MIT course "Computer Systems Security". Lecture 15: "Medical software", part 2
Massachusetts Institute of Technology. Lecture course # 6.858. "Security of computer systems". Nikolai Zeldovich, James Mykens. year 2014
Computer Systems Security is a course on the development and implementation of secure computer systems. Lectures cover threat models, attacks that compromise security, and security methods based on the latest scientific work. Topics include operating system (OS) security, capabilities, information flow control, language security, network protocols, hardware protection and security in web applications.
Lecture 1: "Introduction: threat models" Part 1 / Part 2 / Part 3
Lecture 2: "Control of hacker attacks" Part 1 / Part 2 / Part 3
Lecture 3: "Buffer overflow: exploits and protection" Part 1 / Part 2 / Part 3
Lecture 4: "Separation of privileges" Part 1 / Part 2 / Part 3
Lecture 5: "Where Security Errors Come From" Part 1 / Part 2
Lecture 6: "Opportunities" Part 1 / Part 2 / Part 3
Lecture 7: "Sandbox Native Client" Part 1 / Part 2 / Part 3
Lecture 8: "Model of network security" Part 1 / Part 2 / Part 3
Lecture 9: "Web Application Security" Part 1 / Part 2 / Part 3
Lecture 10: "Symbolic execution" Part 1 / Part 2 / Part 3
Lecture 11: "Ur / Web programming language" Part 1 / Part 2 / Part 3
Lecture 12: "Network Security" Part 1 / Part 2 / Part 3
Lecture 13: "Network Protocols" Part 1 / Part 2 / Part 3
Lecture 14: "SSL and HTTPS" Part 1 / Part 2 / Part 3
Lecture 15: "Medical Software" Part 1 / Part 2 / Part 3
By the way, do not hesitate to ask questions, if you want to learn more, dive deep into the causes of any of these incidents. Another interesting thing that I discovered is that the suppliers themselves are a relatively common source of infection, and sometimes they are not even aware of this. In this case, there is a "factory installation of viruses." Therefore, I am going to go to the cases where the supplier itself turned out to be a malware distributor.
')
I talked to the chief security officer of the Veterans Administration, VA. They have about 153 clinics in the United States. Once they had a supplier who intended to update the software of a piece of medical equipment.

At the same time, the antivirus programs literally screamed everywhere this Bob went, because during the software update process he used his own USB drive infected with a virus. He infected the machines by accident, because somehow the malware got on his flash drive.
It is believed that if you are not online, then you are safe. But if you think about it, you will understand that despite the fact that very few people used the Internet 20 years ago, people still suffered from computer viruses. The most common carrier of viral infection in the clinic is a USB drive. I knew two manufacturers, I can not tell you their names, which almost sent to clinics infected with malware medical devices. Fortunately, they realized it before they included this equipment in their product line.
How many of you have done any programming work or dealt with software distribution using the cloud? A few people, great.
The medical community also uses cloud technologies. This gives them more control over the distribution, but is associated with risks that are qualitatively different from the risks of your typical software. If you want to get an update for a text editor, this is one thing, and if you want to get an update for a breathing apparatus, it is a completely different matter.
I noticed that the FDA published a review about the firmware update for this device, saying that the manufacturer posted a link on the site where you can download this update. I wanted to check their PGP digital signatures, but I could not find them anywhere, but at the bottom of the product support page there was a link that says "Click here for software updates." I thought, "This is great, let me try!", Clicked on link, and on the screen immediately jumped out a dialog box with the following text: "Warning: a visit to this site could harm your computer. The website you are about to visit probably contains malicious programs."
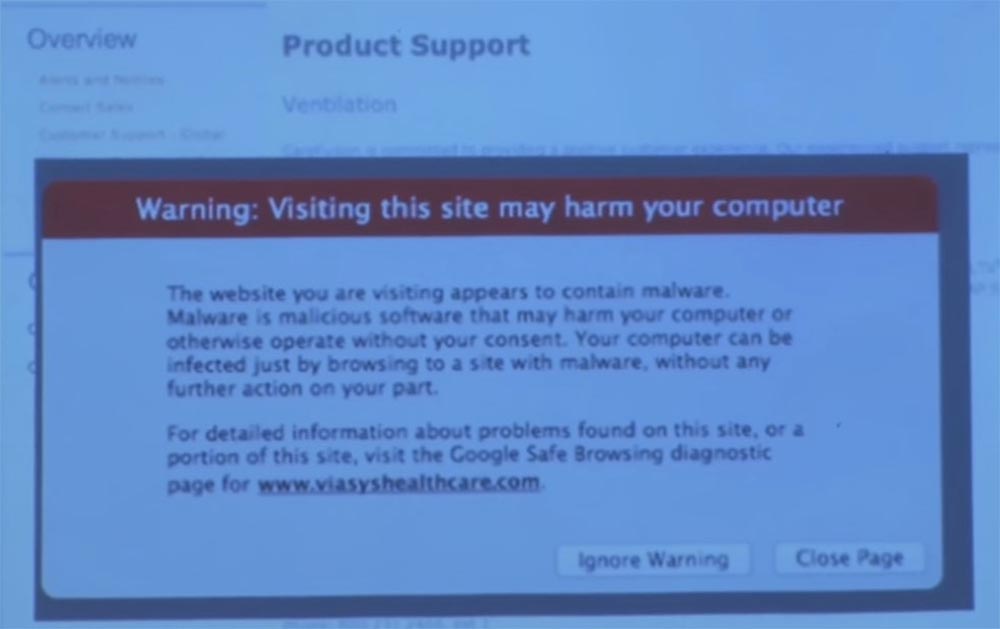
Has anyone seen this window before? Do you know what it is? What's going on here?
Audience: did your anti-virus software probably work?
Professor: almost guessed, but this is not my antivirus, but something similar.
Audience: for sure this is a warning from the Chrome browser!
Professor: yes, it seems that in this case I used Chrome. Google has what's called a safe web browsing service, the Safe Web Browsing service.
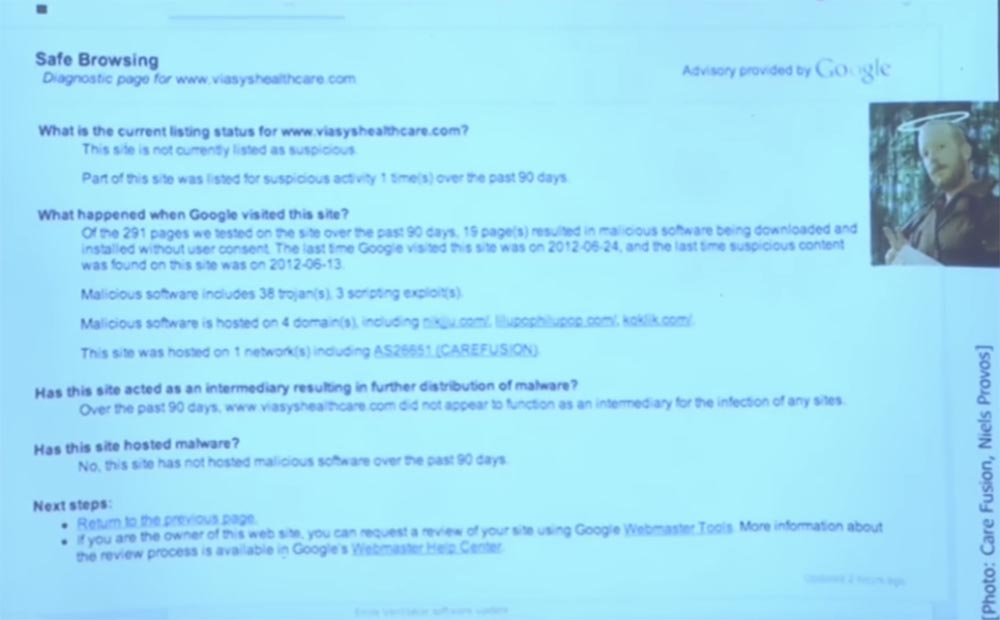
The guy who developed this service is called Nils Provoz. I consider him one of the leading programmers of OpenSSH, he is also from Michigan. He created this service in Google, which simply “roams” on the Internet, downloading random executable files, and then running them. Interestingly, they created a bunch of virtual machines. This is my understanding of Niels technology, I can distort the essence, but I understand that they create a lot of virtual machines, load these executable files on them, run and see if the virtual machine gets infected with a virus.
If this happens, this site is flagged as a malware distributor. Perhaps the spread of viruses is not included in the intentions of the owners of this site, but if the site allows you to download infected software, then it will definitely be included in the list of distributors of malicious programs.
This is what can be called "drive-by downloads", it is a very common way of getting malware on the Internet, which is used by spammers and organized cybercrime.
But in this case, it looks like their website was just hacked, and instead of sending me the firmware update of the respirator, they were going to provide me with malware. In any case, Google’s sample showed that all requests for updating the firmware of this breathing apparatus in the last 90 days sent the user to this site. Suppose that the FDA published this review, you are a biomedical engineer, you work in a clinic, and your job is to ensure the safety and effectiveness of medical devices. You just go and download this program.
What do you think, what button will this engineer click? Leave the page or ignore the warning? I’m sure 99% of engineers would click the ignore button! And there are thousands of such engineers, and they roam around the hospital with malware in their laptops. I hope that viruses do not get into the program of the device for ventilation of the lungs, but only to local computers.
You can do such an interesting thing - make a search in the MAUDE database for the key phrase “computer virus” and look at the result - there will be all the stories presented by clinics and manufacturers of medical equipment. The most interesting thing to read about a device called Compounder, I have one such device in the laboratory. It is quite difficult to get it, it produces liquid medicine. In the upper part of the compounder there are 16 funnels, where you can put the serum, and at the exit to get the desired mixture in the dropper, from which the drug enters the patient in a vein. Many clinics have such devices for the production of medicinal cocktails. So, MAUDE published a report that one of these compounders was infected with a virus.
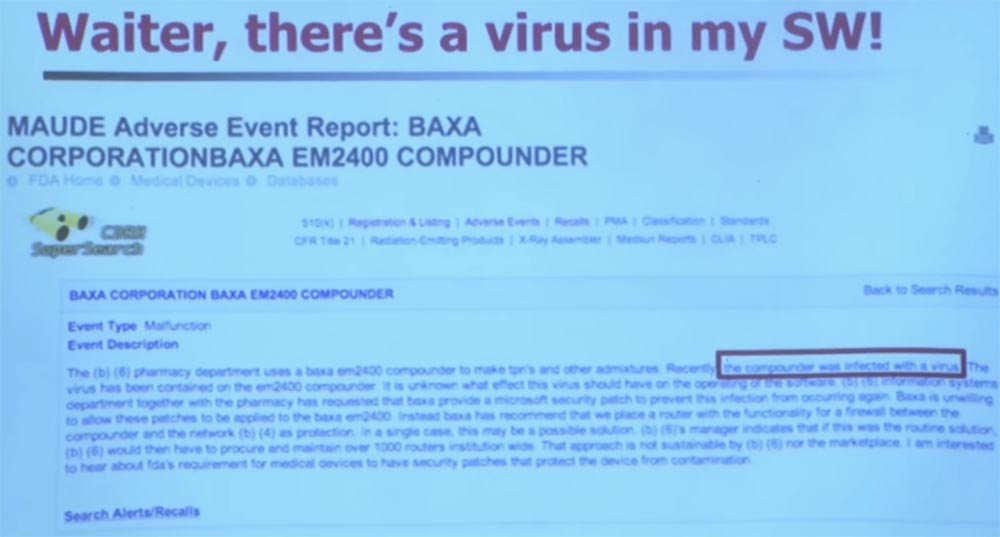
We bought such a compounder and found that it is running Windows XP Embedded. Therefore, it was vulnerable to malware, like any other edition of Windows XP. But I was a little surprised by the reaction of the manufacturer, followed by this message. I thought they changed the record, but their answer was the usual: "Well, yes, we do not regularly install operating system updates and patches." This is exactly what surprised me, and my first reaction was: “What-what? What do you have in mind? Did you not know that Windows XP has not been supported for several years now? What updates are you talking about?
Thus, on the face of a complete lack of understanding of what should be expected from the OS update. Let me clarify the situation. The FDA expects manufacturers to keep software up to date. But many manufacturers claim that they are not able to make updates due to some non-existent FDA rules. So if you ever come across a medical device manufacturer claiming that the FDA rules prohibit them from updating software, just tell him that he is lying.
On this occasion, Professor Freeman created this poster. So, let's go: “Homework prevents me from attending school,” “eHarmony prevents me from dating” and “FDA rules prevent updating software.” And under these statements is stamped: "Bullshit"!

Yes, it is true that the release of a software update takes effort. It takes engineering time. This is not an easy process. There is a huge amount of approvals and approvals of the work done. But this is what you must do if you are involved in the manufacture of medical devices. You are expected to have exactly this kind of behavior if you are engaged in this industry.
Therefore, the question often arises: do we need to worry about it? Are there any problems caused intentionally? How significant are they?
The good news is that I don’t know a single specific case when a targeted hacker attack would have been carried out on medical equipment, and I hope that this will never happen. But I think it would be foolish to assume that bad people do not exist at all.
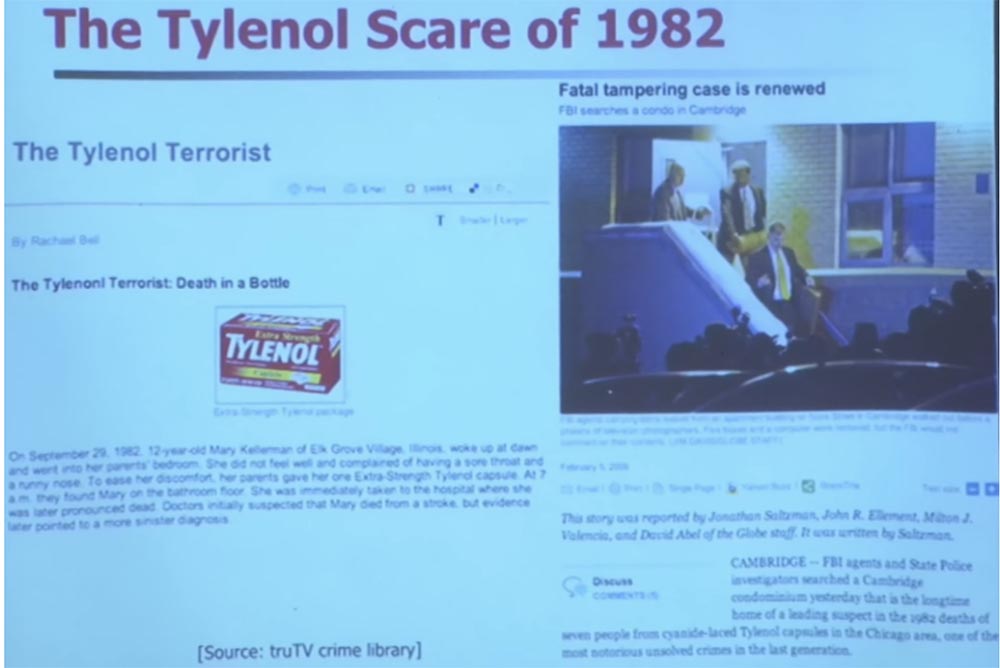
So, if you look back, you can recall the 1982 incident in Chicago, where someone deliberately falsified a genuine “Tylenol” on the shelves of pharmacies, introducing cyanide into it. Several people swallowed these pills and died. A little later, at the funeral, some of the relatives of the deceased took the medicine from the same vial and also died.
For several days, the United States seized "Tylenol" from all shelves with drugs. You could not find a single bottle of this medicine throughout America. A year later, Congress passed a new legislation in the field of pharmaceuticals, requiring the protection of medical products from unauthorized opening of packaging and the physical safety of non-prescription drugs.
This case caused that when you open the medicine bottle, you see a protective metal foil.
So we know that bad people really exist. Cases that we know of are more about ordinary stupidity, but the danger still exists. In the next slide, you see a woman who says that she had one of the most severe attacks that she has ever experienced after someone posted a blinking animation on the site of the epilepsy support group. So in this case, there is malicious intent. It was probably someone who was not aware of the consequences of their actions, because you can seriously harm a patient who is sensitive to such things. But, again, bad people exist.

Thus, one of the problems of a lack of a culture of thinking is that most manufacturers of medical devices think statistically, predicting future device performance based on past data. But as we know, in fact, in the security world, the fact that you do not see any problems at the moment may mean that a whole bunch of them will appear soon.
For example, look at the Mac - two years ago there were practically no viruses capable of infecting these computers. But one night, more than half a million Mac computers were infected with the Flashback virus.

Therefore, one of the problems is overcoming the cultural divide. To move further and implement safety parameters in risk management when using medical devices, it is not necessary to rely on the fact that so far there have been no particular problems with them. I hope that we will be able to prevent reports of such a collapse in the weekly world news, but it can happen anyway.
Now I am trying to draw some kind of analogy. Before we get into ways to solve problems, I want to remind you a story with doctors who have denied the need to wash their hands. However, there was a reason for this. In the 1800s, there was no running water in the hospitals, latex gloves had not yet been invented, so the procedure for washing hands was actually quite complicated.
The same can be said about security, in almost any context. There is no magic dust you can spray and there are no magic latex gloves you can wear to add safety to your devices. Therefore, when you ask a manufacturer or a doctor to, say, keep your device safe, this can be quite a difficult task. I think it will take some time.
If the opponents of washing hands were alive, they would say that all doctors are gentlemen, so their computers are safe. But I'm still optimistic, because most of the manufacturers with whom I speak, now understand that this is a real problem.
They just do not know what to do next. So perhaps in the future they will hire you to help them solve these security problems.
But it all comes down to the fact that it is very difficult to add security in fact; it is very difficult and often very expensive to make changes to ready-made software in some cases. You really have to design security from the very beginning so that everything works out right. Therefore, the FDA expects manufacturers to start doing things right when they are still working with a pen and paper, on design boards, before they make a medical device.
So what do we have with time? 40 minutes, great. I tell faster than I expected. Sorry, if you write, then I will try to speak more slowly.
I want to talk a little about technologies that make medical devices more reliable, so I’ll try to blow your brain, okay? So why do you trust the sensor, let's say, in your smartphone? I see you have a smartphone, do you know which sensors are in it?

Audience: GPS.
Professor: GPS, accelerometer, I heard. Any more thoughts? What else could we find on the phone?
Audience: Compass.
Professor: Compass, light, electromagnetic field, temperature sensors? Technically, the camera has a CCD matrix, so sensors are everywhere. Medical devices also have sensors.
Why do you trust what the sensor says to your processor? If you write software and the sensor says that today is 77 degrees, or 25 degrees Celsius, why do you believe that?
My lab works a lot on sensors. Now I will give you a look at one of these sensors, this is a sensor without batteries, equipped with an MSP430 microcontroller. But there are no batteries, because it has a capacitor with a capacity of 10 microfarads, which collects the energy of radio transmission to power the microprocessor.
He has all these funny little things, such as a 3D accelerometer, temperature sensors, light. But they are quite difficult to turn on. Again, why do you trust the readings of all the components included in this sensor? After all, something turns physical phenomena into these small electrical impulses. There is one important circumstance why you cannot fully trust what this sensor shows.

This is the work of one of my lab technicians, Denis Phu Kun, who rides a board on Lake Michigan. But the rest of the time, he likes to interfere with the work of the sensors. Let us forget for a moment about security - in 2009, one gentleman reported that every time his cell phone rang in the kitchen, an oven was switched on in the stove. You can find this post in The New York Times. It so happened that the resonant frequency of the bell was just perfect for triggering the sensor turning on the kitchen oven.

So there is interference everywhere. This is a constant battle of devices speaking in the same frequency range. But there are technologies that can reduce this intervention. The problem is what happens during the frequency interference of the signal. I want to talk a little bit about analog devices.
Tell me, does the course of lectures 6.003 still exist? Is it really? Fine. I would advise all of you to go through it if you have not done it yet. This is one of the most amazing courses for a computer science person, because you don’t need to dive too deep into electrical circuits.
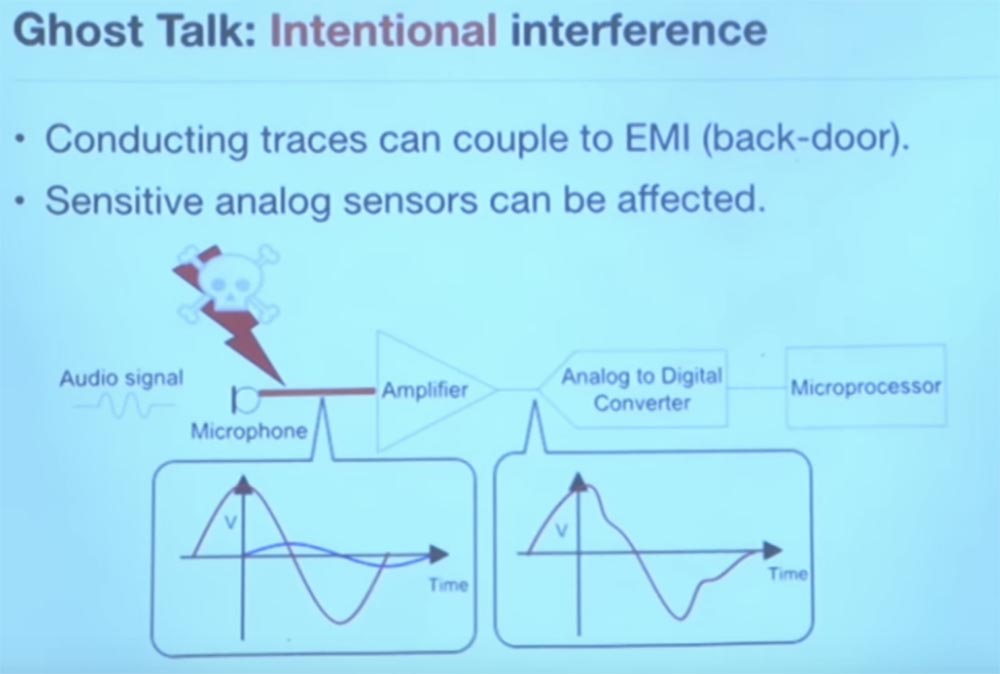
So, it was interesting to me, I tried to understand why I should believe in what the sensor tells me. I began to study the structural scheme. For example, if you have a Bluetooth headset, inside it you will find a microphone, a piece of wire, an amplifier, another wire that goes to a converter that converts an analog signal to digital, there may be some kind of filter, and then everything goes to the microprocessor. But there are also all these things that interfere with the data before they get into your software. However, the software simply believes everything that this wire says. Do you know what exactly interested me?
For example, this piece of wire from the microphone to the amplifier has a length and a resonant frequency. What happens if someone creates artificial electromagnetic interference that is optimized to capture the resonant frequency of this piece of wire? They will go to the amplifier, where they will be amplified, then to this analog-to-digital converter and from there to the microprocessor.
One of the questions was, is it possible in principle? If so, how difficult is it to implement? What kind of energy is needed to do this? And what would be the quality of the signal that reaches the microprocessor?
The main reason why this is possible is that we are talking about intentional rather than random interference in the frequency range.
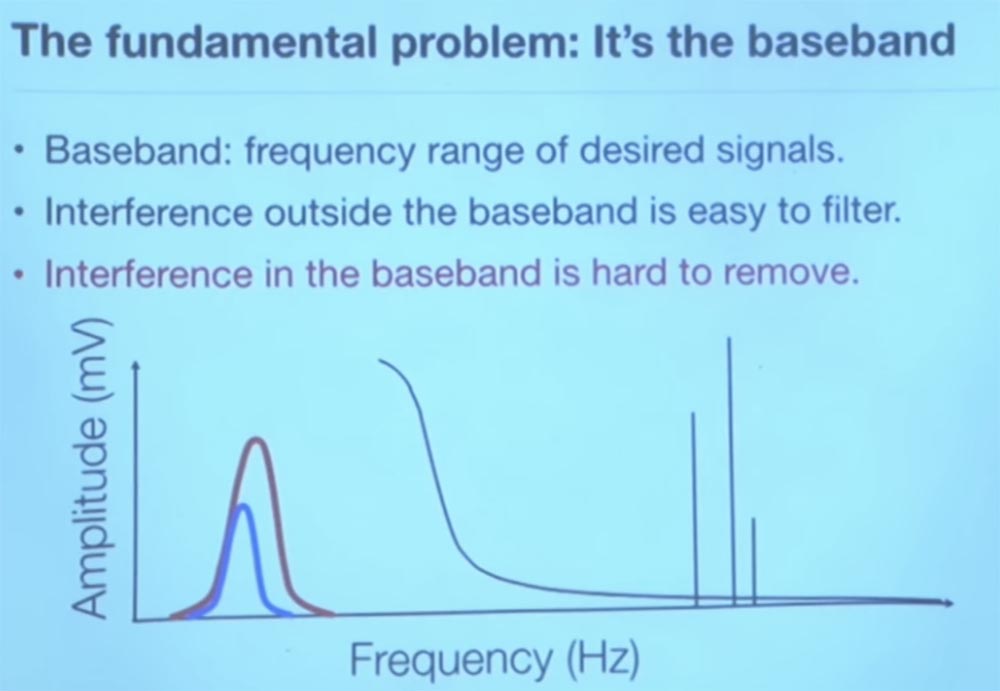
Imagine that your medical device is designed to receive physiological signals from the body in the low frequency range, since the heart does not beat too fast. We are talking about a few hertz frequency. Therefore, if your electrodes collected high-frequency signals, you would simply insert an analog filter, you would say that it is unrealistic for your heart to beat like an electric mixer, with which you prepare your lunch. . , , . , , .
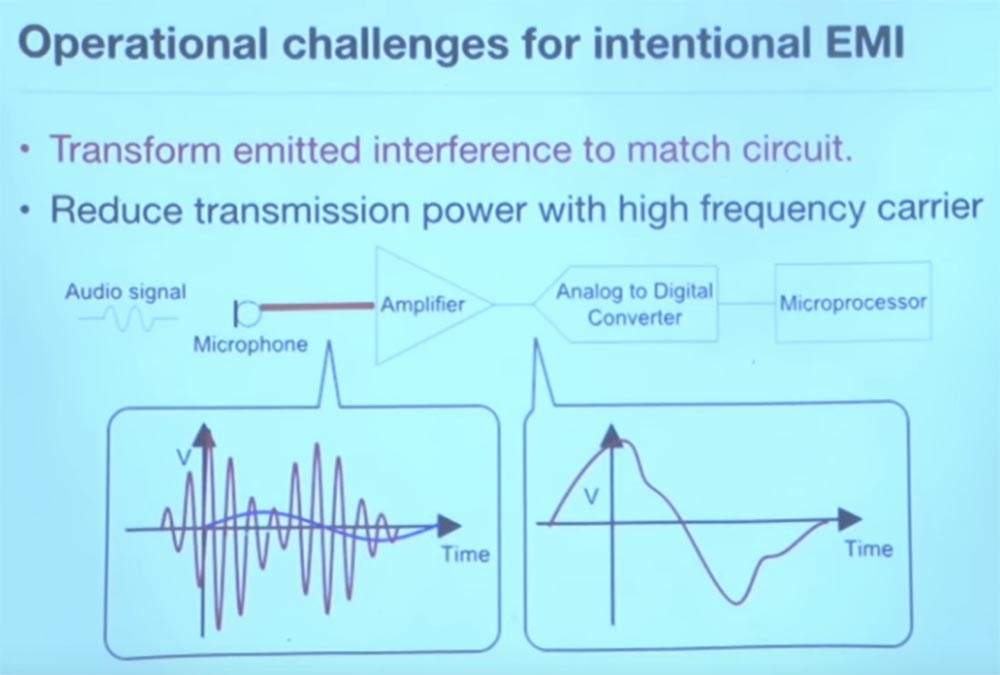
Consider a few examples. Bluetooth-, . , , . , -.

, , - . - USB- . . , .

, – . , . , software radio, . Python . .
, Weezer — «Island in the Sun».
Like this! , , - . , , Hi-Fi. – .
, , .
bluetooth-, , . FCC, , . , , , .
. , Bluetooth . DTMF-, . , .
, , , , .

Bluetooth , , , , , . .
, , . - - , .
, , . . , . -, , , - .

, , . , . , , . , , .
. . , . , , , .
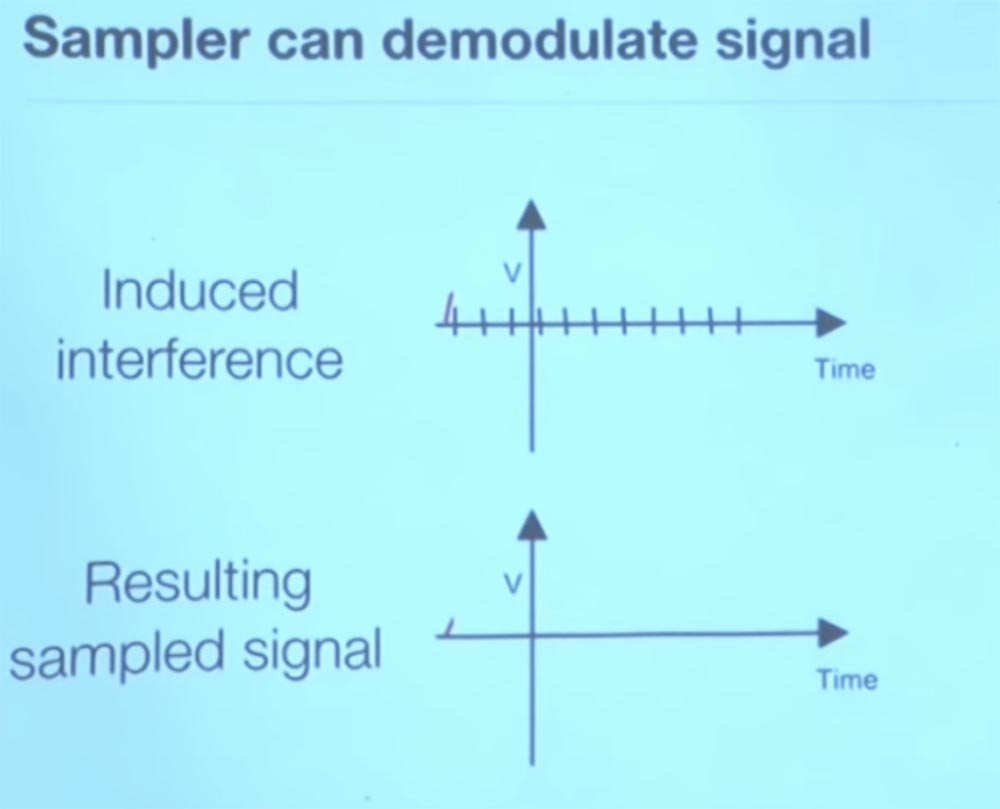
, , , . - , : «- - - ». , , . , , , , , .

, , , .
, – .

, ? , . , 826 , . .
, – 826 . , , , . , , . , , . , , , . 1, . , .
, , . .
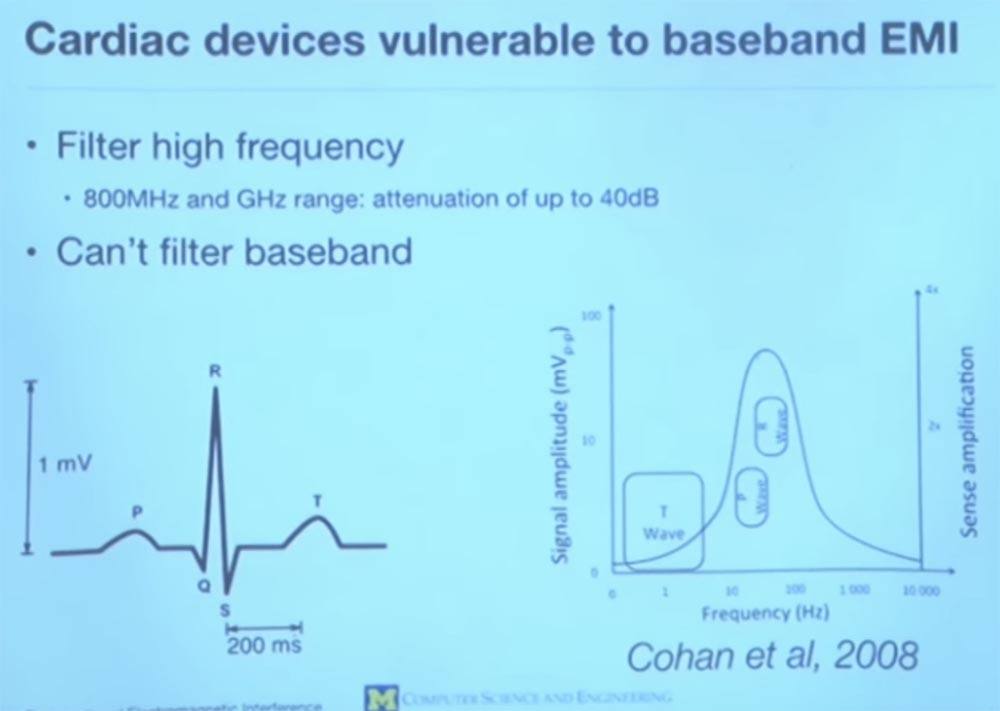
, . , , . , , – .
, , . , P, Q, R, S, T. QRS – , . — R, , . , , P T.
, , 100 . , .
, . . , , . , .

— . , . , . , , . , , . . , , 3D , , 4D. , .
, , .
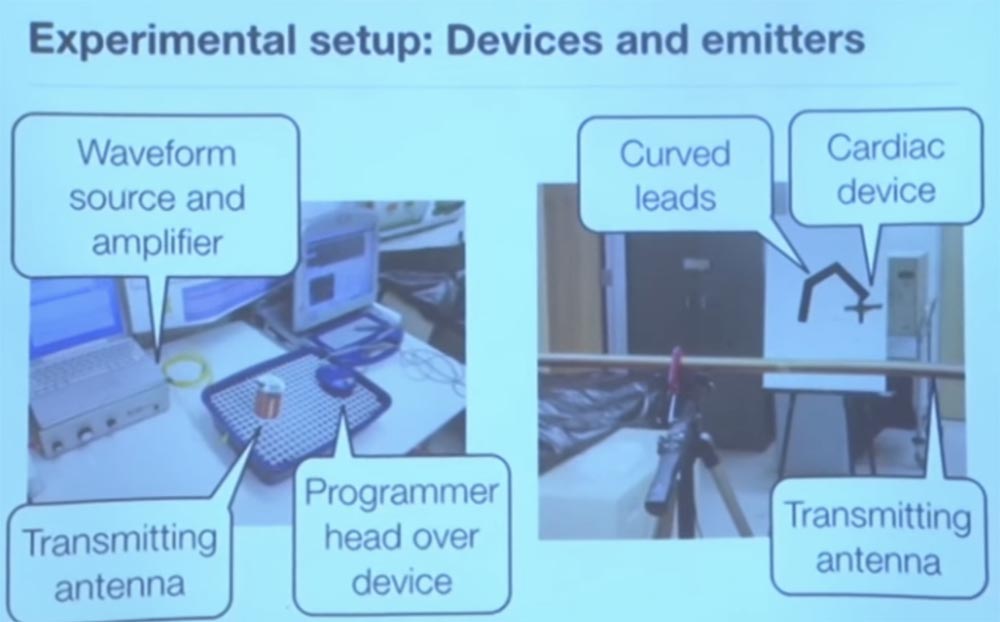
. . , , , , , . 2D- . , – , .
49:50
MIT course "Computer Systems Security". 15: « », 3
Full version of the course is available here .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/428654/
All Articles