BLACK HAT conference. How to make a spy phone. Part 1
Host: Kevin McNami is director of the Bell Labs Security Studies Lab, which is part of Alcatel-Lucent. His presentation is called "How to make a spy phone", and if you have any questions, please save them until the end of the speech, so that we know that we have enough time left for them.
Kevin McNami: I welcome everyone, I am glad that I am speaking here today. I'm going to talk about how to make a good spy phone, but I think that the basis of your interest will be how you can take this SpyPhone spy phone module and put it in an Android application.

')
My performance will consist of 3 parts. The first is a demonstration of SpyPhone in action, then we will talk a little about the special design of the “spy phone”. The third part of the conversation will be devoted to how you can inject the SpyPhone service into the application, and at the end I will summarize the results and answer the questions.
The next slide shows how people used to perceive a “spy phone”. Basically, they believed that such a phone allows you to spy on other people.

Modern spy phone looks different, it is a regular smartphone running the Android OS. Android is a very flexible platform that is easy to work with, it is very open and allows you to do many things. So, this is what a modern SpyPhone looks like. I think that the same can be done with phones running iOS, but I focused my efforts on Android.

Previously, for the organization of outdoor surveillance, you would need a variety of equipment, ranging from tape recorders to recording telephone conversations to tape and ending with cars with hidden surveillance equipment. Today, all you need is an Android phone. You use such a phone with special software installed on it and can track the person who owns this phone. You can monitor his phone calls, you can control his location, you can even send messages from that person’s phone, view a list of contacts, etc.

This is a very powerful type of cyber surveillance device. If someone's phone is infected with this spyware application and this person brings it to the office, you can follow this person at work, watch business meetings and so on. Management and control of the spy device is carried out through the Internet. Spy module does not require any special additional equipment, everything is located inside the phone. When he has something to convey interesting, he communicates with you through the site command & control and transmits information. Later I will show you a demo how it works.
Now consider the countermeasures. In the old days, the so-called “cone of silence” was used to prevent eavesdropping. If someone was spying on you, you could always enter the "cone of silence" and communicate with the interlocutor completely freely.
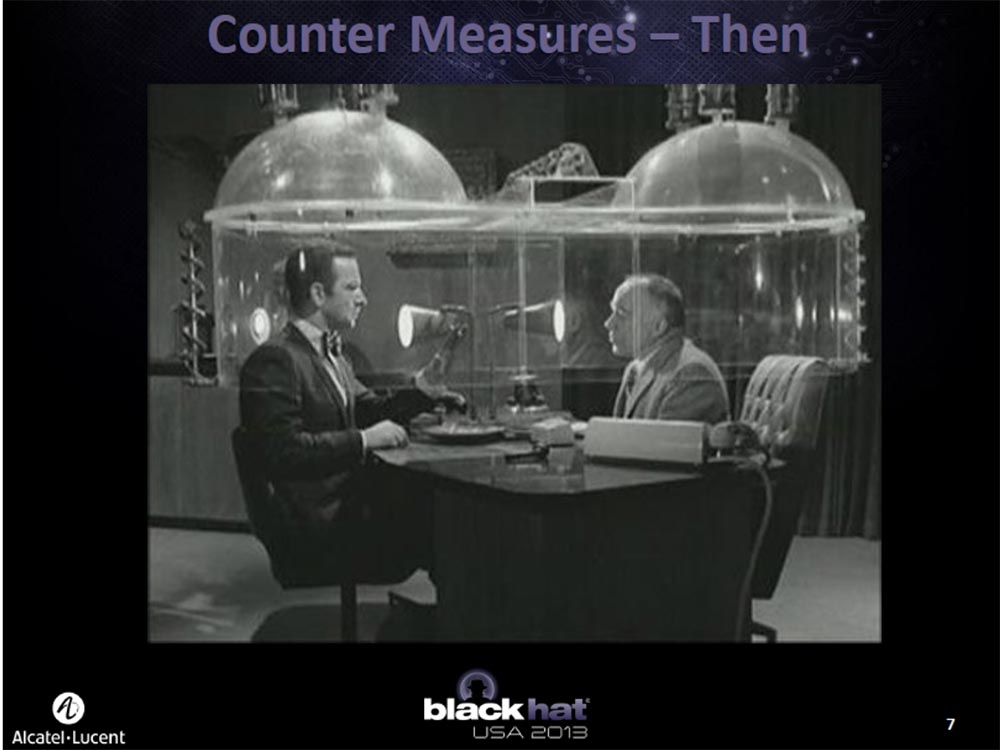
Today's "cone of silence" looks a little different. The company in which I work has developed a technology that can be placed on the network and which automatically detects the traffic of command & control, mediated by the transfer of which is the phone on the Android platform.
That is why we created the SpyPhone module, which we use as a demonstration when we go to our customers, who are mainly providers of mobile communication services and mobile Internet. We show them a “spy phone” to show that there is a huge security problem in the mobile network. This threat is still in its infancy, but could potentially cause great damage in the future. We use this module to educate our customers on hazards, so it’s natural that the second part of the demonstration is the presentation of our product, which can counter these hazards.
The smartphone is a very powerful device. It provides access to your location, connects to the Internet from almost anywhere, has a microphone, a camera, connects to local networks via Wi-Fi, and all this makes it an ideal platform for espionage.
I would say that a smartphone is an ideal cyber espionage tool that can be used to track a victim’s location, upload personal information, intercept and send messages, record conversations and take pictures without the owner’s knowledge. In the context of BYOD and APT, this is the ideal platform for launching internal attacks against corporate or government networks.
I think I’ve talked enough about this, so let's move on to the demonstration. On the left you see a screenshot from the screen of the phone, which will soon become spyware, this is the phone that I use now. On the right you can see the command & control console, which will be used by the person tracking this phone.
So, we took the malware, the SpyPhone module, and embedded it in a copy of the very popular game Angry Birds. Then we sent an email to one guy saying that he can download this cool game and play it. We can also place this infected game on third-party sites, where the user can download it. Now I’ll go to my browser to browse my received email.
So, when this guy receives a letter, he clicks on the link and goes to the real working app store for Android on the page with our game. We decided to name it Very Angry Birds (“Very Angry Birds”) because it contains the SpyPhone module.
So, the user downloads this game. On an Android phone, when you install an application, it provides you with a list of all the permissions it needs for its work.

It says that the application needs access to your location, personal information, network communications, data storage, paid services, phone calls. Since the user wants to install the application, he usually does not pay attention to all these permissions, which constantly appear during the installation of programs, and simply presses the "Install" button. Now you can see on the screen how the installation process is going. Next, we run the installed application. Now on the left you see a running game, and on the right - information of the command & control site that the smartphone is under control, and you can hear the sounds that accompany the game.

I will turn off the sound because it annoys me. So, note that the game is going on as usual, there is nothing extraordinary here that could attract the user's attention. There is no evidence that something strange is happening with the phone.
The user is playing, this is very cool, but even when he stops playing and closes the game, the spy module will continue its work in the background. Even if you restart the phone, the SpyPhone service will be restarted, now it is constantly present on this smartphone. So, this phone is infected with a cyber spy and is now displayed here in the console command & control. If I click on this line, the site will give me the information stored on this device. We can get a map with the location of this device - this is Las Vegas.
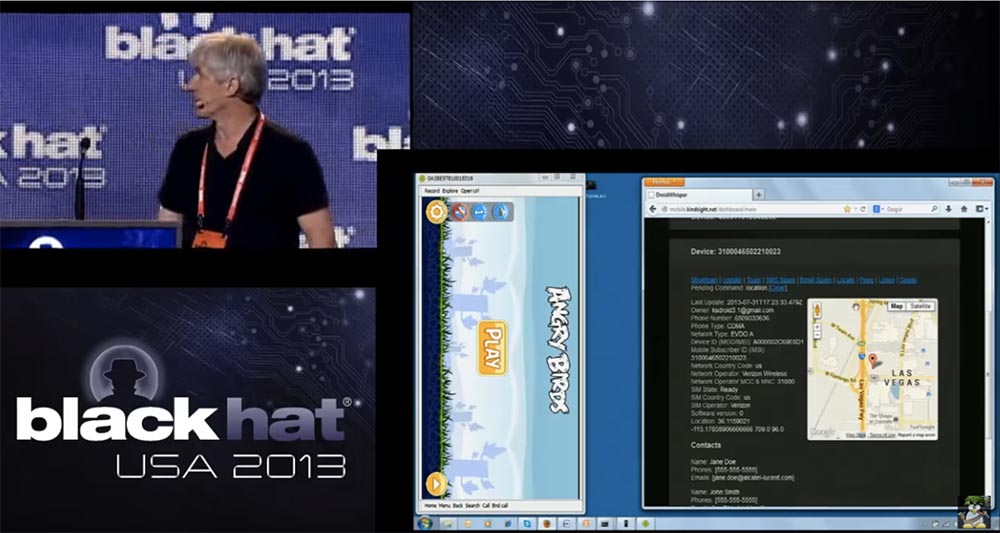
Let me emphasize that here the connection between the phone and the computer is not carried out directly, but via the Internet using a web server, which is located in Ottawa, where I work. The only reason why I connected this phone with a cable to a computer is the need to take screenshots. The console shows that we have other phones working at the same time. Here is one of them, located in China, so you can create an international network of "spy phones" and monitor them all the time while they are online.
So back to our phone in Las Vegas. You can see that here is the email address of the phone’s owner’s account, phone number, CDMA communication standard, network type, IMEI, country of the cellular operator, its name, SIM card status, location coordinates and phone owner’s contacts. All this information is uploaded to the command & control server, and we can track the owner of this phone 24 hours a day, 7 days a week, and use all the information that the phone provides, including downloading the contact list of this particular person. This will give us a list of other potential targets, if we use a kind of industrial cyber espionage, when we want to know who the owner of the phone communicates with and who does business with. We could use this contact list to target specific individuals.
You can imagine that an attacker distributes this game to all stores Android applications, and after people download it, you focus on some employee of a particular company, on the list of his contacts and so on.
Another thing we can do is update the installed spyware and send messages to the infected phone. You can use it for other purposes, for example, just to frighten people with such messages. We can access SMS messages and email, determine the location of the phone. All these operations are indicated in the upper part of the management console of the captured phone, they are highlighted by the blue interface. Another thing you can do is turn on the camera of the phone, I will try to do it right now. I take the phone in my hands and click on the “Peep” function in the control console, it will take some time, since you need to take a photo and send it to the command & control site. As you can see, my photo made by the front camera first appears, followed by a photo of this room taken by the rear camera. Thus, I can remotely take pictures on the infected phone and receive these photos.
If you notice, the game is still on the screen, so that the person will not even notice that the photo was taken. This is done in the background without the user's knowledge. We can use the same technology to shoot video. The last thing I want to demonstrate is the listening function. So, I say to the phone "This is a test, one, two, three, this is a test, one, two, three." Then I click on the Play Audio button, the connection takes a little time, and now you hear the repetition of my words.

So, I recorded the conversation through the microphone of the phone and uploaded it to the command & control site, so this is pretty cool. So this was a demonstration of what SpyPhone technology can do.
Now let's talk a little about how we developed the design and technology of our software and why we made such design decisions. I will go back to the previous slides.
First, we wanted to combine our malware with the original functions of the phone and create a trojan-type spyware program with remote access that would work with the phone on the Android platform. We took as a basis the demo application called “Searchable dictionary” and modified it so that it could insert a spyware module, and implemented it as a normal application for “Android”.
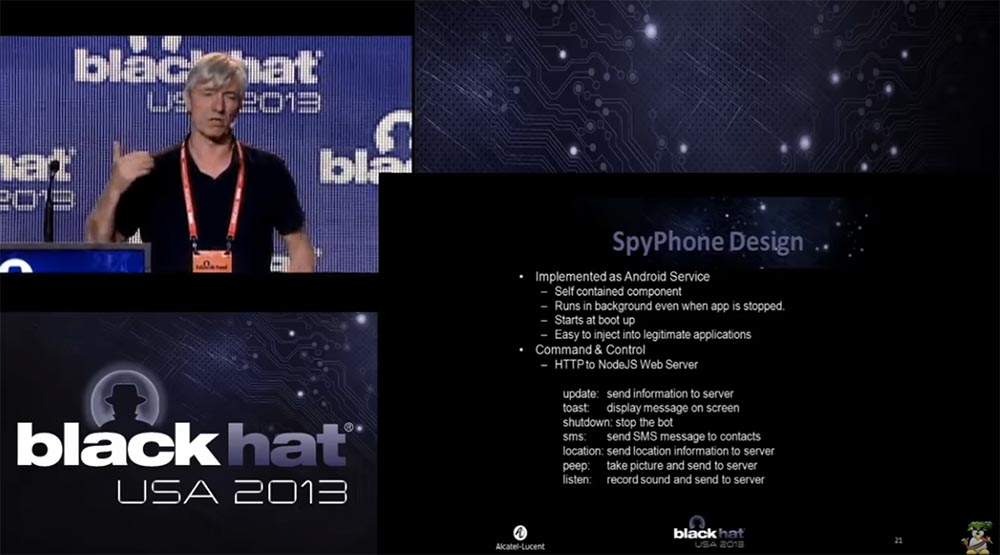
That is, we have adhered to the design of the original programs for "Android" using Java. We needed it to contain all the necessary components inside, to work in the background, even if the application was stopped, started when the phone was loaded. Our second task was to provide easy integration of SpyPhone into official applications. It worked, and our malware didn’t interfere at all with other applications installed on the phone. As the command and control command & control server, we chose NodJS a web server with HTTP data transfer. For the teams managing our program, we used the JS interface, and the teams themselves looked like this:
update - send information to the server,
toast - display a message on the screen,
shutdown - stop working SpyPhone,
sms - send SMS message to contact
location — send phone location information to the server,
peep - take a photo and send it to the server,
listen - record sound and send to server.
All of this was fairly easy to program, since the creators of Android provided their system with a fairly powerful full set of SDK development tools. This set provides an interface for everything you want. We have never been engaged in the development of programs for Android, but thanks to this SDK we didn’t even have to learn anything and we developed this thing in a few weeks.
The next slide shows the initial “Searchable dictionary” design, on the basis of which we created the SpyPhone, using the Java codes that you see here. We added a part to this app called droidwhisper.
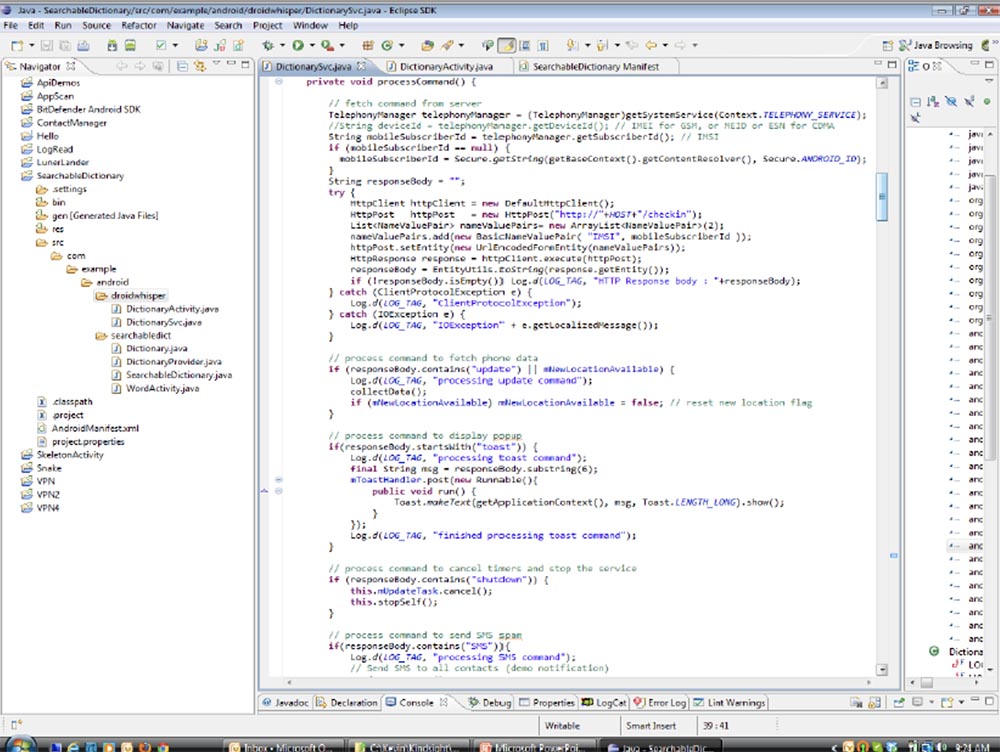
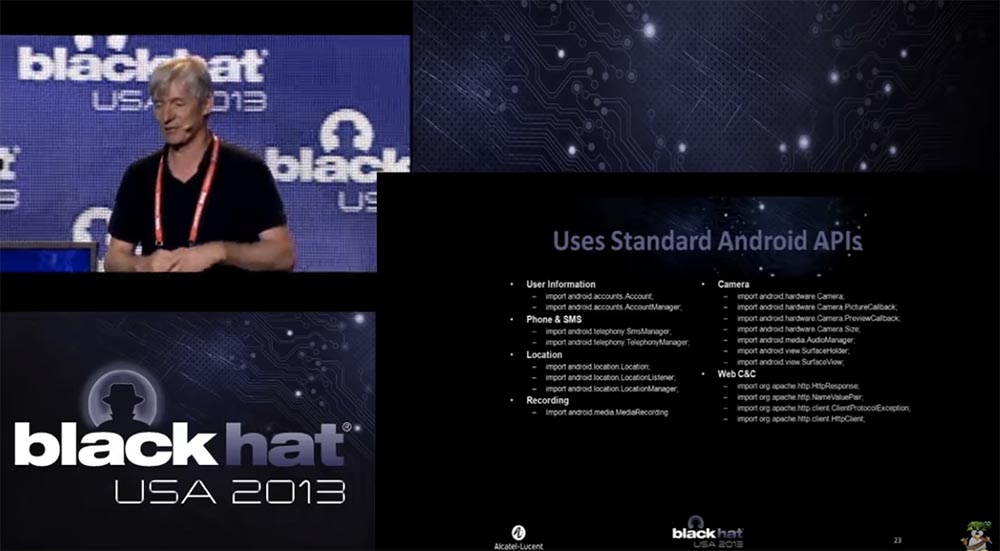
This is the part that we were going to cut and paste into the appropriate application later. We had no experience creating special exploits that would exploit application vulnerabilities, so we imported a standard API that Android provides:
User information
- import android.accounts.Account;
- import android.accounts.AccountManager.
Phone and SMS
–Import android.telephony.SmsManager;
–Import android.telephony.TelephonyManager.
Location
–Import android.location.Location;
–Import android.location.LocationListener;
–Import android.location.LocationManager;
Record media files (audio and video)
- import android.media.MediaRecording.
Camera
–Import android.hardware.Camera;
–Import android.hardware.Camera.PictureCallback;
–Import android.hardware.Camera.PreviewCallback;
–Import android.hardware.Camera.Size;
–Import android.media.AudioManager;
–Import android.view.SurfaceHolder;
–Import android.view.SurfaceView.
the Internet
–Import org.apache.http.HttpResponse;
–Import org.apache.http.NameValuePair;
–Import org.apache.http.client.ClientProtocolException;
–Import org.apache.http.client.HttpClient.
Someone said that recording video and taking pictures when the phone is in the user's pocket is not very good. Therefore, if you want to make a good photo, you send a text message to the owner, because we have his phone number. He receives a message, holds the phone face to himself to read it, and during this time you take a photo with the front camera. If you just call him, he brings the phone to his ear, and at that moment you can take a picture with the rear camera.
Making the camera work is a bit more complicated, so we used a whole set of classes, for example, AudioManager, SurfaceHolder, and the like. We had to provide for a temporary shutdown of the click sound when a photo is taken so as not to attract the user's attention, if this function is activated in the settings of his camera. In addition, we made sure that the taken spy photos or videos were displayed in the phone gallery in the form of 1-pixel thumbnails so that the user could not see them. So we had to use several tricks to ensure the invisible work of our spyware module. As I have already noted, almost everything to ensure communication with the command & control server is contained in the phone itself. We also used some of the security flaws of Android.
As you know, these applications must be signed to be installed on the phone, but this is not a problem, because you can use any old certificate for signing, because the main thing is that the application has a certificate at all, no matter which one. Later I will tell you more about it.
So, this was a brief description of the design that we used to create the application. Now I will tell you about the implementation process, that is, how we took our malicious module and inserted it into the application.
The first thing we did was choose the game Angry Birds. We chose it not because it is a very good game, but because of its popularity. Our SpyPhone module can be entered into absolutely any application. First of all, we need a copy of the original .apk file. This is an archive containing all the components of the application. Inside the application file is Java code, or rather, not quite Java — this is the code for the Dalvik virtual machine to work. This code can be replaced with other content, this is called a master key vulnerability. So, we have to open this .apk file and disassemble it, that is, have a list of all the components to be disassembled.
So, first of all, we extract all the components of the Angry Birds 2000 application.

Then we insert our example / android / droidwhisper directory into the smali directory, and it is in the final droidwhisper folder that we find the modified files of the Searchable dictionary application containing our spyware module.

We downloaded the Angry Birds game from the Google Play Market and made a copy of it. The next thing we’re worried about is signature keys. All these files you see in our directory called inject.
During the disassembly process, we used Apk_tools, a tool for managing .apk files. Now, using the command line, I show how we proceeded to disassembling Angry Birds.
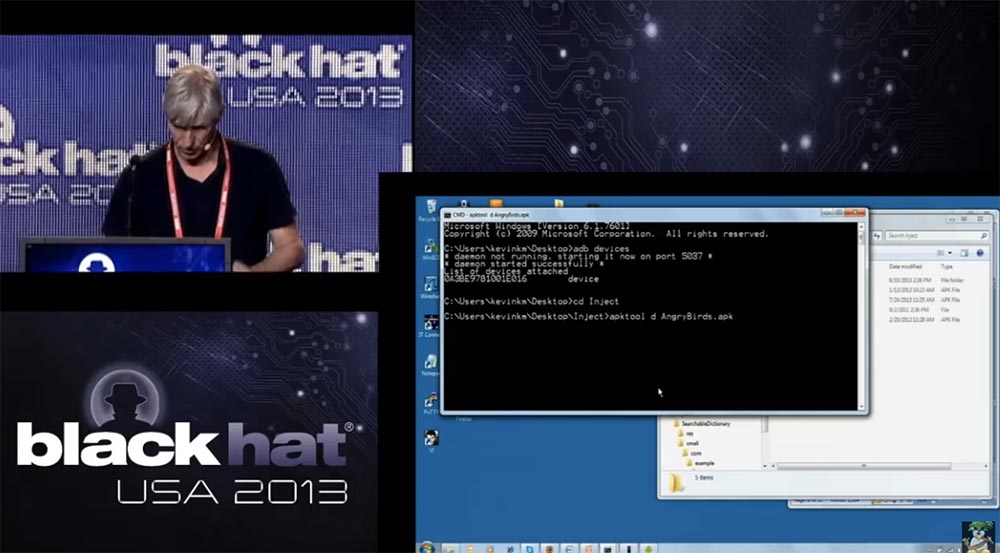
Then we started directly disassembling the application. We created the Angry Birds directory where we inserted all the components of the application. Since this is a demo, you have to wait a bit until the disassembly process is over. So, you see rad catalogs, the assets folder is located first, there are such things as sounds, then there are resourses folders, lib libraries, but the key is the smali directory, which contains the code and the assembly language format.
23:00 min
BLACK HAT conference. How to make a spy phone. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Kevin McNami: I welcome everyone, I am glad that I am speaking here today. I'm going to talk about how to make a good spy phone, but I think that the basis of your interest will be how you can take this SpyPhone spy phone module and put it in an Android application.

')
My performance will consist of 3 parts. The first is a demonstration of SpyPhone in action, then we will talk a little about the special design of the “spy phone”. The third part of the conversation will be devoted to how you can inject the SpyPhone service into the application, and at the end I will summarize the results and answer the questions.
The next slide shows how people used to perceive a “spy phone”. Basically, they believed that such a phone allows you to spy on other people.

Modern spy phone looks different, it is a regular smartphone running the Android OS. Android is a very flexible platform that is easy to work with, it is very open and allows you to do many things. So, this is what a modern SpyPhone looks like. I think that the same can be done with phones running iOS, but I focused my efforts on Android.

Previously, for the organization of outdoor surveillance, you would need a variety of equipment, ranging from tape recorders to recording telephone conversations to tape and ending with cars with hidden surveillance equipment. Today, all you need is an Android phone. You use such a phone with special software installed on it and can track the person who owns this phone. You can monitor his phone calls, you can control his location, you can even send messages from that person’s phone, view a list of contacts, etc.

This is a very powerful type of cyber surveillance device. If someone's phone is infected with this spyware application and this person brings it to the office, you can follow this person at work, watch business meetings and so on. Management and control of the spy device is carried out through the Internet. Spy module does not require any special additional equipment, everything is located inside the phone. When he has something to convey interesting, he communicates with you through the site command & control and transmits information. Later I will show you a demo how it works.
Now consider the countermeasures. In the old days, the so-called “cone of silence” was used to prevent eavesdropping. If someone was spying on you, you could always enter the "cone of silence" and communicate with the interlocutor completely freely.

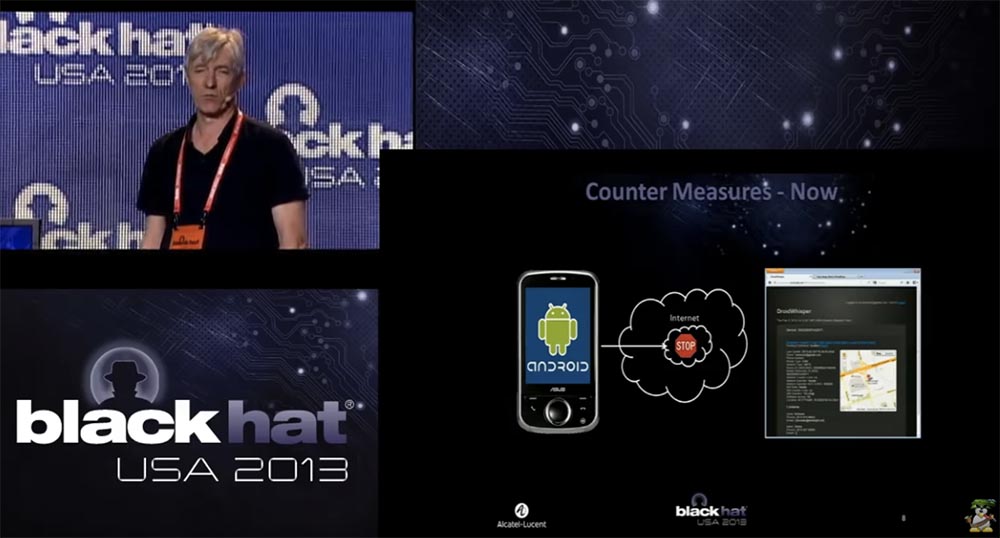
Today's "cone of silence" looks a little different. The company in which I work has developed a technology that can be placed on the network and which automatically detects the traffic of command & control, mediated by the transfer of which is the phone on the Android platform.

That is why we created the SpyPhone module, which we use as a demonstration when we go to our customers, who are mainly providers of mobile communication services and mobile Internet. We show them a “spy phone” to show that there is a huge security problem in the mobile network. This threat is still in its infancy, but could potentially cause great damage in the future. We use this module to educate our customers on hazards, so it’s natural that the second part of the demonstration is the presentation of our product, which can counter these hazards.
The smartphone is a very powerful device. It provides access to your location, connects to the Internet from almost anywhere, has a microphone, a camera, connects to local networks via Wi-Fi, and all this makes it an ideal platform for espionage.
I would say that a smartphone is an ideal cyber espionage tool that can be used to track a victim’s location, upload personal information, intercept and send messages, record conversations and take pictures without the owner’s knowledge. In the context of BYOD and APT, this is the ideal platform for launching internal attacks against corporate or government networks.
I think I’ve talked enough about this, so let's move on to the demonstration. On the left you see a screenshot from the screen of the phone, which will soon become spyware, this is the phone that I use now. On the right you can see the command & control console, which will be used by the person tracking this phone.

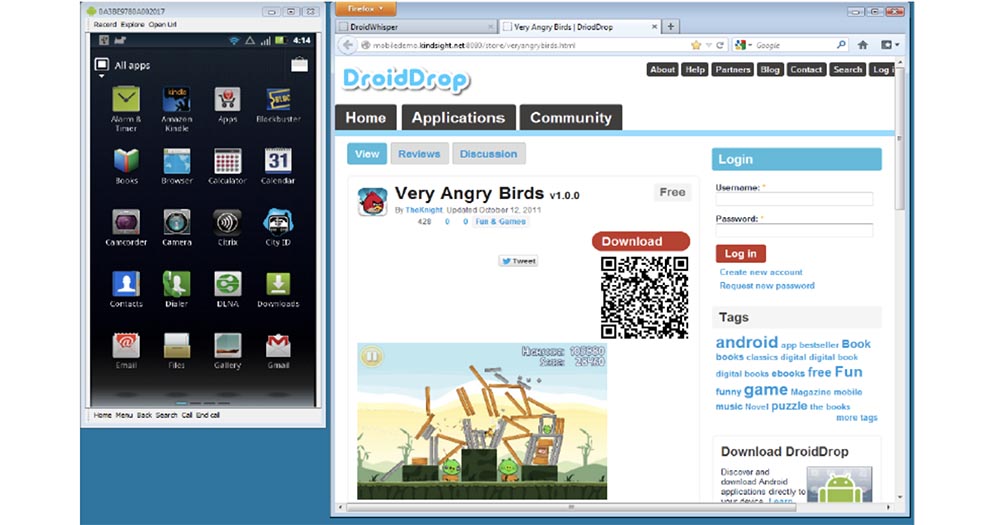
So, we took the malware, the SpyPhone module, and embedded it in a copy of the very popular game Angry Birds. Then we sent an email to one guy saying that he can download this cool game and play it. We can also place this infected game on third-party sites, where the user can download it. Now I’ll go to my browser to browse my received email.
So, when this guy receives a letter, he clicks on the link and goes to the real working app store for Android on the page with our game. We decided to name it Very Angry Birds (“Very Angry Birds”) because it contains the SpyPhone module.

So, the user downloads this game. On an Android phone, when you install an application, it provides you with a list of all the permissions it needs for its work.

It says that the application needs access to your location, personal information, network communications, data storage, paid services, phone calls. Since the user wants to install the application, he usually does not pay attention to all these permissions, which constantly appear during the installation of programs, and simply presses the "Install" button. Now you can see on the screen how the installation process is going. Next, we run the installed application. Now on the left you see a running game, and on the right - information of the command & control site that the smartphone is under control, and you can hear the sounds that accompany the game.

I will turn off the sound because it annoys me. So, note that the game is going on as usual, there is nothing extraordinary here that could attract the user's attention. There is no evidence that something strange is happening with the phone.
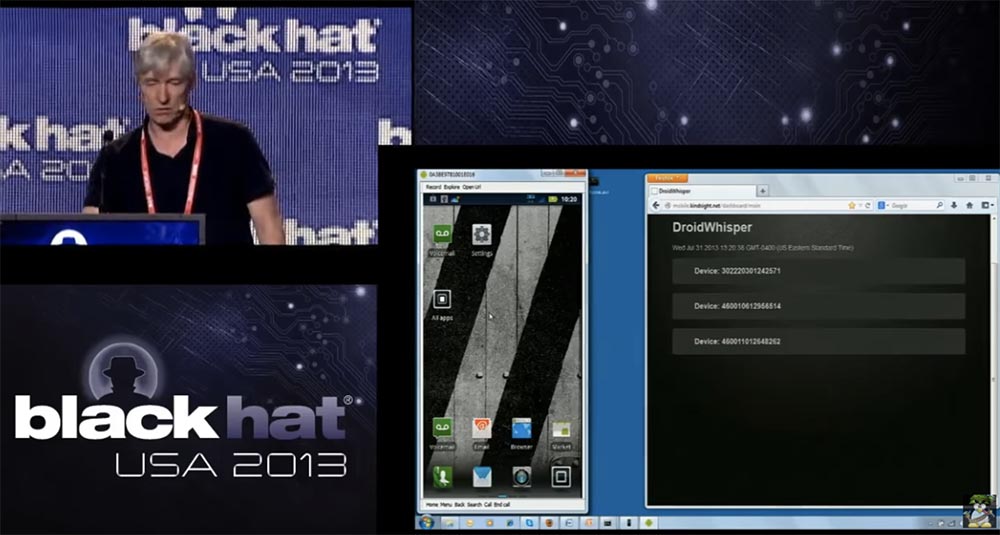
The user is playing, this is very cool, but even when he stops playing and closes the game, the spy module will continue its work in the background. Even if you restart the phone, the SpyPhone service will be restarted, now it is constantly present on this smartphone. So, this phone is infected with a cyber spy and is now displayed here in the console command & control. If I click on this line, the site will give me the information stored on this device. We can get a map with the location of this device - this is Las Vegas.

Let me emphasize that here the connection between the phone and the computer is not carried out directly, but via the Internet using a web server, which is located in Ottawa, where I work. The only reason why I connected this phone with a cable to a computer is the need to take screenshots. The console shows that we have other phones working at the same time. Here is one of them, located in China, so you can create an international network of "spy phones" and monitor them all the time while they are online.
So back to our phone in Las Vegas. You can see that here is the email address of the phone’s owner’s account, phone number, CDMA communication standard, network type, IMEI, country of the cellular operator, its name, SIM card status, location coordinates and phone owner’s contacts. All this information is uploaded to the command & control server, and we can track the owner of this phone 24 hours a day, 7 days a week, and use all the information that the phone provides, including downloading the contact list of this particular person. This will give us a list of other potential targets, if we use a kind of industrial cyber espionage, when we want to know who the owner of the phone communicates with and who does business with. We could use this contact list to target specific individuals.
You can imagine that an attacker distributes this game to all stores Android applications, and after people download it, you focus on some employee of a particular company, on the list of his contacts and so on.
Another thing we can do is update the installed spyware and send messages to the infected phone. You can use it for other purposes, for example, just to frighten people with such messages. We can access SMS messages and email, determine the location of the phone. All these operations are indicated in the upper part of the management console of the captured phone, they are highlighted by the blue interface. Another thing you can do is turn on the camera of the phone, I will try to do it right now. I take the phone in my hands and click on the “Peep” function in the control console, it will take some time, since you need to take a photo and send it to the command & control site. As you can see, my photo made by the front camera first appears, followed by a photo of this room taken by the rear camera. Thus, I can remotely take pictures on the infected phone and receive these photos.
If you notice, the game is still on the screen, so that the person will not even notice that the photo was taken. This is done in the background without the user's knowledge. We can use the same technology to shoot video. The last thing I want to demonstrate is the listening function. So, I say to the phone "This is a test, one, two, three, this is a test, one, two, three." Then I click on the Play Audio button, the connection takes a little time, and now you hear the repetition of my words.

So, I recorded the conversation through the microphone of the phone and uploaded it to the command & control site, so this is pretty cool. So this was a demonstration of what SpyPhone technology can do.
Now let's talk a little about how we developed the design and technology of our software and why we made such design decisions. I will go back to the previous slides.

First, we wanted to combine our malware with the original functions of the phone and create a trojan-type spyware program with remote access that would work with the phone on the Android platform. We took as a basis the demo application called “Searchable dictionary” and modified it so that it could insert a spyware module, and implemented it as a normal application for “Android”.
That is, we have adhered to the design of the original programs for "Android" using Java. We needed it to contain all the necessary components inside, to work in the background, even if the application was stopped, started when the phone was loaded. Our second task was to provide easy integration of SpyPhone into official applications. It worked, and our malware didn’t interfere at all with other applications installed on the phone. As the command and control command & control server, we chose NodJS a web server with HTTP data transfer. For the teams managing our program, we used the JS interface, and the teams themselves looked like this:
update - send information to the server,
toast - display a message on the screen,
shutdown - stop working SpyPhone,
sms - send SMS message to contact
location — send phone location information to the server,
peep - take a photo and send it to the server,
listen - record sound and send to server.
All of this was fairly easy to program, since the creators of Android provided their system with a fairly powerful full set of SDK development tools. This set provides an interface for everything you want. We have never been engaged in the development of programs for Android, but thanks to this SDK we didn’t even have to learn anything and we developed this thing in a few weeks.
The next slide shows the initial “Searchable dictionary” design, on the basis of which we created the SpyPhone, using the Java codes that you see here. We added a part to this app called droidwhisper.

This is the part that we were going to cut and paste into the appropriate application later. We had no experience creating special exploits that would exploit application vulnerabilities, so we imported a standard API that Android provides:
User information
- import android.accounts.Account;
- import android.accounts.AccountManager.
Phone and SMS
–Import android.telephony.SmsManager;
–Import android.telephony.TelephonyManager.
Location
–Import android.location.Location;
–Import android.location.LocationListener;
–Import android.location.LocationManager;
Record media files (audio and video)
- import android.media.MediaRecording.
Camera
–Import android.hardware.Camera;
–Import android.hardware.Camera.PictureCallback;
–Import android.hardware.Camera.PreviewCallback;
–Import android.hardware.Camera.Size;
–Import android.media.AudioManager;
–Import android.view.SurfaceHolder;
–Import android.view.SurfaceView.
the Internet
–Import org.apache.http.HttpResponse;
–Import org.apache.http.NameValuePair;
–Import org.apache.http.client.ClientProtocolException;
–Import org.apache.http.client.HttpClient.
Someone said that recording video and taking pictures when the phone is in the user's pocket is not very good. Therefore, if you want to make a good photo, you send a text message to the owner, because we have his phone number. He receives a message, holds the phone face to himself to read it, and during this time you take a photo with the front camera. If you just call him, he brings the phone to his ear, and at that moment you can take a picture with the rear camera.

Making the camera work is a bit more complicated, so we used a whole set of classes, for example, AudioManager, SurfaceHolder, and the like. We had to provide for a temporary shutdown of the click sound when a photo is taken so as not to attract the user's attention, if this function is activated in the settings of his camera. In addition, we made sure that the taken spy photos or videos were displayed in the phone gallery in the form of 1-pixel thumbnails so that the user could not see them. So we had to use several tricks to ensure the invisible work of our spyware module. As I have already noted, almost everything to ensure communication with the command & control server is contained in the phone itself. We also used some of the security flaws of Android.
As you know, these applications must be signed to be installed on the phone, but this is not a problem, because you can use any old certificate for signing, because the main thing is that the application has a certificate at all, no matter which one. Later I will tell you more about it.
So, this was a brief description of the design that we used to create the application. Now I will tell you about the implementation process, that is, how we took our malicious module and inserted it into the application.
The first thing we did was choose the game Angry Birds. We chose it not because it is a very good game, but because of its popularity. Our SpyPhone module can be entered into absolutely any application. First of all, we need a copy of the original .apk file. This is an archive containing all the components of the application. Inside the application file is Java code, or rather, not quite Java — this is the code for the Dalvik virtual machine to work. This code can be replaced with other content, this is called a master key vulnerability. So, we have to open this .apk file and disassemble it, that is, have a list of all the components to be disassembled.
So, first of all, we extract all the components of the Angry Birds 2000 application.

Then we insert our example / android / droidwhisper directory into the smali directory, and it is in the final droidwhisper folder that we find the modified files of the Searchable dictionary application containing our spyware module.

We downloaded the Angry Birds game from the Google Play Market and made a copy of it. The next thing we’re worried about is signature keys. All these files you see in our directory called inject.
During the disassembly process, we used Apk_tools, a tool for managing .apk files. Now, using the command line, I show how we proceeded to disassembling Angry Birds.

Then we started directly disassembling the application. We created the Angry Birds directory where we inserted all the components of the application. Since this is a demo, you have to wait a bit until the disassembly process is over. So, you see rad catalogs, the assets folder is located first, there are such things as sounds, then there are resourses folders, lib libraries, but the key is the smali directory, which contains the code and the assembly language format.
23:00 min
BLACK HAT conference. How to make a spy phone. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/434052/
All Articles