EOS Blockchain Vulnerabilities on ZeroNights 2018

This article will look at several real-world vulnerabilities in the EOS blockchain (one of Ethereum's competitors) and how they were built into the New-Generation Secure Slot Machine competition on the ZeroNights 2018. If you are interested in getting to know how things are going with security in this blockchain network, then welcome under cat.
Introduction
It all started with the fact that recently, during the audit of Etherium's smart contracts for security, one of our friends throws off an article about vulnerabilities in smart contracts in the EOS network. We are very interested, and we decided to understand the vulnerabilities in more detail.
All this eventually led to the creation of a competition for 2018 ZeroNights called “One-armed Bandit” with vulnerabilities in a smart contract.
')
We begin directly with the EOS blockchain network, how to work with it, and how everything is arranged inside it. There are a lot of articles describing the technology on the Internet, therefore, most likely, there will not be all the technical details, but we will try to convey the general sense in such a way that an ordinary user can get a basic idea of the EOS blockchain operation mechanisms.
EOS Technology Description
EOS.io is a blockchain of a new generation from the company Block.one , based on the concept of PoS ( Proof of stake ).
From the description of the network creators themselves: “EOS is an open source free blockchain network software that provides developers and entrepreneurs with a platform for creating, deploying and running high-performance decentralized applications (DAPP).”
If you briefly try to explain the concept, then it is well reflected in an excerpt from an article on Wikipedia:
The idea of a proof-of-stake (PoS) is to solve the problem of proof-of-work (PoW) associated with large amounts of electricity. Instead of the computational power of the participants, the number of cryptocurrency in their account counts. Thus, instead of using a large amount of electricity to solve the PoW problem, a PoS participant has a limited percentage of possible transaction checks. The limit corresponds to the number of cryptocurrencies held by the participantThe network is completely new, and the first launch of the main network (mainnet) took place on June 10, 2018. The main crypto-currency is EOS, and the main portal for developers, developers.eos.io
EOS.io Blockchain supports user-created applications using the WebAssembly code (WASM) - a new web standard with broad support from large companies such as Google, Microsoft, Apple and others.
At the moment, the most recent tool for creating applications that compile code into WASM is clang / llvm with their C / C ++ compiler.
For better compatibility, developers recommend using the EOSIO CDT (Contract Development Toolkit) - a set of utilities from the developers themselves for convenient and correct work on creating smart contracts.
The previous eosiocpp compiler is already deprecated and not supported, so everyone is recommended to switch to the new (at the time of writing) EOSIO CDT 1.5.
Unlike ether
Ether uses PoW (Proof of Work) in its concept, which requires costly calculations and the one who first solved a mathematical problem receives an award. That is, those who solved in parallel, but did not have time to decide, wasted electricity. In this situation, miners are fighting among themselves for more advanced technologies and equipment. To quickly generate blocks and, thus, earn.
Unlike Ether, in the EOS network, according to the PoS concept, the creator of the new unit will be selected by the system, and this is determined by the number of personal status - a fraction of the total cryptocurrency. Thus, who has more state, he has more chances to be selected by the system. But unlike PoW (air), the remuneration for generating a new unit is absent in principle, and the income of the miner is made up exclusively of transaction fees.
Conclusion - cryptocurrency based on PoW can be 1000 times more energy efficient.
Expand development environment
So, with a theory like done, go to practice. But in practice, everything looks much more interesting. The documentation at the time when we tried to figure out the summer and start doing something for ZeroNights 2018 was all very bad, and the main development portal was buggy, it was half empty and sometimes it didn't even work.
Test networks have not yet been properly launched, so I had to deploy my node. By the way, unlike opinion on the Internet, it was not so difficult to start it. Using the official documentation, we launched it from the docker by developers.eos.io/eosio-nodeos/docs/docker-quickstart
We will talk about the main utilities, programs for working with the EOS blockchain, which we had to deal with at the time of working on the competition:
- Nodeos - in fact, the service of the EOSIO node itself; You can configure and configure various plugins, such as CORS, history, and others.
- Cleos is a console utility for working with a node, calling contract methods and interacting with the wallet, keys, and accesses. The most frequent tool when working with EOS.
- Keosd - a console wallet, or more precisely also a wallet service, a private key repository.
- Eosio.cdt - Contract Development Toolkit, a so-called set of developer utilities for debugging and compiling contracts, generating ABI files and more.
- Eos.js - Javascript API library for convenient work with nodes and contracts via the web, is embedded on the site.
- Scatter - desktop wallet for secure storage of your account keys. There is a web library scatter.js, which interacts with the desktop Scatter wallet on web sockets and thus helps to work with DAPP applications in the browser.
Whew! .. Yes, there are a lot of applets, it's also not quite easy to figure them out. The description of all this deserves a separate post and is beyond the scope of this article. But let's imagine that we installed a node on our server and even learned how to call contract methods using cleos, if we had one.
Yes, the most important thing. We ought to scribble the smart contract itself. We will write it in C ++ and in order to do at least something sensible, we had to read a lot of documentation.
For understanding contracts, an example of a Hello contract is given everywhere. The main file is hello.cpp and the entire contract is described in it.
#include <eosiolib/eosio.hpp> using namespace eosio; class hello : public eosio::contract { public: using contract::contract; /// @abi action void hi( account_name user ) { print( "Hello, ", name{user} ); } }; EOSIO_ABI( hello, (hi) ) If you try to explain in a few words, then everything is simple . We load the eosio.hpp library, then we create the class (aka contract) hello and inherit the contract class. Create a void method hi and put the user variable into the parameters with the type account_name, also uint64_t. In the method, we output “Hello,” and the name that we will specify when calling the method. The last line, where EOSIO_ABI is located, is an auxiliary macro that accepts our class and public methods from this class, and also participates in the generation of the .abi file, where all public methods of the contract are indicated.
We study vulnerabilities
So, in the framework of that article , several vulnerabilities were described - let's consider them now in more detail.
Numerical Overflow - numeric overflow
When you call a contract, the node checks the type of the parameter, and if the data we are trying to feed it does not fit, the node will start swearing and this disorder will not be missed. BUT! If there is any algorithm for changing a number inside the contract, a sum of numbers or, say, a multiplication, then the number can change already inside the contract. This means that you can specify a number that the node will miss, but the contract will multiply, and the number will go beyond the permissible data type, which will lead to overflow.
What can it give? For example, there is a check for some numeric parameter, say, int Number <0, and it is known that int y is a signed number, and if a number overflows, the sign of the number will change to negative for large values. Thus, the check will be overflowed. And then, of course, it all depends on the criticality of this test.
For example, in the same article about vulnerabilities there is a real case where attackers could influence the balance parameter, thereby deceiving the system. The comments to the code describe in more detail the mechanism of interaction with the contract:
// typedef struct acnts { account_name name0; account_name name1; account_name name2; account_name name3; } account_names; // ( 1 EOS) // , , // «» void batchtransfer( symbol_name symbol, account_name from, account_names to, uint64_t balance ){ // require_auth(from); // account fromaccount; // require_recipient(from); require_recipient(to.name0); require_recipient(to.name1); require_recipient(to.name2); require_recipient(to.name3); // , . // is_balance_within_range ( eosio_assert(is_balance_within_range(balance), "invalid balance"); // , «» // , «» 1111111111111111 0, eosio_assert(balance > 0, "must transfer positive balance"); // amount 4 // , amount int64_t amount = balance * 4; // from, int itr = db_find_i64(_self, symbol, N(table), from); // , eosio_assert(itr >= 0, "wrong name"); // fromaccount db_get_i64(itr, &fromaccount, (account)); // , // , 0.1 EOS // , amount eosio_assert(fromaccount.balance >= amount, "overdrawn balance"); // sub_balance(symbol, from, amount); // 4 add_balance(symbol, to.name0, balance); add_balance(symbol, to.name1, balance); add_balance(symbol, to.name2, balance); add_balance(symbol, to.name3, balance); } Hacking was most likely carried out as follows. The attacker previously created 4 accounts and called the batchtransfer method directly, something like this:
cleos push action contractname batchtransfer \'{"symbol ":"EOS", "from":”attacker”, "to":{ “name0”:”acc0”, “name1”:”acc1”, “name2”:”acc2”, “name3”:”acc3”}, "balance":"111111111111111111 EOS"}' -p attacker@active 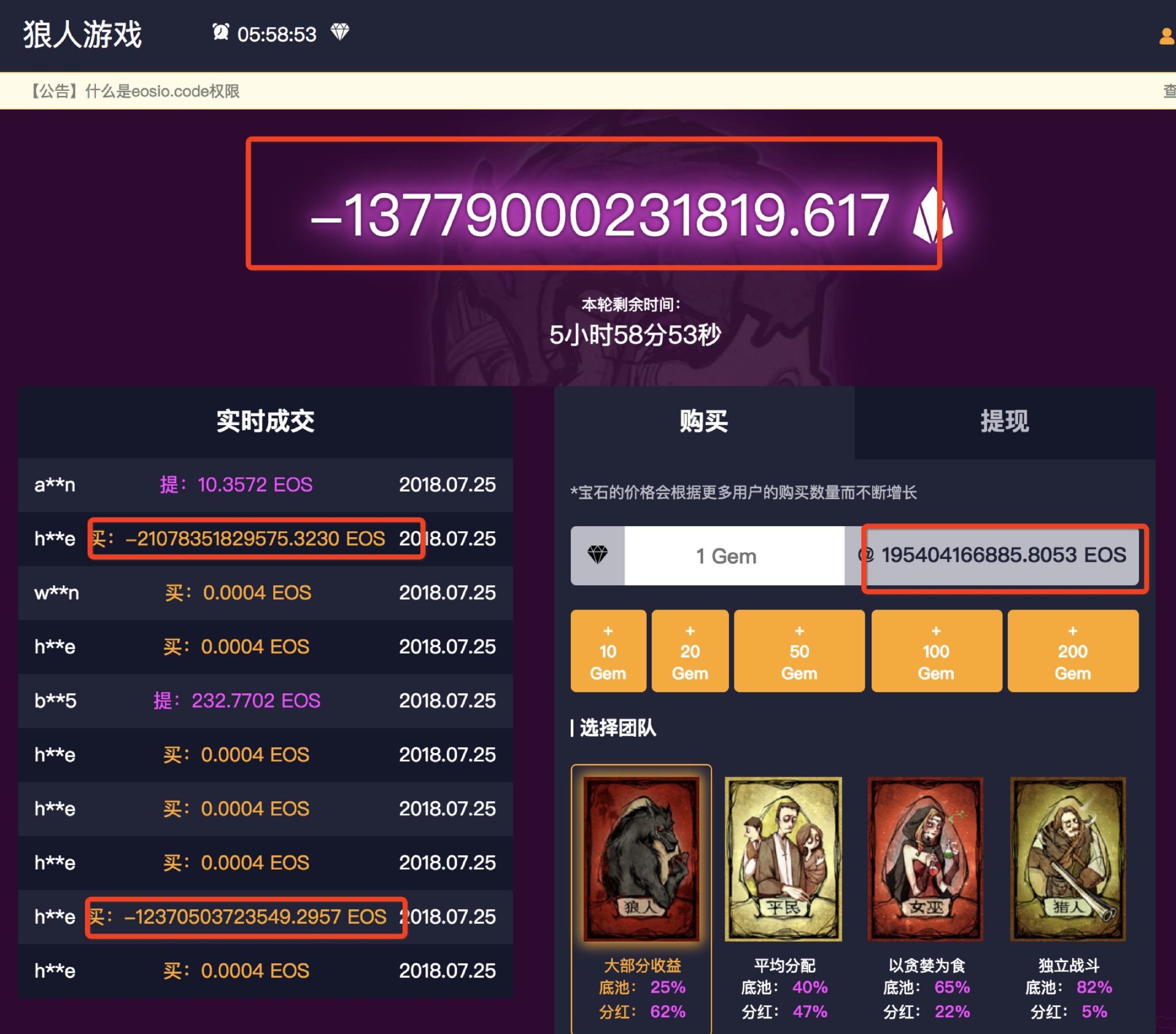
Immediately, this is only a guess; how exactly the hacking was done - we do not know, and if there are other thoughts on this or more accurate information, write in the comments.
Autherization check, authorization check
The lack of verification of the require_auth () contract method on user authorization will lead to the fact that any person who does not have the necessary rights can use privileged contract methods, for example, withdrawing money from a contract.
Lack of verification of method call rights
When sending money to a contract (EOS), you can indicate in a special macro what will happen next and what to do. Say, when receiving money, a certain algorithm will be called, for example, a roulette or something else will be triggered, as well as a check:
if( code == self || code == N(eosio.token) || action == N(onerror) ) { \ TYPE thiscontract( self ); \ switch( action ) { \ EOSIO_API( TYPE, MEMBERS ) \ } } // action == N(transfer) In this test, there is no limitation on calling the transfer method, which is why you can call the transfer method directly, without sending money to the contract. And this means launching a mechanism with a further gain, without spending a dime.
Competition for ZeroNights 2018
The idea of the contest was born on its own: once everything is connected with games and three vulnerabilities, therefore, we will make a game on the smart contract mechanism in the EOS.io blockchain. The game should be as simple as possible, but interesting.
Slot machine "One-armed bandit"! People who longed for easy money were always surprised - remember, there are no freebies in the world, or almost no. Here, by the way, it is quite there, or rather, it will appear when vulnerabilities are used in the course.
Frontend
Frontend games decided to make fashionable, beautiful and three-dimensional. Thanks vtornik23 , for not refusing to participate and helped us to make a fully front-end on the Unity3d engine.

Three-dimensional gaming machine "one-armed bandit"; By sending 1 EOS to it and pulling the plush lever, the player gets the opportunity to start the wheel of fortune and take the jackpot!
Contract Vulnerabilities
According to the idea of the game, the gain was considered to be the loss of three ZeroNights dolls, which in the numerical coefficient would be either 777 or 0. The chances of winning were equal to 0.02%, and some inattentive programmer tried to complicate the randomization algorithm by adding only multiplication (multiplication overflow) to it the amount of money sent, and was too lazy to think about the conditions in more detail, so I simply wrote if (result == 777 || result <1), which makes it possible to slip a negative value.
int rnd = random(999); int result = rnd * price.amount; uint64_t prize = 0; print("Result:", result); // BINGO 777 or 000 !!! ~ 0.02% if(result == 777 || result < 1 ) { prize = 100; sendtokens(from); } The smart contract itself is laid out on a githab , so that everyone can take a closer look at it from all sides and identify other vulnerabilities. About them already written a little higher, so that difficulties in their search should not be.
Rules of participation
The rules of participation are very simple: it was necessary to try to win or hack the mechanisms of the system. With the fall of 3 nesting dolls - Jackpot !!! The system charges 100 cryptocurrency units. If a participant receives the jackpot 3 times in a row, he becomes the winner and receives prizes from the organizers - branded hoodie, badges, various merch.
Of course, you could win by pulling the lever for a long time and hoping for luck, but fortune is unpredictable, and the winning percentage is very small, so it was easier to crack.
Contest results
As a result, the competition, in our opinion, was perfect. Awards were planned for 3 people, and just three managed to cope with the competition before the scheduled end date. The contest was held for 2 days, during which the participants had to solve the task. The official awarding ceremony and the presentation of gifts was at the closing of the conference on the main stage of ZeroNights 2018.
The main focus was on learning about the EOS blockchain technology, and we left a couple of clues, one of which no one could find. We will leave this riddle for later ...
Feedback from participants
Alexey (1 place)
ZeroNights is one of my favorite conferences, starting from the very first one, in Petersburg I didn’t miss a single one. Always gives a charge of enthusiasm for half a year exactly, and there in the spring PHDays :). The last 3 years I have been developing blockchain. This year, the blockchain got to ZeroNights (in the past, the truth seems to be the same, it was on the hax, but I missed it). First of all, after registering at the conference, I went to see what and how there with the blockchain. I thought it would be something like on PHDays, some kind of curved random or race condition on the air. But it turned out to be EOS, with which I had a little acquaintance on the first EOS hackathon, but it was not long, and besides all the settings for development were lost. The fighting spirit fell, and I went to wait for the start of the conference. But curiosity got the better, after all, what's wrong with EOS is wrong!
Stanislav Povolotsky (2 place)
For me it was a long but interesting competition. And it was a great opportunity to get to know the EOS blockchain architecture. The competition began with a surprise that the EOS (mainnet) network just does not get in - just for $$$. After prompting that the contract is deployed in the test network, registration in this network, scatter settings and viewing the transaction history for the gaming contract, it became immediately clear how to deceive the slot machine (the author of the contract did this several times during testing). But the confidence that so quickly and simply I was able to cope with the competition quickly evaporated as soon as the network did not approve all of my transactions with parameters identical to the winning transaction.
Irina (3 place)
Before participating in the contest, the work of smart contracts was presented only in theory, so it was very interesting to “meet them live”, see the source code, test the tools (and once again make sure that python is best of all)). The task turned out really very exciting. Thank!
In conclusion
Not to say that everyone coped easily. For some, it was a difficult 2 days, and only at the end the lucky ones managed to win using the drawbacks of any blockchain - if the information got into the blockchain, it is available to everyone, and if someone has already hacked something, then the other can see it way.
We thank all the participants and those who helped in organizing the competition.
See you at ZeroNights 2019, you will be waiting for new adventures!
Source: https://habr.com/ru/post/433552/
All Articles