Import Substitution Operating Systems. How do I see domestic OS
 When we talk about the distribution of the operating system, then it is, first of all, not about the kernel of the operating system, but about the applications that are part of the distribution. And when we talk about import substitution of operating systems, then we are talking about a particular version of Linux. Nothing else is proposed for import substitution in the Russian market. As for the linux kernel, Linus Benedict Torvalds is responsible for its development. And to be honest, I don’t know anything about the Russian linux kernel. But the environment of any linux distribution is developed by various organizations, and not to list them all: KDE, Mozilla, Google, IBM, etc. etc. And one would expect that with the advent of domestic OS ala linux, this list will be expanded with domestic developments or modifications. But this is not. No, this is not necessarily a domestic browser or email client in these distributions. But I would like to see something refined to reflect the Russian realities in the digital economy. Let's stop on this.
When we talk about the distribution of the operating system, then it is, first of all, not about the kernel of the operating system, but about the applications that are part of the distribution. And when we talk about import substitution of operating systems, then we are talking about a particular version of Linux. Nothing else is proposed for import substitution in the Russian market. As for the linux kernel, Linus Benedict Torvalds is responsible for its development. And to be honest, I don’t know anything about the Russian linux kernel. But the environment of any linux distribution is developed by various organizations, and not to list them all: KDE, Mozilla, Google, IBM, etc. etc. And one would expect that with the advent of domestic OS ala linux, this list will be expanded with domestic developments or modifications. But this is not. No, this is not necessarily a domestic browser or email client in these distributions. But I would like to see something refined to reflect the Russian realities in the digital economy. Let's stop on this.They will say to me: “Why, what does not suit from what is?”. First, if we don’t contribute anything, then why do we call “domestic software”? Only due to the fact that, at best, is stored in Russia? As an example, let's consider the use of X509 electronic certificates, electronic signatures, encryption of documents and traffic (tls / https). And this helped me a very interesting analysis (in some ways I may not agree with him, but this is particular) problems with the use of digital signature tools that arise for users of Linux. Here is one of the conclusions:
In some cases, developers of public service portals recommend using non-Registry operating systems, as well as software and configurations that deliberately reduce the security of user data.By the words “non-registered operating systems”, naturally, one should understand MS Windows. The state service portal should be considered a benchmark among state and other services portals. It allows you to work with it with any native Linux family of OS. All in all, the plugin that it distributes provides support for the PKCS # 11 standard for tokens / smartcards and this makes it independent of the OS, and for MS Windows it provides support for the MS CSP standard with Russian cryptoalgorithms. And that's all. It (the state service plugin) does not impose a cryptographic provider (whether it is CSP or PKCS # 11) from one manufacturer or another, it checks the cryptographic provider’s compliance with the standard. And why this positive experience does not extend to other departments mystery. Moreover, the practice of plug-ins is still flawed, it binds the user one way or another to certain operating systems, and even browsers. This browser supports these plugins (of which one CAPICOM costs), but this one does not, etc. Why not to request in the authentication process, for example, that the user provides his business card or something of that kind signed by him, his means to the portal.
And so, the first thing that needs to be done is to untie, make the service portals independent of the OS and crypto-providers, including modernizing the portal of state services.
But today it comes to the ridiculous, the whole company works on a domestic OS (including accounting), but for access to the FTS (GOST-tovy tls / https is required) they keep a special computer with MS Windows.
Above, we talked about the improvements in domestic OS. Let's go back to them. Why and why they are needed. Today, having bought and installed a domestic OS on a workplace, the Russian consumer turns out to receive nothing from the point of view of Russian cryptography: he cannot create a request for a certificate (what is so well written here ), do not view the GOST certificate normally, do not sign the document or check Signature, do not protect your email. Immediately the question arises: - “And what have I acquired? Whether it was easier to download the Linux distribution on the Internet, especially since they are constantly evolving. ” In the West or the East, people acquiring (not necessarily for money) the OS immediately receive a bunch of useful services. And where are our Linux distributions with browsers or email clients using Russian cryptography, where are the utilities that allow us to verify the electronic signature delivered by the FTS under an extract from the Unified State Register? Etc. I do not know such distributions. Therefore, I take the Mageia distribution kit and fasten to it everything that I am writing here:
')
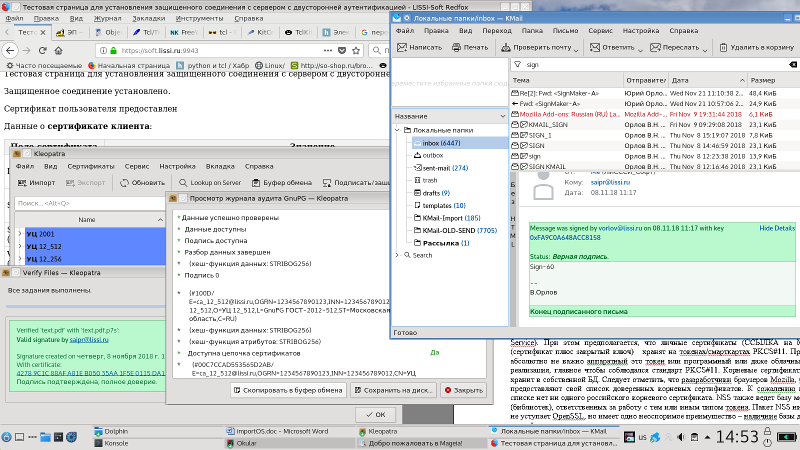
How certificates are stored and keys are used in most Linux applications. The absolute majority of applications in Linux (Mozilla, Google, LibreOffice, GnuPG, etc., etc.) use the NSS (Network Security Service) package as a certificate store:

It is assumed that personal certificates (certificate plus private key) are stored on PKCS # 11 tokens / smartcards. At the same time, it is absolutely not important whether the hardware is a token or software or even cloud. This is an implementation, the main thing is to comply with the PKCS # 11 standard. NSS root certificates are stored in their own database. It should be noted that developers of Mozilla, Google browsers provide their list of trusted root certificates. Unfortunately, there is not a single Russian root certificate in this list. NSS also maintains a database of modules (libraries) responsible for working with one type of token or another. The NSS package is not inferior to OpenSSL in any way, but it has one indisputable advantage - the availability of a certificate database.
And what do we have in the end? The NSS package, which is included in the domestic Linux distributions, does not support the work with the national GOST-based tokens PKCS # 11. And this leads to the fact that Firefox and other programs do not want to work with domestic tokens. Do we have domestic tokens with built-in support for GOSTs? It turns out there are in sufficient quantities. This and hardware tokens from different manufacturers:

Unfortunately, the vast majority of hardware tokens today is used as an ordinary flash drive for storing keys and certificates.
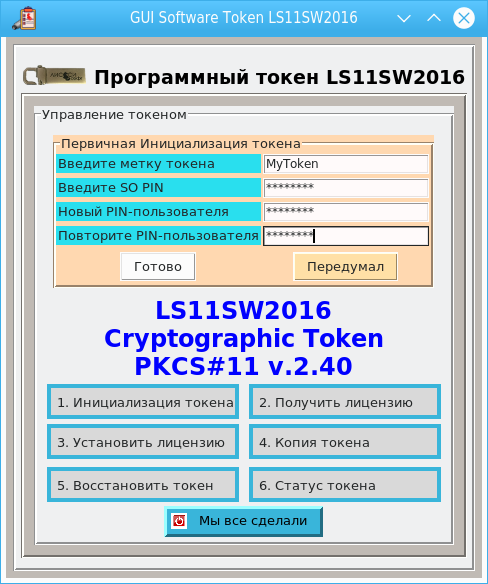
There are free software tokens both non-certified and certified:
And even PKCS # 11 cloud tokens are available:

It is also a shame that the NSS package, which includes a number of utilities, comes with bugs that sometimes appear only on GOST certificates ( calgoid , pp ).
And it would be great if the composition of domestic distributions included the NSS package, which supports the work with PKCS # 11 tokens with GOST-based cryptography. It can be objected, it is difficult, expensive, etc. But if the developers were interested, then they knew that back in 2010 a bug was registered with GOST for NSS. I myself monitor NSS and add support for it to GOST, starting with version NSS-3.11 and up to the present NSS-3.41. And with whom I have just not met over the years (anyone can count), the result is zero. I like the answer: “Did they add them there in the west?” But they do not need. And it turns out to us too.
And now, if NSS with the support of GOSTs would be in domestic distributions, it would have been possible to add support for GOSTs in Firefox, Thunderbird, KMail , LibreOffice , etc. with a little blood. And about all this one way or another on the pages of Habr was written. Yes, I almost missed OpenSSL with GOST. There are also versions certified by the FSB of Russia. And openssl with GOST s almost automatically leads to the appearance in domestic distributions and versions of openvpn at GOST s:

Let's add Apache here, with tls / https support on GOST, but PHP and GOST won't hurt.
And in the hands of the user of the domestic OS, there would already be both openssl and p7sign / p7verify utilities for signing files with electronic signature. But there would be a Cleopatra graphic utility for the same purpose and a GUI for NSS .
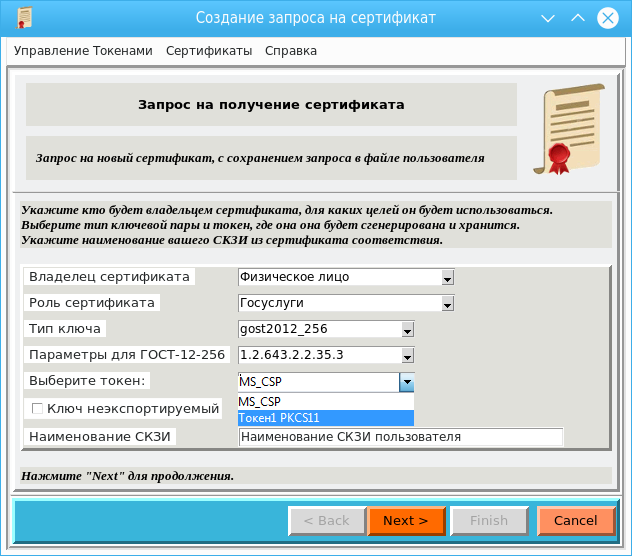
To create a certificate request, you could use the guicreate_csp utility:
And if someone wanted to deploy a certification center in their enterprise, then please:
Someone might have said, but what about certification? And in the west they sell and use certified Linux? Of course not. But after all, all domestic manufacturers of all the above products are part of certified distributions. What prevents the certification include in the modified packages. And what would be cool distributions would be for use in the educational process in the specialty "Information Security" or in schools. In my opinion, the Ministry of Digital Development, Communications and Mass Communications of the Russian Federation should be interested in certification.
And so, what is the conclusion? I remind you, we talked about the electronic signature, about the use of domestic cryptography.
First, access to portals should not depend on the type of operating system and cryptographic provider used.
Second, domestic operating systems should have browsers with the support of GOST https.
Third, domestic OSs should include mail clients with GOST support (signing / encryption).
Fourth, domestic operating systems must have electronic signature and encryption
Fifth, domestic OSs should have support for PKCS # 11 tokens / smartcards with support for Russian cryptography.
Now, if this minimum is implemented, then we can speak from domestic operating systems such as Linux.
And not so long ago I was in the same ministry, and there I saw a unique import substitution: they were offered some kind of domestic Linux, they started a virtual machine with Windows and with all the gadgets that were used in the Ministry on Windows, and they could report on import substitution. I hope my last paragraph will not be a guide to action.
This is really cool !!! What we just do not have!
Source: https://habr.com/ru/post/434358/
All Articles