Security Week 50: forecasts for 2019
 At the end of the year, Kaspersky Lab releases a traditional set of reports, summing up the outgoing year and predicting the development of cyber threats to the next. Today is a brief squeeze out of documents, the full versions of which can be read on the links:
At the end of the year, Kaspersky Lab releases a traditional set of reports, summing up the outgoing year and predicting the development of cyber threats to the next. Today is a brief squeeze out of documents, the full versions of which can be read on the links:Highlight the main topics: the evolution of targeted attacks, the emergence of new APT-groups with a fairly simple (but effective) malicious arsenal; the use of IoT for targeted attacks, and for mass; reducing the number of attacks aimed at mining cryptocurrency following the fall of the exchange rate. Directions of development of cyber threats: difficult to detect attacks on "iron" to obtain the widest possible access, the evolution of phishing using the personal data of victims, attempts to compromise the system for protecting mobile devices.
In a review of the main events of 2018, Kaspersky Lab specialists pay special attention to attacks on network devices and the Internet of things. A landmark example is the Slingshot campaign. The attackers exploited vulnerabilities in Mikrotik routers (about which they wrote a lot this year, for example, here and here ). Traditionally hacked routers are used to collect data, DDoS, attacks on other vulnerable devices and redirect users to phishing pages. In this case, the router was broken to attack its administrator at the time of visiting the device’s web interface, with further compromise of the entire enterprise network. The problem is not limited to routers, perhaps an increase in the frequency of attacks on the strategic infrastructure (companies or entire countries) - cellular networks (as has already happened in the case of the Regin campaign) or data processing centers.
Attacks such as Specter and Meltdown, and not only them, pose a potential threat to both infrastructure and end devices. Using vulnerabilities in hypervisors, malicious code in UEFI also theoretically allows you to get the widest possible access to computers, servers and their contents, and such attacks will be extremely difficult to detect. At the moment, this threat as a whole remains theoretical: attacks using the same Specter / Meltdown in nature have not yet been observed.
')
Experts at Kaspersky Lab predict the end of an era of large APT campaigns, but rather in the context of the possibility of attributing various attacks to a specific group. After disclosing a large number of APT security specialists, the organizers of coordinated attacks will seek to use more secretive and advanced methods of hacking, while not abandoning the already proven (and detectable) methods. Simply put, targeted attacks are set to flow, “tasks” are distributed to various “contractors”, which will be harder to combine according to certain features and features of the malicious code used by the command server. In Asia and the Middle East, in addition, many targeted attacks are recorded using widely available tools, and the further you go, the more difficult it will be to figure out who is attacking, why, and how this can be associated with other malicious campaigns.
Finally, experts pay attention to the leakage of users' personal data, which were quite a few this year, and the main “newsmaker” on this topic was the social network Facebook. There is a mass of private information, but it can be assumed that the data obtained on the black market can be used for more efficient and targeted phishing. If you look further into the future, it is more convincing to introduce yourself as a different person to “help” machine learning technologies. This is such a social aspect of the field of information security, when you can no longer guarantee who you are communicating with on the network, by telephone and even via video link.
Finally, the researchers evaluated the prospects for hacking mobile devices. In malicious campaigns, they are targeted more and more often, since successful hacking sometimes gives access to a much larger amount of personal data than hacking a victim’s computer. Moreover, if you look at the frequency of using exploits for vulnerabilities in any type of software (desktop or mobile), then the share of exploits for Android in it falls.

Most likely, this was due to a more rapid closure of vulnerabilities on real devices due to the regular distribution of patches. Nevertheless, the search for effective ways to hack mobile devices continues, not only for Android, but also for iOS. In the Apple ecosystem, for example, this year a vulnerability was discovered in the Device Enrollment Program interface for configuring and managing corporate devices. The possibility of hacking iOS with access to the device was also actively discussed, and in the summer Apple even restricted access to the phone through the Lightning port an hour after the device was locked. Large-scale attacks on mobile devices in 2019 are not expected, but attempts to bypass the protection systems will continue.
The effectiveness of attacks using physical access to the infrastructure is described in a recent study of the DarkVishnya campaign: an investigation of a series of cyber incidents each time led to the discovery of a “Trojan Raspberry Pi” in the corporate infrastructure.

Do not underestimate the traditional malware. According to Kaspersky Lab, in 2018, cyber attacks were detected on 30% of computers, for a total of almost 22 million unique malicious objects. In the statistics of "Kaspersky Lab" pay attention to two interesting points. First, the number of attacks using banker Trojans, directly aimed at stealing money from the accounts of victims:

The number of users attacked by banker Trojans exceeded the number of attacks using encryption. Secondly, it is interesting to look at the statistics of attempts to infect computers with malware with a built-in miner cryptocurrency:
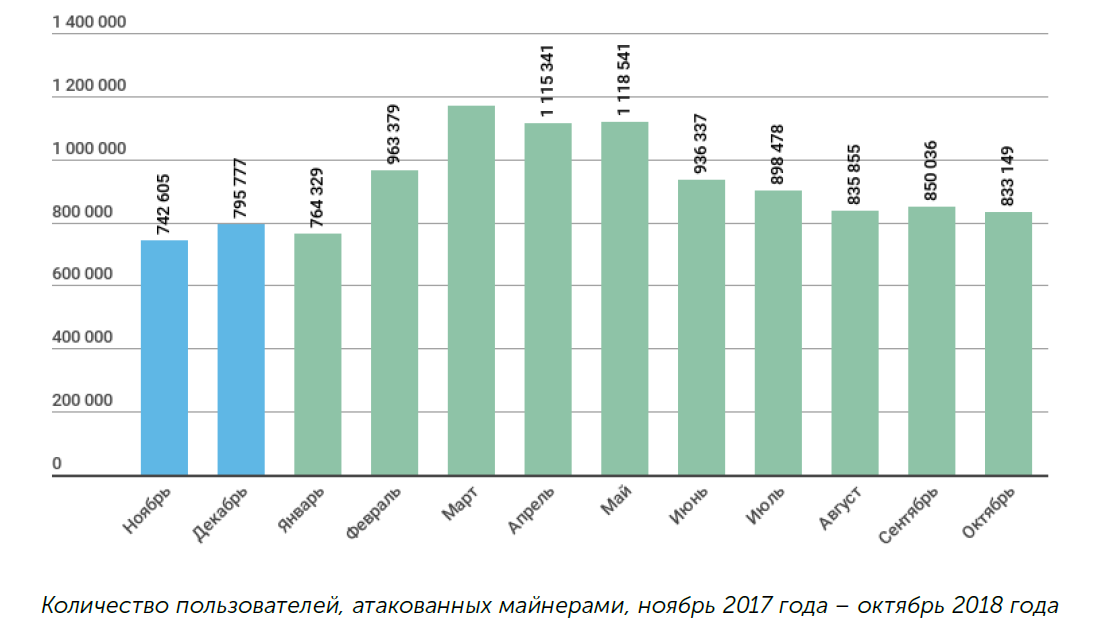
8.5% of all attacks with the use of malware occur in unauthorized crypto-mining. This is a lot, but even more interesting is the coincidence of the number of attacks with the course dynamics of the main cryptocurrencies: the fall in their value affected the intensity of the attacks. More statistics on crypto-miners are in a separate publication. Forecast on threats against cryptocurrency is given here .
In addition to the main link reports at the beginning of the post, Kaspersky Lab also published two specialized documents with forecasts of the development of cyber threats for the industry and the financial sector. All reports (including issues for previous years) are collected here .
Disclaimer: The opinions expressed in this digest generally reflect the position of Kaspersky Lab, but a digest without a disclaimer is not a digest. Dear editors are still recommending to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/432714/
All Articles