Puzzle "Test My Patience" by Check Point Security Academy
I mentioned the program “Check Point Security Academy” several times on Habré: its essence is that the Check Point firm in the summer announced a contest in the Capture the Flag format, where the participant’s past experience is not important, but only his ability to disentangle cyber- puzzles. According to the results of this competition, the company recruited twenty participants for a three-month professional course on cyber security, and all participants from the very beginning of the course receive a full salary of a specialist in KB, under the obligation to work in the company two years after the end of the course.

In a CTF competition, the flag may even be a picture, for example.
The selection of participants was completed in August, but the competition site will continue to operate until next summer, and I invite those who wish to register and try their hand for the sake of sports interest. The competition consists of 12 puzzles of varying difficulty, rated from 10 to 150 points.
Here I want to make out the “Test My Patience” puzzle from the “Surprise” category. She is of medium difficulty (50 points), and here is her full text:
')
Inside the binary is encrypted; it refuses to run under the debugger; if you try to connect a debugger to it that is running, it ends instantly. Probably, experts from Check Point wrapped their puzzle in a crypto-packer, borrowed from some Malvari.
How can we guess the number, thought of by a watchmaker?
There are two ways. The first one can conditionally be called “the power is, the mind is not necessary”: if the program cannot be debugged live, then we will debug the dead!
Launch the 32-bit Task Manager (\ Windows \ SysWOW64 \ taskmgr.exe), right-click on the mysterious process, and select Create dump file. (The 64-bit Task Manager for 32-bit processes creates a wow64cpu emulator dump, which is more difficult to work with.)
We look at the dump and see that at least the lines in it are already decoded:

But the lines with neither the number nor the flag is not visible yet.
Go to the main caliber gun: WinDbg (X86) -> Open Crash Dump ...
Where in memory is the line that we want to see printed - “Good job my friend!”?
The
Let's now find out where this line is printed: maybe some command contains bytes
Luck! - such a command was found:

What is the code around this command? (
We see that, depending on the result of the function
Function code
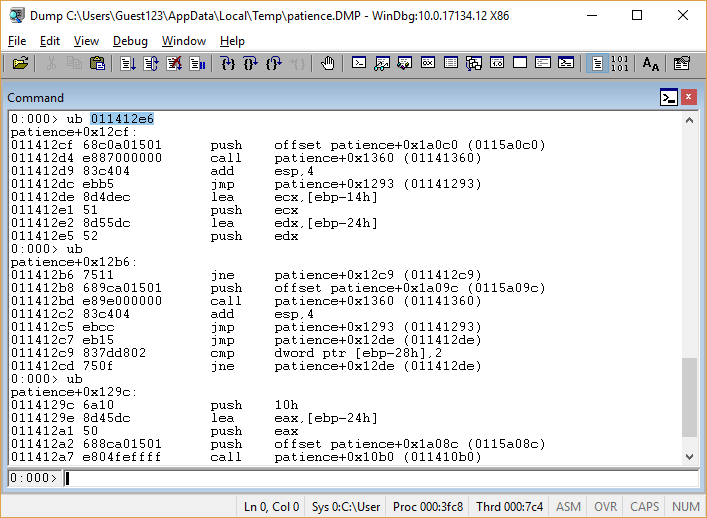
Two pointers are
Is this the function that requests the hidden number? Check by call stack (
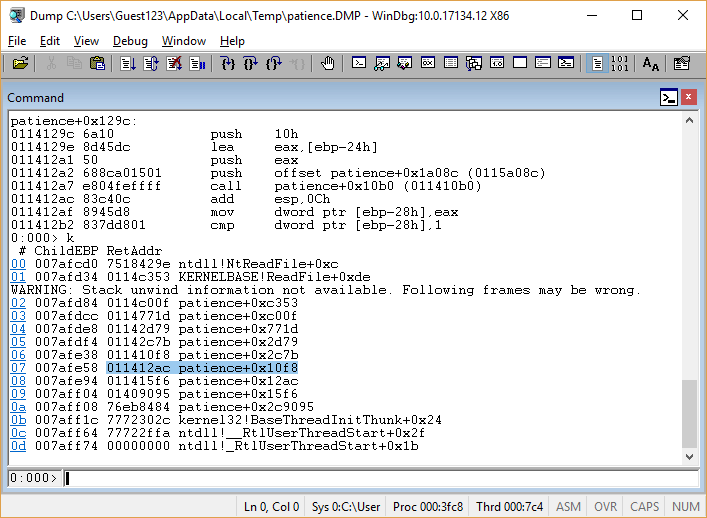
Yes, it is she!
The general scheme of the puzzle is now clear: the user's guess is saved at
All that remains is to pull the hidden number out of the stack frame. We already know his

Well, well ...

Success! You can uncork something tasty.
But three mysterious things were left without explanation:
So, it turns out that there is a second - more intellectual - way of guessing the conceived number. If you just try randomly the numbers 0-9, then it is easy to see that on the nine, the program slightly freezes. If you try the numbers 90-99, then you will notice that at the number 98 the program “freezes” twice as long. (By picking up her offal, we already understand what's the matter: a successful comparison of each pair of characters causes a delay of 0.7s.) To solve the puzzle, even without launching the debugger, it was enough to select each next digit so that the delay before the response increased - either manually with an accurate stopwatch or simple script. Thus, the compilers hinted at the old way of attacking cryptographic algorithms when the time to an error message is measured and analyzed.
But learning how to unzip programs wrapped in unknown crypto-packers is, in my opinion, both more interesting and more valuable :-)
Notice that we didn’t have to figure out how the binary is encrypted, nor how a line appears with a hidden number in the stack (we saw in the dump that it’s not among the string constants) - we managed to get both About a dozen WinDbg commands were enough.

In a CTF competition, the flag may even be a picture, for example.
The selection of participants was completed in August, but the competition site will continue to operate until next summer, and I invite those who wish to register and try their hand for the sake of sports interest. The competition consists of 12 puzzles of varying difficulty, rated from 10 to 150 points.
Here I want to make out the “Test My Patience” puzzle from the “Surprise” category. She is of medium difficulty (50 points), and here is her full text:
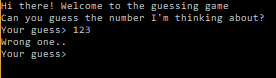
Hi thereThe link is a 32-bit binary for Windows, which some antiviruses swear , but if it is launched, it looks like this:
We found this to be executable on the local watchmaker's computer.
It is a rumored person.
What is your watchmaker?
This note is not malicious in any way.
')

Inside the binary is encrypted; it refuses to run under the debugger; if you try to connect a debugger to it that is running, it ends instantly. Probably, experts from Check Point wrapped their puzzle in a crypto-packer, borrowed from some Malvari.
How can we guess the number, thought of by a watchmaker?
There are two ways. The first one can conditionally be called “the power is, the mind is not necessary”: if the program cannot be debugged live, then we will debug the dead!
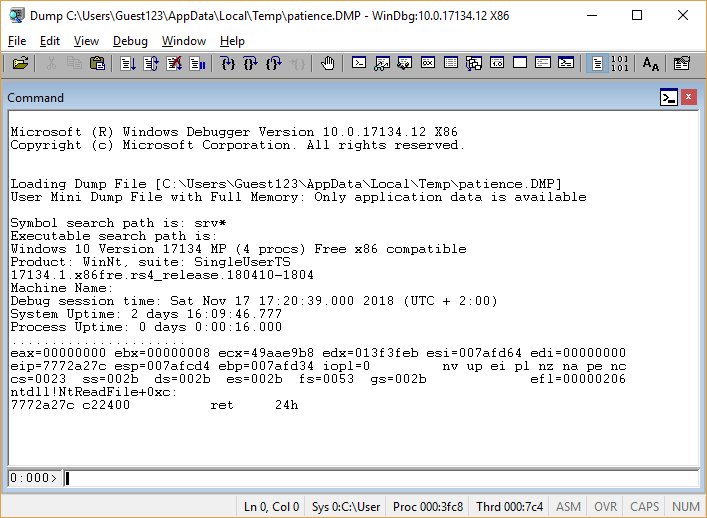
Launch the 32-bit Task Manager (\ Windows \ SysWOW64 \ taskmgr.exe), right-click on the mysterious process, and select Create dump file. (The 64-bit Task Manager for 32-bit processes creates a wow64cpu emulator dump, which is more difficult to work with.)
We look at the dump and see that at least the lines in it are already decoded:

But the lines with neither the number nor the flag is not visible yet.
Go to the main caliber gun: WinDbg (X86) -> Open Crash Dump ...

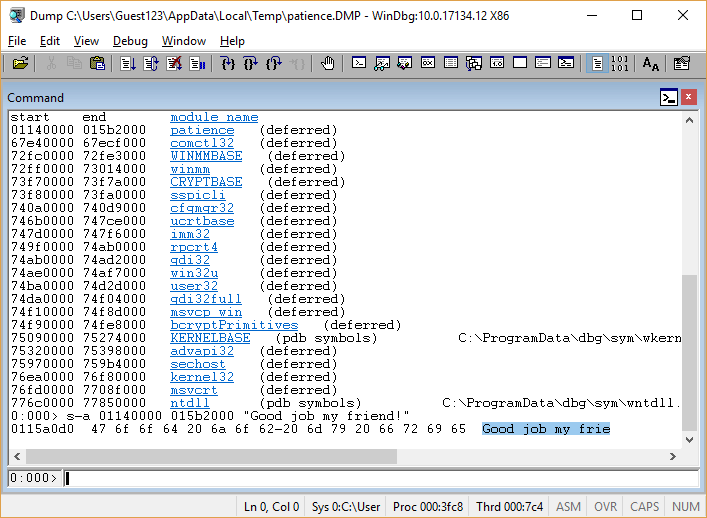
Where in memory is the line that we want to see printed - “Good job my friend!”?
The
lm command allows you to determine that the binary is loaded from 01140000 to 015b2000 ; then sa 01140000 015b2000 "Good job my friend!" finds the required string at 0115a0d0 :
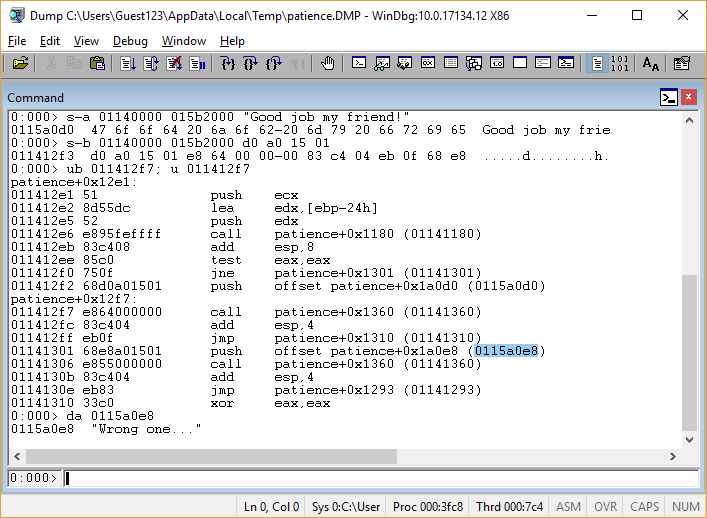
Let's now find out where this line is printed: maybe some command contains bytes
d0 a0 15 01 , corresponding to the address of the desired line? ( sb 01140000 015b2000 d0 a0 15 01 )Luck! - such a command was found:

What is the code around this command? (
ub 011412f7; u 011412f7 )
We see that, depending on the result of the function
01141180 either the message being 01141180 or “Wrong one ...” is printed.Function code
01141180 takes up three screens; it's pretty easy to understand that this is the implementation of strcmp() , inside of which the Sleep(700) call is added. It is not yet clear why there is Sleep() ; but it still does not affect the result of the function, so we better understand what the lines are compared:
Two pointers are
ebp-14h , equal to ebp-14h and ebp-24h ; The second of them was passed to the function 011410b0 .Is this the function that requests the hidden number? Check by call stack (
k ):
Yes, it is she!
The general scheme of the puzzle is now clear: the user's guess is saved at
ebp-24h , the hidden number is at ebp-14h , then they are compared, and either "Good job my friend!" Or "Wrong one ..." is printedAll that remains is to pull the hidden number out of the stack frame. We already know his
ebp from the call stack:
Well, well ...

Success! You can uncork something tasty.
But three mysterious things were left without explanation:
- Why inside the local
strcmp()call theSleep(700)call? - Why, when we entered the hidden number, did the program hang for a dozen seconds before typing “Good job my friend!”?
- What does the watchmaker have to do with this whole puzzle?
So, it turns out that there is a second - more intellectual - way of guessing the conceived number. If you just try randomly the numbers 0-9, then it is easy to see that on the nine, the program slightly freezes. If you try the numbers 90-99, then you will notice that at the number 98 the program “freezes” twice as long. (By picking up her offal, we already understand what's the matter: a successful comparison of each pair of characters causes a delay of 0.7s.) To solve the puzzle, even without launching the debugger, it was enough to select each next digit so that the delay before the response increased - either manually with an accurate stopwatch or simple script. Thus, the compilers hinted at the old way of attacking cryptographic algorithms when the time to an error message is measured and analyzed.
But learning how to unzip programs wrapped in unknown crypto-packers is, in my opinion, both more interesting and more valuable :-)
Notice that we didn’t have to figure out how the binary is encrypted, nor how a line appears with a hidden number in the stack (we saw in the dump that it’s not among the string constants) - we managed to get both About a dozen WinDbg commands were enough.
Source: https://habr.com/ru/post/430210/
All Articles