Typical NGFW implementation scenarios
Disclaimer
This article provides only examples of typical NGFW deployment scenarios. Do not take the proposed scheme for the finished template. In real life, almost every introduction is unique. There are many pitfalls that you need to pay attention to when planning a network topology. But in general, all the options will “revolve” around several concepts. We will try to discuss them.
Typical network architecture in terms of information security
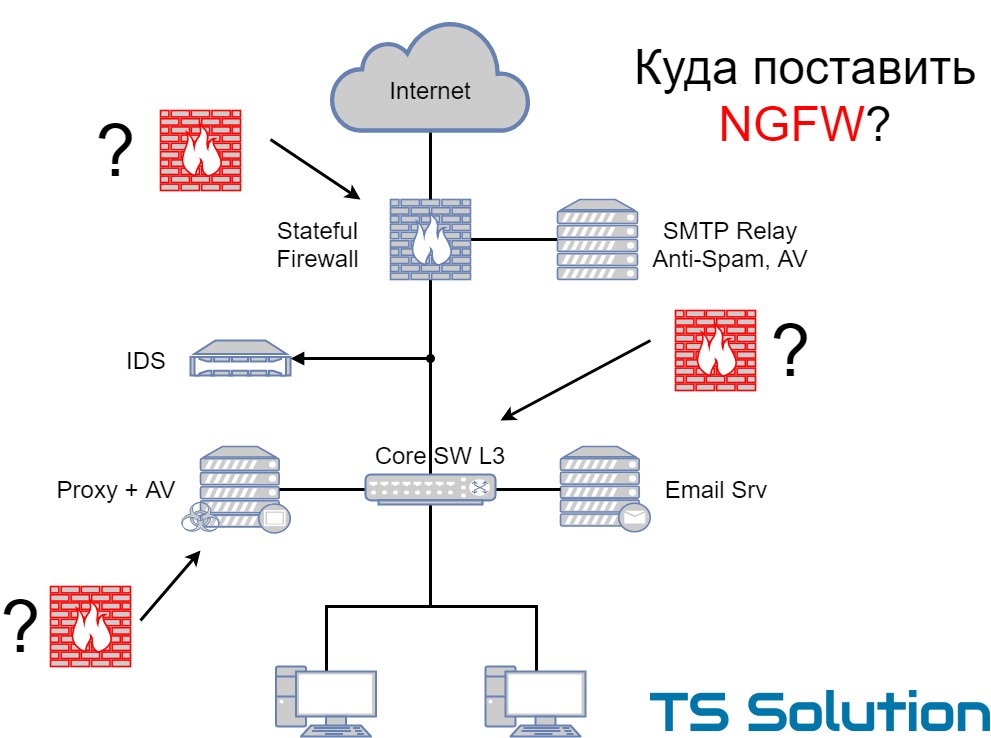
Before describing the options for implementing NGFW, I would like to discuss a few typical scenarios for the use of network protection tools. We will consider the most common means that almost every company has (of course, as simple and superficially as possible, otherwise the whole book will turn out). Most often in practice you can find the three most common options:
')
1) Advanced

Pretty typical layout. On the perimeter of the network, any Stateful Firewall is used, which has at least three segments: Internet, DMZ, local area network. At this ME, Site-to-Site VPN and RA VPN can be organized. In the DMZ are usually public services. In the same place most often there is any Anti-Spam solution with antivirus functionality.
A local switch (L3) is responsible for routing local traffic, on which there are at least two segments: a user segment and a server segment. A proxy server with antivirus functionality and a corporate mail server are located in the server segment. Quite often, the server segment is protected by additional MEs (virtual or “iron”).
As an additional protection measure, IPS can be used, which monitors a copy of the traffic (connected to the SPAN port). In practice, few people “dare” to put IPS in inline mode.
I am sure that many have guessed their network in this scheme.
2) Simplified
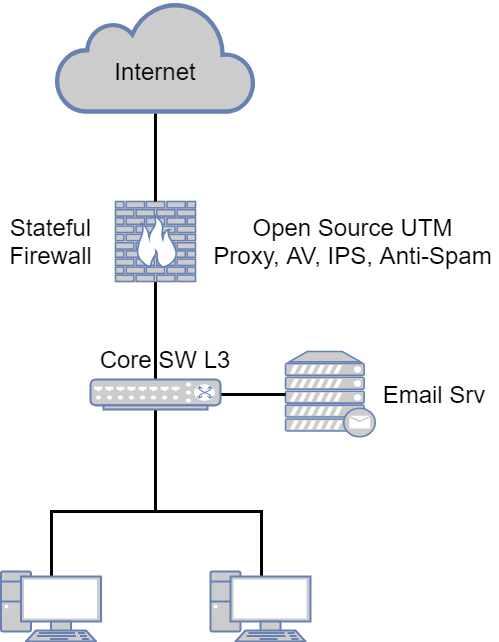
This option is also quite common. Almost all security functionality is deployed as part of a single UTM solution (Firewall, Proxy, AV, Anti-Spam, IPS). The core switch (Core SW L3) is used to route local traffic. It also highlights the server segment with the mail server and other services of the company.
3) SMB

The easiest option. Differs from the previous lack of a kernel switch. Those. traffic between local segments and the Internet is routed through a single UTM device. This option is often found in small companies where there is little traffic.
As I wrote above, this is a very superficial description of three typical scenarios for using the most common network protection tools.
Ngfw
Next Generation Firewall is the next generation firewall. We have repeatedly discussed what it is, how it differs from UTM , which market leaders and what you need to pay attention to when choosing. Initially, the main thing for the sake of which NGFW was implemented - application monitoring and deep packet inspection (the first is actually impossible without the latter). Applications mean not only classic “fat” applications, but also micro-applications of web format. An example is posting, video, chatting in social networks.
However, almost all modern NGFW have much more functions:
- Application control
- URL filtering
- VPN
- IPS
- Anti-Virus
- Anti-spam
Some solutions have additional functionality:
- DLP
- Sandboxing
- Log analyzer and correlation unit
Because of such a large availability of functions and there are questions with the implementation. If you bought a proxy server (ironport for example), then the application scenarios would be much less. The same goes for narrowly targeted anti-spam solutions. But what to do with such “combines” like modern NGFW? Where to put and how to use? Let's look at a few sample scenarios and discuss how best to implement. All subsequent conclusions are very subjective and based only on personal experience and in accordance with certain "best practice".
1) NGFW as a perimeter device
The easiest and most correct implementation option. NGFW for this and thought - to stand on the edge of the network.
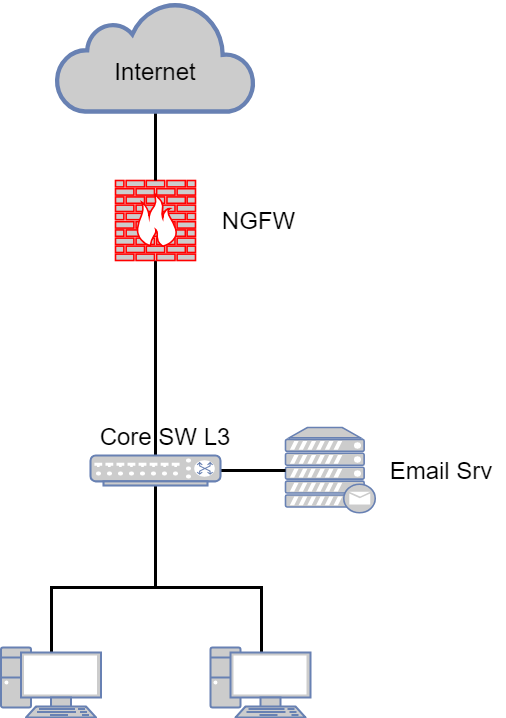
What are the benefits:
- There is no need to use a dedicated proxy. Most NGFWs can operate in proxy mode, but all the necessary functionality works in the “default route” mode for all local networks. Configured default gateway and forgot. No explicit proxies in user browsers.
- By default, there is IPS and immediately in inline mode. You can set Detect if you are afraid of problems. No need to think about how to wrap traffic through a dedicated IPS device and how to quickly return traffic back in case of problems.
- Antivirus for web traffic, including for HTTPS traffic (with SSL inspection enabled).
- Antivirus for email traffic. Check links and attachments.
- Anti-spam functionality.
- The ability to quickly implement the functional "sandbox" (sandbox). Almost all modern NGFW have the ability to activate the sandbox (cloud or local).
- Integrated reporting for all information security incidents.
As you can see, the scheme is greatly simplified. Removed several traditional means of network protection. On the one hand, this is a plus (administration is simplified), on the other hand, minus (a single point of failure). We will not discuss now what is better. We are simply discussing the concept.
What to look for when choosing NGFW, which will stand on the perimeter of the network:
- Most attention here should be paid to the mail check functionality (of course, if you are going to remove the current anti-spam solution). For full-fledged mail handling, NGFW must have an MTA (mail transfer agent) on board. In fact, in this mode, NGFW replaces SMTP-relay, which allows for deep checking of mail traffic. Including verification of investments in the sandbox. If there is no MTA, then at least SMTP relay should be left.
- Even if the MTA is present in NGFW, carefully read the mail filtering features. One of the most important criteria is the availability of quarantine (or ways to organize it).
- HTTPS inspection should of course be supported. Without this function, one name remains from NGFW.
- The number of applications that NGFW can distinguish. Be sure to check if your chosen solution determines the applications you need (including web applications).
Possible limitations or problems
Often a router is used as an edge device and not a ME. In this case, the current scheme can use functionality that is not present in its pure form on the NGFW (various WAN technologies, routing protocols, etc.). This should be taken into account and carefully planned before implementation. It may be logical to leave the router and use it in parallel (for example, for organizing a WAN network). Example:
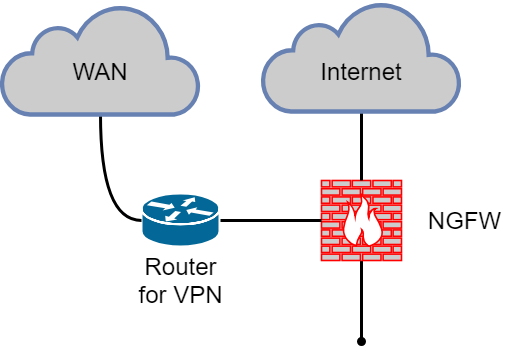
Summary
As I wrote above, the “NGFW on the perimeter of the network” option is ideal when you get the most out of it. But do not forget that NGFW is not a router. The usual functions (bgp, gre, ip sla, etc.) may be absent or present in a very truncated functional.
2) NGFW as a proxy server
Oddly enough, but it is also a fairly common option. Although NGFW and was not developed as a proxy. Typical scheme:

The advantages of this option:
- The speed of implementation. Replaced the old proxy and done.
- No need to change the current scheme or routing.
This is perhaps the pluses end. Although the benefits are voiced very often become decisive for many companies.
What to look for when choosing NGFW, which will stand as a proxy:
- The most important point here is the user authentication method (NTLM, Kerberos, Captive Portal, etc.). Be sure to verify that your chosen solution supports the current authorization method or is able to replace it with something adequate.
- Check that you are comfortable with NGFW user built-in reporting (consumed traffic, visited resources, etc.).
- Opportunities for limiting traffic - QoS, restrictions on the speed (shaping) and the volume of downloadable traffic (limiting).
Possible limitations or problems:
- The first thing to remember is that NGFW in proxy mode is almost always a stripped-down feature. You will not be able to use it 100 percent. Especially when it comes to checking email traffic.
- Lower bandwidth. Almost all NGFW solutions in proxy mode demonstrate lower speed per user.
- You will still be forced to use IPS. Since Some of your traffic may go to the Internet past the proxy.
Summary
Personal advice - if there is an opportunity to avoid “NGFW as proxy”, then avoid. In practice, undocumented features suddenly begin to "vylazit". And the biggest disadvantage is the impossibility of a full check of mail (technically, of course, this can be done, but it will be a “crutch”).
3) NGFW as core
A common option for small networks. Routing of all traffic (Internet, local, server) is “hung up” on NGFW. L3 switch is absent, or simply not used for routing.
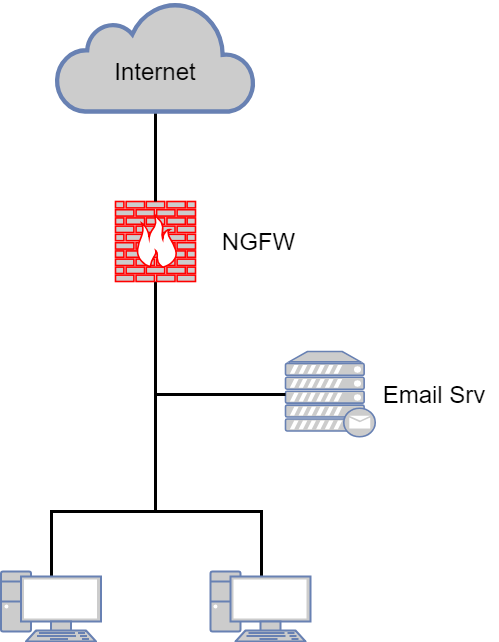
The advantages of this option:
- Ease of administration. All access-lists in one place.
- Deployment speed As a rule, NGFW is placed in this way in topologies where, before that, the ME was the core of the network.
- All the advantages of the option “NGFW on the perimeter of the network”.
What to look for when choosing NGFW in kernel mode
Almost everything is the same as for “NGFW on the perimeter of the network”. But in this case it is worth paying special attention to the presence of the MTA function. In such a small network, it is desirable to do without an additional device in the form of an SMTP relay. It is better if this functionality is present in your NGFW.
Possible limitations or problems:
- Perhaps the main problem is a single point of failure. When selecting a device, do not forget to consider your local traffic so that the selected NGFW model will cope with the load.
- The network is less flexible in terms of change. Fewer routing devices — less traffic control.
Summary
Perhaps this is an ideal option for small companies. Of course, if you accept the risk of a single point of failure.
4) NGFW in bridge mode
A less popular option, but still occurs more often than we would like. In this case, the current network logic does not change at all, the traffic at the second level passes through NGFW, which operates in bridge mode:

Leaving a third-party IPS in this case does not make sense (especially on monitoring traffic). NGFW will perfectly cope with its function. This option is used most often in more advanced infrastructures, where topology changes are for some reason impossible or highly undesirable.
The advantages of this option:
- The speed of implementation. You do not need to change the network logic; you need to overwrite the cable or “wrap” the VLAN.
- Less hops - easier network logic.
This is probably all.
What to look for when choosing NGFW in “bridge” mode:
- On the restrictions of the “bridge” mode! Read them carefully.
- It is desirable to have bypass modules so that traffic goes through the device, even if it is turned off.
Possible limitations or problems
And here are a lot of pitfalls. I have not yet met a single NGFW solution that would adequately work in bridge mode. Maybe I had no luck. But I share in this article only my experience. In addition to the official (documented) limitations in the functionality, “unofficial” in the form of bugs and heaps of problems always appear. Of course, it all depends on the functions you use in bridge mode. If you configure only the Firewall, then there will be almost no problems. However, if you include things like IPS, Application Control, HTTPS inspection, or even Sandboxing, then be prepared for surprises.
Summary
As with the proxy, it is advisable to avoid the bridge mode. If this is not possible, then it is highly desirable to test this mode on your infrastructure. Then make a decision.
fault tolerance
I could not touch this point. Almost all NGFW solutions support two clustering modes:
- High Availability . One node of the cluster is active and routes traffic, the second node is passive and is in hot standby, ready to become active in case of problems with the first.
- Load Sharing . Both nodes are active and traffic is “divided” between them.
Many people rely heavily on Load Sharing mode when planning and implementing NGFW.
- If the traffic is divided between devices, then the load on them will be two times less, and therefore the device can be laid weaker and cheaper?
- Not!
As numerous tests show, it is impossible to achieve adequate balancing of traffic. And the maximum that you will give Load Sharing - reducing the load on the device by 15 percent, not more. At the same time, this mode almost always has some limitations that are not found in High Availability. Be sure to read them. And when choosing a device, always count that one “piece of hardware” should cope with all traffic.
Summary
Use High Availability mode.
Virtual NGFW or “piece of hardware”
Another very frequent question when planning NGFW. Choose a virtual solution or appliance. There is no definite answer. It all depends on your current infrastructure, budget and possibilities for changing the logic of the network. But we still have general recommendations for different implementation options:
- NGFW on the perimeter of the network. Here is certainly the best option - appliance. This is logical, because the network perimeter must have a physical distinction. If you still want a virtual solution, it is VERY desirable that NGFW is deployed on a dedicated server that has a physical separation from the local network. In fact, you get the same appliance, just instead of the “hardware” of the vendor, you use your server with a hypervisor. You also need to carefully approach the settings of the hypervisor itself so that it is not accessed from the external network.
- NGFW as proxy. There is no difference what to choose. In my opinion a virtual solution would be more preferable and convenient option.
- NGFW as the core of the network. Basic requirements as in the first paragraph. Since NGFW is directly connected to the Internet, then the solution must be physically separated from the company's servers - an appliance or a virtual machine on a dedicated server. Since NGFW in this case also performs the role of the kernel, then you need to understand how many physical ports you need and which ports (1g, 10g, optics). It also greatly influences the choice.
- NGFW in bridge mode. For this option, a hardware device is strictly recommended, since preferably bypass modules (traffic will pass even when the device is turned off).
Let's take a look at the pros and cons of a virtual solution.
Advantages of a virtual solution:
- The main advantages of a virtual solution are the ease of management (backup, snapshot) and deployment speed.
- It is also very often cheaper and more scalable. Typically, licensing is based on the number of cores used. If necessary, you can simply purchase a few cores.
Cons of the virtual solution:
- No hardware warranty. If the server fails, you have to deal with it yourself.
- If you are safe, then you have to interact with the IT department. Oddly enough, in many companies this is a very big problem.
For appliance, the opposite is true. In addition, out of the box, more physical ports are available.
Conclusion
I hope this article did not work too boring and superficial. I wanted to highlight the main points and not stretch the “lecture” for a few hours of reading. I would be glad if this article is really useful to someone. If you have any questions or comments, then I am ready to discuss them in comments or personal messages.
Source: https://habr.com/ru/post/430484/
All Articles