Conference DEFCON 18. You have spent all this money, but you continue to "have". Part 1
As usual, as in the past year, I cannot believe that people really come to my presentations to listen to what I am telling. Last year it was Sunday, at 10 am, I was in a state of hangover and thought that no one would come to see me.
Today is again Sunday, 4 pm, today I wanted to fly home, but, despite this, I thank you and really appreciate your attention, as in the past year, and I damn like such people and DefCon.
')
Theme of the presentation - you have spent all this money, but you continue to “have”. I did a lot of penetration tests, was in a lot of countries where I did pentesting, and everywhere I fought with various means of protection such as firewalls, AWS, and intrusion detection systems IDS and MAC. We still give them a run-up and this is very bad. Often, when I test, my report turns into an incident report, and I want to say: “hey, man, but you are the owner of all this, how can you use this sludge”? A whole topic was devoted to this, but let me first tell you who I am.
I’m a network application penster and I’m teaching this to people, and I’m a black guy at security conferences, yes, it's me! So, I break in, I'm fierce and I drink. Orders change, but I remain the same. So if you don't like guys like me, you can get up and leave.
So let me go back a little, about 10 years. I always do that because I have a special nostalgia for those times. In those days, pentesting was an easy task, we came to the client and said: “Hi, man, we are people from security,” and the client raised his hands up, thinking: “Damn, here are people from security!”
After that, we hacked into a client network with open source tools like ISS or Nessus. How many remembers that Nessus was free then?

So, we came to the client with all these things and easily hacked his website using exploits like RootShell with PacketStorm - raise your hands, who remembers them! We scanned the ports to find the target, used all sorts of compilations, point-slash, all of these libraries, and opened the control panel.


Then we took screenshots of the vulnerability, on which you could see your passwords and other confidential information, and said: "well, everything, man, your network is captured!".

Then we compiled a report, wrote how lame was their network, and got paid for it. “Your network is fucking sucks, so pay me!”

But today, guys, all around is CISSP, independent certification of information security, and the dude who hires you thinks he knows more than you. I want him to say: “then why the hell did you hire me?”, And he answers: “you know, we did it, and that, we have IDS and MAC, we have that, we have it ...”. And you're spinning around in all this shit.
Let me tell you a little story. Everyone who knows me knows that I always have a story.
A few years ago I had a client who ordered pentesting. He said, “OK, Joe, I want you to audit these subnets and the ACL access control list for the VLAN.” Probably some of you have already done an ACL for the VLAN, so you guys are smarter than me, because I have never done this.
I say - well, what kind of audit should I do? He responds - VLAN audit, okay, I think I will go, look at the configuration of their network. And here I am sitting with a network administrator and I see that they have 90 VLANs for 300 users! I was just in shock and told him how this is possible, but he just answered - well, it happened! I took a small piece of paper and began to go around the people, asking, “Do you need this network? Do you need this network? Maybe you need this network? ”. So, I got around to everyone, I learned that who needed it, and it was a big, damn big company. I checked all these VLANs, certified some networks and reached one of the DMZ segments, which were 4 pieces in the company. I said to myself: “Hey, man, all these boxes need updating, they really need to be patched.” I went to the deputy general director and said that you have all this hardware that needs a software update, since you missed some SQL patches, PHP patches, and much more.
They had a meeting, because they constantly meet, and here one of the developers gets up and says: “No, no, we can't update it, these are our servers for development!” (Laughter and applause in the hall). How can I comment on the fact that the developer server is in the DMZ? And they answer me: “That's better!”.
So, I continue to work for the client, start my small pentesting and “bring down” a couple of racks, because it is easy to do. The client asks why our IDS system could not catch you, and I answer, and what, was IDS there? He says yes, we observe security with her help. I answer: “well, probably because someone worked on this IDS”!
Companies hire other companies to outsource their IDS, they manage them, compile reports and do a lot of other shitty things. So, I had to take a look at their “box” and asked the guy to give me access to quickly examine it. I, hell, spent more than 2 minutes to log in via SSH, and saw that this bitch is slow to hell, so I began to check it for rootkits. It turned out that there were already 4 rootkits!

So pentesting is a cool thing! So, what do I do when I oppose these guys from large companies, when I audit all these fucking banks, all these fucking companies - I turn to Google for help. First of all, I'm looking for SQL error messages, looking for files for remote control, everything that will give me quick access to the shell, the most vulnerable place. Never engage in such nonsense, like scanning vulnerabilities, immediately take the system "by the throat." So I always look for SQL injections, RF files, cross-site scripting, and after I find them, I turn to passive intelligence and OSINT, open source intelligence, for this I use Maltego. I act as a woman who wants to catch her husband for adultery - I look everywhere! I'm trying to understand what their subnets are, where all these things are located, I use this incredible tool called Firefox. Believe me, what he can do will surprise you!
Passive intelligence is a basic tool that you really should try. I am sure that most of you are already using it, this technique definitely needs to be used. Then I look for load balancers, now I pass about 30% of my penetration tests through load balancers, this is really a handy thing. I adjust the load to the “box” and find out if it is load balancing DNS or HTTP. For example, when you send packages and they fly through all of these paths, it makes testing a little more difficult.

Then I return to the awesome Firefox browser and change the contents of the HTTP Headers search bar header in real time. This allows you to send some general requests to the server.

So if you send the first packet and the answer “5” is returned to you, then you send another packet to the same box and it returns you the answer “6”, it means that you have load balancing. The same with the dig command and Netcraft.
Netcraft is an amazing thing. For example, you are looking for something like “F5 BigIP” and get IP addresses with already balanced load. During pentesting this was very important to me. The load balancer is detected by a shell script or using Halberd, a Python script that does the same thing. So these are really good things that help you determine the real IP of the host that you intend to attack and which is behind the load balancer.

The next thing I come across is the detection of IPS, or intrusion prevention systems. It seems that everyone has an IPS, but the vast majority of my clients use it in IDS mode. Just as it makes no sense to use hacking tools against a load-balanced host, it makes no sense to use them against a host that is IPS protected. Do any of you use this thing? Turn it off to hell because it blocks traffic! Indeed, try turning it off and see what happens. How many of you believe that this system blocks illegal traffic, she wrote to you about this? This is the same crap as all its similar systems. Do you agree with me? I just want to make sure that I'm not the only one who thinks so.
So, I need to find out if I need to fight against IPS, that is, if the attacked host is not under its protection, and for this I do some really simple things.

I’m a Linux guy, but now I’m forced to use Windows, so I feel a little soiled. First of all, I use cURL - these are command line tools, or scripts, and a library that passes data via a URL. With cURL, I'm going to win ../../WINNT/system32/cmd.exe?d. Believe me, this attack has not worked since Jesus walked the earth, so let me know if you can make it happen.
The only reason why this should be done is to try to find out if something is blocking your IP address or sending packets to reset your connection. Because if this thing sends you reset packets, you need to refer to cmd.exe? D, since it is likely that your address is blocking IPS. Reflecting in the same way, the guys from purehacking.com came up with the Active Filter Detection tool, or active filter detection. This is a very good Python tool that allows you to modify it a bit and customize to fit your needs.
I often encounter IPS, so I use 3-4 different IP addresses from which I shoot packets and see if I get a reset packet in response. If I receive, it means my IP address is blocked. I note that most IDS / IPS solutions do not monitor SSL-encoded traffic and other encrypted traffic. So the next thing I do is see if IPS can handle SSL. Let me remind you once again why we use Linux.
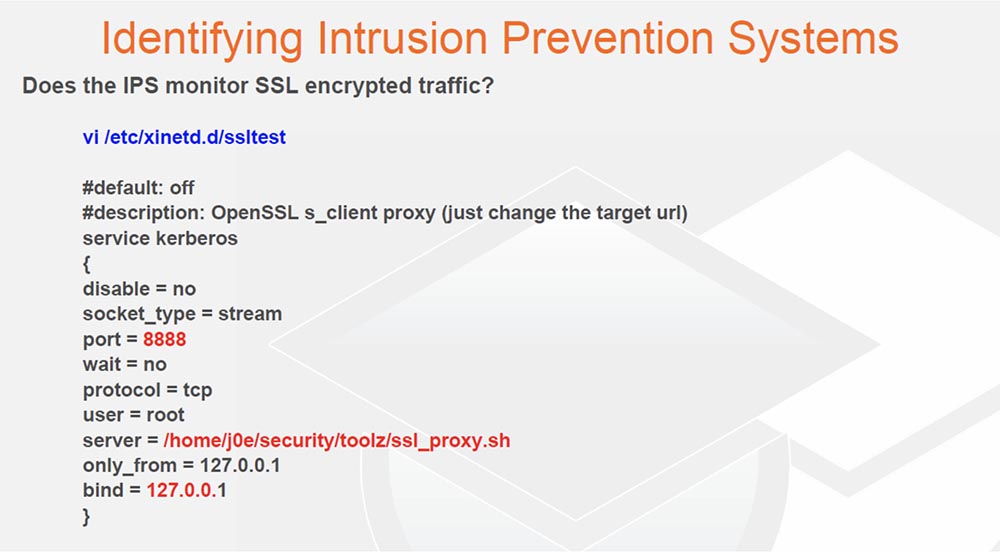
I create the xlnetd file and perform what I call the "SSL test". You see that I open port 8888, and then any data that I transfer to the local host 8888 falls into this little shell script, you see server = /home/j0e/security/toolz/ssl_proxy.sh.
On the next slide you can see the amazing abilities of my script - just look at this script from one line! Thus, the traffic goes straight to the open SSL, and then the connection is made to the target and all the same Active Filter Detection or cmd.exe is launched against the local host in order to determine whether my IP address is blocked.

The vast majority of my clients who deploy IPS and use blocking mode do not decrypt SSL traffic before it goes through IPS or IDS. Therefore, if you want to make your customers spend money with benefit, tell them to buy an SSL accelerator. It interrupts the SSL protocol before IPS and tries to decrypt the traffic.
Now let's see how you can attack a host through Tor and how to launch tools to scan the network through it. I do this quite often, launching privoxy and in hidden mode I use tools like Nessus to attack the host through port 8080. In this regard, it is worth recommending to your customers to block Tor output nodes.

Most companies have no reason to allow their customers to connect to their network through private networks, but they never block such connections. Therefore, you must force companies to block these nodes, this is what I primarily do for my clients. I don't have a slide with a description of the GLib proxy, because the hangover really affected my ability to do these slides this morning.
The last thing I do is identify WAF, Web Application Firewalls, or web application firewalls. How can I determine if a host is using WAF?
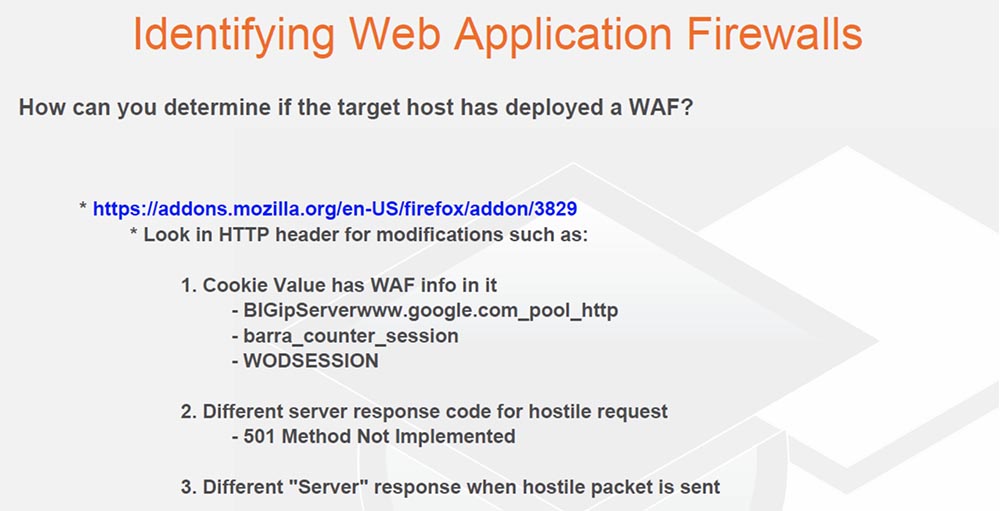
Since I am doing a lot of PCI-pinging, I know that some brilliant heads in the PCI representation realized that if you have vulnerable web applications that you don’t want to fix them and fix the vulnerability, then you can use WAF. In fact, detecting the use of such firewalls is easy. To do this, it is enough to send 1 real request to the host, one malicious request and see how its answers will differ. A malicious HTTP request may contain a payload that includes any nonsense such as apostrophe, quotes, question mark, minus, brackets, asterisks, and so on.

So it’s not at all difficult to find out if you are attacking a host protected with WAF.
So, you send any invalid characters, and then the tools shown on the next slide give you all kinds of these weird things. So, if you query cmd.exe and use the grep command line utility for the “501” method, that is, instead of error 404 “not found”, you will receive error message 501 - “the request method is not supported by the server”, then you probably encountered firewall mod_security, protecting the server Apache. New versions of this firewall have changed the situation, but who really cares about updating your WAF?
So I use the methods shown on the next slide quite widely, and also skip my attacks through the AQTRONIX Web Knight firewall.
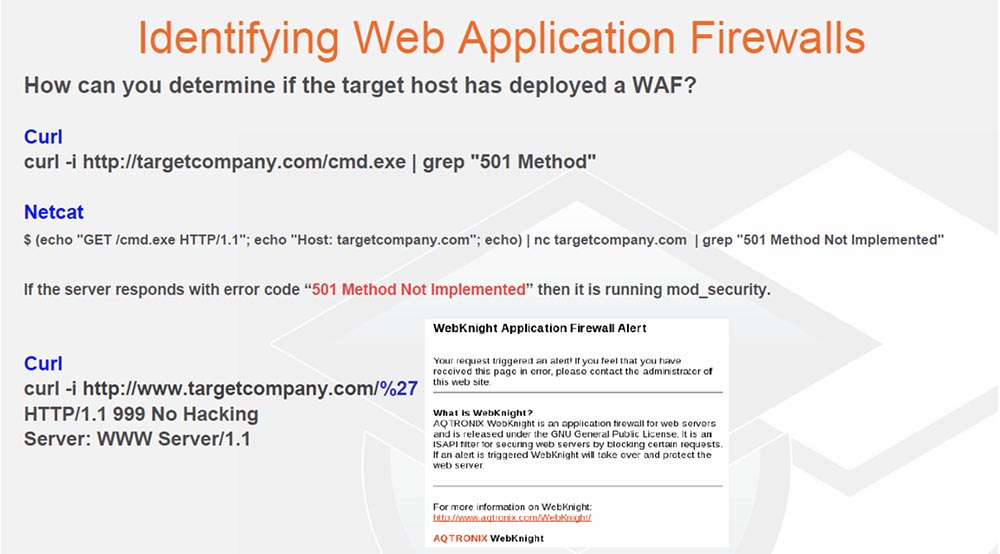
You see in the response header the code 999 No Hacking, I launch such a thing while testing - “No hacking”. So you just start adding things to the address bar to see what it gives and if you do not receive a 404 error message for a file that is not on the host.

I mean, if you send the correct request, which gives you message 200, and then send the wrong request for a file that does not exist, and the server generates an error 404, and then suddenly insert something for cross-site scripting, the server will send you have a completely different meaning of error. This will indicate that in this case there is some kind of protective mechanism.
Let's return to our games with coding. If you have determined that you are against WAF, see if this thing supports HEX, whether it processes utf7, utf-8, base16, base64, or a mixture of these encodings. Most WAFs don't work well with encodings, especially if you start mixing them with each other.
My good buddies, Sancho Gaci and Windell, last year created a Python tool called WAFW00F, a utility for detecting WAF.

This thing takes away the “fingerprints” of HTTP response headers and identifies WAF. I like this thing very much, now we already have a list of 10 or 12 WAFs, and it is constantly growing. The next thing you should pay attention to is called WAF Fun, which is a tool that uses the brute-force method on a set of web application firewall rules, and it is also written in Python.
I really admire these guys and wish that we have made even greater progress, but you know that we drink a little, then we work, then we drink again and we work again, so the process of creating such things is not easy. But I still hope that at the next DefCon conference I will be able to demonstrate how WAF Fun works using the brute-force method.
Another interesting thing is what we can do with Unicode. True, it is written in Ruby, and we all know that Ruby is crap.
17:00 min
Conference DEFCON 18. You have spent all this money, but you continue to "have". Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

Today is again Sunday, 4 pm, today I wanted to fly home, but, despite this, I thank you and really appreciate your attention, as in the past year, and I damn like such people and DefCon.
')
Theme of the presentation - you have spent all this money, but you continue to “have”. I did a lot of penetration tests, was in a lot of countries where I did pentesting, and everywhere I fought with various means of protection such as firewalls, AWS, and intrusion detection systems IDS and MAC. We still give them a run-up and this is very bad. Often, when I test, my report turns into an incident report, and I want to say: “hey, man, but you are the owner of all this, how can you use this sludge”? A whole topic was devoted to this, but let me first tell you who I am.
I’m a network application penster and I’m teaching this to people, and I’m a black guy at security conferences, yes, it's me! So, I break in, I'm fierce and I drink. Orders change, but I remain the same. So if you don't like guys like me, you can get up and leave.
So let me go back a little, about 10 years. I always do that because I have a special nostalgia for those times. In those days, pentesting was an easy task, we came to the client and said: “Hi, man, we are people from security,” and the client raised his hands up, thinking: “Damn, here are people from security!”
After that, we hacked into a client network with open source tools like ISS or Nessus. How many remembers that Nessus was free then?

So, we came to the client with all these things and easily hacked his website using exploits like RootShell with PacketStorm - raise your hands, who remembers them! We scanned the ports to find the target, used all sorts of compilations, point-slash, all of these libraries, and opened the control panel.


Then we took screenshots of the vulnerability, on which you could see your passwords and other confidential information, and said: "well, everything, man, your network is captured!".

Then we compiled a report, wrote how lame was their network, and got paid for it. “Your network is fucking sucks, so pay me!”

But today, guys, all around is CISSP, independent certification of information security, and the dude who hires you thinks he knows more than you. I want him to say: “then why the hell did you hire me?”, And he answers: “you know, we did it, and that, we have IDS and MAC, we have that, we have it ...”. And you're spinning around in all this shit.
Let me tell you a little story. Everyone who knows me knows that I always have a story.
A few years ago I had a client who ordered pentesting. He said, “OK, Joe, I want you to audit these subnets and the ACL access control list for the VLAN.” Probably some of you have already done an ACL for the VLAN, so you guys are smarter than me, because I have never done this.
I say - well, what kind of audit should I do? He responds - VLAN audit, okay, I think I will go, look at the configuration of their network. And here I am sitting with a network administrator and I see that they have 90 VLANs for 300 users! I was just in shock and told him how this is possible, but he just answered - well, it happened! I took a small piece of paper and began to go around the people, asking, “Do you need this network? Do you need this network? Maybe you need this network? ”. So, I got around to everyone, I learned that who needed it, and it was a big, damn big company. I checked all these VLANs, certified some networks and reached one of the DMZ segments, which were 4 pieces in the company. I said to myself: “Hey, man, all these boxes need updating, they really need to be patched.” I went to the deputy general director and said that you have all this hardware that needs a software update, since you missed some SQL patches, PHP patches, and much more.
They had a meeting, because they constantly meet, and here one of the developers gets up and says: “No, no, we can't update it, these are our servers for development!” (Laughter and applause in the hall). How can I comment on the fact that the developer server is in the DMZ? And they answer me: “That's better!”.
So, I continue to work for the client, start my small pentesting and “bring down” a couple of racks, because it is easy to do. The client asks why our IDS system could not catch you, and I answer, and what, was IDS there? He says yes, we observe security with her help. I answer: “well, probably because someone worked on this IDS”!
Companies hire other companies to outsource their IDS, they manage them, compile reports and do a lot of other shitty things. So, I had to take a look at their “box” and asked the guy to give me access to quickly examine it. I, hell, spent more than 2 minutes to log in via SSH, and saw that this bitch is slow to hell, so I began to check it for rootkits. It turned out that there were already 4 rootkits!

So pentesting is a cool thing! So, what do I do when I oppose these guys from large companies, when I audit all these fucking banks, all these fucking companies - I turn to Google for help. First of all, I'm looking for SQL error messages, looking for files for remote control, everything that will give me quick access to the shell, the most vulnerable place. Never engage in such nonsense, like scanning vulnerabilities, immediately take the system "by the throat." So I always look for SQL injections, RF files, cross-site scripting, and after I find them, I turn to passive intelligence and OSINT, open source intelligence, for this I use Maltego. I act as a woman who wants to catch her husband for adultery - I look everywhere! I'm trying to understand what their subnets are, where all these things are located, I use this incredible tool called Firefox. Believe me, what he can do will surprise you!
Passive intelligence is a basic tool that you really should try. I am sure that most of you are already using it, this technique definitely needs to be used. Then I look for load balancers, now I pass about 30% of my penetration tests through load balancers, this is really a handy thing. I adjust the load to the “box” and find out if it is load balancing DNS or HTTP. For example, when you send packages and they fly through all of these paths, it makes testing a little more difficult.

Then I return to the awesome Firefox browser and change the contents of the HTTP Headers search bar header in real time. This allows you to send some general requests to the server.

So if you send the first packet and the answer “5” is returned to you, then you send another packet to the same box and it returns you the answer “6”, it means that you have load balancing. The same with the dig command and Netcraft.
Netcraft is an amazing thing. For example, you are looking for something like “F5 BigIP” and get IP addresses with already balanced load. During pentesting this was very important to me. The load balancer is detected by a shell script or using Halberd, a Python script that does the same thing. So these are really good things that help you determine the real IP of the host that you intend to attack and which is behind the load balancer.

The next thing I come across is the detection of IPS, or intrusion prevention systems. It seems that everyone has an IPS, but the vast majority of my clients use it in IDS mode. Just as it makes no sense to use hacking tools against a load-balanced host, it makes no sense to use them against a host that is IPS protected. Do any of you use this thing? Turn it off to hell because it blocks traffic! Indeed, try turning it off and see what happens. How many of you believe that this system blocks illegal traffic, she wrote to you about this? This is the same crap as all its similar systems. Do you agree with me? I just want to make sure that I'm not the only one who thinks so.
So, I need to find out if I need to fight against IPS, that is, if the attacked host is not under its protection, and for this I do some really simple things.

I’m a Linux guy, but now I’m forced to use Windows, so I feel a little soiled. First of all, I use cURL - these are command line tools, or scripts, and a library that passes data via a URL. With cURL, I'm going to win ../../WINNT/system32/cmd.exe?d. Believe me, this attack has not worked since Jesus walked the earth, so let me know if you can make it happen.
The only reason why this should be done is to try to find out if something is blocking your IP address or sending packets to reset your connection. Because if this thing sends you reset packets, you need to refer to cmd.exe? D, since it is likely that your address is blocking IPS. Reflecting in the same way, the guys from purehacking.com came up with the Active Filter Detection tool, or active filter detection. This is a very good Python tool that allows you to modify it a bit and customize to fit your needs.
I often encounter IPS, so I use 3-4 different IP addresses from which I shoot packets and see if I get a reset packet in response. If I receive, it means my IP address is blocked. I note that most IDS / IPS solutions do not monitor SSL-encoded traffic and other encrypted traffic. So the next thing I do is see if IPS can handle SSL. Let me remind you once again why we use Linux.

I create the xlnetd file and perform what I call the "SSL test". You see that I open port 8888, and then any data that I transfer to the local host 8888 falls into this little shell script, you see server = /home/j0e/security/toolz/ssl_proxy.sh.
On the next slide you can see the amazing abilities of my script - just look at this script from one line! Thus, the traffic goes straight to the open SSL, and then the connection is made to the target and all the same Active Filter Detection or cmd.exe is launched against the local host in order to determine whether my IP address is blocked.

The vast majority of my clients who deploy IPS and use blocking mode do not decrypt SSL traffic before it goes through IPS or IDS. Therefore, if you want to make your customers spend money with benefit, tell them to buy an SSL accelerator. It interrupts the SSL protocol before IPS and tries to decrypt the traffic.
Now let's see how you can attack a host through Tor and how to launch tools to scan the network through it. I do this quite often, launching privoxy and in hidden mode I use tools like Nessus to attack the host through port 8080. In this regard, it is worth recommending to your customers to block Tor output nodes.

Most companies have no reason to allow their customers to connect to their network through private networks, but they never block such connections. Therefore, you must force companies to block these nodes, this is what I primarily do for my clients. I don't have a slide with a description of the GLib proxy, because the hangover really affected my ability to do these slides this morning.
The last thing I do is identify WAF, Web Application Firewalls, or web application firewalls. How can I determine if a host is using WAF?

Since I am doing a lot of PCI-pinging, I know that some brilliant heads in the PCI representation realized that if you have vulnerable web applications that you don’t want to fix them and fix the vulnerability, then you can use WAF. In fact, detecting the use of such firewalls is easy. To do this, it is enough to send 1 real request to the host, one malicious request and see how its answers will differ. A malicious HTTP request may contain a payload that includes any nonsense such as apostrophe, quotes, question mark, minus, brackets, asterisks, and so on.

So it’s not at all difficult to find out if you are attacking a host protected with WAF.
So, you send any invalid characters, and then the tools shown on the next slide give you all kinds of these weird things. So, if you query cmd.exe and use the grep command line utility for the “501” method, that is, instead of error 404 “not found”, you will receive error message 501 - “the request method is not supported by the server”, then you probably encountered firewall mod_security, protecting the server Apache. New versions of this firewall have changed the situation, but who really cares about updating your WAF?
So I use the methods shown on the next slide quite widely, and also skip my attacks through the AQTRONIX Web Knight firewall.

You see in the response header the code 999 No Hacking, I launch such a thing while testing - “No hacking”. So you just start adding things to the address bar to see what it gives and if you do not receive a 404 error message for a file that is not on the host.

I mean, if you send the correct request, which gives you message 200, and then send the wrong request for a file that does not exist, and the server generates an error 404, and then suddenly insert something for cross-site scripting, the server will send you have a completely different meaning of error. This will indicate that in this case there is some kind of protective mechanism.
Let's return to our games with coding. If you have determined that you are against WAF, see if this thing supports HEX, whether it processes utf7, utf-8, base16, base64, or a mixture of these encodings. Most WAFs don't work well with encodings, especially if you start mixing them with each other.
My good buddies, Sancho Gaci and Windell, last year created a Python tool called WAFW00F, a utility for detecting WAF.

This thing takes away the “fingerprints” of HTTP response headers and identifies WAF. I like this thing very much, now we already have a list of 10 or 12 WAFs, and it is constantly growing. The next thing you should pay attention to is called WAF Fun, which is a tool that uses the brute-force method on a set of web application firewall rules, and it is also written in Python.
I really admire these guys and wish that we have made even greater progress, but you know that we drink a little, then we work, then we drink again and we work again, so the process of creating such things is not easy. But I still hope that at the next DefCon conference I will be able to demonstrate how WAF Fun works using the brute-force method.
Another interesting thing is what we can do with Unicode. True, it is written in Ruby, and we all know that Ruby is crap.
17:00 min
Conference DEFCON 18. You have spent all this money, but you continue to "have". Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/432456/
All Articles