Conference DEFCON 21. DNS can be dangerous for your health. Part 2
Conference DEFCON 21. DNS can be dangerous for your health. Part 1
It was assumed that the boundaries of the organization’s domain are foo.com and you never want to use www.com . Microsoft changed this DNS behavior because, obviously, not all organizations have two levels for domain names.
')
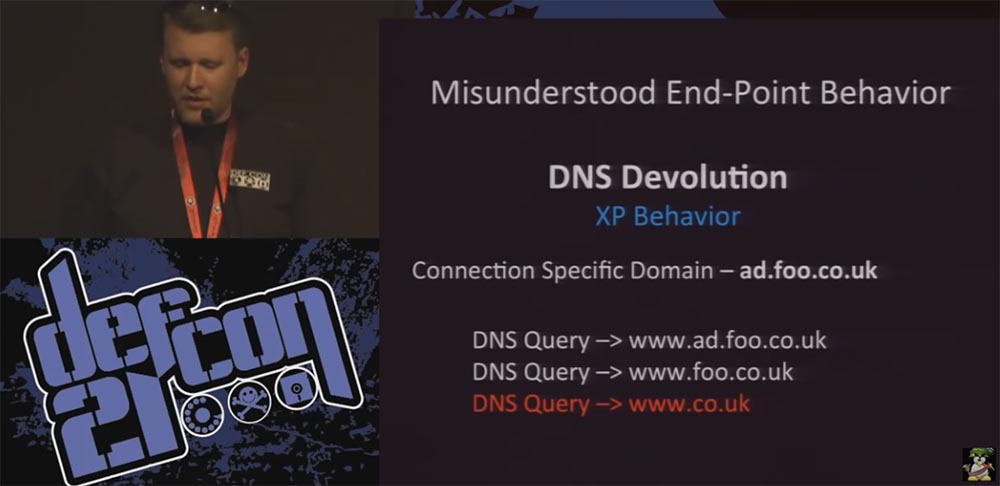
If your top-level domain is UK, then when you connect to a specific ad.foo.co.uk domain, the default DNS behavior will look like this:
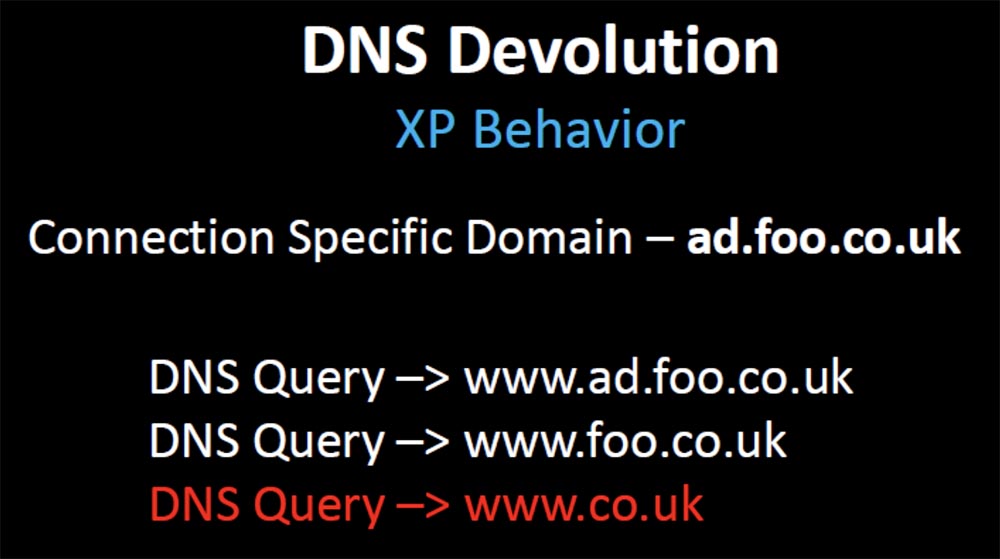
That is, the request will be sent beyond your domain name to www.co.uk. Therefore, a random hotfix was created, a security fix narrowing the organizational boundaries of the domain to 3, in which case the DNS resolution stopped after the second query www.foo.co.uk.
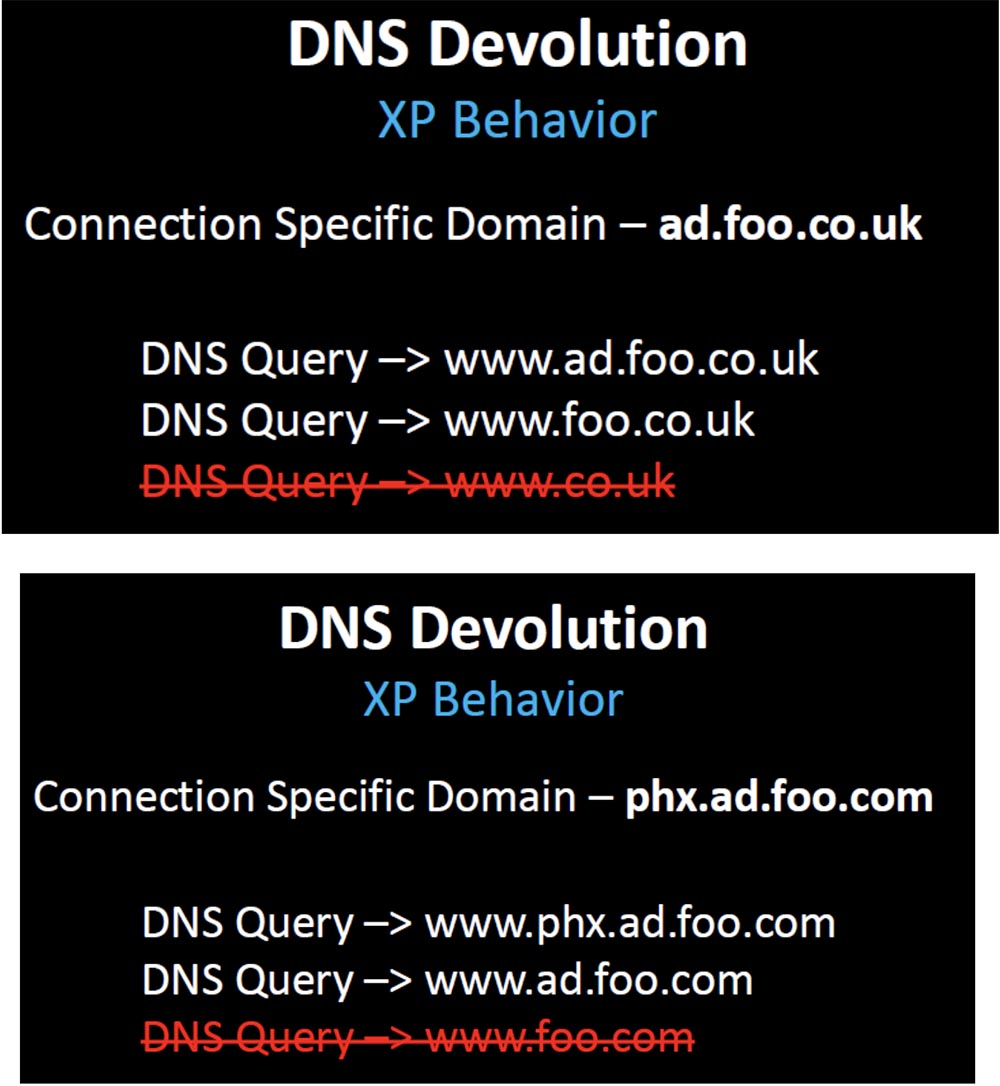
But in our example of a domain name, this security fix, designed to stop unnecessary advertising, broke hundreds of thousands of client companies whose domain name design depended on the original, initial DNS behavior. What are these companies doing? Do they change the design of the infrastructure to fit the new behavior that takes into account this random hotfix? No, they change the behavior back to what it was before.
The next slide shows the decision tree that Microsoft uses before creating the DNS query.
I know that it looks simple (laughter in the audience), and of course you are surprised that someone might understand this in the wrong way.
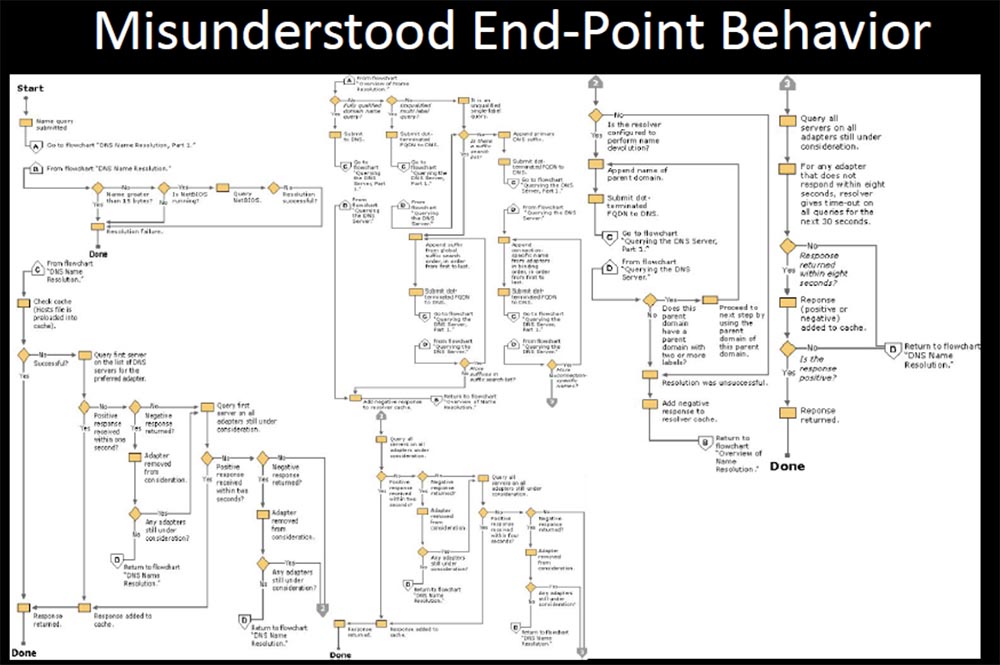
After that, there were dozens of fixes and updates to this DNS behavior, changing from version to version. But they documented it once, and if one of the branches of this tree changed, it completely broke your way of using DNS, and you could not change the settings to restore the original behavior. You had a problem, because with each new update your settings behave differently. Maybe something will break, or maybe not, that is, something that you do not expect at all may happen.
Thus, companies make changes through register or group policy editing, trying to restore the original behavior of the DNS, but some of them cannot do this properly where the behavior has been changed by another patch package. They are trying to undo the changes in order to restore this lost behavior because they want customers to be able to contact foo.com again.
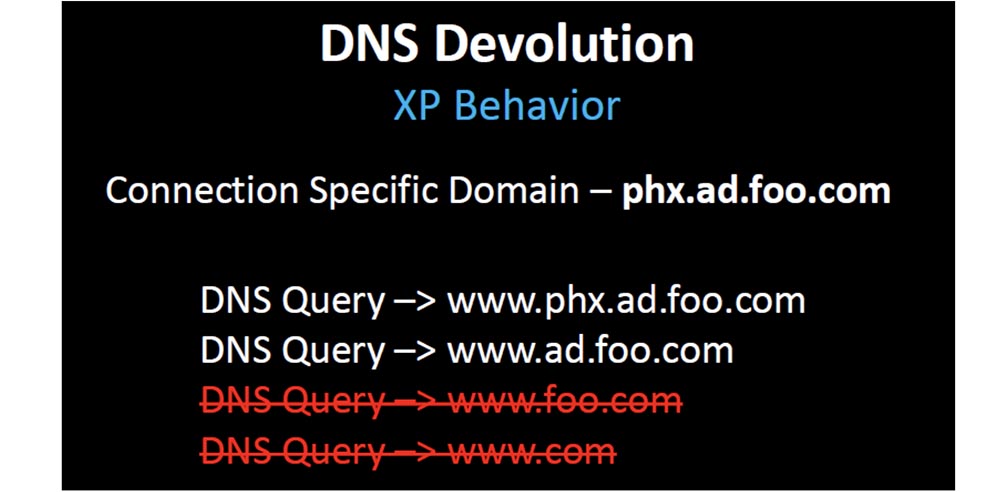
But in most cases, when they cannot restore two-level devolution, they simply get rid of the original two-level restriction. Thank you, Microsoft, for Windows 7 - now you can change the three default domain levels to 2, but the system will not allow you to reduce them to one.
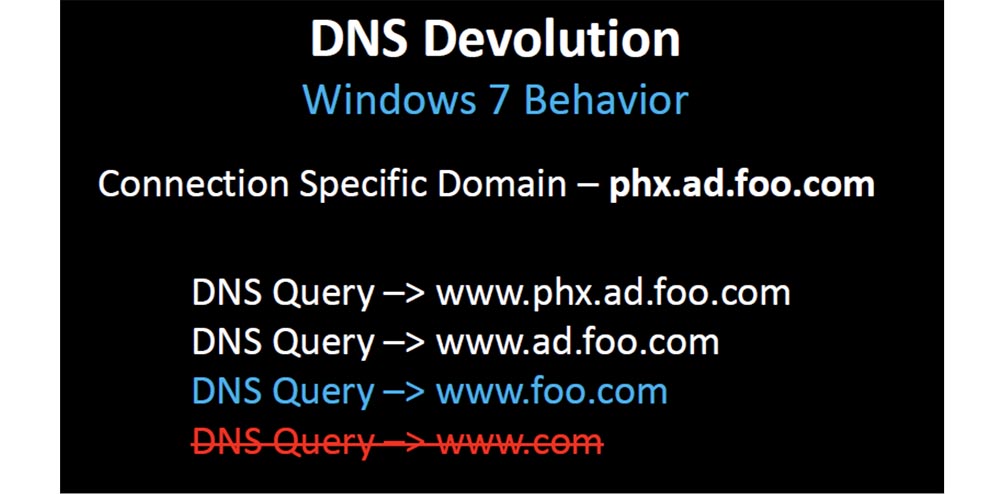
You might think that now everything is fixed, but what about BYOD devices and mobile devices using the XP configuration? I decided to check how many damaged configurations can still exist there. I have registered several domains, which are usually used only in a corporate environment.
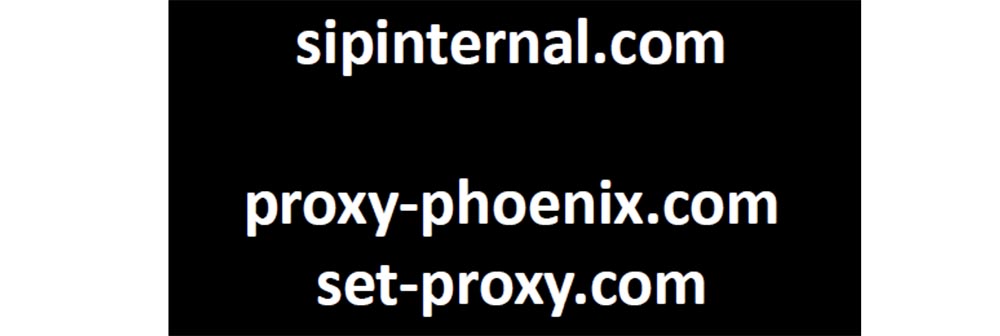
The first domain is the abbreviated name of the Microsoft Office Communicator, which requests an internal SIP server. The next two names I found on Google are the abbreviated names of the keys registry keys that contain the web proxy, so I assigned these names to my servers and waited for the clients to contact me. And they did it.
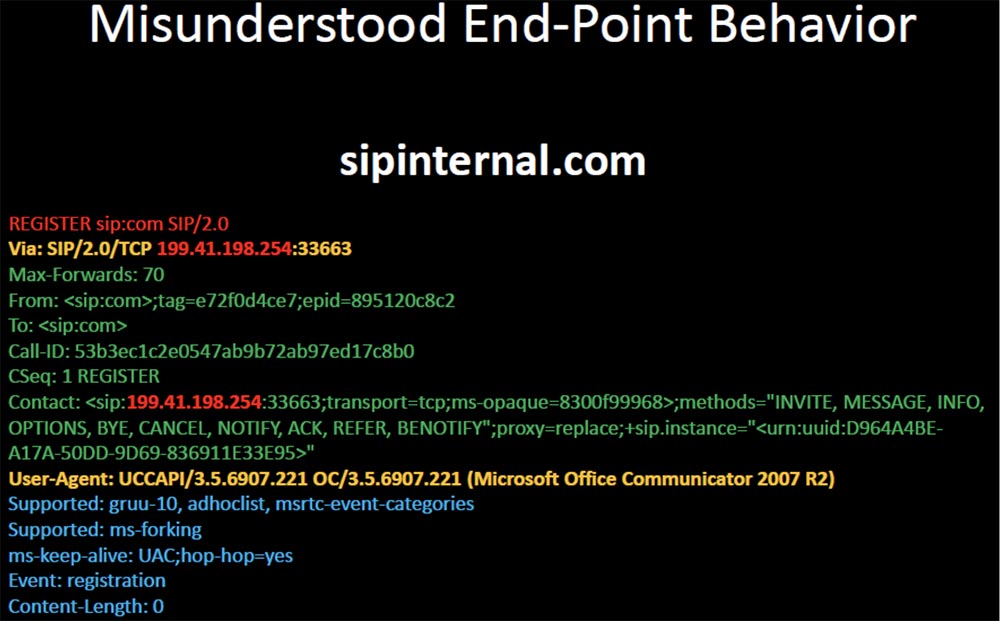
After I registered sipinternal.com, I started receiving requests from clients of the office communicator - on the slide an example of a request to register one of the DHL resources is shown, and as it turned out, there are thousands of random devices in the world who tried to register with me.
I “played a little” with them, and it looked like several attacks that the malicious SIP server carries out against the client’s communicators. This will be my next story about proxy-phoenix.com

There were several end users from IBM and HP who started asking me to become their proxy server, and now they have a client in Phoenix, which “pushes” proxy-phoenix as a short name to its users. I thought it was interesting. But set-proxy.com was even more interesting.
The first requests I received were attempts by thousands of Windows clients to download the proxy installation package file. I found out that the source IP address was registered to Arthur Andersen, an unsuccessful accounting firm that went bankrupt with Enron.
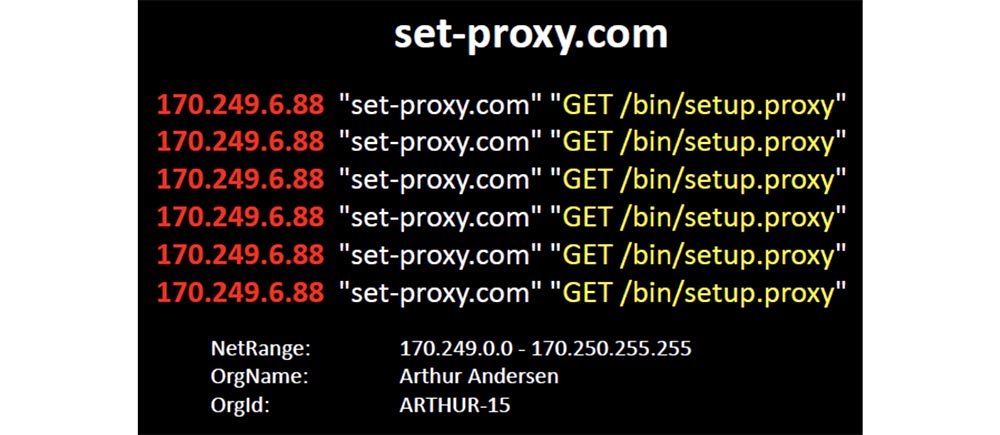
Accenture has separated from its consulting group, which makes more sense in the next part. From her it is clear that their policy of using mobile devices has failed (laughter in the hall).
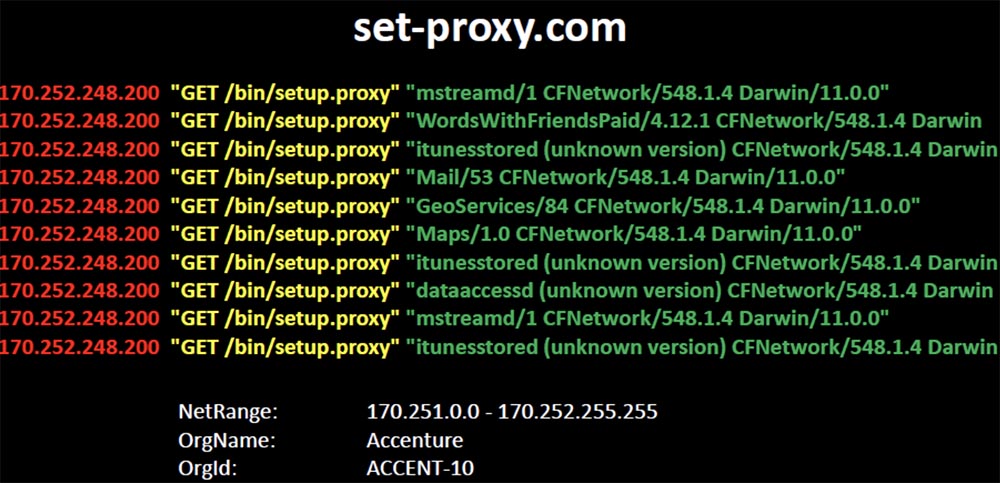
They promote a configuration that refers to the location of the proxy package by abbreviated domain name. And thousands of iPhones and iPads responded to this short name and began to ask me to provide them with these file packages. Even the fact that this configuration does not allow customers to get the requested one did not make them think, and they went directly to the Internet, bypassing the proxy to request these files from me.
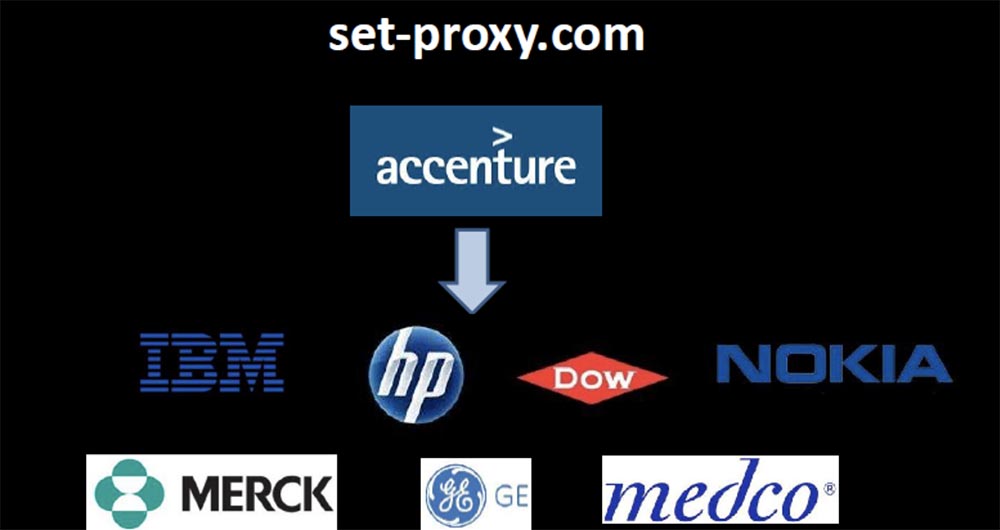
Looking closer, I noticed that I was receiving inquiries not only from Accenture, but also from their clients connected to the network of this company. Thus, Accenture through the wrong DNS jeopardized not only its local network, but also the networks of all clients connected to it, allowing it to hack all the devices there. I was directly contacted by devices owned by employees of IBM, HP, Dow, Nokia, GE, Merck, Medco. All of them asked me to be their proxy, and I’ll tell you that I expected the best from Accenture.
From this you can learn such lessons. Watch your DNS traffic, because if now Windows behaves one way, it does not mean that it will behave the same after the second Tuesday of the month (laughter in the hall).
Do not trust expectations based on the fact that things will go as they should, watch the traffic and learn to understand how normal DNS traffic should look in your network. You need to clearly understand what normal traffic looks like before you make any changes to the settings, so that you can compare them with something.

The inscription on the slide: “You are not the owner of this domain. He is me. "
I have demonstrated some pretty unique ways in which “flipping” a bit in the DNS can be dangerous. However, beat-squatting is not a huge threat, so it is more interesting to perform tricks with unexpected DNS behavior caused by the combination of Microsoft patches with the original configuration, which makes it completely unintelligible.
At the same time, one of the worst things that companies do in relation to DNS is 100% harming themselves through carelessness.
I have seen companies that repeatedly, over several years, sometimes accidentally, and sometimes deliberately, create all the conditions for an attacker to be able to take over every part of their infrastructure.
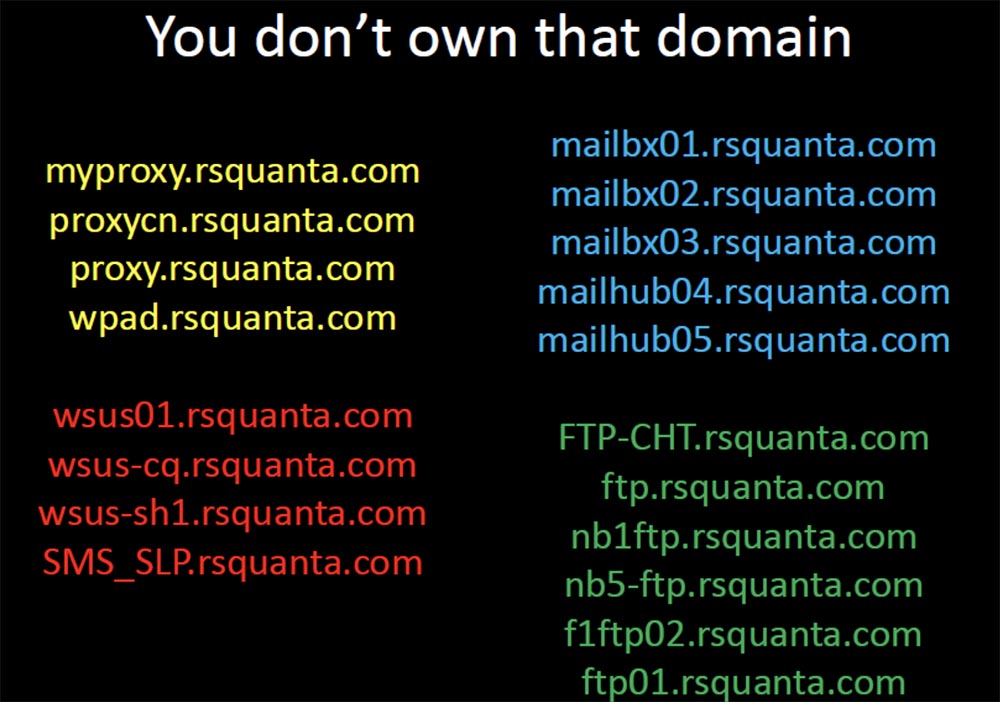
The problem is that companies actually use those domains that are not owned by. These domains, placed in the suffix search string, “push” all their clients to the inevitable exit to the external Internet when they need technical support.
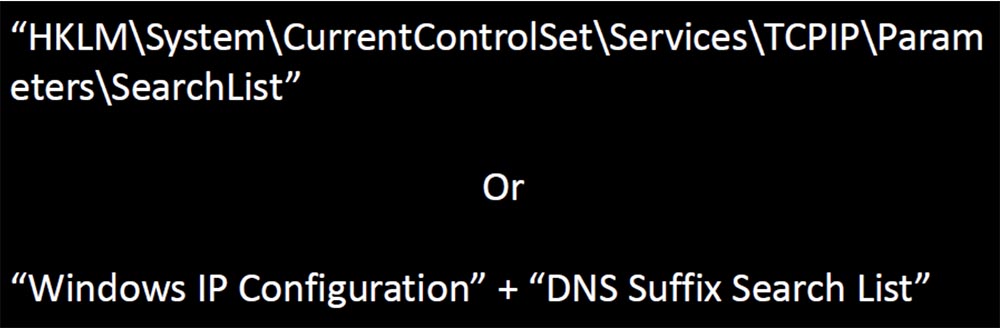
I decided to study how many companies are forced to act in this way, and it was no difficulty for me. I started by asking for help from a Google search engine to find registry key names that store the search list for the Windows IP configuration output and the DNS suffix search list.
Technical support forums encourage users to post configuration information about the workstation to help with troubleshooting.
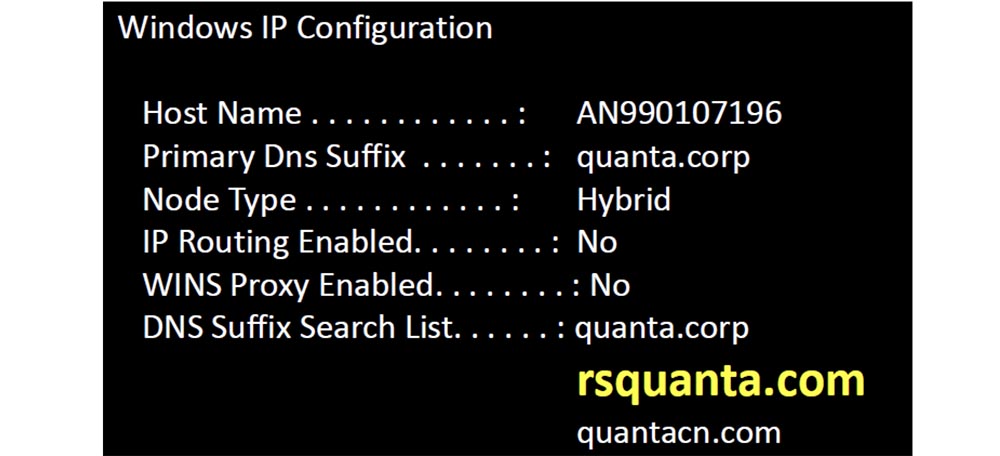
I went through Google and created a unique list of domains, and then began to register them. When looking at the IP configuration, I came across the DNS suffix rsquanta and made it the basis for my domain registration list.

After registering the domains with the distorted names shown on the next slide, I began to receive thousands of requests from mobile devices, which did not even know which company they applied to. But I found out. It turned out that the suffix of the domain name rsquanta.com belongs to a large Taiwanese computer hardware company Quanta Computer, which employs 60 thousand people.
They designed and manufactured the OLPC Kids' One Hundred Dollar Laptop and collaborate with Facebook, designing and building their new servers based on their devices. I received requests for autodiscovery of proxies, SMS servers, mail servers, file transfer servers. There were dozens of ways in which I could safely take over these devices in Thailand and enter exploits to steal credentials or intercept transferred files. After they asked me to help them find the right resources, an attack in the “man in the middle” way would look trivial.
But when I identified the sources of the requests I received on my dummy servers, it really struck me. I found that regular traffic was coming from client networks, which indicated the existence of Quanta Computer devices in Cisco, Apple, 3m, and Dell.

Therefore, they had to have field staff whose duty was to help implement the Quanta equipment. And these are just some of the company's customers who have Quanta Computer employees in the field — I found out about them, because they all asked me to give access to the company's assets.

Their hardware was firmly established in the equipment of well-known companies and was related to confidential intellectual property. Thus, there was a lot of passive information that I could extract from their traffic. I owned a list of names of each device in their network, I saw the traffic of companies hidden from the public, which indicated the presence of a new contract. If traffic suddenly stopped, I could assume that they had lost the contract, and could track where they would go next, where these employees travel and where they are.
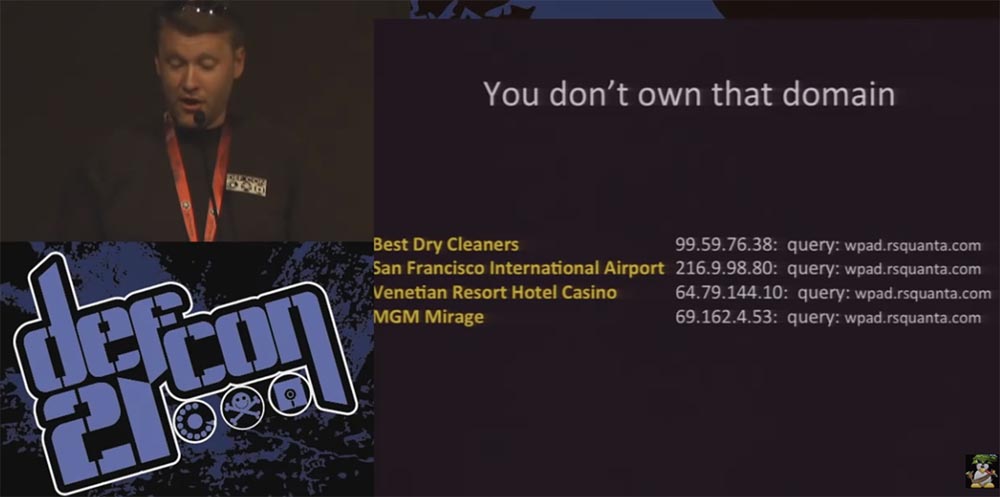
For example, I see a dry-cleaner with Wi-Fi opened near the company's office, because hundreds of devices send me requests from time to time from there. I even see that in this city there are people for Black Hat and DefCon, later we will talk about it (laughter in the hall).
So this kind of mistake is pretty serious. To avoid it, please check your DNS configuration. Use the Internet to find out the details of your internal configuration using resources such as Pastebin and Bleeping Computer.
Watch your DNS logs and make sure that your customers and customers of your partners and manufacturers fulfill queries exactly as you expect from them. If you are tracking logs, then it is easy to determine the frequently requested domains for each device, each corporate asset.
A couple of years ago, I started buying expired domains that were previously used as C & C servers. (laughter in the hall). It was a lot of fun, so at first I wanted to understand how much more infection there was, then find out what kind of devices were still infected and where they were.
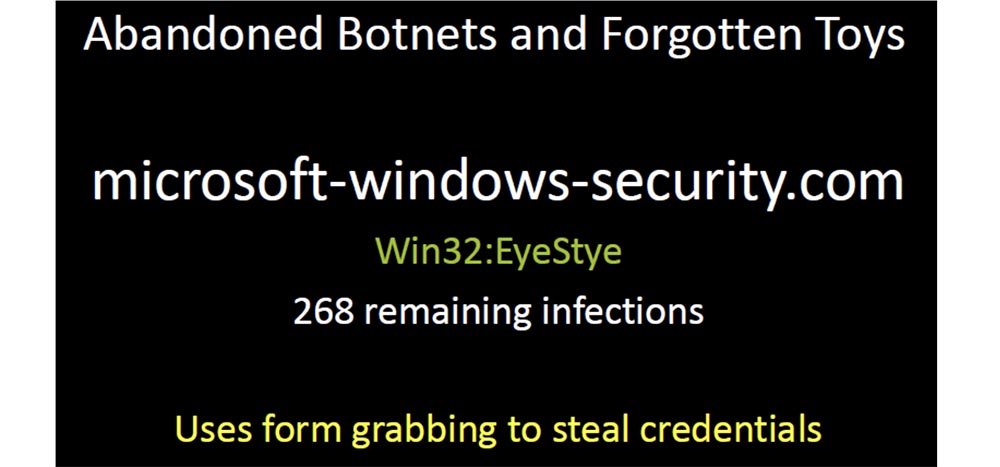
The search for domains from the “black list” was not difficult, so I had a choice of thousands of domains at a price of 99 cents, and I bought a few of them. The next slide shows the first domain I bought - microsoft-windows-security.com. It was infected with a Win32: EyeStye virus, a bot trojan, a keyboard interceptor that was used to steal confidential information. He intercepted the entered data, and then sent them to this domain in the form of unencrypted messages. I didn’t do anything to him, I just sent him a 404 error every time he wanted to contact me, but he still tried to send me the stolen data.
This bot reports its unique identifier, the name of the process that controls the intercepted function, the data it contains and the payload in the form of a username and password.
Many such bots continue to blindly deliver their payload to their domain. I have registered dozens of such domains, covering thousands of infected devices. These representatives of the botnet network were simply abandoned by their previous owners, who did not want to make efforts to close them, but simply left them on the network until the domain usage expired. So I spent my first 6 dollars on these domains infected with viruses (applause in the hall).
I had 23,000 devices sending reports to my server, and all these domains were taken from published blacklists. Why did so many companies allow their customers to contact domains that have long been considered malicious?
We can all improve our work by controlling one of the simplest mechanisms, so, just digging through the logs of my domains, I came across one that looked really unusual.
One of the clients of 82 thousand devices of my network requested it regularly, and when I began to understand, I found out that this domain overdue for half a year was not in one “black list” and there was not a single mention of it in Google. It looked too suspicious, so I bought it, and it was immediately overwhelmed by customers. It was the usual “grabber” that sent its payload in an unencrypted form and controlled 10,000 infected devices around the world. Some of them were located in areas with the highest security regime, and I discovered that one of the infected devices belonged to the wastewater treatment plant of the city of Phoenix.
I contacted someone there from this company and said that I could identify the virus if a sample of the infected file was sent to me. As soon as they sent me a sample, I uploaded it to Virustotal, and found that none of the 42 anti-virus scanners could identify this virus. This malware was 2 years old, and it seemed strange to me that it was not designated as a threat in any antivirus. But what was even stranger, this is why it was abandoned? Completely invisible to antiviruses, it really was a very valuable viral infection. And here is one of the ironic examples - it was the QA engineer of Symantec, I hope it is not here.
Here I see how it works in the online ticketing system, and in this case it closes the ticket due to the security problem of the product's sim card. I think it is rather sad that a part of malicious software, which is already 2 years old, is still included in the exclusion list of the company's antivirus program by an engineer who works on eliminating dangerous defects and ensuring the safety of the company's products.
There are quite a few infected devices that belong to high-ranking government officials and employees, such as the court clerk, the lower house of representatives of the US Congress, money transfer offices, newspapers, and even the cashier of the Credit Union of Federal Employees in Langley! These are definitely the top 99 cents I've ever spent.
It is terrible to think that there are probably millions of infected devices trying to reach Command & Control servers, access to which is no longer allowed. If you use an open or local DNS of almost any major provider, do not allow infected devices to achieve everything they are trying to resolve, and it does not matter whether such a domain exists or not. Because they will fake the answer of what does not exist, and they will give you the default landing page IP address. So the server log, which is the host of this page, contains a myriad of stolen data. Do you think host owners do anything to prevent this?
They are only trying to monetize untargeted traffic with advertising that inadvertently steals your personal data. You expect that if the malware tries to allow you to contact the C & C server that has been disabled, you will not get anywhere, you simply will not be allowed in there.

In reality, it happens as shown on the next slides - open DNS is so kind that it will give you an answer to anything, no matter whether this domain exists or not, and will gladly provide you with the IP address of the malicious site that will steal your data.
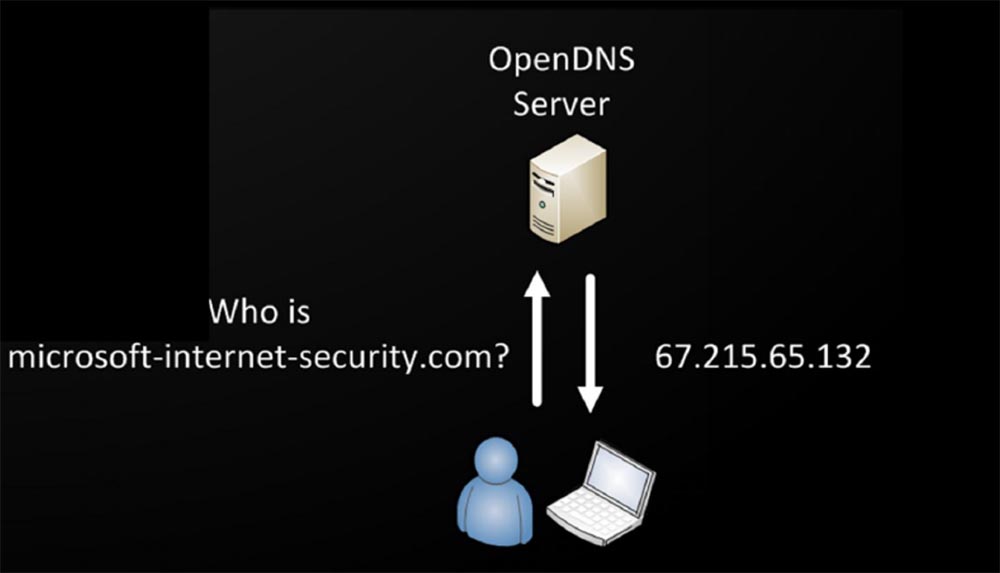
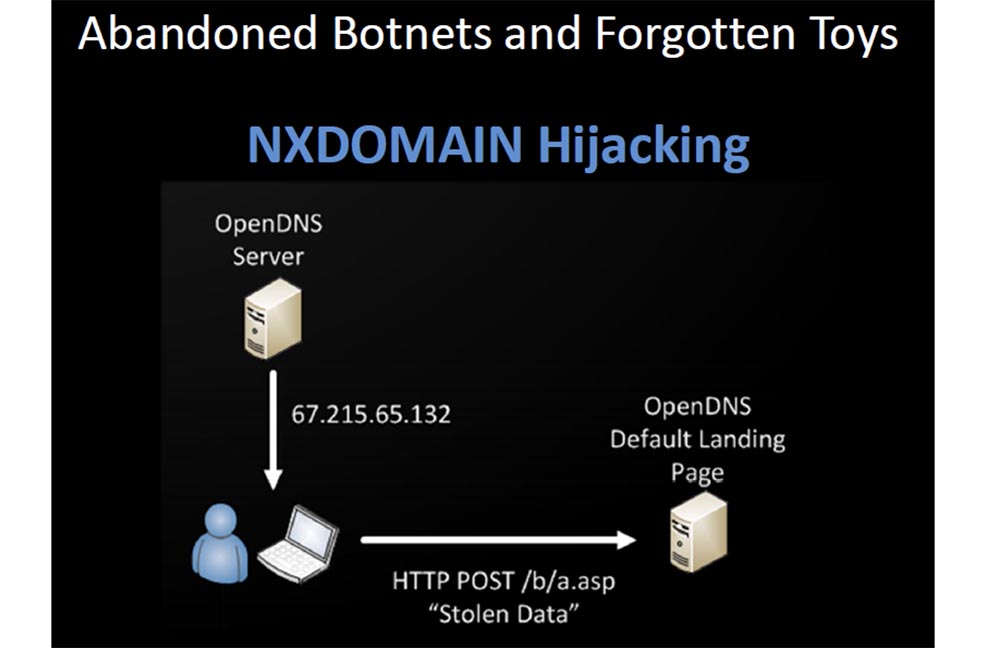
I have registered several domains that are not on any black list now. I found all the samples of malware that went unnoticed by major anti-virus vendors by analyzing the DNS logs. In order to detect such viruses, I act like this:
The network is quite easy to identify things that stand out for their unusual. You can generate a list every day, it is small enough to handle manually. In the next slide, I provide links to some of the resources that you should visit and use if you are going to begin DNS reconnaissance.
The Bro site supports registration of DNS queries and keeps logs of queries. DNS Anomaly Detection – , , , , - .
Passive DNS – Microsoft, «» , «» .pcap .

Response Policy Zones , , . DNS Sinkholes, , .
The last slide provides links to documentation that will help inspire you to begin “digging up” DNS traffic, with which you can find much more than you expected.
Thank you for spending your time on me! You can contact me at any time at this address: bobx@rot26.net.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
It was assumed that the boundaries of the organization’s domain are foo.com and you never want to use www.com . Microsoft changed this DNS behavior because, obviously, not all organizations have two levels for domain names.

')
If your top-level domain is UK, then when you connect to a specific ad.foo.co.uk domain, the default DNS behavior will look like this:

That is, the request will be sent beyond your domain name to www.co.uk. Therefore, a random hotfix was created, a security fix narrowing the organizational boundaries of the domain to 3, in which case the DNS resolution stopped after the second query www.foo.co.uk.

But in our example of a domain name, this security fix, designed to stop unnecessary advertising, broke hundreds of thousands of client companies whose domain name design depended on the original, initial DNS behavior. What are these companies doing? Do they change the design of the infrastructure to fit the new behavior that takes into account this random hotfix? No, they change the behavior back to what it was before.
The next slide shows the decision tree that Microsoft uses before creating the DNS query.
I know that it looks simple (laughter in the audience), and of course you are surprised that someone might understand this in the wrong way.

After that, there were dozens of fixes and updates to this DNS behavior, changing from version to version. But they documented it once, and if one of the branches of this tree changed, it completely broke your way of using DNS, and you could not change the settings to restore the original behavior. You had a problem, because with each new update your settings behave differently. Maybe something will break, or maybe not, that is, something that you do not expect at all may happen.
Thus, companies make changes through register or group policy editing, trying to restore the original behavior of the DNS, but some of them cannot do this properly where the behavior has been changed by another patch package. They are trying to undo the changes in order to restore this lost behavior because they want customers to be able to contact foo.com again.

But in most cases, when they cannot restore two-level devolution, they simply get rid of the original two-level restriction. Thank you, Microsoft, for Windows 7 - now you can change the three default domain levels to 2, but the system will not allow you to reduce them to one.

You might think that now everything is fixed, but what about BYOD devices and mobile devices using the XP configuration? I decided to check how many damaged configurations can still exist there. I have registered several domains, which are usually used only in a corporate environment.
The first domain is the abbreviated name of the Microsoft Office Communicator, which requests an internal SIP server. The next two names I found on Google are the abbreviated names of the keys registry keys that contain the web proxy, so I assigned these names to my servers and waited for the clients to contact me. And they did it.

After I registered sipinternal.com, I started receiving requests from clients of the office communicator - on the slide an example of a request to register one of the DHL resources is shown, and as it turned out, there are thousands of random devices in the world who tried to register with me.

I “played a little” with them, and it looked like several attacks that the malicious SIP server carries out against the client’s communicators. This will be my next story about proxy-phoenix.com

There were several end users from IBM and HP who started asking me to become their proxy server, and now they have a client in Phoenix, which “pushes” proxy-phoenix as a short name to its users. I thought it was interesting. But set-proxy.com was even more interesting.
The first requests I received were attempts by thousands of Windows clients to download the proxy installation package file. I found out that the source IP address was registered to Arthur Andersen, an unsuccessful accounting firm that went bankrupt with Enron.

Accenture has separated from its consulting group, which makes more sense in the next part. From her it is clear that their policy of using mobile devices has failed (laughter in the hall).

They promote a configuration that refers to the location of the proxy package by abbreviated domain name. And thousands of iPhones and iPads responded to this short name and began to ask me to provide them with these file packages. Even the fact that this configuration does not allow customers to get the requested one did not make them think, and they went directly to the Internet, bypassing the proxy to request these files from me.
Looking closer, I noticed that I was receiving inquiries not only from Accenture, but also from their clients connected to the network of this company. Thus, Accenture through the wrong DNS jeopardized not only its local network, but also the networks of all clients connected to it, allowing it to hack all the devices there. I was directly contacted by devices owned by employees of IBM, HP, Dow, Nokia, GE, Merck, Medco. All of them asked me to be their proxy, and I’ll tell you that I expected the best from Accenture.

From this you can learn such lessons. Watch your DNS traffic, because if now Windows behaves one way, it does not mean that it will behave the same after the second Tuesday of the month (laughter in the hall).
Do not trust expectations based on the fact that things will go as they should, watch the traffic and learn to understand how normal DNS traffic should look in your network. You need to clearly understand what normal traffic looks like before you make any changes to the settings, so that you can compare them with something.

The inscription on the slide: “You are not the owner of this domain. He is me. "
I have demonstrated some pretty unique ways in which “flipping” a bit in the DNS can be dangerous. However, beat-squatting is not a huge threat, so it is more interesting to perform tricks with unexpected DNS behavior caused by the combination of Microsoft patches with the original configuration, which makes it completely unintelligible.
At the same time, one of the worst things that companies do in relation to DNS is 100% harming themselves through carelessness.
I have seen companies that repeatedly, over several years, sometimes accidentally, and sometimes deliberately, create all the conditions for an attacker to be able to take over every part of their infrastructure.
The problem is that companies actually use those domains that are not owned by. These domains, placed in the suffix search string, “push” all their clients to the inevitable exit to the external Internet when they need technical support.
I decided to study how many companies are forced to act in this way, and it was no difficulty for me. I started by asking for help from a Google search engine to find registry key names that store the search list for the Windows IP configuration output and the DNS suffix search list.

Technical support forums encourage users to post configuration information about the workstation to help with troubleshooting.

I went through Google and created a unique list of domains, and then began to register them. When looking at the IP configuration, I came across the DNS suffix rsquanta and made it the basis for my domain registration list.

After registering the domains with the distorted names shown on the next slide, I began to receive thousands of requests from mobile devices, which did not even know which company they applied to. But I found out. It turned out that the suffix of the domain name rsquanta.com belongs to a large Taiwanese computer hardware company Quanta Computer, which employs 60 thousand people.

They designed and manufactured the OLPC Kids' One Hundred Dollar Laptop and collaborate with Facebook, designing and building their new servers based on their devices. I received requests for autodiscovery of proxies, SMS servers, mail servers, file transfer servers. There were dozens of ways in which I could safely take over these devices in Thailand and enter exploits to steal credentials or intercept transferred files. After they asked me to help them find the right resources, an attack in the “man in the middle” way would look trivial.
But when I identified the sources of the requests I received on my dummy servers, it really struck me. I found that regular traffic was coming from client networks, which indicated the existence of Quanta Computer devices in Cisco, Apple, 3m, and Dell.

Therefore, they had to have field staff whose duty was to help implement the Quanta equipment. And these are just some of the company's customers who have Quanta Computer employees in the field — I found out about them, because they all asked me to give access to the company's assets.

Their hardware was firmly established in the equipment of well-known companies and was related to confidential intellectual property. Thus, there was a lot of passive information that I could extract from their traffic. I owned a list of names of each device in their network, I saw the traffic of companies hidden from the public, which indicated the presence of a new contract. If traffic suddenly stopped, I could assume that they had lost the contract, and could track where they would go next, where these employees travel and where they are.

For example, I see a dry-cleaner with Wi-Fi opened near the company's office, because hundreds of devices send me requests from time to time from there. I even see that in this city there are people for Black Hat and DefCon, later we will talk about it (laughter in the hall).
So this kind of mistake is pretty serious. To avoid it, please check your DNS configuration. Use the Internet to find out the details of your internal configuration using resources such as Pastebin and Bleeping Computer.
Watch your DNS logs and make sure that your customers and customers of your partners and manufacturers fulfill queries exactly as you expect from them. If you are tracking logs, then it is easy to determine the frequently requested domains for each device, each corporate asset.
A couple of years ago, I started buying expired domains that were previously used as C & C servers. (laughter in the hall). It was a lot of fun, so at first I wanted to understand how much more infection there was, then find out what kind of devices were still infected and where they were.
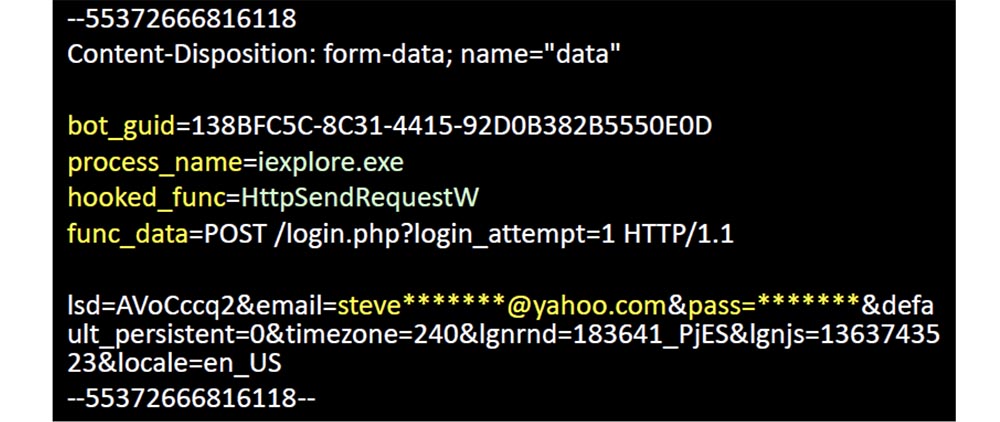
The search for domains from the “black list” was not difficult, so I had a choice of thousands of domains at a price of 99 cents, and I bought a few of them. The next slide shows the first domain I bought - microsoft-windows-security.com. It was infected with a Win32: EyeStye virus, a bot trojan, a keyboard interceptor that was used to steal confidential information. He intercepted the entered data, and then sent them to this domain in the form of unencrypted messages. I didn’t do anything to him, I just sent him a 404 error every time he wanted to contact me, but he still tried to send me the stolen data.

This bot reports its unique identifier, the name of the process that controls the intercepted function, the data it contains and the payload in the form of a username and password.

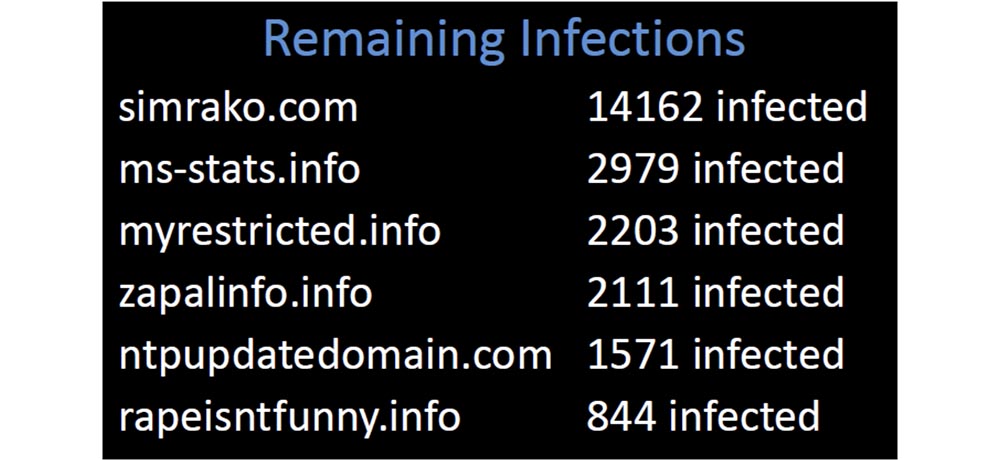
Many such bots continue to blindly deliver their payload to their domain. I have registered dozens of such domains, covering thousands of infected devices. These representatives of the botnet network were simply abandoned by their previous owners, who did not want to make efforts to close them, but simply left them on the network until the domain usage expired. So I spent my first 6 dollars on these domains infected with viruses (applause in the hall).

I had 23,000 devices sending reports to my server, and all these domains were taken from published blacklists. Why did so many companies allow their customers to contact domains that have long been considered malicious?
We can all improve our work by controlling one of the simplest mechanisms, so, just digging through the logs of my domains, I came across one that looked really unusual.

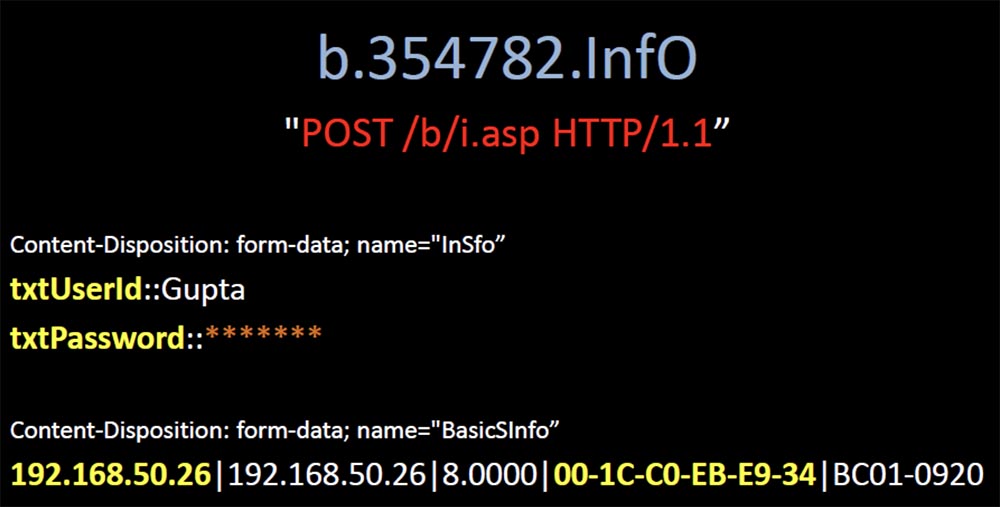
One of the clients of 82 thousand devices of my network requested it regularly, and when I began to understand, I found out that this domain overdue for half a year was not in one “black list” and there was not a single mention of it in Google. It looked too suspicious, so I bought it, and it was immediately overwhelmed by customers. It was the usual “grabber” that sent its payload in an unencrypted form and controlled 10,000 infected devices around the world. Some of them were located in areas with the highest security regime, and I discovered that one of the infected devices belonged to the wastewater treatment plant of the city of Phoenix.
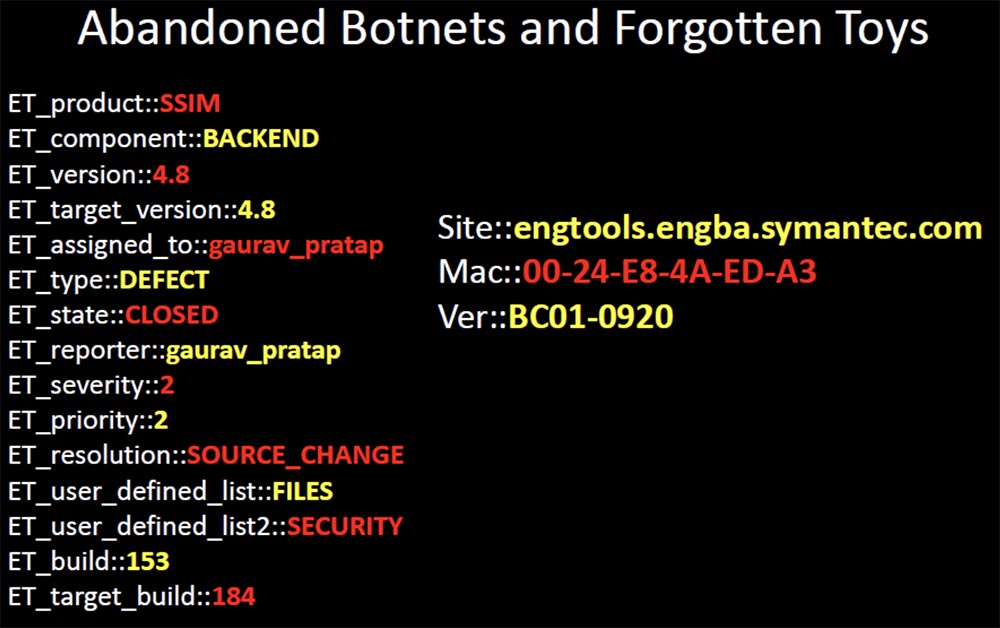
I contacted someone there from this company and said that I could identify the virus if a sample of the infected file was sent to me. As soon as they sent me a sample, I uploaded it to Virustotal, and found that none of the 42 anti-virus scanners could identify this virus. This malware was 2 years old, and it seemed strange to me that it was not designated as a threat in any antivirus. But what was even stranger, this is why it was abandoned? Completely invisible to antiviruses, it really was a very valuable viral infection. And here is one of the ironic examples - it was the QA engineer of Symantec, I hope it is not here.

Here I see how it works in the online ticketing system, and in this case it closes the ticket due to the security problem of the product's sim card. I think it is rather sad that a part of malicious software, which is already 2 years old, is still included in the exclusion list of the company's antivirus program by an engineer who works on eliminating dangerous defects and ensuring the safety of the company's products.
There are quite a few infected devices that belong to high-ranking government officials and employees, such as the court clerk, the lower house of representatives of the US Congress, money transfer offices, newspapers, and even the cashier of the Credit Union of Federal Employees in Langley! These are definitely the top 99 cents I've ever spent.
It is terrible to think that there are probably millions of infected devices trying to reach Command & Control servers, access to which is no longer allowed. If you use an open or local DNS of almost any major provider, do not allow infected devices to achieve everything they are trying to resolve, and it does not matter whether such a domain exists or not. Because they will fake the answer of what does not exist, and they will give you the default landing page IP address. So the server log, which is the host of this page, contains a myriad of stolen data. Do you think host owners do anything to prevent this?
They are only trying to monetize untargeted traffic with advertising that inadvertently steals your personal data. You expect that if the malware tries to allow you to contact the C & C server that has been disabled, you will not get anywhere, you simply will not be allowed in there.

In reality, it happens as shown on the next slides - open DNS is so kind that it will give you an answer to anything, no matter whether this domain exists or not, and will gladly provide you with the IP address of the malicious site that will steal your data.


I have registered several domains that are not on any black list now. I found all the samples of malware that went unnoticed by major anti-virus vendors by analyzing the DNS logs. In order to detect such viruses, I act like this:
- I collect DNS logs that people provide to me in a common database;
- regularly monitor the requested names that first appeared in my environment;
- I find the names requested by only one client;
- I look through the registration dates and set the owners and country of registration of the new domain;
- looking for domains that allow you to use the IP address 127.0.0.1, probably they are created by "nerds".
The network is quite easy to identify things that stand out for their unusual. You can generate a list every day, it is small enough to handle manually. In the next slide, I provide links to some of the resources that you should visit and use if you are going to begin DNS reconnaissance.
The Bro site supports registration of DNS queries and keeps logs of queries. DNS Anomaly Detection – , , , , - .
Passive DNS – Microsoft, «» , «» .pcap .

Response Policy Zones , , . DNS Sinkholes, , .
The last slide provides links to documentation that will help inspire you to begin “digging up” DNS traffic, with which you can find much more than you expected.

Thank you for spending your time on me! You can contact me at any time at this address: bobx@rot26.net.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/430936/
All Articles