As I spoke at the fifth time on DefCamp
On November 8-9, 2018, the 8th DefCamp 2018 International Conference was held in Bucharest (Romania), devoted to the issues of information security and information protection technologies. DefCamp is one of the most successful conferences on hacking and information security in Central and Eastern Europe; among others, Hacktivity (Hungary) and CONFidence (Poland). The purpose of the event is to engage in a discussion on practical new research security experts, entrepreneurs, academic, public and private sectors.
DefCamp gathered more than 1,800 participants from Romania and neighboring countries, with different knowledge and experience - from students to managers in various fields, information security experts and researchers.

The event is organized directly by a non-governmental organization, the Cyber Security Research Center from Romania . According to them, this year the number of participating countries was 35, including Europe, the USA, India and the United Arab Emirates, 60 speakers and 400 companies.

')
The format of the event included a traditional section with reports and a CTF competition.
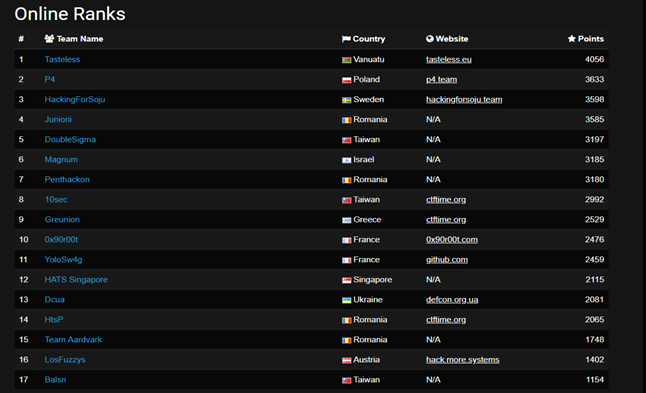
The first three CTF places: the Republic of Vanuatu (Melanesia), Poland and Sweden team; in fourth place is the team from Romania; teams from Russia this year was not. The full list is available by reference .
The section with reports this year took place with three parallel tracks; for comparison, last year there were two tracks.

This year, DefCamp was again HackerVillage, where various projects were exhibited - from information security to gaming. Unlike last year, the startup section was removed as not justified.
This year was also marked by the participation of the group of the Austrian consulate (as it was last year), but now it was a small discussion panel for 3-4 people for a couple of hours.
The conference part of the event was aimed at the exchange of progressive and innovative ideas, the results of the latest research and development, professional experience in all areas of IT security. At the same time, it is important to note that the quality of reports is high, the experience of the speakers is different and a look at security issues also differs taking into account personal opinions and peculiarities of solving problems in each specific case, including from country to country. For example, speakers from India, Pakistan and Eastern Europe willingly detail the technical side of the problem under discussion, while American colleagues reduce them to an organizational issue and the issue of trainings / training or the presentation of facts, examples with ornate narrative logic. However, this year most of the reports were in the format of business & high level rather than technical, and most of these were labeled as “technical” instead of “business” in the program.

The subject matter of the conference included:
The report on the old-fashioned offline principles and getting information from the network together with misinformation, ranging from fake news articles to specially prepared interviews. Speaker Dan Demeter from the Romanian representative of Kaspersky Lab tried to tell how to distinguish true news from fakes, but the proposed methods were mostly empirical, with poorly expressed metrics, and from the metrics were reduced to an excess of news (and formulations used in them) of the same type to the news opposite content.

Rapporteur Cosmin Radu has built a speech around Burp's capabilities for an attack on encryption: identifying weak encryption and its errors, disclosing a key, analyzing the stages of key formation within the context of setting up connections using the example of individual applications. In general, the report can be viewed as a business report from the Burp team or related researchers about the capabilities of the tool.
Report on the methodology for assessing and calculating indicators of security risks, taking into account the uniformity of metrics and the inclusion of CVSS ratings. The proposed methodology is reduced to a variation of the formulas like “how many did not apply protection mechanisms or did not close vulnerabilities in relation to the total number of mechanisms and measures”. In general, the latest publications of the ISECOM organization are connected with the universalization of tips and metrics.
A 2017 Kaspersky Lab staff report on the vulnerabilities of yachts and connected equipment on them, including navigation and IoT, security errors, brute force passwords of Microtik routers with ready-made tools (from the set for pentesters), hardcode passwords in firmware and yacht management software, and interception unencrypted traffic.

A report by Positive Technologies about mobile network vulnerabilities, their current state of security and its impact on the exchange of information between devices, applications in the context of everyday mobility and the Internet of things. The report has something in common with the materials vulnerability rating exposure 2018 and PT Telecom Attack Discovery and represents more research statistics on the subject of security of SS7 networks.

The next report of Jason Street about the main security problem - “human fail”. Jason touched on aspects related to end-user errors, their behavioral habits, which are supported by security teams in companies. The report, however, did not include the "human errors" of the developers, but the report noted that the main thing is the metrics for improving safety literacy in humans. This was a report on security training & security awareness for users with examples of different situations and cases in companies that bought user training and security auditing services.
Report on the analysis of the problem of IoT devices, the imbalance of CVE / CVSS databases and free-access publications on IoT vulnerabilities, features of vulnerabilities and malicious code for IoT. Partly, the problem of incomplete CVE / CVSS bases is that information about CWE (Common Weakness problems) is excluded to a greater extent, and a large number of IoT devices that no one has analyzed in such a volume and, all the more, has not brought together. The speakers, whose material can be found at the link , suggested several tools for automatic problem analysis:
Serbian report on security issues in medical institutions. The report is not related to IoT, but more was aimed at discussing the application of existing security solutions without taking into account the specific features of work and the needs of medical staff. Refinement of decisions should take into account these features and requirements of the GDPR (so that they do not strain or irritate)
HackerVillage has become a traditional event for the conference, in which various competitions are held.
CTF is one of the permanent events of the conference, covering various topics: artificial intelligence and machine learning, cyber warfare, cryptography, steganography, web security, network security, forensics, and reverse. Basic rules for participation:
The prize fund is 3 thousand euros and gadgets.
Contest participants created IPS signatures to reflect the greatest number of attacks. Conditions of the competition:
Exploit list:
IoT VILLAGE was designed to show a practical approach to hacking devices, allowing participants to win gadgets that they hacked (routers, webcams, etc.). Rules:
List of devices by category
Routers
Network attached storage
Security Systems
Home appliances
Printer
Cold hard cash

As part of the task of Critical Infrastructure Attack, it was proposed to gain experience in hacking industrial systems. For this you could choose from 4 tracks:
Malicious programs and attacks of the new generation are aimed at industrial systems, which can lead to huge financial and human losses. Testing for the penetration of industrial systems requires deep knowledge and skills, the acquisition of which depends on the availability of equipment. This competition focused on pentest of commercial hardware devices: PLCs and simulators, the configuration of which simulated the infrastructure using real-time PLCs and SCADA applications.
Typical attacks on ATMs were presented at the seminar “ATM: daily problems” (confidential information disclosure and unauthorized withdrawal of money from the terminal). The competition was divided into two phases. At the first stage, participants could intercept and analyze various types of traffic (network and USB). At the second stage, the contestants were given access to the USB interfaces for issuing commands to ATM devices and the network interface for conducting the MiTM attack. The purpose of the competition is to show different approaches to withdrawing money and intercepting card data.
Conditions of the competition:
Wifi PWNED Board is a demonstration of risks in real time when a person trusts wireless connections. The DefCamp team automatically analyzed the traffic on the network and looked for traces of users logging in to mail, to the website or other network services without using any protection mechanisms. The results were displayed on Wifi PWNED Board, in a friendly way to show everyone the danger of unreliable networks. As a tool, a rack with 50 routers was used, which for the user were fake Wi-Fi networks.

Target John is a competition in which participants received several details about a real goal, and they had to find out information about this particular person or group. During the competition, participants could express themselves in many areas: forensic science, pentest, network search. The task of the participants is to “hijack” the registration of the target without any notification, to introduce the backdoors of its device, and so on.
Rules of participation:
Startup corner is an opportunity to get startup support from the event partner Orange for an annual period. Up to three start-ups were selected based on the priority of filing an application and the degree of development of a startup.
I found the event useful due to the opportunity to hear first-hand the news regarding the security of the Internet of things (I will separately tell about my report in the following publications).

On the other hand, many materials often recur from event to event for several years, which is in a certain sense a plus, if the material is narrow. All tracks for performance are simply numbered, but behind the scenes it is known that materials on the main track are more general in order to attract an audience, on the second track 50/50 business and technical, and on the third - separate technical materials or interesting ones to a narrow circle of guests. Among the shortcomings it can be noted that this year they began to introduce fast-tracks for 15 minutes each, and often they were filled with materials that claimed to be a full-length report.
DefCamp gathered more than 1,800 participants from Romania and neighboring countries, with different knowledge and experience - from students to managers in various fields, information security experts and researchers.

The event is organized directly by a non-governmental organization, the Cyber Security Research Center from Romania . According to them, this year the number of participating countries was 35, including Europe, the USA, India and the United Arab Emirates, 60 speakers and 400 companies.
About DefCamp 2018

')
The format of the event included a traditional section with reports and a CTF competition.
The first three CTF places: the Republic of Vanuatu (Melanesia), Poland and Sweden team; in fourth place is the team from Romania; teams from Russia this year was not. The full list is available by reference .

The section with reports this year took place with three parallel tracks; for comparison, last year there were two tracks.

This year, DefCamp was again HackerVillage, where various projects were exhibited - from information security to gaming. Unlike last year, the startup section was removed as not justified.
This year was also marked by the participation of the group of the Austrian consulate (as it was last year), but now it was a small discussion panel for 3-4 people for a couple of hours.
The conference part of the event was aimed at the exchange of progressive and innovative ideas, the results of the latest research and development, professional experience in all areas of IT security. At the same time, it is important to note that the quality of reports is high, the experience of the speakers is different and a look at security issues also differs taking into account personal opinions and peculiarities of solving problems in each specific case, including from country to country. For example, speakers from India, Pakistan and Eastern Europe willingly detail the technical side of the problem under discussion, while American colleagues reduce them to an organizational issue and the issue of trainings / training or the presentation of facts, examples with ornate narrative logic. However, this year most of the reports were in the format of business & high level rather than technical, and most of these were labeled as “technical” instead of “business” in the program.

The subject matter of the conference included:
- IoT security is the theme of the year.
- Infrastructure protection.
- Cybersecurity
- Malicious software.
- Social engineering.
- Mobile security in a broad sense, incl. in related areas.
- Other miscellaneous reports.
About the reports DefCamp 2018, which I was able to visit
The Hitchhiker's Guide to Disinformation, Public Opinion Swinging and False Flags
The report on the old-fashioned offline principles and getting information from the network together with misinformation, ranging from fake news articles to specially prepared interviews. Speaker Dan Demeter from the Romanian representative of Kaspersky Lab tried to tell how to distinguish true news from fakes, but the proposed methods were mostly empirical, with poorly expressed metrics, and from the metrics were reduced to an excess of news (and formulations used in them) of the same type to the news opposite content.

Burp-ing through your cryptography shield
Rapporteur Cosmin Radu has built a speech around Burp's capabilities for an attack on encryption: identifying weak encryption and its errors, disclosing a key, analyzing the stages of key formation within the context of setting up connections using the example of individual applications. In general, the report can be viewed as a business report from the Burp team or related researchers about the capabilities of the tool.
OSSTMM: The “Measure, Don't Guess” Security Testing Methodology
Report on the methodology for assessing and calculating indicators of security risks, taking into account the uniformity of metrics and the inclusion of CVSS ratings. The proposed methodology is reduced to a variation of the formulas like “how many did not apply protection mechanisms or did not close vulnerabilities in relation to the total number of mechanisms and measures”. In general, the latest publications of the ISECOM organization are connected with the universalization of tips and metrics.
Remote Yacht Hacking
A 2017 Kaspersky Lab staff report on the vulnerabilities of yachts and connected equipment on them, including navigation and IoT, security errors, brute force passwords of Microtik routers with ready-made tools (from the set for pentesters), hardcode passwords in firmware and yacht management software, and interception unencrypted traffic.

Mobile signaling threats and vulnerabilities
A report by Positive Technologies about mobile network vulnerabilities, their current state of security and its impact on the exchange of information between devices, applications in the context of everyday mobility and the Internet of things. The report has something in common with the materials vulnerability rating exposure 2018 and PT Telecom Attack Discovery and represents more research statistics on the subject of security of SS7 networks.
You're right, this talk isn't really about you!

The next report of Jason Street about the main security problem - “human fail”. Jason touched on aspects related to end-user errors, their behavioral habits, which are supported by security teams in companies. The report, however, did not include the "human errors" of the developers, but the report noted that the main thing is the metrics for improving safety literacy in humans. This was a report on security training & security awareness for users with examples of different situations and cases in companies that bought user training and security auditing services.
IoT Malware: Comprehensive Survey, Analysis Framework and Case Studies
Report on the analysis of the problem of IoT devices, the imbalance of CVE / CVSS databases and free-access publications on IoT vulnerabilities, features of vulnerabilities and malicious code for IoT. Partly, the problem of incomplete CVE / CVSS bases is that information about CWE (Common Weakness problems) is excluded to a greater extent, and a large number of IoT devices that no one has analyzed in such a volume and, all the more, has not brought together. The speakers, whose material can be found at the link , suggested several tools for automatic problem analysis:
- Cuckoo Sandbox - for analyzing malicious files and websites of Windows, Linux, MacOS, Android, call tracing and behavioral analysis, dumping and analysis of network traffic, including encrypted, as well as support for the Volatility analysis tool.
- Firmware.RE is a free service for scanning and analyzing files (packages) of device firmware and fast detection of vulnerabilities, backdoors, and malicious code built-in (when building firmware).
Environment in healthcare
Serbian report on security issues in medical institutions. The report is not related to IoT, but more was aimed at discussing the application of existing security solutions without taking into account the specific features of work and the needs of medical staff. Refinement of decisions should take into account these features and requirements of the GDPR (so that they do not strain or irritate)
Hackerville
HackerVillage has become a traditional event for the conference, in which various competitions are held.
DefCamp Capture the Flag (D-CTF)
CTF is one of the permanent events of the conference, covering various topics: artificial intelligence and machine learning, cyber warfare, cryptography, steganography, web security, network security, forensics, and reverse. Basic rules for participation:
- Only 5 people in the team, including the team leader.
- DoS is prohibited.
- Finding vulnerabilities in the CTF infrastructure will bring more points.
- Hacks are counted only if the team was not hacked first.
The prize fund is 3 thousand euros and gadgets.
Defend the castle
Contest participants created IPS signatures to reflect the greatest number of attacks. Conditions of the competition:
- Legitimate traffic should not be blocked.
- Signatures cannot be used per port and protocol type.
- They are tested on exploits.
- FalsePositive exploits should not be blocked.
- Non-commercial signatures (after published as winners).
Exploit list:
- CVE-2018-3924 Foxit PDF Reader Javascript MailForm Remote Code Execution Vulnerability
- CVE-2018-7600 Drupal core Remote Code Execution
- CVE-2018-16509 Ghostscript Command Execution
- CVE-2018-17128 MyBB Visual Editor 1.8.18 - Cross-Site Scripting
- CVE-2018-9866 SonicWall XML-RPC Remote Code Execution
- CVE-2018-12895 WordPress 4.9.6 Directory Traversal
- CVE-2018-7745 Mikrotik Router OS SMB BOF
- CVE-2018-8840 Schneider Electric induSoft RCE
- CVE-2018-7756 Dewesoft X3 Remote Command Internal Access
- Atmosphere Java Framework Reflected XSS
Iot village
IoT VILLAGE was designed to show a practical approach to hacking devices, allowing participants to win gadgets that they hacked (routers, webcams, etc.). Rules:
- Each participant / team participating in the competition will be provided with the means to connect to the network, but they need their own laptop.
- Then each participant / team begins to attack the devices declared in the competition, using any tools or scripts that are available.
- At any given time to the devices are allowed no more than two participants.
- If a participant discovers a vulnerability on any of the devices, he informs his arbitrator on the spot (one of the judges).
- If a participant exploits a vulnerability in relation to any of the devices, he informs his arbitrator on the spot (one of the judges).
- All vulnerabilities must be granted to the organizers.
- Confirmation of winnings may vary from one participant to another depending on the risk of detecting a vulnerability, but if you managed to get root, the winnings are not disputed.
List of devices by category
Routers
- NETGEAR Nighthawk AC1900 Dual Band Wi-Fi Gigabit Router (R7000) with Open Source Support. Compatible with Amazon Echo / Alexa
- Zyxel Armor Z2 AC2600 MU-MIMO Wireless Cable Router
- Synology RT2600ac Wireless Router
Network attached storage
- Western Digital My Cloud EX2 Ultra, 2 Bay-uri, Gigabit, Dual Core, 1300 MHz, 1 GB DDR3 (Negru)
- Qnap TS-251A 2-bay TS-251A personal cloud NAS / DAS with USB direct access
- Synology DS718 + 2-Bay 2GB Black DS718 +
- Each NAS will be equipped with (1x) WD Black 1TB Performance Desktop Hard Disk Drive
Security Systems
- ANNKE Security Camera System HD 1080P Lite HD 4 + 1 Channels DVR Recorder
- Vstarcam C7833-X4 Wireless Remote HD Camera
Home appliances
- Bluesmart One - Smart Luggage
- HoneyGuaridan S25 Smart Automatic Pet Feeder (pet or petfood not included)
- LED TV Smart Toshiba, 81 cm
Printer
- Brother HL-L8260CDW Wireless Color Laser Printer
Cold hard cash
- 50 euro: find more than 1 vulnerability for any device.
- 50 euros: find more than 1 vulnerability for 4 any devices.
- 100 euros: find more than 1 vulnerability for any 9 devices.
- 100 euros: get root for any 2 devices.
- 200 euros: get root for any 6 devices.
Critical Infrastructure Attack

As part of the task of Critical Infrastructure Attack, it was proposed to gain experience in hacking industrial systems. For this you could choose from 4 tracks:
- The layout of the railway infrastructure, which used the SCADA application (control and data collection) to display operational data and control automation of railway switches, as well as mock-ups of solar and wind power plants with renewable energy sources.
- A simulated substation control system with a protective relay that received and transmitted signals from / to a special testing unit and directly connected to a single-line diagram / single-line diagram of a substation, illustrating some of the primary switching devices of the substation.
- Various hacking PLCs that emulated industrial control processes.
- Industrial arm of a robot.
ICS Humla CTF
Malicious programs and attacks of the new generation are aimed at industrial systems, which can lead to huge financial and human losses. Testing for the penetration of industrial systems requires deep knowledge and skills, the acquisition of which depends on the availability of equipment. This competition focused on pentest of commercial hardware devices: PLCs and simulators, the configuration of which simulated the infrastructure using real-time PLCs and SCADA applications.
Hack the Bank
Typical attacks on ATMs were presented at the seminar “ATM: daily problems” (confidential information disclosure and unauthorized withdrawal of money from the terminal). The competition was divided into two phases. At the first stage, participants could intercept and analyze various types of traffic (network and USB). At the second stage, the contestants were given access to the USB interfaces for issuing commands to ATM devices and the network interface for conducting the MiTM attack. The purpose of the competition is to show different approaches to withdrawing money and intercepting card data.
Conditions of the competition:
- The goal is to get confidential information from a bank card or withdraw money from an ATM.
- Each participant / team participating in the competition was provided with a bank card and funds for receiving network and USB traffic.
- Denial of service attacks are prohibited.
- Be sure to report the detected approach for obtaining confidential information and withdrawing money.
- Points are awarded based on the difficulty of finding.
- Extra points were awarded for attacks via USB.
- Tools and scripts at the discretion of the participants.
WiFi PWNED Board
Wifi PWNED Board is a demonstration of risks in real time when a person trusts wireless connections. The DefCamp team automatically analyzed the traffic on the network and looked for traces of users logging in to mail, to the website or other network services without using any protection mechanisms. The results were displayed on Wifi PWNED Board, in a friendly way to show everyone the danger of unreliable networks. As a tool, a rack with 50 routers was used, which for the user were fake Wi-Fi networks.

Target John
Target John is a competition in which participants received several details about a real goal, and they had to find out information about this particular person or group. During the competition, participants could express themselves in many areas: forensic science, pentest, network search. The task of the participants is to “hijack” the registration of the target without any notification, to introduce the backdoors of its device, and so on.
Rules of participation:
- The way to search for artifacts is not important.
- Points were awarded based on the corresponding artifact value.
- Bonus points were awarded for extreme style and creativity.
- The maximum team size is 1 player.
- Photo and video evidence was provided to the organizers.
Startup corner
Startup corner is an opportunity to get startup support from the event partner Orange for an annual period. Up to three start-ups were selected based on the priority of filing an application and the degree of development of a startup.
Afterword
I found the event useful due to the opportunity to hear first-hand the news regarding the security of the Internet of things (I will separately tell about my report in the following publications).

On the other hand, many materials often recur from event to event for several years, which is in a certain sense a plus, if the material is narrow. All tracks for performance are simply numbered, but behind the scenes it is known that materials on the main track are more general in order to attract an audience, on the second track 50/50 business and technical, and on the third - separate technical materials or interesting ones to a narrow circle of guests. Among the shortcomings it can be noted that this year they began to introduce fast-tracks for 15 minutes each, and often they were filled with materials that claimed to be a full-length report.
Source: https://habr.com/ru/post/433660/
All Articles