Capturing private conversations on Skype with Devicelock DLP
In August of this year, Microsoft included in the new release of Skype end-to-end end-to-end encryption, called “Private Conversations”. Encryption works for calls, text messages, as well as files and uses the Signal protocol developed by the non-profit organization Open Whisper Systems.
Of course, in Skype and before the advent of "private conversations" encryption was used, but it was not channel encryption between two users, on keys developed only for their end devices. Prior to the purchase of this messenger by Microsoft, Skype used AES encryption of the channel with 256-bit session keys, but then it was completely abandoned. And now, for normal communication, Skype uses the TLS protocol, which “covers” the channel between the user and the company's cloud.
Virtually all modern data leakage prevention systems (DLP systems) have learned to track (and some even control) the usual transfer of messages and files to Skype through a fairly standard technique - certificate substitution, known as the man-in-the-middle attack (MitM). However, for “private conversations” this trick no longer passes.
We in DeviceLock solved this problem by using simultaneous monitoring of network connections and local agents working directly on the monitored machine. As a result, DeviceLock DLP can fully control “private conversations” in Skype. Fully - it means that the system not only monitors the fact of data transfer and even its composition, but also makes a decision in real time on whether to allow the transfer of files and messages depending on their content and the security policies set for this user.
I will show with a real example how the transfer of messages containing email addresses or TIN files in “private conversation” is prohibited. Create two rules for the Skype protocol, prohibiting email address and TIN in outgoing files and messages.

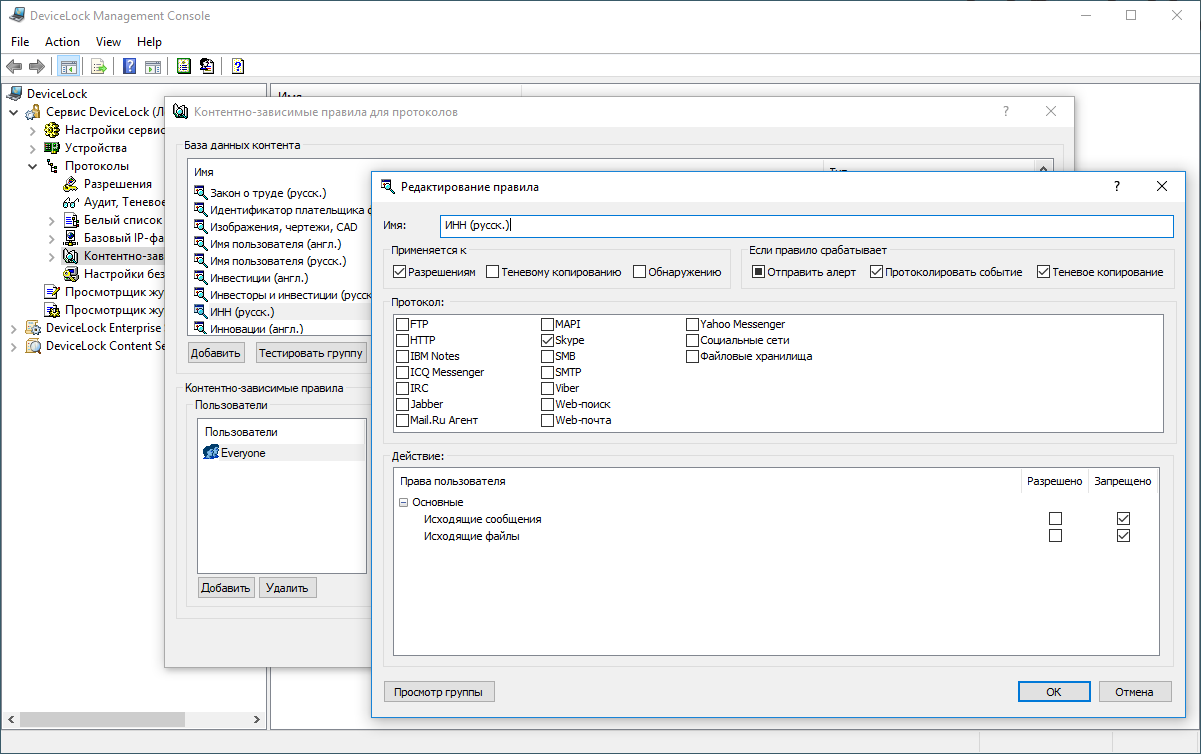
We try to transfer the e-mail address in “private conversation” by message.
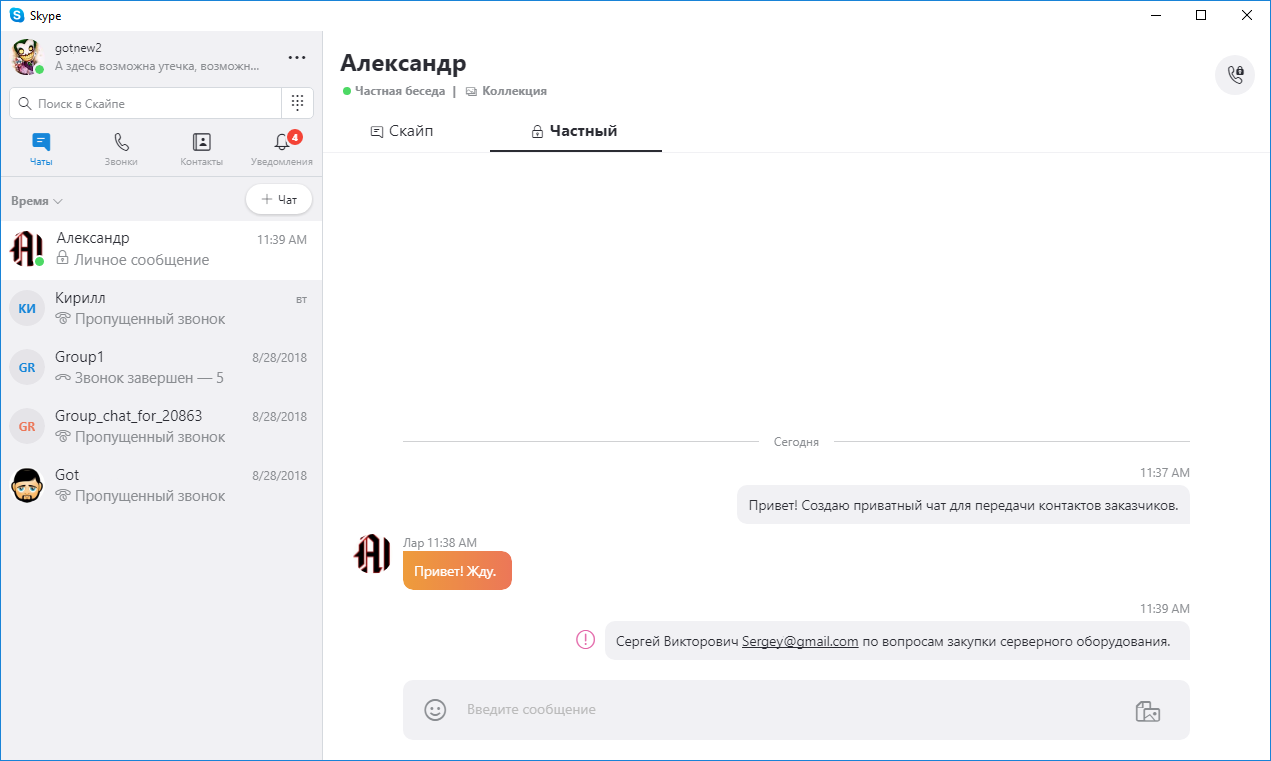
Send an email address in a Skype Private Chat
As you can see, Skype could not send only the message that contains the email address. At the same time, the entire conversation is recorded in the DeviceLock DLP shadow copy log:
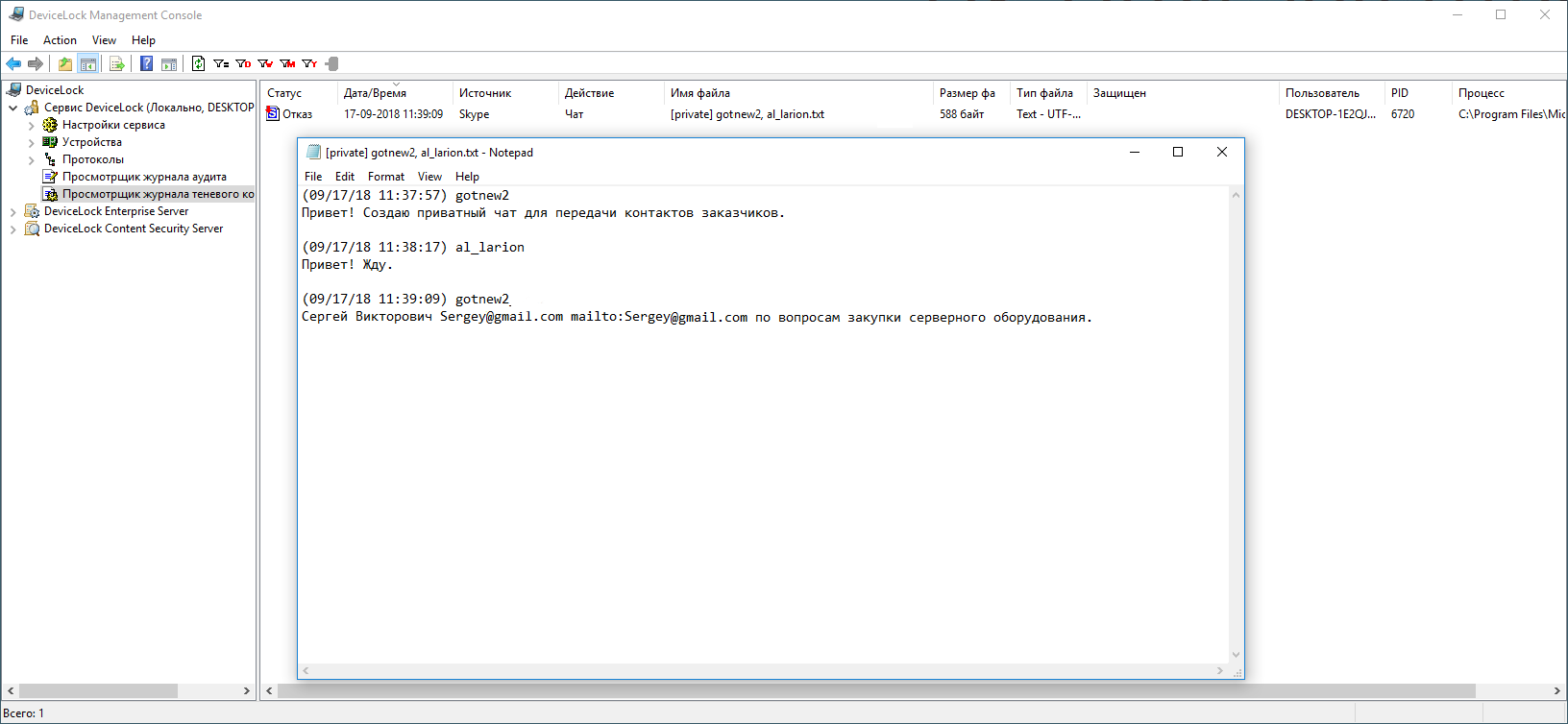
A shadow copy of Skype private messaging messages created by DeviceLock DLP
Now we will try to transfer two files in “private conversation”, one of which contains
INN.
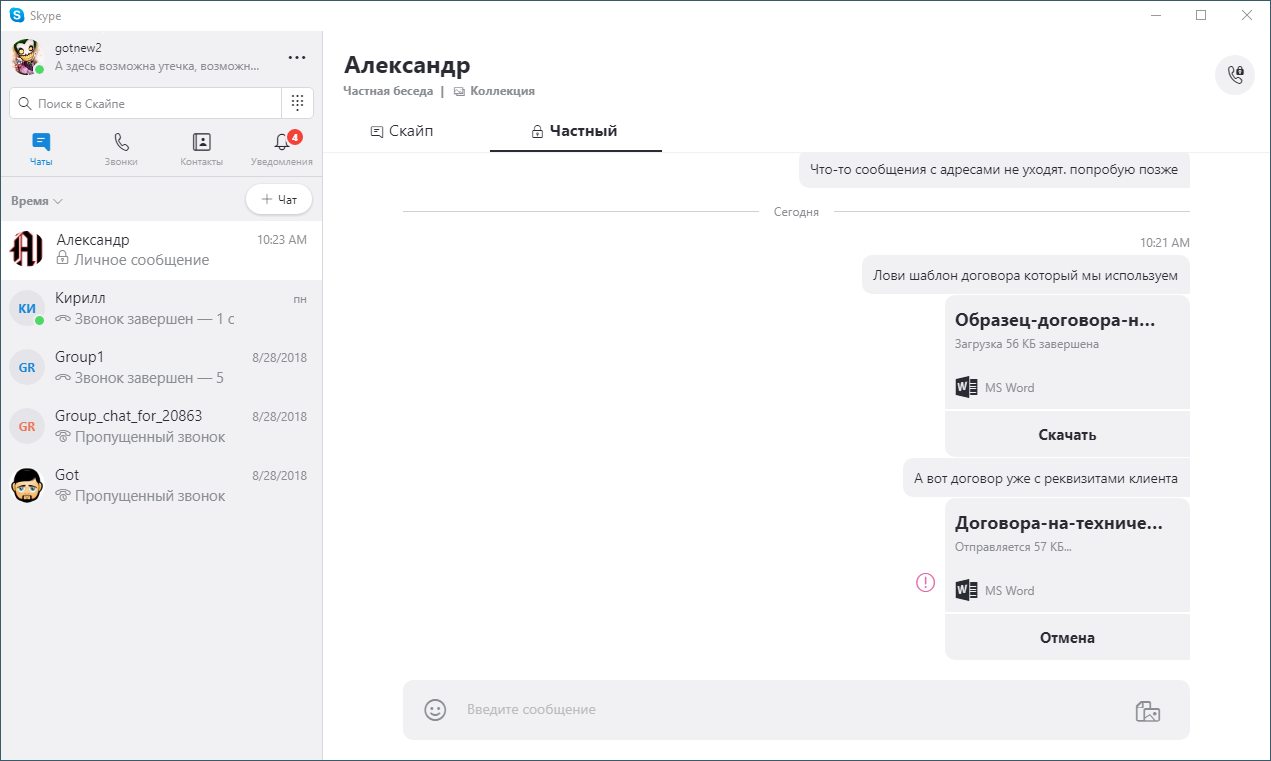
Skype File Transfer
We see that the second file could not be sent, but blocked in the shadow copy log:
A shadow copy of a Skype Private Chat file created by DeviceLock DLP
This is the simplest example of real-time content filtering, demonstrating the ability of DLP to fully control the transfer of data to Skype, even if it uses pass-through encryption.
')
Source: https://habr.com/ru/post/429572/
All Articles