Conference DEFCON 18. Practical espionage using a mobile phone. Part 1
Welcome to the "Practical Spying on a Cell Phone" presentation. Before we begin, I’ll make a few comments about privacy. First, a cell phone call can be recorded directly during a call. Surprise! So if you do not want your call to be recorded, turn off your phone. If you use the services of mobile operators Sprint or Verizon, you are not in GSM networks, and my system cannot talk to your phones at all, so you have nothing to worry about.

I must note that I encourage people to keep their phones in sight during a call, especially if they use a GSM handset, because the whole point of this is to show how your phone calls can be intercepted. If you do not use your pipe, this technique does not work.
')
So, this is a computer presentation, you can see a big slot on the side of my laptop where the HDD should be, but I use a bootable USB flash drive, because the BTS base receiving and transmitting station for GSM network can be downloaded from a portable media without using a hard disk . At the end of the presentation, I will cut this flash drive in half using the Leatherman multitool, because I am going to record very confidential information on it, all the settings of your phone, a log of phone calls and so on. All this will be destroyed at the end of the presentation, so you can not worry about it.
Let me plug in the power cord and get back to the subject. I'm currently connected to the Verizon network, so my VerizonDroid provides me with a VoIP connection.
If you are connecting to my network, then the only way to find out if you really are connected is to try to make a call. If you call, you will receive a voice message that your conversation is intercepted, blah blah blah. So just take your phones during the presentation, try dialing and see what happens. And if you hear such a message on the handset, it means that you are connected to my system. If you do not hear, it means that you are all right. In any case, at any time, if someone connects to this network, everything for making calls will be done in the best possible way.
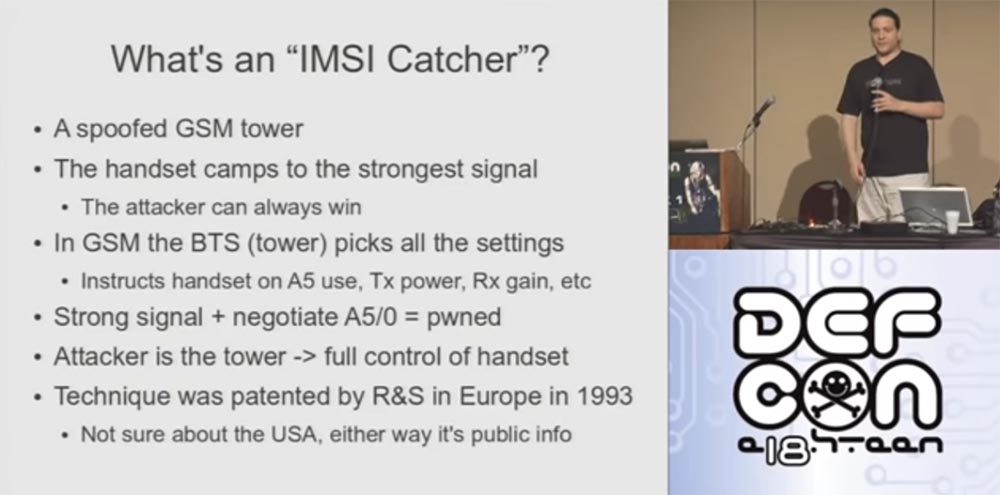
So, before we talk about the IMSI interceptor, I’ll tell you what it is. The IMSI, or international mobile subscriber identifier, is a unique 15-digit number used to authenticate a subscriber moving from the network to another network. You can think of it as something like a GSM username. It consists of two parts that are on your SIM card and authenticate you.

Your MSI is the username and secret network authentication key located in the read-only part of the SIM card. A little protection is done like this: when connected to a network, the IMSI is replaced with a temporary TMSI. During the presentation, I will show you how many of these TMSIs arise, to give an opportunity to see how many people are connected to the base station.
So IMSI is a kind of secret, and ICCID, the long string of numbers printed on the SIM card, is a unique identifier for the card itself, something like its serial number. These two identifiers are closely related. In many cellular networks in the US and some other countries, you can identify IMSI by ICCID and vice versa, and this is not a secret. In other countries, they have done a little better; there, the ICCID is in no way associated with another identifier and is simply a random set of numbers.
In fact, it does not really matter, but I often mention this because, at least in the US, you can learn from it IMSI. So what is the IMSI "catcher"?
The basic idea is that this is a fake GSM tower, a fake base station. In theory, when the phone is looking for a signal, it selects the tower that provides the most powerful signal, and connects to the tower with the best signal. If there is an antenna with the highest gain near, directed directly at you, then I will be this tower! I produce a very weak signal, only 25 milliwatts, but I am close and I use directional antennas. Therefore, I hope that your phones will choose exactly my signal and you will connect to my network.
It should be borne in mind that in a GSM network, the base station determines all settings, so when you connect to my tower, it will tell your phone whether to use encryption, switching to other signal frequencies and similar things. If I order not to use encryption, your phone will think: "excellent, no encryption, I will use plain text."
Take my word for it, I do not do anything harmful, my test only affects the functionality and will not cause any permanent changes in the characteristics of your phones if they connect to my network. But if I wanted, I could do a lot of things with them, for example, update the SIM card and generally get a lot of pleasure from it.
So, if I have the opportunity to generate a really powerful signal, then by canceling A5 encryption, I can easily take control of your phone, and you can’t do anything and don’t even know about it. The idea of the IMSI interceptor arose simultaneously with the GSM standard, and the interceptor technology was patented by Rode and Schwartz in Europe in 1993. I have never seen references to similar patents in the United States, but in any case, patents in Europe are public knowledge, so this vulnerability is well known. The meaning of the patent is that if you contact R & S and say that you want to buy an IMSI catcher, they will charge you a couple of million dollars.
From the equipment that is on the table, the most expensive is my laptop, then the USRP transceiver follows, for about $ 1,500, and the next most expensive is an instant messaging device for $ 20. Thus, using this equipment, you can do the same thing that makes commercial equipment worth 1000 times more expensive.
Briefly tell you what is the encryption involved in the IMSI interceptor. If I am an attacker who has created my base station, and you have a phone that has connected to it, I just tell him to turn off encryption. I do not need to crack ciphers, build rainbow tables, I do not need any hard drives for quick viewing. I'm just telling your phone to turn off encryption, it's that simple.

In fact, the GSM standard specification provides for sending a message to the subscriber when your phone connects to a network that does not use encryption. But if you continue reading further, you will see that there is another place in the specification that says: “if you want to turn off the warning message, then install this small bit configuration on the SIM card”. Each SIM card I have seen, and I have seen many different networks of cellular operators around the world, contains these bits. Every operator I've ever met turns off this warning, so I never came across a phone that would give the message: “You are connecting to an insecure network!”, As required by the GSM specification.
This is a deliberate choice of operators. The idea is that if you are traveling to a country like India, where cellular encryption is not supported, since it’s illegal there, but you want to use your phone, it must support the unencrypted A5 / 0 calls. If you start receiving a warning each time you connect to a new GSM tower, you will think what the hell is going on, start cursing AT & T or someone else, and so on.
Let's pay attention to the spectrum of the used frequency range. One of the questions that was raised by the press concerned a problem in which operators use different frequencies. Therefore, throughout the world, it was decided to use only 4 GSM standards: 850, 900, 1800 and 1900. Frequencies 850 and 1900 are used mainly in the USA, and 900 and 1800 - in Europe.
If you look at the size of the band of these frequencies, you will see that there is an overlap between the European frequency of 900 and the American 850. In fact, the GSM 900 standard operates in the range from 880 to 914 MHz, and the US ISM standard - from 902 to 928 MHz, so the frequencies of these standards will overlap in the range from 902 to 912 MHz.
So, I will launch my transmitter in an absolutely legal frequency range, moving towards the European standard of communication. In this case, your phone will be absolutely all the same, it does not care about the geographical features of communication, it will just catch the strongest signal and say: “fine, here is my tower”!
If you have a European telephone, or a 4-band telephone, operating in all 4 communication standards, you will see a network. If you have an American phone that only sees American frequencies, you will not see the network.
What is the American standard ISM? It stands for Industrial, Scientific, Medical, that is, created for industrial, scientific and medical cellular networks. The idea of the standard is that it is designed for low-power devices, which very quickly change the frequency, and the design of which provides minimal user intervention in the operation of the phone.

Formally, this is an auxiliary communication range, intended mainly for radio amateurs, but they do not like to use these frequencies, because they are too noisy, and besides, amateurs believe that this is just a lame range. However, it is quite suitable for our purposes, and we can legally launch our base station BTS in the amateur GSM band. So, we will act as radio amateurs.
What we need in the first place is a license to use amateur frequencies, and it is extremely easy to get it. You can go to kb0mga.net/exams and start answering exam questions. You can do this again and again, until you accidentally stumble upon the correct answer, because if you answer incorrectly, you will continue to ask questions. You can spend a few hours on it, and when, finally, correctly answer all the questions, then pass the exam. I would advise all the same to study the material, if you decide to become a radio amateur, because I definitely learned a lot by answering exam questions. The next requirement for an amateur radio station - its power should not exceed 1500 W, which is more than enough for our purposes. I have another amplifier that I use for RFID, its power is 600 watts, and this is a terrifying amount of energy, its power is too high, so 1500 watts will be enough for whatever purposes.
Regarding what we are going to broadcast, we can say that technically we are going to transmit an undefined digital code - these are the bits traveling back and forth between the phone and my tower. Thus, in terms of radio amateurs, you are allowed to transmit an undefined numeric code until its specification is published. In our case, all GSM protocols and specifications are published, so this question can not be bothered.
You are also not allowed to use encryption, that is, your messages should not be encrypted in any way. So according to the law, when I launch my base station, I simply have to disable encryption! What I am doing.
For radio amateurs there are no restrictions on the size of the antenna, the only thing that is limited is the radio frequency exposure. The FCC publishes standards for which radiation absorption coefficient is safe for humans. My equipment is far from these limits, because it emits only 25 milliwatts. If your phone works in the higher frequency range of GSM 1800/1900, then it studies about 1 W, that is 40 times more, and in the lowest GSM 800/900 - about 2 W, that is, 80 times more. So the phone in your pocket radiates much more than my “big and scary” antenna.
The only important requirement is that the station must identify itself every 10 minutes. The call sign of a radio station is a direct carrier wave, Morse code, a signal that is periodically broadcast. It is rather difficult to integrate this into GSM, so the optimal solution is the second transmitting station operating on the frequency of the main base station. It is slightly more powerful and replaces the signal from the GSM base station, making a DoS attack on it for 1 second to transmit the call. I simply integrated this function into the USRP transmitter, it is not at all difficult. So all we need is an easily controlled 900 MHz transmitter.
Next, I have this little pink box for instant messaging Instant messaging device, it is called ID-ME, or “identify me”. It was brought to me by Travis Goodspeed. It has an output power of +10 dBm, a wide coverage of the frequency range and is programmed in C language. This device has no safe firmware, it can be “flashed” with the help of Travis utility called GoodFET. Unfortunately, it is not compatible with the JTAG interface and RF connectors, but they are fairly easy to add.
So, we can write the firmware for this device, we know the corresponding frequencies, so we can bring the frequency and power in line with the USRP, combine and amplify the signals of the main station and the additional transmitter.
Now consider the installation of a base transceiver station cellular BTS. So, I have an IMEI for a radio amateur, this is what I need for GSM, and now I need a universal software radio USRP. All peripherals are available for it online, there it costs about $ 1,500 for two RFX900 daughter boards.
In addition, you need a device called ClockTamer - code.google.com/p/clock-tamer , which allows you to create a very accurate clock generator to synchronize with GPS. It is specifically designed to be shared with the USRP.

Phones receive their frequencies from base stations. Base stations provide highly accurate frequencies, and phones find out how compatible their own frequencies are with the frequency of the transmitting station.
So if I come from the side with my own station, the frequency stability of which does not match the frequency stability of the local towers, which are located around, then all the phones will be calibrated to the frequency of these local towers and will not even pay attention to my station, even if the difference of our frequencies will be only a few kilohertz.
"Right out of the box" ClockTamer extremely accurately adjusts the frequency in increments of ± 100 Hz in the range of up to 1.9 GHz, compared to this accuracy, the GPS module is just sucks. This device has a crazy precision and is flexible to program.
The software of my cellular station provides a laptop with Debian, OpenBTS and Asterix. OpenBTS provides everything connected with GSM, Asterix receives calls from OpenBTS and sends them via VoIP. I used the basic version of BTS, it transmits voice and SMS, but does not transmit data.
For this presentation, I have disabled the use of SMS, mainly due to the fact that it is difficult for me to get your caller ID when you send SMS. Yes, I can send it via the Internet and connect it to where it should be connected, but the person who receives it will not be able to determine who it came from and will not be able to answer. So I thought that it would be easier to simply disable this feature of BTS, although the system supports it.
So, let's get down to the first demo and run BTS in test mode. I am connecting to the USRP laptop, everything else is already on, so let's launch the base station. I do not know how much you can see the image on the screen of my laptop, now I will move it closer to the camera. The only thing I want to show is the launch of the TMSI command — it shows me a list of all the temporary MSIs that were allocated by the base station, in other words, how many people are currently connected to it. At the bottom of the screen you can see that in table 0, that is, at the moment no one is connected to my network.
Now I will type some more commands. Cell ID is a cell ID, which indicates that the mobile country code that I am currently using is 001, 00 is a country code according to the GSM specification, 1 means a test. Then I use the MNC mobile network code, it is 01, the unit here also means a test, so this is a test network in a test country, this is not Europe and not America. Below is the name of the cellular network that I represent is DEFCON18. Some phones will display it, some will not.
I want to draw your attention to the fact that at present it is not a “hostile” configuration, it is a test mode, it is not an advertisement of any known network and it does not work on the US cellular frequency, so until I start this thing, no one can connect to my network.
If you want to scan available cellular networks, you can, but I recommend that you just leave your phones alone. Just pull them out of your pockets every few minutes and try to call. In just a minute I will show you how easy it works.

So, how do I substitute a particular network to use the IMSI interceptor not just on a random network? , – MCC, , MNC – . MCC 310. . MNC 2-3 , , , , OpenBTS. . , MNC MCC, , , , .
, , . .
, №2, , MNC/ MCC . , TMSIS. ! 15 , 15 «», . 15 , . , , !
( )

: , iPhone. , , . , «». «» .
, TMSIS 30 ! , . , , MNC/ MCC. ell ID, MCC/MNC . . , , T-mobile. , , AT&T. , !
, ID . , MCC 310, AT&T. , 410, 6610. , AT&T. — Cell ID 31041066610, . , GSM, AT&T.
, . , , IMSI, 20 , AT&T, . , – . , , .
26:15
DEFCON 18. . Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

I must note that I encourage people to keep their phones in sight during a call, especially if they use a GSM handset, because the whole point of this is to show how your phone calls can be intercepted. If you do not use your pipe, this technique does not work.
')
So, this is a computer presentation, you can see a big slot on the side of my laptop where the HDD should be, but I use a bootable USB flash drive, because the BTS base receiving and transmitting station for GSM network can be downloaded from a portable media without using a hard disk . At the end of the presentation, I will cut this flash drive in half using the Leatherman multitool, because I am going to record very confidential information on it, all the settings of your phone, a log of phone calls and so on. All this will be destroyed at the end of the presentation, so you can not worry about it.
Let me plug in the power cord and get back to the subject. I'm currently connected to the Verizon network, so my VerizonDroid provides me with a VoIP connection.
If you are connecting to my network, then the only way to find out if you really are connected is to try to make a call. If you call, you will receive a voice message that your conversation is intercepted, blah blah blah. So just take your phones during the presentation, try dialing and see what happens. And if you hear such a message on the handset, it means that you are connected to my system. If you do not hear, it means that you are all right. In any case, at any time, if someone connects to this network, everything for making calls will be done in the best possible way.
So, before we talk about the IMSI interceptor, I’ll tell you what it is. The IMSI, or international mobile subscriber identifier, is a unique 15-digit number used to authenticate a subscriber moving from the network to another network. You can think of it as something like a GSM username. It consists of two parts that are on your SIM card and authenticate you.

Your MSI is the username and secret network authentication key located in the read-only part of the SIM card. A little protection is done like this: when connected to a network, the IMSI is replaced with a temporary TMSI. During the presentation, I will show you how many of these TMSIs arise, to give an opportunity to see how many people are connected to the base station.
So IMSI is a kind of secret, and ICCID, the long string of numbers printed on the SIM card, is a unique identifier for the card itself, something like its serial number. These two identifiers are closely related. In many cellular networks in the US and some other countries, you can identify IMSI by ICCID and vice versa, and this is not a secret. In other countries, they have done a little better; there, the ICCID is in no way associated with another identifier and is simply a random set of numbers.
In fact, it does not really matter, but I often mention this because, at least in the US, you can learn from it IMSI. So what is the IMSI "catcher"?
The basic idea is that this is a fake GSM tower, a fake base station. In theory, when the phone is looking for a signal, it selects the tower that provides the most powerful signal, and connects to the tower with the best signal. If there is an antenna with the highest gain near, directed directly at you, then I will be this tower! I produce a very weak signal, only 25 milliwatts, but I am close and I use directional antennas. Therefore, I hope that your phones will choose exactly my signal and you will connect to my network.
It should be borne in mind that in a GSM network, the base station determines all settings, so when you connect to my tower, it will tell your phone whether to use encryption, switching to other signal frequencies and similar things. If I order not to use encryption, your phone will think: "excellent, no encryption, I will use plain text."
Take my word for it, I do not do anything harmful, my test only affects the functionality and will not cause any permanent changes in the characteristics of your phones if they connect to my network. But if I wanted, I could do a lot of things with them, for example, update the SIM card and generally get a lot of pleasure from it.
So, if I have the opportunity to generate a really powerful signal, then by canceling A5 encryption, I can easily take control of your phone, and you can’t do anything and don’t even know about it. The idea of the IMSI interceptor arose simultaneously with the GSM standard, and the interceptor technology was patented by Rode and Schwartz in Europe in 1993. I have never seen references to similar patents in the United States, but in any case, patents in Europe are public knowledge, so this vulnerability is well known. The meaning of the patent is that if you contact R & S and say that you want to buy an IMSI catcher, they will charge you a couple of million dollars.

From the equipment that is on the table, the most expensive is my laptop, then the USRP transceiver follows, for about $ 1,500, and the next most expensive is an instant messaging device for $ 20. Thus, using this equipment, you can do the same thing that makes commercial equipment worth 1000 times more expensive.
Briefly tell you what is the encryption involved in the IMSI interceptor. If I am an attacker who has created my base station, and you have a phone that has connected to it, I just tell him to turn off encryption. I do not need to crack ciphers, build rainbow tables, I do not need any hard drives for quick viewing. I'm just telling your phone to turn off encryption, it's that simple.

In fact, the GSM standard specification provides for sending a message to the subscriber when your phone connects to a network that does not use encryption. But if you continue reading further, you will see that there is another place in the specification that says: “if you want to turn off the warning message, then install this small bit configuration on the SIM card”. Each SIM card I have seen, and I have seen many different networks of cellular operators around the world, contains these bits. Every operator I've ever met turns off this warning, so I never came across a phone that would give the message: “You are connecting to an insecure network!”, As required by the GSM specification.
This is a deliberate choice of operators. The idea is that if you are traveling to a country like India, where cellular encryption is not supported, since it’s illegal there, but you want to use your phone, it must support the unencrypted A5 / 0 calls. If you start receiving a warning each time you connect to a new GSM tower, you will think what the hell is going on, start cursing AT & T or someone else, and so on.
Let's pay attention to the spectrum of the used frequency range. One of the questions that was raised by the press concerned a problem in which operators use different frequencies. Therefore, throughout the world, it was decided to use only 4 GSM standards: 850, 900, 1800 and 1900. Frequencies 850 and 1900 are used mainly in the USA, and 900 and 1800 - in Europe.
If you look at the size of the band of these frequencies, you will see that there is an overlap between the European frequency of 900 and the American 850. In fact, the GSM 900 standard operates in the range from 880 to 914 MHz, and the US ISM standard - from 902 to 928 MHz, so the frequencies of these standards will overlap in the range from 902 to 912 MHz.
So, I will launch my transmitter in an absolutely legal frequency range, moving towards the European standard of communication. In this case, your phone will be absolutely all the same, it does not care about the geographical features of communication, it will just catch the strongest signal and say: “fine, here is my tower”!
If you have a European telephone, or a 4-band telephone, operating in all 4 communication standards, you will see a network. If you have an American phone that only sees American frequencies, you will not see the network.
What is the American standard ISM? It stands for Industrial, Scientific, Medical, that is, created for industrial, scientific and medical cellular networks. The idea of the standard is that it is designed for low-power devices, which very quickly change the frequency, and the design of which provides minimal user intervention in the operation of the phone.

Formally, this is an auxiliary communication range, intended mainly for radio amateurs, but they do not like to use these frequencies, because they are too noisy, and besides, amateurs believe that this is just a lame range. However, it is quite suitable for our purposes, and we can legally launch our base station BTS in the amateur GSM band. So, we will act as radio amateurs.
What we need in the first place is a license to use amateur frequencies, and it is extremely easy to get it. You can go to kb0mga.net/exams and start answering exam questions. You can do this again and again, until you accidentally stumble upon the correct answer, because if you answer incorrectly, you will continue to ask questions. You can spend a few hours on it, and when, finally, correctly answer all the questions, then pass the exam. I would advise all the same to study the material, if you decide to become a radio amateur, because I definitely learned a lot by answering exam questions. The next requirement for an amateur radio station - its power should not exceed 1500 W, which is more than enough for our purposes. I have another amplifier that I use for RFID, its power is 600 watts, and this is a terrifying amount of energy, its power is too high, so 1500 watts will be enough for whatever purposes.
Regarding what we are going to broadcast, we can say that technically we are going to transmit an undefined digital code - these are the bits traveling back and forth between the phone and my tower. Thus, in terms of radio amateurs, you are allowed to transmit an undefined numeric code until its specification is published. In our case, all GSM protocols and specifications are published, so this question can not be bothered.
You are also not allowed to use encryption, that is, your messages should not be encrypted in any way. So according to the law, when I launch my base station, I simply have to disable encryption! What I am doing.
For radio amateurs there are no restrictions on the size of the antenna, the only thing that is limited is the radio frequency exposure. The FCC publishes standards for which radiation absorption coefficient is safe for humans. My equipment is far from these limits, because it emits only 25 milliwatts. If your phone works in the higher frequency range of GSM 1800/1900, then it studies about 1 W, that is 40 times more, and in the lowest GSM 800/900 - about 2 W, that is, 80 times more. So the phone in your pocket radiates much more than my “big and scary” antenna.
The only important requirement is that the station must identify itself every 10 minutes. The call sign of a radio station is a direct carrier wave, Morse code, a signal that is periodically broadcast. It is rather difficult to integrate this into GSM, so the optimal solution is the second transmitting station operating on the frequency of the main base station. It is slightly more powerful and replaces the signal from the GSM base station, making a DoS attack on it for 1 second to transmit the call. I simply integrated this function into the USRP transmitter, it is not at all difficult. So all we need is an easily controlled 900 MHz transmitter.
Next, I have this little pink box for instant messaging Instant messaging device, it is called ID-ME, or “identify me”. It was brought to me by Travis Goodspeed. It has an output power of +10 dBm, a wide coverage of the frequency range and is programmed in C language. This device has no safe firmware, it can be “flashed” with the help of Travis utility called GoodFET. Unfortunately, it is not compatible with the JTAG interface and RF connectors, but they are fairly easy to add.
So, we can write the firmware for this device, we know the corresponding frequencies, so we can bring the frequency and power in line with the USRP, combine and amplify the signals of the main station and the additional transmitter.
Now consider the installation of a base transceiver station cellular BTS. So, I have an IMEI for a radio amateur, this is what I need for GSM, and now I need a universal software radio USRP. All peripherals are available for it online, there it costs about $ 1,500 for two RFX900 daughter boards.
In addition, you need a device called ClockTamer - code.google.com/p/clock-tamer , which allows you to create a very accurate clock generator to synchronize with GPS. It is specifically designed to be shared with the USRP.

Phones receive their frequencies from base stations. Base stations provide highly accurate frequencies, and phones find out how compatible their own frequencies are with the frequency of the transmitting station.
So if I come from the side with my own station, the frequency stability of which does not match the frequency stability of the local towers, which are located around, then all the phones will be calibrated to the frequency of these local towers and will not even pay attention to my station, even if the difference of our frequencies will be only a few kilohertz.
"Right out of the box" ClockTamer extremely accurately adjusts the frequency in increments of ± 100 Hz in the range of up to 1.9 GHz, compared to this accuracy, the GPS module is just sucks. This device has a crazy precision and is flexible to program.
The software of my cellular station provides a laptop with Debian, OpenBTS and Asterix. OpenBTS provides everything connected with GSM, Asterix receives calls from OpenBTS and sends them via VoIP. I used the basic version of BTS, it transmits voice and SMS, but does not transmit data.
For this presentation, I have disabled the use of SMS, mainly due to the fact that it is difficult for me to get your caller ID when you send SMS. Yes, I can send it via the Internet and connect it to where it should be connected, but the person who receives it will not be able to determine who it came from and will not be able to answer. So I thought that it would be easier to simply disable this feature of BTS, although the system supports it.
So, let's get down to the first demo and run BTS in test mode. I am connecting to the USRP laptop, everything else is already on, so let's launch the base station. I do not know how much you can see the image on the screen of my laptop, now I will move it closer to the camera. The only thing I want to show is the launch of the TMSI command — it shows me a list of all the temporary MSIs that were allocated by the base station, in other words, how many people are currently connected to it. At the bottom of the screen you can see that in table 0, that is, at the moment no one is connected to my network.
Now I will type some more commands. Cell ID is a cell ID, which indicates that the mobile country code that I am currently using is 001, 00 is a country code according to the GSM specification, 1 means a test. Then I use the MNC mobile network code, it is 01, the unit here also means a test, so this is a test network in a test country, this is not Europe and not America. Below is the name of the cellular network that I represent is DEFCON18. Some phones will display it, some will not.
I want to draw your attention to the fact that at present it is not a “hostile” configuration, it is a test mode, it is not an advertisement of any known network and it does not work on the US cellular frequency, so until I start this thing, no one can connect to my network.
If you want to scan available cellular networks, you can, but I recommend that you just leave your phones alone. Just pull them out of your pockets every few minutes and try to call. In just a minute I will show you how easy it works.

So, how do I substitute a particular network to use the IMSI interceptor not just on a random network? , – MCC, , MNC – . MCC 310. . MNC 2-3 , , , , OpenBTS. . , MNC MCC, , , , .
, , . .
, №2, , MNC/ MCC . , TMSIS. ! 15 , 15 «», . 15 , . , , !
( )

: , iPhone. , , . , «». «» .
, TMSIS 30 ! , . , , MNC/ MCC. ell ID, MCC/MNC . . , , T-mobile. , , AT&T. , !
, ID . , MCC 310, AT&T. , 410, 6610. , AT&T. — Cell ID 31041066610, . , GSM, AT&T.
, . , , IMSI, 20 , AT&T, . , – . , , .
26:15
DEFCON 18. . Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/435354/
All Articles