcha and the convenience of customers. Do you have any questions before I proceed to review support for clicks?
Audience: It turns out that one of the reasons why encrypted emails are not widely accepted is the large role of spam filters?
Professor: do you mean that then the filters will not be able to view the contents of the letter and will not understand what is happening? This is a good question. , , – .

, , . , . , . , , . , , . ? , , -. .
, . ? , DNS-, , , IP-. - -, IP-. , , DNS- -. , , .

, «» IP-, , , -URL? - ? - 183.4.4… russianjewels.biz?
: .
: , , , . , , . , - , . , DNS — . DNS, -, . , «» IP- -.
, , , -URL , , bit.ly. , - . HTML JavaScript, - . , . , , -, .
, , « » 10% URL, 90%. .
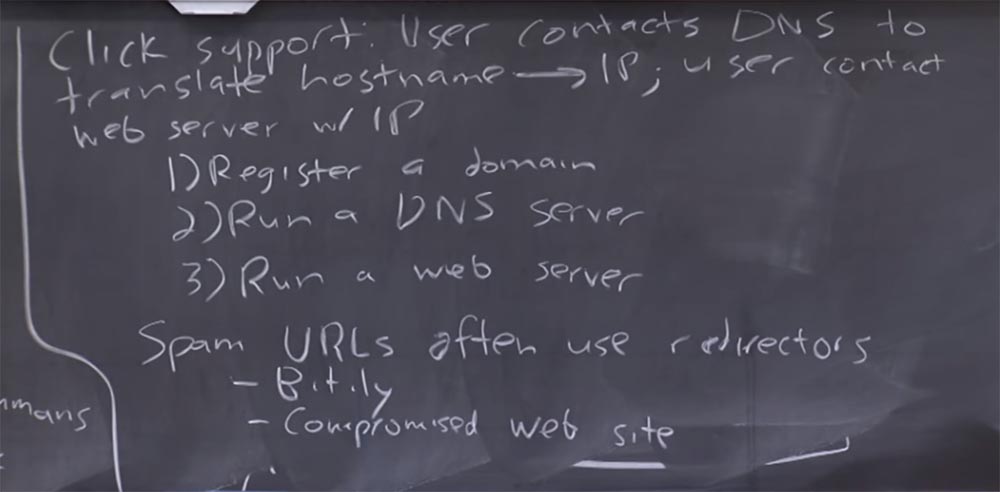
- DNS-, . , , , , .
, -.
. .
, ? , SPECTRE . , . - , , , . , , .
, . , , , Windows, . , - . , , . .
52:00
.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/435788/
All Articles