Vulnerabilities of Kyivstar: 1) analysis of the previous post about passwords + 2) info about purchases passing through the services of Kyivstar
Hey. I am the one who six months ago received the logins and passwords of Kyivstar from such important services as: JIRA, Amazon Web Services, Apple Developer, Google Developer, Bitbucket and many others, wrote them through Bug Bounty and received $ 50 various comments on the repost of my publication .
For example:
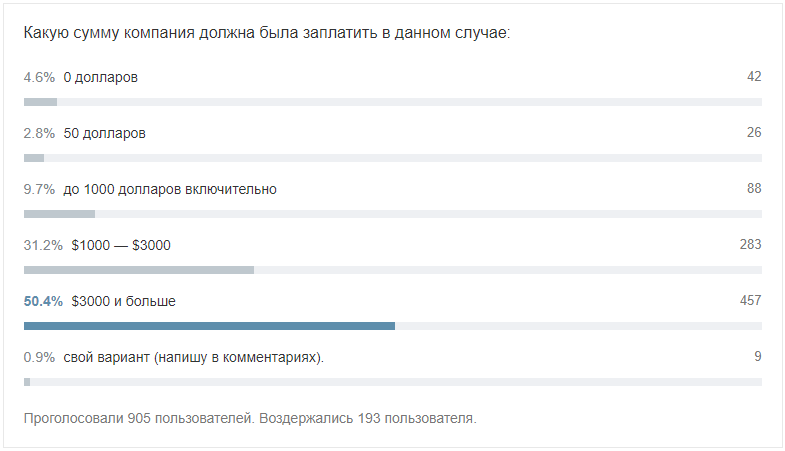
Thank you for your support and comments! Voting results:
')
For some reason I did not respond to some comments, but I cannot but answer now.
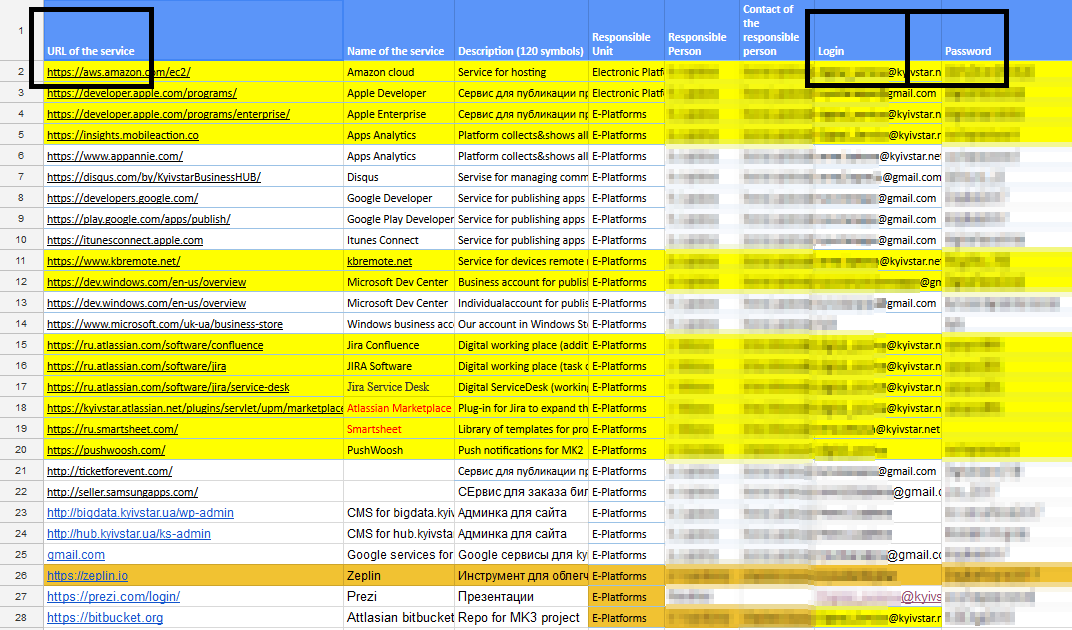
Let me remind you that I accidentally received a letter with bookmarks from the Kyivstar employee’s working browser. I opened all 113 bookmarks in turn and found a file with the names of services, logins and passwords, and other information among them. Yes, the file was on Google Docs with “For All” access rights.
When my colleague Yegor Papyshev shared his opinion on Facebook, it was unpleasant to hear how another respected person (Vladimir Styran, information security specialist - CISSP, CISA, OSCP, CEH), was negatively disposed to the situation, and wrote to Egor that he was not knows the details and did not understand the situation.
At the same time, Vladimir himself did not understand the situation. Here is his mocking post:
I will translate and comment on the last few points:
However, as I know, Vladimir participated in the launch of the Bug Bounty company Kyivstar, so I admit that he has a blurred eye.
Go ahead. A simple example: Apple Developer, you saw screenshots of their console in my post.
In the file with passwords there were still lines and columns, and specifically Apple indicated the following: Last modified - 05/18/2016.
Those. The last time the Apple developer account data was edited back in May of 2016, more than a year before I received the letter and found the link in it. Which, again, is confirmed by the fact that I was able to log in with the specified password.
Thus, speaking of the security of business processes in Kyivstar, we can summarize:
What else. Many did not understand why such a strange amount of $ 5,800 was indicated, why not exactly $ 6,000 exactly, why not just a million dollars? “In his opinion, only the official cost of accounts exceeds $ 5,800.”
The answer to this question was from the very beginning on Habré, they simply did not notice it:
The key here is " open it in a new tab " - when you click on the image ( direct link ), the full picture opens, where other columns are also visible: Last modified, Paid till (date), Need till (date), Project (as in ASUP), Type of payment, Cost, Currency.
By simply summing up the numbers from the “Cost” column, I obtained a figure of $ 5800 - this is the official (and not the cost I’ve thought of) accounts in the listed services, which I indicated in the report on Bugcrowd.
I didn’t ask or demand this amount, or any other amount, as Soultan did then, but compared their indicated reward of $ 50 with the minimum possible damage - simply speaking, with the loss of access to services, for the purchase of which they spent> $ 5800.
Further.
I added the information outlined above with a small update to the original post. I do not gloat over this. They made a mistake then - perhaps they are paying the price.
pyrk2142 in the comments asked :
And now I can say that yes, the information on Bug Bounty Kyivstar is irrelevant: I found the opportunity to receive information about the purchases of people passing through Kyivstar payment services, even if they are not its customers. I gave the company a second chance - but she did not use it .
So, the info about purchases passing through Kyivstar services, using even non-customer’s cards.
During testing of an application by one company, I discovered that Kyivstar acts as a payment provider in the framework of cooperation with Visa QR Payments - mVisa - payments using a QR code go through qrpayments.kyivstar.ua .
These are transactions of clients in such points of sale, as, for example:
An example of the data obtained:
The service responded to requests only with the correct "Authorization" and "Map-AuthToken", the last of which contained those encoded in Base64
But despite the need for the request to have the correct parameters specified above, once having received the Map-AuthToken, then it was possible to perform GET requests to the address of the form https://qrpayments.kyivstar.ua/map/api/consumers/ many times.
And although in the period since the launch, April 16, 2017, not many operations have been carried out (~ 2000 pieces) and the data obtained themselves are not critical, this situation is alarming:
even if you do not use Kyivstar, but simply pay at theU Uchan store with a B ank bank card, hackers can hack the K C provider and get information about you.
In the field of payment cards, there is a situation that fits the description: a single point of compromise - this could be a terminal, an ATM, a trading company, an acquirer, a processing center through which there were thefts from different cards of different customers.
Transferring the situation to this mobile operator: hacking one service, you can get information from several.
Before publishing this material, I gave Kievstar a second chance - I sent three letters to bounty@kyivstar.net, which is listed on their special page : December 17th, December 20th and December 27th, all working days.
I sent, just in case, from a box that was not specified in a situation with leaked passwords. Letters received, but no feedback, even an automatic response, was not followed.
As you understand, the vulnerability is not covered, so I can’t give more details. However, everything is clear.
For example:
- Actually, Habr, 33 thousand views, 188 comments: Bug Bounty Kyivstar: a reward for admin access to Jira, AWS, Apple, Google Developer, Bitbucket services - $ 50
- AIN.UA, 12 thousand views: Tester got access to Kyivstar corporate services. He was offered only $ 50
- ITC.ua, 350 comments: Kyivstar offered the user $ 50 for the found passwords to corporate systems, he was not satisfied
- Ebanoe.IT, 26 thousand views, 169 comments: Hacker was given a handout of $ 50 for a found vulnerability in Kyivstar
Thank you for your support and comments! Voting results:
')

For some reason I did not respond to some comments, but I cannot but answer now.
Let me remind you that I accidentally received a letter with bookmarks from the Kyivstar employee’s working browser. I opened all 113 bookmarks in turn and found a file with the names of services, logins and passwords, and other information among them. Yes, the file was on Google Docs with “For All” access rights.
I had concerns in their future reaction to the report, so
First, I told Bugcrowd to urgently change their passwords. I was told that they know about indexing files from a post on Habré and have already closed such files everywhere.
I indicated that they had not closed, and sent screenshots, where it is clear that I could enter randomly into their accounts.
Then I was asked how I received such data, and I indicated how (received by e-mail).
Then they asked how I could receive such an e-mail - and I replied that I was lucky, or simply the employee was sealed when she sent the bookmarks to herself (as it turned out).
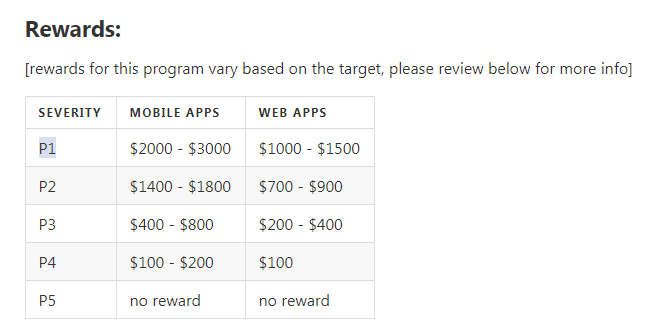
During the correspondence, my signal was assigned the highest priority - P1 (Sensitive Data Exposure: Critically Sensitive Data - Password Disclosure), within which payments range from $ 1000 to $ 3000 (and you can also add Mobile + WEB apps).
Well, then you know.
I indicated that they had not closed, and sent screenshots, where it is clear that I could enter randomly into their accounts.
Then I was asked how I received such data, and I indicated how (received by e-mail).
Then they asked how I could receive such an e-mail - and I replied that I was lucky, or simply the employee was sealed when she sent the bookmarks to herself (as it turned out).
During the correspondence, my signal was assigned the highest priority - P1 (Sensitive Data Exposure: Critically Sensitive Data - Password Disclosure), within which payments range from $ 1000 to $ 3000 (and you can also add Mobile + WEB apps).

Well, then you know.
When my colleague Yegor Papyshev shared his opinion on Facebook, it was unpleasant to hear how another respected person (Vladimir Styran, information security specialist - CISSP, CISA, OSCP, CEH), was negatively disposed to the situation, and wrote to Egor that he was not knows the details and did not understand the situation.
At the same time, Vladimir himself did not understand the situation. Here is his mocking post:
I will translate and comment on the last few points:
- If you do not know that the support of the broker, through which you told the vendor a bug, could actually appeal against the amount of the payment, because in general this is one of his roles in your trilateral relations, this is called lohanut. - The support Bugcrowd in correspondence with me has repeatedly supported my opinion and the opinion of the majority that Kyivstar is wrong and should have paid more. "Broker" could not affect the operator. And I was not stuck here.
- If you begin to threaten the vendor of Full Disclosure in the event of no increase in payments, this is called extortion or blackmail. But most likely it will be called extortion, because there is no article for blackmail in the code. - There was no blackmail and extortion. There was no threat. Vladimir would have known about this if he had read that report. That is characteristic, my account on Bugcrowd was blocked (it is not scary) not immediately after the post on Habré, but about a week later, just at the same time as his other caustic post in FB.
- If you don't have a bug, you read about it on Habré, you told about it on your Facebook page to get N likes and + M followers, then you are a blogger and there is nothing to be proud of. - There is nothing to add.
However, as I know, Vladimir participated in the launch of the Bug Bounty company Kyivstar, so I admit that he has a blurred eye.
Go ahead. A simple example: Apple Developer, you saw screenshots of their console in my post.
In the file with passwords there were still lines and columns, and specifically Apple indicated the following: Last modified - 05/18/2016.
Those. The last time the Apple developer account data was edited back in May of 2016, more than a year before I received the letter and found the link in it. Which, again, is confirmed by the fact that I was able to log in with the specified password.
Thus, speaking of the security of business processes in Kyivstar, we can summarize:
- moreover, logins and passwords were stored (or stored?) on an external shared Google Docs resource with “For all” access rights,
- not only does not require two-factor authentication for entry,
- not only that many passwords were dictionary and easily selectable and looked like (changed) upsups92, suchapassword, DigitTeam2017, Digital2016, Kyivstardigteam2017, ks-anya $ bd2016, KSDigit2018,
- so these passwords have not changed yet for more than a year.
What else. Many did not understand why such a strange amount of $ 5,800 was indicated, why not exactly $ 6,000 exactly, why not just a million dollars? “In his opinion, only the official cost of accounts exceeds $ 5,800.”
The answer to this question was from the very beginning on Habré, they simply did not notice it:
(to enlarge the image, open it in a new tab)
The key here is " open it in a new tab " - when you click on the image ( direct link ), the full picture opens, where other columns are also visible: Last modified, Paid till (date), Need till (date), Project (as in ASUP), Type of payment, Cost, Currency.
By simply summing up the numbers from the “Cost” column, I obtained a figure of $ 5800 - this is the official (and not the cost I’ve thought of) accounts in the listed services, which I indicated in the report on Bugcrowd.
I didn’t ask or demand this amount, or any other amount, as Soultan did then, but compared their indicated reward of $ 50 with the minimum possible damage - simply speaking, with the loss of access to services, for the purchase of which they spent> $ 5800.
Further.
If anyone is interested, not so long ago, the Kyivstar BugBounty program was closed completely (not a private mode, but it was closed), and an employee of Soultan, who responded to comments here, recently left Kyivstar.
By the way, in the comments under his farewell record of leaving the company he writes “Good luck, Vitaly!” An employee, who sent that ill-fated e-mail. So it goes.
I added the information outlined above with a small update to the original post. I do not gloat over this. They made a mistake then - perhaps they are paying the price.
pyrk2142 in the comments asked :
This is quite unexpected. It turns out that the information is no longer relevant here?
And now I can say that yes, the information on Bug Bounty Kyivstar is irrelevant: I found the opportunity to receive information about the purchases of people passing through Kyivstar payment services, even if they are not its customers. I gave the company a second chance - but she did not use it .
So, the info about purchases passing through Kyivstar services, using even non-customer’s cards.
During testing of an application by one company, I discovered that Kyivstar acts as a payment provider in the framework of cooperation with Visa QR Payments - mVisa - payments using a QR code go through qrpayments.kyivstar.ua .
These are transactions of clients in such points of sale, as, for example:
- Crema Caffe, Kyiv,
- Smachno, Kyiv,
- Third Floor Cafe, Kyiv - the first and most often operations were here. Apparently, this is a cafe on the 3rd floor in the Kyivstar office, where they started testing QR payments;
- Auchan, Kyev,
- Auchan, Lviv,
- Auchan, Dnipropetrovska - Auchan hypermarket chain (Ukraine);
- mVisa merchant;
- GIVC, Kiev - Main Information and Information Center, Main Information and Computing Center, Kiev. Here there are accruals and payments for the majority of utility payments of residents of Kiev;
- GERC, Odesa - GERC, City Single Settlement Center, Odessa. Similar to the GIVTS above, only the coverage is even greater: the site is intended not only for the population of Odessa, but also for such cities as: Kiev, Belgorod-Dniester, Reni, Chernomorsk and Yuzhny;
- and so forth
An example of the data obtained:
{"Id":1305 Date:"2018-10-05T15:15:42.3921295" State:0 Amount:-1278.8100 TipsAmount:0.0000 Currency:"UAH" MerchantName:"Auchan" MerchantCity:"Lviv" MerchantId:"4109499405597549" ApprovalCode:"516634" ReferenceNumber:"" CardNumber:"5375XXXXXXXX3858"} {"Id":1308 Date:"2018-10-06T12:43:31.1179667" State:3 Amount:-4192.9700 TipsAmount:0.0000 Currency:"UAH" MerchantName:"Auchan" MerchantCity:"Kyev" MerchantId:"4109494835704666" ApprovalCode:"" ReferenceNumber:"827991150697" CardNumber:"4824XXXXXXXX6937"} {"Id":1702 Date:"2018-12-06T18:40:02.657213" State:3 Amount:-81.0000 TipsAmount:0.0000 Currency:"UAH" MerchantName:"GIVC" MerchantCity:"Kiev" MerchantId:"4109499632222754" ApprovalCode:"605231" ReferenceNumber:"834091189417" CardNumber:"5168XXXXXXXX9997"} The service responded to requests only with the correct "Authorization" and "Map-AuthToken", the last of which contained those encoded in Base64
{"alg":"RS256","kid":"33E283272B0433E283281FF404CA6F031E28320","typ":"JWT"}{"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/mobilephone":"0800300466", "http://schemas.lime-systems.com/identity/claims/authId":"1199333", "http://schemas.lime-systems.com/identity/claims/userId":"25046", "http://schemas.lime-systems.com/identity/claims/deviceId":"12342", "nbf":1541370000, "exp":1541380001, "iat":1541390001, "iss":"http://localhost", "aud":"http://localhost"} and other data.But despite the need for the request to have the correct parameters specified above, once having received the Map-AuthToken, then it was possible to perform GET requests to the address of the form https://qrpayments.kyivstar.ua/map/api/consumers/ many times.
And although in the period since the launch, April 16, 2017, not many operations have been carried out (~ 2000 pieces) and the data obtained themselves are not critical, this situation is alarming:
even if you do not use Kyivstar, but simply pay at the
In the field of payment cards, there is a situation that fits the description: a single point of compromise - this could be a terminal, an ATM, a trading company, an acquirer, a processing center through which there were thefts from different cards of different customers.
Transferring the situation to this mobile operator: hacking one service, you can get information from several.
Before publishing this material, I gave Kievstar a second chance - I sent three letters to bounty@kyivstar.net, which is listed on their special page : December 17th, December 20th and December 27th, all working days.
I sent, just in case, from a box that was not specified in a situation with leaked passwords. Letters received, but no feedback, even an automatic response, was not followed.
As you understand, the vulnerability is not covered, so I can’t give more details. However, everything is clear.

Source: https://habr.com/ru/post/435074/
All Articles