SSD vulnerabilities with hardware encryption allow attackers to easily circumvent defensive measures

Researchers from the University of Radboud (Netherlands) spoke about the vulnerabilities in the protection system of some solid-state drives. They allow an attacker to bypass the disk encryption function and access information on the disk without having to know the access password.
However, the voiced problem concerns only those SSD models that support hardware encryption due to the presence of an embedded chip that is separate from the main module.
Such devices are called - SSD with built-in hardware encryption. They have become very popular over the past few years, because it is believed that encrypting the contents of the disk prevents data access from malicious users. However, there is one way to bypass the protection - cybercriminals can steal access passwords by manipulating the contents of the RAM.
')
But that's not all, the problem is that there is a way to access data without a password at all - you need to use a vulnerability in the SED firmware. Vulnerabilities of this kind affect the specifications of " ATA security " and " TCG Opal ".
The main problem is that in addition to the access passwords that are specified by the owners of the SSD, there is also a master password, which is set at the factory. If you change this password, the vulnerability in question is eliminated, if not, the SSD and its data are open to attackers - of course, those who know exactly what to do.
But there is another snag: the fact is that as a result of the flaws of the manufacturers of such devices, the encryption password chosen by the user and the DEK encryption key are not cryptographically linked. In other words, an attacker can find out the DEK value (the necessary data is hidden inside the SED chip) and then use it to decrypt the data without having to know the user-defined password.
“The lack of a cryptographic bundle is a catastrophe. Due to a flaw, user data is weakly protected. The data stored on the disk can be easily restored and copied, ”says one of the researchers who discovered the problem. Experts published their research results and conclusions in the form of an article ( you can download it here ).
Unfortunately, scientists were able to examine a small number of solid-state drives, their models are indicated below. Nevertheless, all the studied devices were vulnerable.
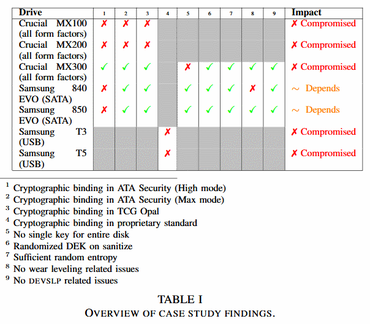
The researchers studied both external and embedded SSD with hardware encryption support. In their opinion, a much wider range of such devices is subject to hacking. The study was completed in April of this year, until now scientists, together with the police of the Netherlands, tried to inform all manufacturers of the devices studied about the problem.
It is reported that companies such as Crucial (Micron) and Samsung have released a firmware update for solid-state drives, thus solving the problem. True, this may not be enough.
The fact is that the researchers began to deepen their work, conducting a study of the security of user data of different systems. Windows users are most at risk because in this OS some services exacerbate the problem. So, the problem can be called Windows BitLocker, a software-based data encryption system on a disk operating in the Windows OS environment.
As soon as BitLocker detects a hardware-encrypted SSD, the service shuts down, and the data is not encrypted using Windows, the OS “relies” on hardware support. So, users who are still working with SSD racial and Samsung and have not updated the firmware of their drives, in fact, keep their data open to all.
The good news is that BitLocker can still be made to work in this case, for this you need to change some of the Group Policy settings. But in this case, you need to format the drive and start working with it from scratch.
But in this case, the protection is double and there are no particular problems. According to the researchers who discovered the problem, its root is in the specifications created by the developers of hardware encryption.
Source: https://habr.com/ru/post/428964/
All Articles