MIT course "Computer Systems Security". Lecture 22: MIT Information Security, Part 3
Massachusetts Institute of Technology. Lecture course # 6.858. "Security of computer systems". Nikolai Zeldovich, James Mykens. year 2014
Computer Systems Security is a course on the development and implementation of secure computer systems. Lectures cover threat models, attacks that compromise security, and security methods based on the latest scientific work. Topics include operating system (OS) security, capabilities, information flow control, language security, network protocols, hardware protection and security in web applications.
Lecture 1: "Introduction: threat models" Part 1 / Part 2 / Part 3
Lecture 2: "Control of hacker attacks" Part 1 / Part 2 / Part 3
Lecture 3: "Buffer overflow: exploits and protection" Part 1 / Part 2 / Part 3
Lecture 4: "Separation of privileges" Part 1 / Part 2 / Part 3
Lecture 5: "Where Security Errors Come From" Part 1 / Part 2
Lecture 6: "Opportunities" Part 1 / Part 2 / Part 3
Lecture 7: "Sandbox Native Client" Part 1 / Part 2 / Part 3
Lecture 8: "Model of network security" Part 1 / Part 2 / Part 3
Lecture 9: "Web Application Security" Part 1 / Part 2 / Part 3
Lecture 10: "Symbolic execution" Part 1 / Part 2 / Part 3
Lecture 11: "Ur / Web programming language" Part 1 / Part 2 / Part 3
Lecture 12: "Network Security" Part 1 / Part 2 / Part 3
Lecture 13: "Network Protocols" Part 1 / Part 2 / Part 3
Lecture 14: "SSL and HTTPS" Part 1 / Part 2 / Part 3
Lecture 15: "Medical Software" Part 1 / Part 2 / Part 3
Lecture 16: "Attacks through the side channel" Part 1 / Part 2 / Part 3
Lecture 17: "User Authentication" Part 1 / Part 2 / Part 3
Lecture 18: "Private Internet browsing" Part 1 / Part 2 / Part 3
Lecture 19: "Anonymous Networks" Part 1 / Part 2 / Part 3
Lecture 20: “Mobile Phone Security” Part 1 / Part 2 / Part 3
Lecture 21: “Data Tracking” Part 1 / Part 2 / Part 3
Lecture 22: MIT Information Security Part 1 / Part 2 / Part 3
The next slide shows a message with Gizmodo, this is what I call trolling. From the direction of the attackers, it looked a bit evasive, no matter how many. Here they tell the whole world how they hacked our network, practically the day after it happened.
')
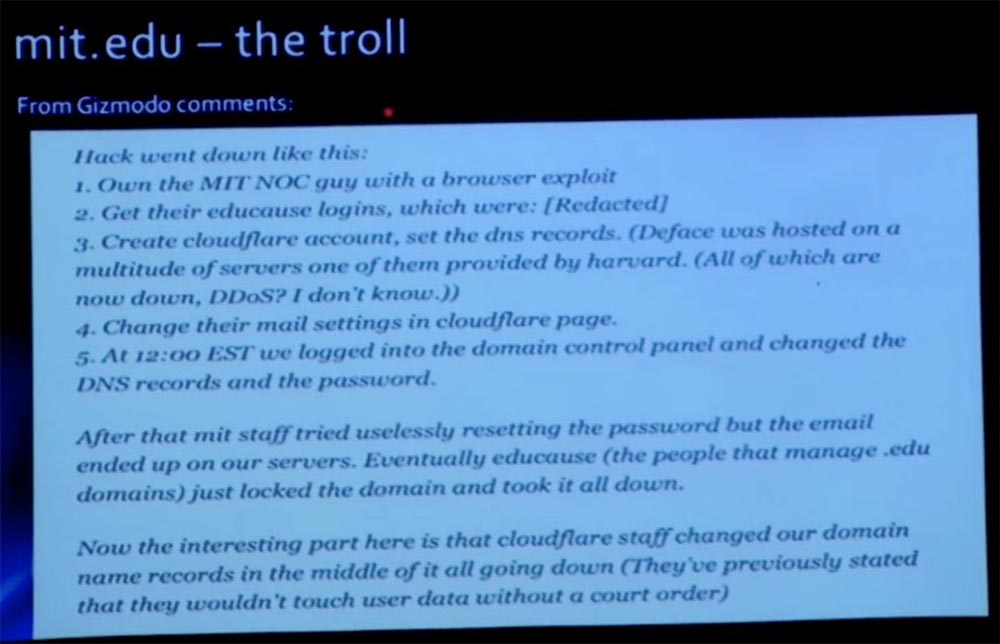
However, as soon as we realized that it was not MIT or anything that had been hacked into our mit.net network, but our registrar, we immediately contacted him, changed our records and blocked everything. However, there was some time in the DNS for some time, some of which exist for hours, so after taking action, we still observed some traffic flow. And while we were trying to eliminate the consequences of the attack, hackers publish such comments on Gizmodo: “They captured a guy from the network control center using a browser exploit”. Boyfriend “We got their training logins that were blah blah blah,” and so on. That is, the attack vector was supposedly a guy from the MIT NOC network control center.
Mark swore that it was not him. In fact, he did not swear, but explained that he was not compromised in any way. Therefore, after the incident, we published the truth about how the attack was actually organized. This link www.exploit-db.com/papers/25306 is still valid if you want to read about it. In fact, hackers hacked into the registrar account of our domain EDUCAUSE. It turns out that every DNS account has been compromised. We do not know how long the hackers owned this data before they decided to use it to attack MIT. There was no fault of our institute in the incident. Later, in 2013, the registrar admitted his mistake of providing access to the top-level domain, and we all had to change passwords, since about 7,000 domain names mit.edu were compromised.
As a result, we have blocked our domain account so that it cannot be changed, but you know that if you tick the box "locked", which does not allow people to update the system, it is not very good. In any case, they fixed their system. So, this was not our fault, but such an attack was interesting in the sense that it showed how some of the basic Internet protocols could be used to attack.
So, the current threat landscape consists of two components: social attacks and network-based attacks. Social attacks can be characterized with the motto: “If you cannot use silicon, use carbon”! In other words, if you were unable to penetrate the victim's “iron”, hack the user through his keyboard. This is what is now observed especially often.
Based on my own 20 years of experience, I can say that network attacks that remotely use hosts do not happen often. Computer systems are becoming increasingly secure, at least outside. You know, in the old days, maybe ten years ago, Windows, Solaris, and Linux were sold with all of their services, and I said that they glowed like a Christmas tree. Everything was included, because of the two criteria - convenience and security - they chose convenience, they wanted the user to get everything out of the box.

Now, I think we have found a reasonable compromise. When you install a "fresh" operating system, it starts a host-based firewall and there are no publicly available services. We have such things as Windows update and Apple update, there are package managers in all Linux distributions, so the OS out of the box, having access to the Internet, will quickly update to the current version. Now you do not have these ancient boxes with ancient services open to the whole world.
So, I tend to the fact that hackers climbed up the stack, perhaps on the eighth or ninth level. Now they deal more with people than with computers. And they try to use human weaknesses or weaknesses, such as fear, greed, gullibility, sociability, to take advantage of the rights of a legitimate user and gain access to applications or privileged access to the system. Instead of using hosts, they use people.
Recently on campus, we witnessed events called “targeted phishing.” I don't want to scare anyone. Manifestations of these attacks were observed in educational institutions throughout the country. This is a very serious threat, so we had to hurry to solve this problem, but MIT did not have to deal with such attacks directly. Targeted phishing is targeted at a specific community and uses believable messages. In the usual spam or phishing attacker, the attacker simply massively sends messages over the Internet, throwing a spammer network to catch people who, for some strange reason, may respond to these messages.
However, when targeted phishing, attackers narrow their network and find a community that believes in the credibility of the message received, for example, the Bank of America customer community or the MIT student, staff and faculty community. In this case, they were able to select communities of various institutions. For example, Boston University was one such community. Attackers attack the community with bogus e-mail messages pointing to a fictitious authentication site. A certain percentage of users clicked on the link and logged in, which, of course, provided the attacker with credentials. Then the attacker went to the real site and redirected the savings of these users to his account. The amount of damage was not reported, but I think it was big.
How can you deal with this? This is largely a problem of the ignorance of the user, so it is necessary to inform the community about this type of fraud. Just tell people that they don’t have to trust email and they’ll have to check links before clicking on them. However, from the experience and knowledge of human nature it follows that there will always be a certain percentage of users who ignore this warning and click where it does not follow, and I am just amazed by this. You can imagine that my mailbox is the recipient of all phishing emails addressed to members of my family. I receive mail from my father, from my sister, and sometimes it is difficult to determine its authenticity, so you should always pay attention to the address of the sender of the letters.
At present, many email clients do not like to show you a link to their address, which is very annoying, so that it becomes more difficult to identify the sender of the letter.

In my opinion, the root of the problem is that passwords are just dead technology. It is based on what you know - this is a password; what you are is biometrics; and on what you own is a token. The man-in-the-middle attack simply steals what you know, that is, the password. But if you can add something to it, it will stop the attack half way, and hackers will not be able to compromise your identity.
In the near future, we will launch a second authentication factor that will be tied to IDP Touchstone. You can familiarize yourself with the early access to this function if you visit duo.mit.edu, where we use a vendor called Duo Security. This is a two-factor authentication cloud system that is used in many educational institutions. The principle of operation is that you register your phone as the second factor and use a small mobile application for it. If you do not have a smartphone, you can authenticate using SMS, that is, the system will send you a message with a number. You can also create lists of 10 one-time passwords. In the near future, we will provide this system to the MIT community, at the moment it is fully functional, but not yet announced.
If you want to go to duo.mit.edu, you can select your phone and include the Touchstone user ID. Now I will show you a short demo about how the integration into the system takes place. The beauty of using standards and federated systems like SAML and Shibboleth, which are at the heart of Touchstone, is that we can easily lay down additional authentication factors. I intend to simply go to the tool that I use, and that will visually authenticate my Touchstone authentication with my certificate.
Now I use the address atlas.mit.edu. So, here is my usual Touchstone login, I’ll click Continue and get another invitation.
Unfortunately, it seems that I can not connect to Wi-Fi. Well, let's leave the demo for later, later we will edit the videotape of this lecture (audience laughter).
I did not rehearse this demo, so it happened. But trust me, it works. If you enter through the Duo, you can register, and all your interactions with Touchstone will now be two-factor. With this authentication scheme, you will be completely safe. It really works well.
Another threat that we have faced in the past few months is also targeted phishing, not only from educational institutions, but from people all over the country. We call this "police ID spoofing." And this kind of fraud goes beyond the digital world. The scam is that members of the MIT community are called from a police station located near their hometown. Police officers give them bad news. They say that you will soon be charged with tax fraud, or report that an accident has happened to your relative and offer to solve the problem for a certain amount.
Of course, in reality there is nothing of this. The call comes from an attacker who uses an outgoing call spoofing by using a fake ANI and SIP phone number, which is configured so that the received call trusts any information located in the "From" field, regardless of which number the call actually came from.
Mark Silis: The attacker signs up for a cheap SIP service, sets the phone number of a Lexington police station in his field, and sends you a message. This service is called “SIP-telephony numbers with substitution”. As soon as the call reaches the transcoding gateway, which turns it back into traditional telephony, the program says that everything is in order - this is the correct number, and we will show it to the user.

David Laporte: so you end up getting a call with very bad news from a place that you think is a police station. Again, criminals exploit human weakness. In this case, it is probably fear.
Mark Silis: or guilt.
David Laporte: Yes, if you did not break the law (laughs). But in any case, the essence of all calls comes down to the fact that you have to pay for something, although this may seem like a fraud. But if they say that my wife got into a car accident, I will not be able to calmly assess the situation and believe any absurd information that I can be told.
We had several people on campus who received such calls. I don't think they paid, but they were the targets of this attack. Again, this is not only ours. If you search Google for information, you’ll find messages about such calls in Pittsburgh newspapers and across the country.
But then again, this is a target phishing attack, right? They figure out where you live by just googling your name or by looking at a list of students or MIT employees, and find out some details about you. They just need to be plausible enough, after which they will call you, scare and engage in extortion.
In this case, mitigation is difficult because the telephone system is involved, which includes several “bridges”, which makes it extremely difficult to determine the real source of the call. Honestly, I am not a telephone guy, and for me this system consists of a lot of things that I will simply give up. But law enforcement agencies must be involved. You should contact your ISP to track these scammers along with the law enforcement agencies.
 \
\There is one more thing regarding targeted phishing via e-mail. Some people call it "whaling" - it is a targeted attack on the top management of the organization.
I ran into this elsewhere, but we also experienced similar attacks here.
Attackers sent targeted messages to MIT executives using employee lists for greater likelihood of information. Being insufficiently attentive, the victims reacted to such messages. For example, an acquaintance asked for money to be transferred to him, and the real person on whose behalf the letter came was not aware of him. By agreeing, the victim sent money to someone on the other side of the country or on the other side of the world. So we also experienced this.
In short, be aware - SMTP is not a reliable protocol. With it, you can not check anything. So treat everything with distrust.
Mark Silis: are you going to tell them our story?
David Laporte: no, let's get you better!
Mark Sailis : well, it happened recently, I will not go into details and disclose names in order to preserve anonymity. So, one of the representatives of the MIT top administration reaches out to me and says: “Hey, I received this letter. It was from a high-ranking leader who asked me for help and asked me to transfer some money to him. I answered him, but he said that he did not know what I was talking about. How could this happen? Has someone hacked my email account? ”
According to Dave, people cannot imagine that email can be somehow forged without hacking into their mailbox, because this is a trust relationship.
It turns out it was someone's internet cafe in Nigeria or something like that. The attacker simply got acquainted with the organizational structure of MIT, found the senior executive director, found someone in the office of the vice-president for finance and wrote: “Hey, I need you to help me with this bank transfer, here is the account number”. Such things happen every day. Obviously, our employee has not transferred any money.
David Laporte: Was the letter absolutely believable?
Mark Sailis: yes.
David Laporte: I've already seen it.
Mark Sailis: even the tone of the letter and everything else seemed very believable.
David Laporte: Yes.

Mark Silis: In fact, the attacker took email messages written by a senior manager for public websites because they send notes to the community and the like, which use exactly the same style, introduction and ending messages. Even the language and terms they used were identical. It was a material that the attacker turned to his advantage. Even I was surprised how plausible this message looked.
David Laporte: fortunately, the employee who was asked about it, took this message as extraordinary, although it looked quite plausible and decided to contact those whom he considered the sender of the letter, thanks to which the fraudulent scheme was revealed. However, things could not happen so quickly.
Therefore, I mentioned that today, in my experience, the network attack vector is not as common as before. . SSL Heartbleed, SChannel Microsoft POODLE SSL v.3.
SSL , , , SSL. , , . Shellshock , Bash, . « » . . , , , .
? , . , - .
-, . , «» . « », , , , . , , , , , , , , .

– . StealthWatch, , «» NetFlow , . , IP- MIT, , .
, «» IP-. , .
BGP, . , . 5 , , . , Shellshock SSL, , , , , - IP- , , , , . .
, IT-. « », MIT . , BYOD, . BYOD , , .
MIT , , , Dropbox, . Dropbox — , , . , , , , , ? , Dropbo , ? , «» , , Dropbox . , IT -, .
. , . , .
. , . , , , , , . , . , - Amazon, Salesforce.com, Google Apps Dropbox. , . . , ?
, SAML , MIT SAML. Dropbox, Touchstone.

, , , , , , SAML Shibboleth, .
– « », mit.net . , , . . , mit.net . . VRF — , , . , . «».
, . , IP- , , , IP- ? , , , .
, , . , — 802.1 X, , , , , , .
.
: , .
: , ! !
: , , Linux Windows, . mit.net , .
, , . , MIT — -, . . . . .

, , - . -, - . 1-2 . , . , , , . , - -, , .
: MIT?
: StealthWatch, , 80% HTTP.
: HTTP- .
: , , . , , , ( ). , , , . , . , , , MIT . , , - - -.
: , . , Netflix, Netflix, . , , Netflix «».
: , , . , , , . -…
: -?
: ?
: , , !
: , . , ? ( ). «», , . , - . , . , , Netflix Amazon Prime, $4 , . Comcast. IPTV, . , , .
: , , !
: , !
: !
.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/434346/
All Articles