WireGuard - the perfect VPN of the future?

The time has come when VPN is no longer some kind of exotic tool for bearded system administrators. Tasks of users are different, but the fact is that VPN has become necessary for everyone at all.
The problem with current VPN solutions is that it is difficult to set them up correctly, it is expensive to maintain, and they also have a lot of legacy code of dubious quality.
A few years ago, Canadian information security specialist Jason A. Donenfeld decided that it was enough to endure, and began work on WireGuard . Now WireGuard is preparing for inclusion in the Linux kernel, it even received praise from Linus Torvalds and in the US Senate .
The advantages of WireGuard over other VPN solutions:
- Easy to use.
- Uses modern cryptography: Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, HKDF, etc.
- Compact readable code, easier to explore for vulnerabilities.
- High performance.
- Clear and detailed specification .
Is a silver bullet found? OpenVPN and IPSec time to bury? I decided to figure it out, and at the same time I made a script to automatically install my personal VPN server .
Work principles
Principles of operation can be described like this:
- The WireGuard interface is created, it is assigned a private key and an IP address. Settings of other peers are loaded: their public keys, IP addresses, etc.
- All IP packets arriving on the WireGuard interface are encapsulated in UDP and safely delivered to other peers.
- Clients set the public IP address of the server in the settings. The server automatically learns the external addresses of clients when they receive correctly authenticated data.
- The server can change the public IP address without interrupting work. At the same time, he will send an alert to connected clients and they will update their configuration on the fly.
- The concept of Cryptokey Routing is used . WireGuard accepts and sends packets based on the public key of the peer. When a server decrypts a correctly authenticated packet, its src field is checked. If it matches the
allowed-ipsauthenticatedallowed-ips, then the packet is accepted by the WireGuard interface. When sending an outgoing packet, the corresponding procedure occurs: the dst field of the packet is taken and, based on it, the appropriate peer is selected, the packet is signed with its key, encrypted with the peer key and sent to the remote endpoint.
The entire core logic of WireGuard takes less than 4 thousand lines of code, while OpenVPN and IPSec have hundreds of thousands of lines. To support modern cryptographic algorithms, it is proposed to include a new Zip cryptographic API in the Linux kernel. At the moment there is a discussion about how successful this idea is.
Performance
The maximum performance advantage (compared to OpenVPN and IPSec) will be noticeable on Linux systems, since WireGuard is implemented as a kernel module. In addition, macOS, Android, iOS, FreeBSD and OpenBSD are supported, but WireGuard runs in the userspace with all the attendant consequences for performance. Windows support is promised to be added in the near future.
Results of benchmarks from the official site :
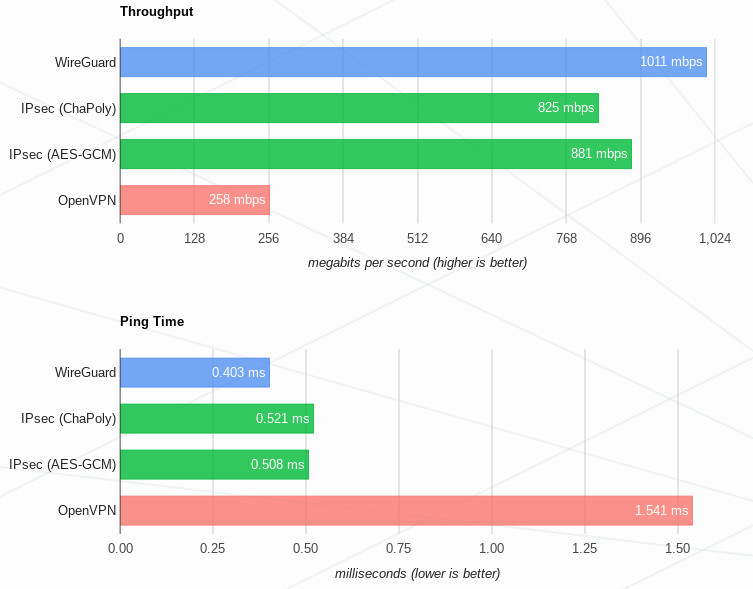
My experience of using
I am not a VPN configuration expert. Once I set up OpenVPN with handles and it was very dreary, and IPSec did not even try. Too many decisions need to be made, it is very easy to shoot yourself in the foot. Therefore, I have always used ready-made scripts to configure the server.
So, WireGuard, from my point of view, is generally ideal for the user. All low-level decisions are made in the specification, so the process of preparing a typical VPN infrastructure takes only a few minutes. Nakapapit configuration is almost impossible.
The installation process is described in detail on the official website, I would like to separately note the excellent support for OpenWRT .
Encryption keys generated by the wg utility are wg :
SERVER_PRIVKEY=$( wg genkey ) SERVER_PUBKEY=$( echo $SERVER_PRIVKEY | wg pubkey ) CLIENT_PRIVKEY=$( wg genkey ) CLIENT_PUBKEY=$( echo $CLIENT_PRIVKEY | wg pubkey ) Next, you need to create a server config /etc/wireguard/wg0.conf with the following content:
[Interface] Address = 10.9.0.1/24 PrivateKey = $SERVER_PRIVKEY [Peer] PublicKey = $CLIENT_PUBKEY AllowedIPs = 10.9.0.2/32 and raise the tunnel with the wg-quick script:
sudo wg-quick up /etc/wireguard/wg0.conf On systems with systemd, sudo systemctl start wg-quick@wg0.service can be used sudo systemctl start wg-quick@wg0.service .
On the client machine, create the config /etc/wireguard/wg0.conf :
[Interface] PrivateKey = $CLIENT_PRIVKEY Address = 10.9.0.2/24 [Peer] PublicKey = $SERVER_PUBKEY AllowedIPs = 0.0.0.0/0 Endpoint = 1.2.3.4:51820 # IP PersistentKeepalive = 25 And in the same way to raise the tunnel:
sudo wg-quick up /etc/wireguard/wg0.conf It remains to configure NAT on the server so that clients can go to the Internet, and everything is ready!
Such ease of use and compactness of the code base was achieved by eliminating the key distribution functionality. There is no complex system of certificates and all this corporate horror, short encryption keys are distributed approximately as SSH keys. But this raises a problem: WireGuard will not be so easy to implement on some already existing networks.
Among the shortcomings, it is worth noting that WireGuard will not work through HTTP proxy, since there is only UDP protocol as a transport. The question arises, is it possible to obfustsirovat protocol? Of course, this is not a direct VPN task, but for OpenVPN, for example, there are ways of masking under HTTPS, which helps residents of totalitarian countries to fully use the Internet.
findings
Summing up, this is a very interesting and promising project, you can now use it on personal servers. What is the profit? High performance on Linux systems, easy setup and support, compact and readable code base. However, it is still too early to rush to transfer complex infrastructure to WireGuard, it is worth waiting for inclusion in the Linux kernel.
To save my (and your) time, I developed the automatic installer WireGuard . With it, you can raise a personal VPN for yourself and your friends without even realizing it.
')
Source: https://habr.com/ru/post/432686/
All Articles