Security Week 47: back to back
 Over the past week, three news about nontrivial security holes have been stolen up at once. This year we already had a release on this topic , then we studied disabling hard drives with
Over the past week, three news about nontrivial security holes have been stolen up at once. This year we already had a release on this topic , then we studied disabling hard drives with Let's start with fingerprints. The fingerprint scanner in smartphones is one of the few features of modern devices that really makes life more convenient. It provides reasonable protection for your phone against unwanted interference and allows you to unlock the device with one touch. With the location of the scanner, smartphone manufacturers have not yet decided: depending on the model, it moves from the front panel to the side panel, moves around the camera, and Apple has completely cut out its scanner in favor of face detection. Chinese researchers from Tencent have discovered a vulnerability in the most recent version of the fingerprint scanner, which is located directly below the display.
Representatives of Xuanwu Lab, one of the research divisions of Tencent, argue that absolutely all phones equipped with a fingerprint scanner under the display are vulnerable ( news ). These are the latest models, next year this technology is expected on almost most of the flagships. Huawei Mate 20 Pro and Porsche Design Mate RS were among the vulnerable smartphones, but this manufacturer has already released patches for these devices. Vulnerability in other models (phones with a scanner included in the display is in Vivo, OnePlus and Xiaomi) is not confirmed, but not refuted.
All existing scanners of this type work in conjunction with the display. When the wearer applies a finger to the screen, the screen illuminates the surface and the miniature optical sensors analyze the fingerprint. The problem was precisely the optical method of recognition, which differs from capacitive sensors used in conventional scanners. The optical sensor, as it turned out, was sensitive enough to recognize not a finger, but a fingerprint on the screen surface. As a result, it is easy to hack the phone: we wait for the owner to put a finger on the screen, select the phone, apply a piece of foil to the fingerprint that remains on the display - and then we are authorized. In the case of Huawei, it was easy to solve the problem: the recognition algorithm was updated, apparently, by lowering the sensitivity.
')

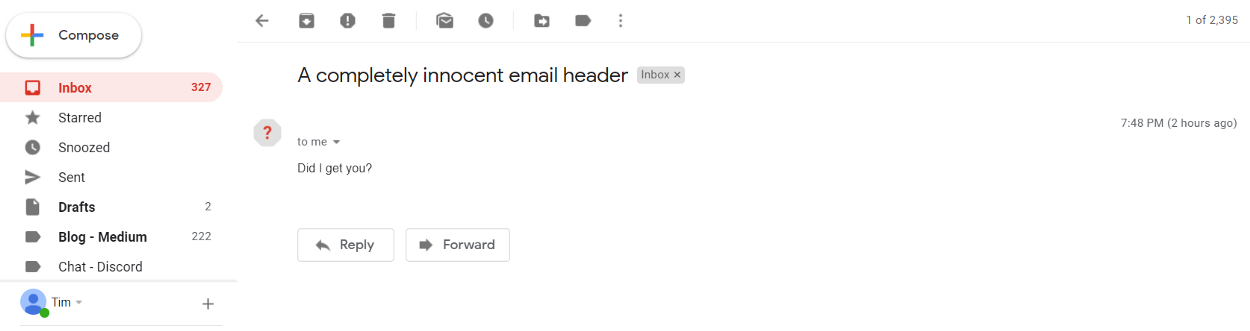
Gmail - spoiler - not hacked. Researcher Tim Cotten discovered last week ( news , a post on a specialist blog ) the method of putting letters in the Sent Items folder. It all started with the fact that Tim found letters in the Sent Items folder that he clearly did not send. As it turned out, if you specify the recipient's e-mail in the sender's information when sending the letter, GMail will automatically put the letter in the appropriate folder.
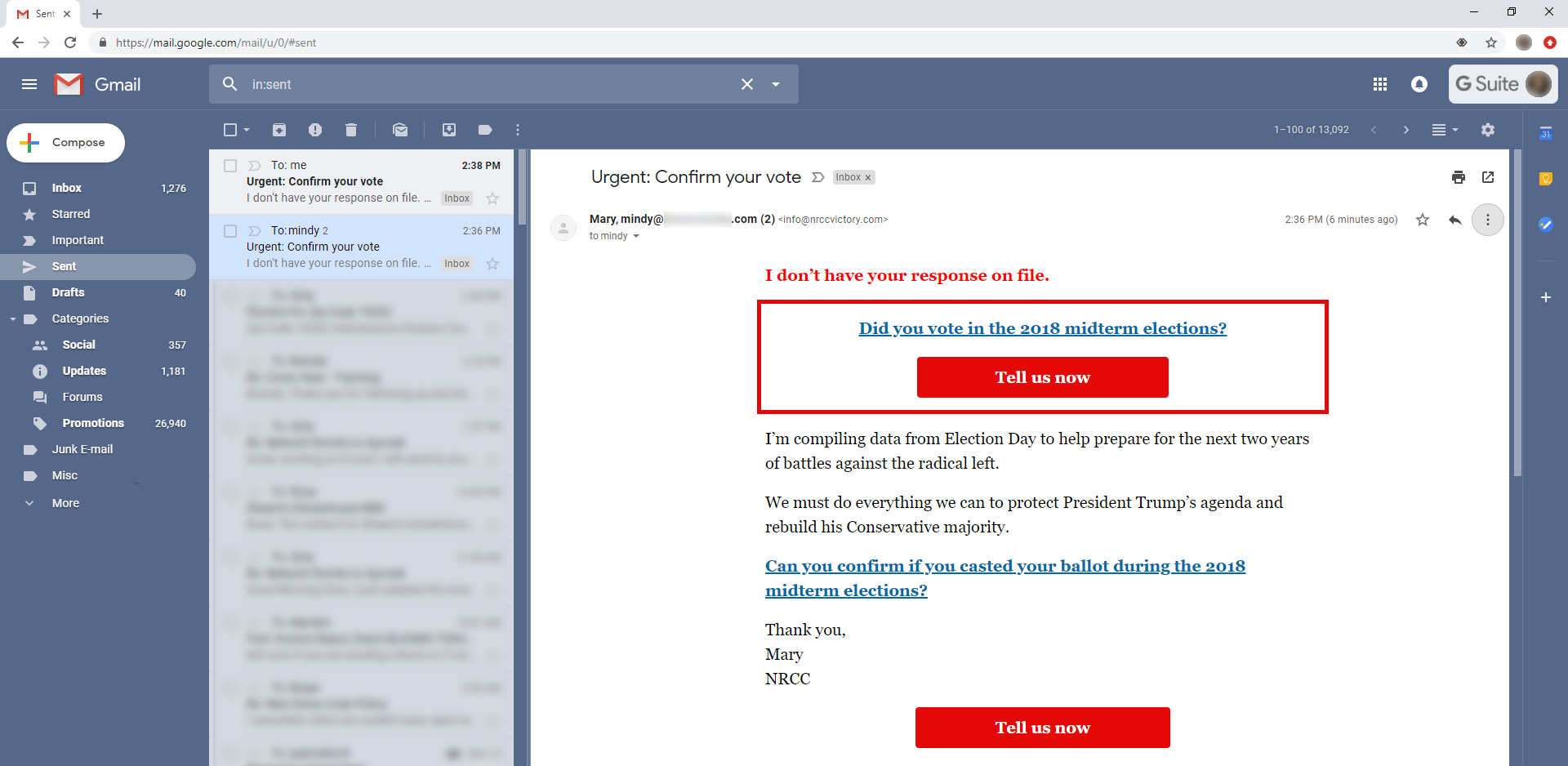
It is noteworthy that GMail itself does not allow sending emails if the sender’s name contains an email address. But when such messages arrive and the address in the sender's name matches the recipient's address, they are in the folder with the sent messages. This may cause at least bewilderment, but such a cunning device can also increase the chances that an inexperienced user will open a malicious link from a letter, trying to understand what he sent. The same researcher later discovered that if you try to insert html-tags into the sender's name, you can make a message appear in the inbox, in which the sender is completely absent.
Finally, SEC Consult Vulnerability Lab found an interesting bug in Skype (we now know who uses it!). Certainly, some versions of the messenger use some very complex algorithms for displaying emoji, so it was not difficult to write a DoS attack on a Skype client. The researchers simply started sending Emoji in many pieces at a time, and when their number in one message reached a hundred, the client began to slow down noticeably.

Eight hundred "kittens of non-destiny" - and the application freezes for a few seconds. If you continue to send Emoji, you can disable the client for a long time. Only some versions of Skype for Business 2016 clients, as well as its predecessor, Microsoft Lync 2013, are vulnerable. Vulnerability was closed this week, but the very fact that such a problem was discovered in the business versions of Skype tells us - what? That emotion at work is not the place! By the way, along with the emotional Skype, Microsoft has closed a much more serious vulnerability in 32-bit Windows 7, previously discovered by Kaspersky Lab experts based on an analysis of a real cyber attack.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/430424/
All Articles