The new Apple T2 chip makes it difficult to audition through the built-in laptop microphone
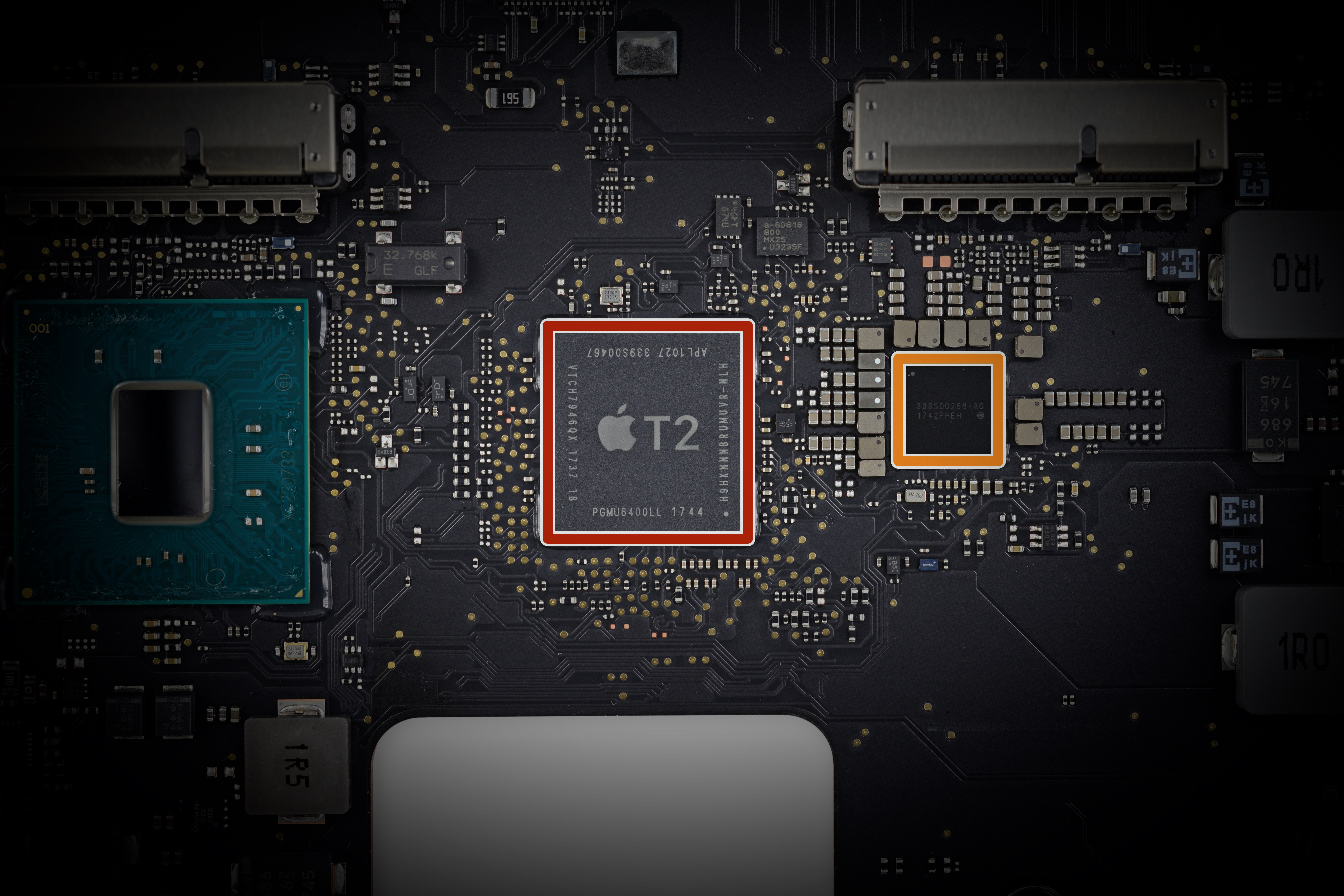
Apple has published documentation on the T2 security chip, which is embedded in the latest branded notebooks, including the MacBook Pro introduced at the beginning of the year and the recently announced MacBook Air.
Until today, little was known about the chip. But now it turns out that this is a very interesting chip. It has a number of security features, including the storage and protection of device encryption keys, fingerprint data, and secure boot functions. In addition, the chip hardware disables the microphone of the built-in camera when closing the lid of the laptop.
"This shutdown is implemented at the hardware level and therefore does not allow any software, even with the privileges of root or kernel in macOS, and even software on the T2 chip, to turn on the microphone when the lid is closed," the published guide says The microphone is given one paragraph.
')

It also adds that the video camera itself is not turned off by the hardware, because “its field of view is completely blocked by the closed lid”.
Apple said the new feature adds an “unprecedented” level of security for the Mac. We are talking about protection against malicious programs, trojans and RAT, which recently became widespread for the operating system macOS (under Windows such programs in large numbers exist a long time ago).
The threat of hackers connecting to webcams on laptops became a reality several years ago, with the proliferation of remote administration tools (RAT). At the same time, the habit has spread among users to stick a laptop webcam with tape or an opaque sticker.
Until a certain point, some users believed that Apple’s webcams on Apple’s laptops were almost impossible to activate without the user's knowledge. But last year, the malware Fruitfly , which dispelled this myth, was discovered.
At first glance, the malware is quite simple and consists of only two files:
~/.client
SHA256: ce07d208a2d89b4e0134f5282d9df580960d5c81412965a6d1a0786b27e7f044
~/Library/LaunchAgents/com.client.client.plist
SHA256: 83b712ec6b0b2d093d75c4553c66b95a3d1a1ca43e01c5e47aae49effce31ee3The .plist file itself simply supports the constant operation of the .client. But the latter is much more interesting: it is a minified and obfuscated Perl script that, among other things, establishes a connection with one of the management servers.
But the most interesting part of the script is at the end of the __DATA__ section. There, a Mach-O binary file was found, a second Perl script and a Java class, which is extracted by the script, written to the / tmp / folder and executed. In the case of the Java class, it starts with pple.awt.UIElement set to true, that is, it does not appear in the Dock.
It is this binary that takes screenshots (from the display) and accesses the webcam. The researchers point out that for this, the malware uses truly “ancient” system calls that were used before OS X appeared.
SGGetChannelDeviceList
SGSetChannelDevice
SGSetChannelDeviceInput
SGInitialize
SGSetDataRef
SGNewChannel
QTNewGWorld
SGSetGWorld
SGSetChannelBounds
SGSetChannelUsage
SGSetDataProc
SGStartRecord
SGGetChannelSampleDescriptionFrom this, they conclude that the authors do not have the experience of modern development for Mac, but use the old documentation, which hints at their foreign origin from a region where Apple equipment is not installed everywhere. In addition, the binary includes the source code of the open library libjpeg in the 1998 version. One way or another, the malware successfully performs its functions and spies on Mac users through the laptop’s built-in webcam.
It is known that espionage through laptop webcams is used not only by curious hackers for entertainment, but also by special services. In the British intelligence service GCHQ for many years acted the department for the development of such trojans in the framework of the Optic Nerve program. Even some well-known techies like Mark Zuckerberg are tapered with a webcam on a laptop.
Source: https://habr.com/ru/post/428792/
All Articles