Network Security Trends in 2019
So it is accepted that at the end of each year, companies remind of themselves, sharing their achievements and publishing forecasts, which, by a lucky chance, are connected with the company's products. I will not break this tradition with two small additions. I will not talk about our achievements over the past year; Perhaps I will write about it in our corporate blog . And with the predictions, the situation is not so obvious advertising. We have a lot to say in the context of cyber security, but I will try to focus on what other companies don’t usually mention, but it’s very important and what should be taken into account in its information security strategy in 2019. In addition, I will not hide, to part of the described trends, we ourselves had a hand. Among other things, we’ll talk about BGP and CDN vulnerabilities, network device hacking, upcoming TLS 1.3 and 5G networks, APIs and cyber attacks.

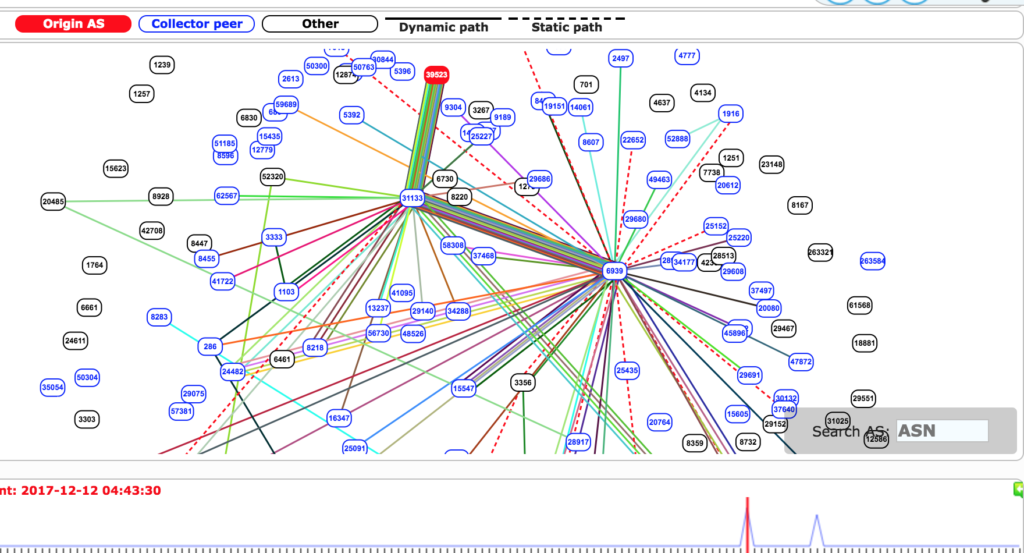
Recently, vulnerabilities have become more frequent in the BGP Internet Routing Protocol. Intercepting and redirecting traffic allows you to analyze and manipulate it, which leads to theft of cryptocurrency, breach of confidentiality, and restoration of control over computers under police control. In the autumn of 2018, a new scheme was used, which was used by cybercriminals for fraudulent Internet advertising. The attacker's operation, dubbed 3ve , allowed the traffic of over 1.5 million IP addresses to be intercepted and made advertising companies believe that billions of Internet banner hits were actually seen by real users. Yes, this is not a theft of traffic from a UK nuclear weapons agency. And yes, this is not intercepting the traffic of 1300 Amazon addresses in order to disguise the MyEtherWallet website with the subsequent theft of 150 thousand dollars in cryptocurrency. And this is not intercepting the traffic of two dozen financial organizations, including MasterCard and Visa (as well as Symantec and Verisign). Some annoying ads that we all try to remove using plug-ins and specialized software. But for advertising campaigns, this attack cost $ 29 million, which was “thrown into the abyss”, that is, paid to fraudsters who exploited vulnerabilities and incorrectly configured BGP.
')
What Cisco will answer : to neutralize the implementation of random or malicious threats via BGP, we will not sell you anything :-) We simply advise you to familiarize yourself with our manuals ( here and here ) and configure your network equipment accordingly. In addition, a good recommendation would be to monitor the route information of your network using the appropriate BGP monitoring services.
45 thousand compromised routers were found at the end of November 2018. A botnet of 100,000 compromised network devices from Broadcom, Asus, TP-Link, Zyxel, D-Link, Netgear, US Robotics, and others was detected a couple of weeks earlier. In May, Cisco Talos experts discovered half a million compromised network devices in 54 countries around the world. Among the affected vendors are ASUS, D-Link, Huawei, Ubiquiti, UPVEL, ZTE, as well as Linksys, MikroTik, Netgear and TP-Link. Hacking network equipment turns from isolated cases into mainstream, as it allows attackers to gain access to large volumes of information of interest to them, which can be transmitted in unencrypted form.
What Cisco will answer : if we are talking about Cisco equipment, then we have developed many recommendations for protecting routers based on Cisco IOS , IOS XR , IOS XE operating systems, the correct implementation of which increases their security many times. In addition, we were among the first to encounter attacks on our routers (because of their popularity), we began to implement Secure Boot, boot protection, memory protection, protection against the substitution of hardware components, etc. into the equipment.
Other manufacturers should also have appropriate instructions on how to update and protect them. In addition, it will be good practice to analyze telemetry from network equipment, which allows you to identify anomalies in network traffic and timely detect compromise at the level of network infrastructure, which in 2019 will continue to interest intruders.
Attacks on network equipment reminded us of the old story that some of our customers faced around the world (there were not many of them). Not having a service contract for our equipment, they downloaded new firmware for already discontinued lines of routers from warez sites on the Internet, which led to the infection of devices, interception of information, and we were pushed to revise the strategy of self-defense of network equipment and the launch of Trustworthy Systems initiative the framework of which we have substantially reworked the architecture of our devices and equipped them with trusted download mechanisms, protection against the execution of malicious code in memory, protection against the substitution of electronic components etc.
In 2018, the US Department of Homeland Security shared a story about how unknown hackers attacked a number of energy companies in North America and they did it through the so-called Waterhole attack. The essence of the attack lies in the fact that attackers begin the first step of their attack not by breaking into the victim company, but by compromising the site of the manufacturer of the software or equipment used by the victim. Sooner or later (with the current software quality, it’s rather early) the company comes to the manufacturer’s website for software updates and firmware downloads and downloads software from the trusted resource, completely trusting it. So attackers get inside the organization and begin to expand the springboard. This attack allows you to infect not one, but many companies at once, which, like at a watering place (hence the waterhole), come to the manufacturer’s website for updates.
At the end of August 2018, the airline British Airways was faced with the fact that several hundred thousand of its customers suffered from the leakage of payment card data, which were entered on the site when ordering tickets. During the investigation, it turned out that the hacker grouping Magecart had hacked ... no, not the British Airways website, but the website of its contractor, from which infected JavaScript was loaded, which caused the leakage of information. Magecart followed a similar tactic in the case of attacks on the Ticketmaster ticket sales site, as well as a number of other e-commerce resources. Finally, it is worth noting that, according to one of the versions, it was not the main site of British Airways that suffered, but one of its clones located in the CDN infrastructure of the Internet service provider and intended to speed up access to the airline's website from certain locations. In this case, it was not the company itself that was hacked, but one of its counterparties, who provided part of their infrastructure.
These examples, as well as the case described above with the interception of traffic through BGP in the case of cryptocurrency theft, show that not only the resources of interest to the company's hackers, but also the infrastructure serving it can be attacked. In our opinion, such attacks will only increase, which raises the question of the need to expand the scope of attention of cybersecurity experts and the development of not only their own security strategy, but also control the security of their partners, contractors and counterparties.
What Cisco will answer : there is no universal recipe here - it all depends very much on how and what infrastructure of the contractor the attackers break into. If we are talking about attacks on BGP, then it is necessary to monitor BGP routes. If we are talking about an attack through an infected script on the site of a compromised manufacturer, then DNS monitoring with Cisco Umbrella will help, if we are talking about downloading firmware replacement software, then analyzing telemetry anomalies with Cisco Stealthwatch can help. Most importantly, include this threat in the list of current in 2019 year.
Everyone has heard of the TLS protocol, the predecessor of which was the SSL protocol. Most recently, in August 2018, the recommendation RFC 8446 was published, which identified a new version 1.3. The advantages of the new version include higher speed and cryptographic strength. At the same time, the vulnerabilities of the previous version were eliminated, and new useful features were added. Today TLS 1.3 is supported by many popular browsers and crypto libraries (for example, Chrome, Firefox, OpenSSL). It seems all is well, but alas. The delay in adopting TLS 1.3 was due, among other things, to the fact that this version of the protocol does not allow inspecting traffic using intermediate devices (NGFW, IDS, proxy, etc.), which is necessary for many corporate cyber security services. A number of companies in the process of discussing TLS 1.3 proposed to include a weaker key exchange protocol, but all of these proposals were rejected in order to protect Internet privacy and protect against government interference in freedom of communication. As TLS 1.3 is actively used, the impossibility of its inspection will rise very sharply and the first problems may begin as early as 2019.
What Cisco will answer : we do not plan to stand in the way of progress and put a spoke in the wheels when introducing a new version of TLS (especially since we are introducing it into our solutions), but we advise you to think about whether you need to switch to it in your infrastructure if TLS 1.2 is not hacked and not yet banned? But since sooner or later such a transition will still happen and the information security specialists in all their glory will face the question - how to monitor traffic that cannot be monitored? The answer may be a technology similar to the one developed by us Encrypted Traffic Analytics , which allows us to understand what is inside the encrypted traffic (but without access to the content itself) without decrypting and decrypting.
Speaking of encryption ... In our annual cybersecurity report (Cisco Annual Cybersecurity Report 2018), we noted that 55% of the global web traffic in the past year was transmitted in encrypted form, which is 12% more than last year, and the number of malicious programs, using encryption has tripled. In the next of his predictions, Gartner predicted that in the year of the Yellow Earthen Pig (yes, this is the 2019th year), 80% of all web traffic will be encrypted. And what to do in this situation? Especially if the traffic is encrypted using the TLS 1.3 described above?
What Cisco will answer : we, in our own infrastructure, also face this problem and have developed a number of recommendations that we are ready to share with you. First, you should not discard intermediate devices (for example, Cisco NGFW or Cisco WSA ), which can terminate tunnels on themselves and inspect the decoded traffic (at least, up to version TLS 1.3). If there are concerns that the network security device will “perform” performance, you can assign the function of terminating encrypted traffic to an external device, for example, Radware Alteon. Without the ability to disassemble the encrypted channel, do not despair. You can use machine learning technologies that “penetrate” inside encrypted traffic without decrypting it (for example, Cisco ETA ), or detect interaction with command servers or other malicious resources on the Internet. In the Cisco portfolio, this task will be solved by Cisco Umbrella . Finally, we should not forget that there is a place where even encrypted traffic is already decrypted — these are the end devices — workstations and servers, where you can (and should) install the appropriate means of protection. But the usual antivirus does not work here - you need something more modern than the solution developed in the late 80s. At Cisco, this solution is called Cisco AMP for Endpoints and we ourselves use it on our laptops (not all security developers can boast of this), but you can of course use other EDR (Endpoint Detection & Response) class solutions.
Anti-virus protection technologies appeared in the late 80s and since then, in a large way, they have not changed much. There is a malware program that is being studied by virus analysts, developing a signature and equipping its products. There is a signature - the malware is caught. No signature - not caught. One of the tasks of the intruders is to go unnoticed as long as possible, and for this they continue to actively play with the cat and mouse safeguards. Some strengthen their competence in the methods of detecting malicious and abnormal activity, others increase the potential to remain imperceptible for as long as possible. One of the growing trends continues to be the use of fileless attacks, actively exploiting the commands built into the OS and PowerShell, posing as legitimate computer users.
What Cisco will answer : since we are talking only about end devices, we have two solutions that are aimed at protecting and controlling against fileless attacks - Cisco AMP for Endpoints and Cisco AnyConnect. The first solution belongs to the EDR class and allows software inventory, including analysis of its vulnerabilities, blocking exploits, including those launched in memory, analyzing activity using constantly updated compromise indicators (IOC), as well as investigating and searching for threats (threat hunting ). Cisco AnyConnect with the Integrated Network Visibility Module (NVM) allows you to collect activity data on a site in an adapted Netflow format to correlate it with data received at the Cisco Stealthwatch network layer. In addition, an additional level of protection will be Cisco Umbrella, which tracks communications with command servers of malicious programs, including non-file ones.
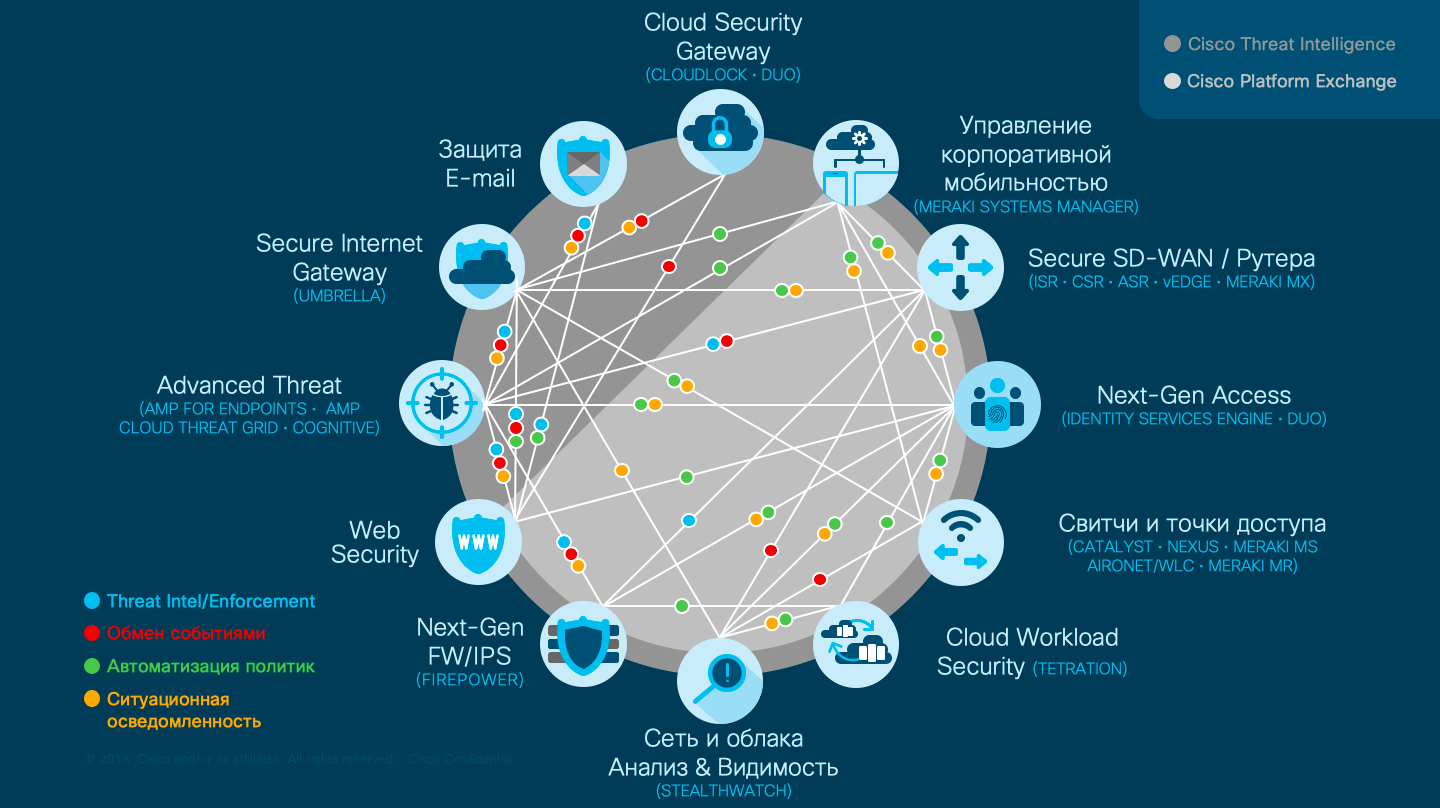
The integration of Cisco AnyConnect with Cisco Stealthwatch is not a vendor’s whim, but a pressing need that is dictated by changing the threat landscape and the emergence of multi-vector attacks that penetrate corporate and departmental networks in many different ways — through web portal vulnerabilities, thrown in USB drives, Waterhole attacks, through vulnerable wi-fi brought by an infected laptop of a manager or contractor, etc. No decision on information security alone can deal with modern threats. It’s too long and unreliable to wait for the consumer to start integrating the acquired products in the field of information security among themselves. We must take the process into our own hands. According to Cisco statistics, many companies use several dozen different protections that do not know how to interact with each other, creating a sense of false security. The average time for undetected malicious activity within the network today is about 200 days. And all because the remedies work as states in the Balkans - each independently of each other (it was not by chance that the term “Internet balkanization” appeared as a synonym for creating national segments of the Internet). But the situation will change, which can already be seen on the example of the same Cisco and its initiatives pxGrid , ACI, Cisco Security Technology Alliance , which combine two hundred software companies that have united to oppose the increasingly complex and accelerating attacks.
What Cisco will answer : our answer is automation and APIs that permeate all our products with the goal of combining them into a single security system and obtaining a synergistic effect from this, which allows you to speed up the threat detection process from a couple of hundred days to 4 and a half hours. This is achieved by exchanging threat data, automating the creation of signatures, gaining access from external sources of indicators of compromise, sending commands between protection tools, etc.
Artificial Intelligence is HYIP. Unlike machine learning, which is already becoming the norm, and not an exception in information security. Automation of routine tasks, acceleration of slow processes, replacement, and so lack of qualified personnel. Here are just a few benefits from the use of machine learning in information security. Today, it can detect malicious code and malicious domains and IP addresses on the Internet, phishing attacks and vulnerabilities, conduct awareness raising and identify insiders. But artificial intelligence is used not only for good, but also for harm. It was chosen by attackers who use machine learning to search for vulnerabilities and implement phishing attacks, bypass biometrics and create fake profiles on social networks, create malicious programs, select passwords and bypass the CAPTCHA mechanism. In 2018, very interesting projects were presented to create fake master fingerprints, synthesize voice, replace faces on video images, synchronize lip movement with synthesized speech superimposed on someone else's image in a video stream. I have no doubt that they will quickly be taken on board by the attackers and attackers, which in 2019 will put a number of new questions to the information security specialists on countering the harmful use of AI.
How Cisco will respond : we will continue our efforts to develop new and improve existing machine learning mechanisms in our cybersecurity products. Already, these models are already built into Cisco AMP for Endpoints , Stealthwatch , CloudLock , Umbrella , Cognitive Threat Analytics, and this list will only expand. In the meantime, we can offer you to visit our website dedicated to the use of artificial intelligence in Cisco solutions.

How many authentication factors can you name? One two Three? And if you think? Here is a small list of what can identify you:
In fact, the old passwords, the most popular of which over the past five years was 123456, are becoming a thing of the past and they are replaced by two- and multifactor authentication, which can significantly increase the security of user access to various services and data — corporate and personal; stored inside corporate data centers and beyond, in the clouds. And we are already accustomed to using the entrance to external services via Facebook or Yandex, and we will get used to using two-factor, and then multi-factor authentication. I think in 2019 there will be a certain change in consciousness, and many security people will think about how to replace unreliable passwords. And yes, biometrics is unlikely to become such a replacement due to its high cost compared with other methods of multifactor authentication and the lack of a model of threats to it.
How Cisco will respond : in 2018, we bought Duo , the market leader in multifactor authentication, which we will introduce to the Russian market.
All gradually abandon the perimeter, leaving the clouds and gradually introducing BYOD. No one cares whether your network is hacked or not (or almost none). But if your data leaks, you will be mixed with mud, regulators will come to you, you will be rinsed in the media, accusing you of not being able to take care of customers and employees. Have you ever thought how many people suffered from leaks of their personal and identification data? I allowed myself to make a small list and abit wondered how much data flowed into the Internet (in millions of records):
I'm afraid to assume, but I think that more than half of the entire Internet has parted with its data (mine, by the way, were also there repeatedly). Note that the number of incidents in which the size of a leak exceeds ten million records is no longer measured by one or even by a dozen. And the situation will be exacerbated. We are too fixated on the perimeter defense, forgetting that security has become data-centric, not perimeter. And it's not just data incidents, but also an increase in the regulatory burden associated with data protection. The GDPR, large user data (this is the topic of the new bill), amendments to the Federal Law 152, and others are waiting for Russians next year with open arms.
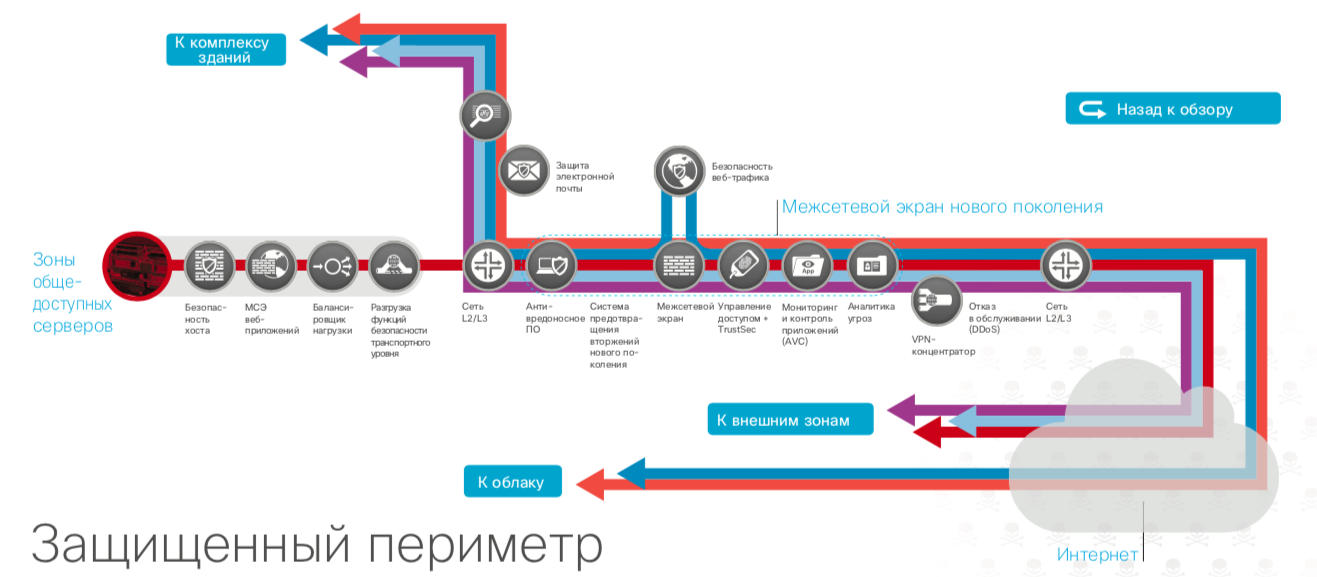
How Cisco will respond : we do not sell projects to bring you in compliance with legal requirements (although in Europe we have quite a few projects on GDPR). And we do not have the means to classify data or combat leaks (DLP). But we have a wealth of experience in building corporate cyber security systems that we have accumulated in the Cisco SAFE project - a set of practical recommendations for protecting various parts of a corporate or departmental network. It's not just about the perimeter , but about the data center, the cloud, Wi-Fi, unified communications, industrial networks, etc. Only the protection of all components will allow to protect data from leaks, at the same time fulfilling the requirements of the legislation.
In the US, several cities have announced that they have practically covered their territory with networks of the 5th generation (5G), which allow working on the Internet at speeds up to 10 Gbit / s. This will eliminate the “middleman” in the face of the router, which today accumulates the majority of connections. In 5G networks, the situation may change, which will multiply the attack surface and make attacks on the Internet of Things more widespread. As, in fact, the use of the Internet of Things as a springboard for attacks (I think Mirai’s 5G reincarnation is not far off), which makes it possible to multiply the power of DDoS attacks. Stop. But in Russia, the introduction of 5G was postponed until the end of 2021. What then is the trend for the year of the yellow earthen pig? Yes, here you are right.I just wanted to demonstrate my know-how. For Russia, our recommendations and solutions for protecting the networks of the new generation are still irrelevant. But, at least, it is worth remembering about this opportunity.
You are already tired of reading my opus about what awaits us all in 2019, so I will be round. And I would like to complete the last observation, which is already becoming a trend, which will only intensify next year. We are talking about cyber attacks, which allow to check the weak points in one or another process of ensuring cyber security and draw up a plan for their elimination. In contrast to the authorized courses that give knowledge, and trainings that allow you to work out quite specific skills for working with certain products, cyber attacks allow you to simulate various situations similar to what can happen in reality (searching for traces of a threat, information leaks about an incident in Media, lobed USB flash drive with malicious code, etc.) and work out methods for stopping them. Usually, within the framework of such cyber crimes, all weaknesses are revealed both in the processes described on paper and in the acquired skills of working with specific products that are not always applicable in real life.
In 2018, cyber attacks became very popular both at the corporate, as well as at the state and interstate level. I had the opportunity to conduct or participate in a couple of dozens of such cyber attacks, and I can safely say that this is becoming a trend for corporate information services, which thus test the skills of their specialists to resist various incidents and abnormal situations.
What Cisco will answer : this trend in Russia is becoming not without our help. We began to conduct the first cyber-attacks of Cisco Cyber Range several years ago, when at Moscow Cisco Connect we had several free sessions for two days for our customers. Then we repeated the success of Cyber Range and want to re-conduct these cyber attacks in April, as part of Cisco Connect in Moscow. True, on Cisco Connect we have a lightweight version, reduced to 4 hours of intensive practical work. In reality, we offer three- or five-day cyber attacks, in which the skill of dealing with hundreds of regularly updated various attack scenarios, taken from real life, is worked out. In addition to Cyber Range, we actively began to conduct one-day Cisco Threat Threats Hunting Workshop cyberservices in our office, where participants are trying to find traces of various threats (you can check the date of the next cyber attacks with your Cisco manager). In addition, we have a number of other online cybercuts that are available to our partners and customers in our online Cisco dCloud demonstration service.
Here is a list of trends that we would like to talk about and which, in our opinion, is waiting for us all in 2019! Happy New Year!

Traffic interception through BGP vulnerabilities
Recently, vulnerabilities have become more frequent in the BGP Internet Routing Protocol. Intercepting and redirecting traffic allows you to analyze and manipulate it, which leads to theft of cryptocurrency, breach of confidentiality, and restoration of control over computers under police control. In the autumn of 2018, a new scheme was used, which was used by cybercriminals for fraudulent Internet advertising. The attacker's operation, dubbed 3ve , allowed the traffic of over 1.5 million IP addresses to be intercepted and made advertising companies believe that billions of Internet banner hits were actually seen by real users. Yes, this is not a theft of traffic from a UK nuclear weapons agency. And yes, this is not intercepting the traffic of 1300 Amazon addresses in order to disguise the MyEtherWallet website with the subsequent theft of 150 thousand dollars in cryptocurrency. And this is not intercepting the traffic of two dozen financial organizations, including MasterCard and Visa (as well as Symantec and Verisign). Some annoying ads that we all try to remove using plug-ins and specialized software. But for advertising campaigns, this attack cost $ 29 million, which was “thrown into the abyss”, that is, paid to fraudsters who exploited vulnerabilities and incorrectly configured BGP.

')
What Cisco will answer : to neutralize the implementation of random or malicious threats via BGP, we will not sell you anything :-) We simply advise you to familiarize yourself with our manuals ( here and here ) and configure your network equipment accordingly. In addition, a good recommendation would be to monitor the route information of your network using the appropriate BGP monitoring services.
Hacking network devices
45 thousand compromised routers were found at the end of November 2018. A botnet of 100,000 compromised network devices from Broadcom, Asus, TP-Link, Zyxel, D-Link, Netgear, US Robotics, and others was detected a couple of weeks earlier. In May, Cisco Talos experts discovered half a million compromised network devices in 54 countries around the world. Among the affected vendors are ASUS, D-Link, Huawei, Ubiquiti, UPVEL, ZTE, as well as Linksys, MikroTik, Netgear and TP-Link. Hacking network equipment turns from isolated cases into mainstream, as it allows attackers to gain access to large volumes of information of interest to them, which can be transmitted in unencrypted form.
What Cisco will answer : if we are talking about Cisco equipment, then we have developed many recommendations for protecting routers based on Cisco IOS , IOS XR , IOS XE operating systems, the correct implementation of which increases their security many times. In addition, we were among the first to encounter attacks on our routers (because of their popularity), we began to implement Secure Boot, boot protection, memory protection, protection against the substitution of hardware components, etc. into the equipment.
Other manufacturers should also have appropriate instructions on how to update and protect them. In addition, it will be good practice to analyze telemetry from network equipment, which allows you to identify anomalies in network traffic and timely detect compromise at the level of network infrastructure, which in 2019 will continue to interest intruders.
Supply Chain Attacks
Attacks on network equipment reminded us of the old story that some of our customers faced around the world (there were not many of them). Not having a service contract for our equipment, they downloaded new firmware for already discontinued lines of routers from warez sites on the Internet, which led to the infection of devices, interception of information, and we were pushed to revise the strategy of self-defense of network equipment and the launch of Trustworthy Systems initiative the framework of which we have substantially reworked the architecture of our devices and equipped them with trusted download mechanisms, protection against the execution of malicious code in memory, protection against the substitution of electronic components etc.
In 2018, the US Department of Homeland Security shared a story about how unknown hackers attacked a number of energy companies in North America and they did it through the so-called Waterhole attack. The essence of the attack lies in the fact that attackers begin the first step of their attack not by breaking into the victim company, but by compromising the site of the manufacturer of the software or equipment used by the victim. Sooner or later (with the current software quality, it’s rather early) the company comes to the manufacturer’s website for software updates and firmware downloads and downloads software from the trusted resource, completely trusting it. So attackers get inside the organization and begin to expand the springboard. This attack allows you to infect not one, but many companies at once, which, like at a watering place (hence the waterhole), come to the manufacturer’s website for updates.
At the end of August 2018, the airline British Airways was faced with the fact that several hundred thousand of its customers suffered from the leakage of payment card data, which were entered on the site when ordering tickets. During the investigation, it turned out that the hacker grouping Magecart had hacked ... no, not the British Airways website, but the website of its contractor, from which infected JavaScript was loaded, which caused the leakage of information. Magecart followed a similar tactic in the case of attacks on the Ticketmaster ticket sales site, as well as a number of other e-commerce resources. Finally, it is worth noting that, according to one of the versions, it was not the main site of British Airways that suffered, but one of its clones located in the CDN infrastructure of the Internet service provider and intended to speed up access to the airline's website from certain locations. In this case, it was not the company itself that was hacked, but one of its counterparties, who provided part of their infrastructure.
These examples, as well as the case described above with the interception of traffic through BGP in the case of cryptocurrency theft, show that not only the resources of interest to the company's hackers, but also the infrastructure serving it can be attacked. In our opinion, such attacks will only increase, which raises the question of the need to expand the scope of attention of cybersecurity experts and the development of not only their own security strategy, but also control the security of their partners, contractors and counterparties.
What Cisco will answer : there is no universal recipe here - it all depends very much on how and what infrastructure of the contractor the attackers break into. If we are talking about attacks on BGP, then it is necessary to monitor BGP routes. If we are talking about an attack through an infected script on the site of a compromised manufacturer, then DNS monitoring with Cisco Umbrella will help, if we are talking about downloading firmware replacement software, then analyzing telemetry anomalies with Cisco Stealthwatch can help. Most importantly, include this threat in the list of current in 2019 year.
Coming TLS 1.3
Everyone has heard of the TLS protocol, the predecessor of which was the SSL protocol. Most recently, in August 2018, the recommendation RFC 8446 was published, which identified a new version 1.3. The advantages of the new version include higher speed and cryptographic strength. At the same time, the vulnerabilities of the previous version were eliminated, and new useful features were added. Today TLS 1.3 is supported by many popular browsers and crypto libraries (for example, Chrome, Firefox, OpenSSL). It seems all is well, but alas. The delay in adopting TLS 1.3 was due, among other things, to the fact that this version of the protocol does not allow inspecting traffic using intermediate devices (NGFW, IDS, proxy, etc.), which is necessary for many corporate cyber security services. A number of companies in the process of discussing TLS 1.3 proposed to include a weaker key exchange protocol, but all of these proposals were rejected in order to protect Internet privacy and protect against government interference in freedom of communication. As TLS 1.3 is actively used, the impossibility of its inspection will rise very sharply and the first problems may begin as early as 2019.
What Cisco will answer : we do not plan to stand in the way of progress and put a spoke in the wheels when introducing a new version of TLS (especially since we are introducing it into our solutions), but we advise you to think about whether you need to switch to it in your infrastructure if TLS 1.2 is not hacked and not yet banned? But since sooner or later such a transition will still happen and the information security specialists in all their glory will face the question - how to monitor traffic that cannot be monitored? The answer may be a technology similar to the one developed by us Encrypted Traffic Analytics , which allows us to understand what is inside the encrypted traffic (but without access to the content itself) without decrypting and decrypting.
Traffic encryption
Speaking of encryption ... In our annual cybersecurity report (Cisco Annual Cybersecurity Report 2018), we noted that 55% of the global web traffic in the past year was transmitted in encrypted form, which is 12% more than last year, and the number of malicious programs, using encryption has tripled. In the next of his predictions, Gartner predicted that in the year of the Yellow Earthen Pig (yes, this is the 2019th year), 80% of all web traffic will be encrypted. And what to do in this situation? Especially if the traffic is encrypted using the TLS 1.3 described above?
What Cisco will answer : we, in our own infrastructure, also face this problem and have developed a number of recommendations that we are ready to share with you. First, you should not discard intermediate devices (for example, Cisco NGFW or Cisco WSA ), which can terminate tunnels on themselves and inspect the decoded traffic (at least, up to version TLS 1.3). If there are concerns that the network security device will “perform” performance, you can assign the function of terminating encrypted traffic to an external device, for example, Radware Alteon. Without the ability to disassemble the encrypted channel, do not despair. You can use machine learning technologies that “penetrate” inside encrypted traffic without decrypting it (for example, Cisco ETA ), or detect interaction with command servers or other malicious resources on the Internet. In the Cisco portfolio, this task will be solved by Cisco Umbrella . Finally, we should not forget that there is a place where even encrypted traffic is already decrypted — these are the end devices — workstations and servers, where you can (and should) install the appropriate means of protection. But the usual antivirus does not work here - you need something more modern than the solution developed in the late 80s. At Cisco, this solution is called Cisco AMP for Endpoints and we ourselves use it on our laptops (not all security developers can boast of this), but you can of course use other EDR (Endpoint Detection & Response) class solutions.
Fileless attacks
Anti-virus protection technologies appeared in the late 80s and since then, in a large way, they have not changed much. There is a malware program that is being studied by virus analysts, developing a signature and equipping its products. There is a signature - the malware is caught. No signature - not caught. One of the tasks of the intruders is to go unnoticed as long as possible, and for this they continue to actively play with the cat and mouse safeguards. Some strengthen their competence in the methods of detecting malicious and abnormal activity, others increase the potential to remain imperceptible for as long as possible. One of the growing trends continues to be the use of fileless attacks, actively exploiting the commands built into the OS and PowerShell, posing as legitimate computer users.
What Cisco will answer : since we are talking only about end devices, we have two solutions that are aimed at protecting and controlling against fileless attacks - Cisco AMP for Endpoints and Cisco AnyConnect. The first solution belongs to the EDR class and allows software inventory, including analysis of its vulnerabilities, blocking exploits, including those launched in memory, analyzing activity using constantly updated compromise indicators (IOC), as well as investigating and searching for threats (threat hunting ). Cisco AnyConnect with the Integrated Network Visibility Module (NVM) allows you to collect activity data on a site in an adapted Netflow format to correlate it with data received at the Cisco Stealthwatch network layer. In addition, an additional level of protection will be Cisco Umbrella, which tracks communications with command servers of malicious programs, including non-file ones.
Integration, automation and API
The integration of Cisco AnyConnect with Cisco Stealthwatch is not a vendor’s whim, but a pressing need that is dictated by changing the threat landscape and the emergence of multi-vector attacks that penetrate corporate and departmental networks in many different ways — through web portal vulnerabilities, thrown in USB drives, Waterhole attacks, through vulnerable wi-fi brought by an infected laptop of a manager or contractor, etc. No decision on information security alone can deal with modern threats. It’s too long and unreliable to wait for the consumer to start integrating the acquired products in the field of information security among themselves. We must take the process into our own hands. According to Cisco statistics, many companies use several dozen different protections that do not know how to interact with each other, creating a sense of false security. The average time for undetected malicious activity within the network today is about 200 days. And all because the remedies work as states in the Balkans - each independently of each other (it was not by chance that the term “Internet balkanization” appeared as a synonym for creating national segments of the Internet). But the situation will change, which can already be seen on the example of the same Cisco and its initiatives pxGrid , ACI, Cisco Security Technology Alliance , which combine two hundred software companies that have united to oppose the increasingly complex and accelerating attacks.
What Cisco will answer : our answer is automation and APIs that permeate all our products with the goal of combining them into a single security system and obtaining a synergistic effect from this, which allows you to speed up the threat detection process from a couple of hundred days to 4 and a half hours. This is achieved by exchanging threat data, automating the creation of signatures, gaining access from external sources of indicators of compromise, sending commands between protection tools, etc.

The growth of the use of artificial intelligence on both sides of the barricades
Artificial Intelligence is HYIP. Unlike machine learning, which is already becoming the norm, and not an exception in information security. Automation of routine tasks, acceleration of slow processes, replacement, and so lack of qualified personnel. Here are just a few benefits from the use of machine learning in information security. Today, it can detect malicious code and malicious domains and IP addresses on the Internet, phishing attacks and vulnerabilities, conduct awareness raising and identify insiders. But artificial intelligence is used not only for good, but also for harm. It was chosen by attackers who use machine learning to search for vulnerabilities and implement phishing attacks, bypass biometrics and create fake profiles on social networks, create malicious programs, select passwords and bypass the CAPTCHA mechanism. In 2018, very interesting projects were presented to create fake master fingerprints, synthesize voice, replace faces on video images, synchronize lip movement with synthesized speech superimposed on someone else's image in a video stream. I have no doubt that they will quickly be taken on board by the attackers and attackers, which in 2019 will put a number of new questions to the information security specialists on countering the harmful use of AI.
How Cisco will respond : we will continue our efforts to develop new and improve existing machine learning mechanisms in our cybersecurity products. Already, these models are already built into Cisco AMP for Endpoints , Stealthwatch , CloudLock , Umbrella , Cognitive Threat Analytics, and this list will only expand. In the meantime, we can offer you to visit our website dedicated to the use of artificial intelligence in Cisco solutions.

Multifactor authentication
How many authentication factors can you name? One two Three? And if you think? Here is a small list of what can identify you:
- Something you know (yes, this is a classic password)
- Something you have (yes, this is a token)
- Something you own (yes, this is biometrics)
- Something that you do
- Something you lost
- Something you forgot
- Something you found
- Something that you and where you saw
- Something where you were
- Something you created
- Something you destroyed
- Something that or what you donated
- Something you stole.
In fact, the old passwords, the most popular of which over the past five years was 123456, are becoming a thing of the past and they are replaced by two- and multifactor authentication, which can significantly increase the security of user access to various services and data — corporate and personal; stored inside corporate data centers and beyond, in the clouds. And we are already accustomed to using the entrance to external services via Facebook or Yandex, and we will get used to using two-factor, and then multi-factor authentication. I think in 2019 there will be a certain change in consciousness, and many security people will think about how to replace unreliable passwords. And yes, biometrics is unlikely to become such a replacement due to its high cost compared with other methods of multifactor authentication and the lack of a model of threats to it.
How Cisco will respond : in 2018, we bought Duo , the market leader in multifactor authentication, which we will introduce to the Russian market.
Data centricity
All gradually abandon the perimeter, leaving the clouds and gradually introducing BYOD. No one cares whether your network is hacked or not (or almost none). But if your data leaks, you will be mixed with mud, regulators will come to you, you will be rinsed in the media, accusing you of not being able to take care of customers and employees. Have you ever thought how many people suffered from leaks of their personal and identification data? I allowed myself to make a small list and a
- Exactis - 340
- Facebook - 50
- Equifax - 145
- Starwood - 500
- Yahoo - 3000
- Under Armor - 150
- Adult FriendFinder - 412
- MySpace - 164
- Ebay - 145
- Target - 110
- Heartland Payment Systems - 130
- LinkedIn - 117
- Rambler - 98
- TJX - 94
- AOL - 92
- Quora - 100
- VK - 100
- Deep Root Analytics - 198
- JP Morgan Chase - 78
- Mail.ru - 25
- Anthem - 80
- Dailymotion - 85
- Uber - 57
- Tumblr - 65
- Dropbox - 68
- Home Depot - 56
- Adobe - 38
- Sony PSN - 77
- RSA Security - 40.
I'm afraid to assume, but I think that more than half of the entire Internet has parted with its data (mine, by the way, were also there repeatedly). Note that the number of incidents in which the size of a leak exceeds ten million records is no longer measured by one or even by a dozen. And the situation will be exacerbated. We are too fixated on the perimeter defense, forgetting that security has become data-centric, not perimeter. And it's not just data incidents, but also an increase in the regulatory burden associated with data protection. The GDPR, large user data (this is the topic of the new bill), amendments to the Federal Law 152, and others are waiting for Russians next year with open arms.

How Cisco will respond : we do not sell projects to bring you in compliance with legal requirements (although in Europe we have quite a few projects on GDPR). And we do not have the means to classify data or combat leaks (DLP). But we have a wealth of experience in building corporate cyber security systems that we have accumulated in the Cisco SAFE project - a set of practical recommendations for protecting various parts of a corporate or departmental network. It's not just about the perimeter , but about the data center, the cloud, Wi-Fi, unified communications, industrial networks, etc. Only the protection of all components will allow to protect data from leaks, at the same time fulfilling the requirements of the legislation.
Using 5G networks as a springboard for attacks
In the US, several cities have announced that they have practically covered their territory with networks of the 5th generation (5G), which allow working on the Internet at speeds up to 10 Gbit / s. This will eliminate the “middleman” in the face of the router, which today accumulates the majority of connections. In 5G networks, the situation may change, which will multiply the attack surface and make attacks on the Internet of Things more widespread. As, in fact, the use of the Internet of Things as a springboard for attacks (I think Mirai’s 5G reincarnation is not far off), which makes it possible to multiply the power of DDoS attacks. Stop. But in Russia, the introduction of 5G was postponed until the end of 2021. What then is the trend for the year of the yellow earthen pig? Yes, here you are right.
Cyberwords
You are already tired of reading my opus about what awaits us all in 2019, so I will be round. And I would like to complete the last observation, which is already becoming a trend, which will only intensify next year. We are talking about cyber attacks, which allow to check the weak points in one or another process of ensuring cyber security and draw up a plan for their elimination. In contrast to the authorized courses that give knowledge, and trainings that allow you to work out quite specific skills for working with certain products, cyber attacks allow you to simulate various situations similar to what can happen in reality (searching for traces of a threat, information leaks about an incident in Media, lobed USB flash drive with malicious code, etc.) and work out methods for stopping them. Usually, within the framework of such cyber crimes, all weaknesses are revealed both in the processes described on paper and in the acquired skills of working with specific products that are not always applicable in real life.
In 2018, cyber attacks became very popular both at the corporate, as well as at the state and interstate level. I had the opportunity to conduct or participate in a couple of dozens of such cyber attacks, and I can safely say that this is becoming a trend for corporate information services, which thus test the skills of their specialists to resist various incidents and abnormal situations.
What Cisco will answer : this trend in Russia is becoming not without our help. We began to conduct the first cyber-attacks of Cisco Cyber Range several years ago, when at Moscow Cisco Connect we had several free sessions for two days for our customers. Then we repeated the success of Cyber Range and want to re-conduct these cyber attacks in April, as part of Cisco Connect in Moscow. True, on Cisco Connect we have a lightweight version, reduced to 4 hours of intensive practical work. In reality, we offer three- or five-day cyber attacks, in which the skill of dealing with hundreds of regularly updated various attack scenarios, taken from real life, is worked out. In addition to Cyber Range, we actively began to conduct one-day Cisco Threat Threats Hunting Workshop cyberservices in our office, where participants are trying to find traces of various threats (you can check the date of the next cyber attacks with your Cisco manager). In addition, we have a number of other online cybercuts that are available to our partners and customers in our online Cisco dCloud demonstration service.
Here is a list of trends that we would like to talk about and which, in our opinion, is waiting for us all in 2019! Happy New Year!
Source: https://habr.com/ru/post/434250/
All Articles