Google Public DNS silently turned on support for DNS over TLS
Suddenly, without prior announcement, at 8.8.8.8 DNS over TLS was earned. Earlier, Google announced only support for DNS over HTTPS.
A public resolver from CloudFlare with an IP address 1.1.1.1 supports DNS over TLS since the project was launched.
')
Why do you need it
When using the classic DNS scheme, providers can crawl their dirty paws into your DNS packets, see which domains you request, and replace the answers as you like. Fraudsters do the same, replacing resolvers on hacked routers in order to direct the user to a fake server.
With DNS over TLS / HTTPS, requests are sent inside an encrypted tunnel so that the provider cannot replace or view the request.
And with the advent of domain name encryption in X.509 certificates ( ESNI ), blocking via DPI over SNI (Server Name Indication, a special field in which the domain name is transmitted in the first TLS packet), which are now used by some large providers, will become impossible.
How it works
A TCP connection is made to TCP port 853, and a resolver certificate is checked using system root certificates, just like HTTPS in a browser. This eliminates the need to add any keys manually. A normal DNS query is performed inside the tunnel. This creates less overhead than DNS over HTTPS, which adds HTTP headers to the request and response.
Unfortunately, currently only in Android 9 (Pie) support for DNS over TLS is built into the system resolver. Setup Instructions for Android 9 .
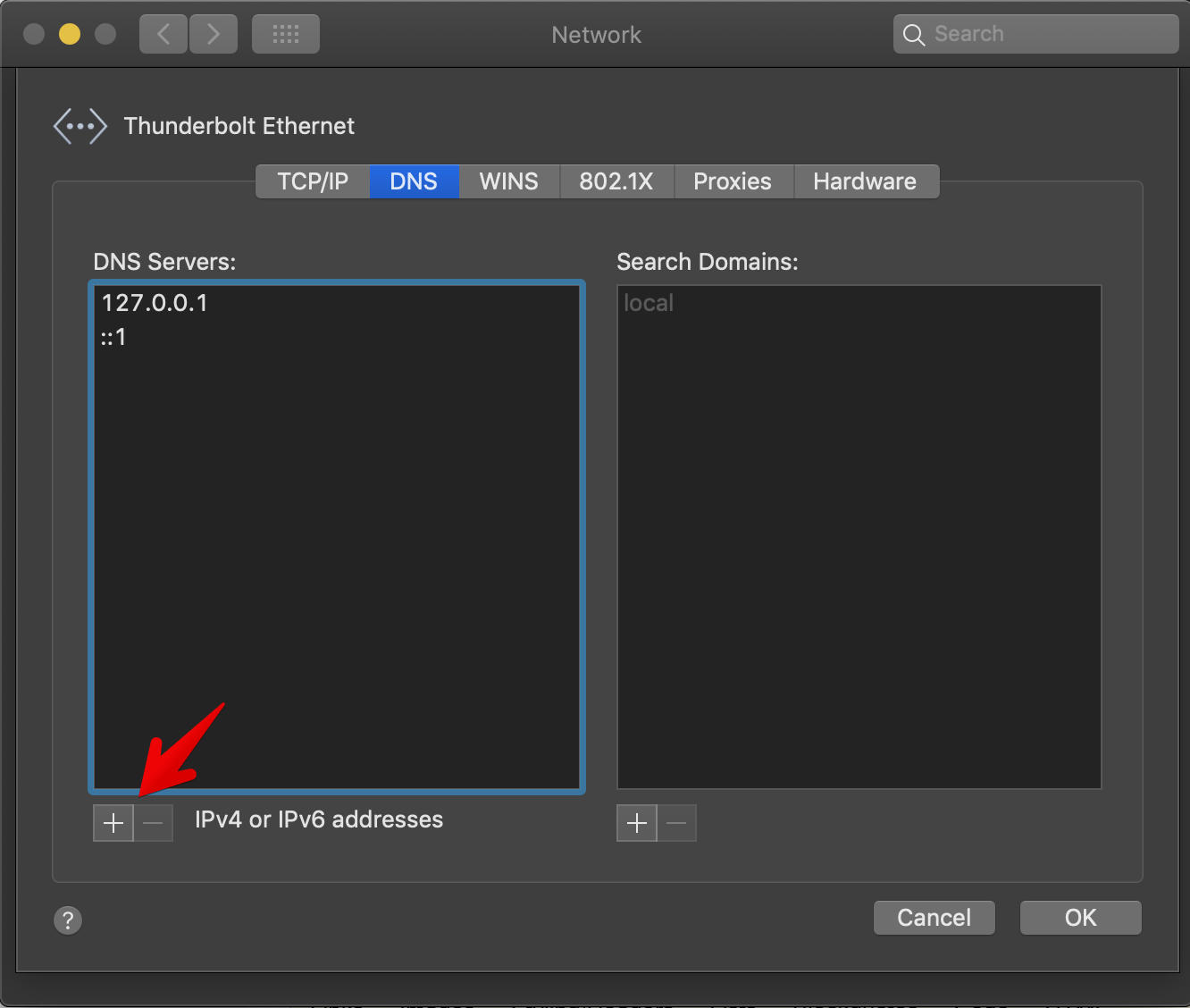
For other systems, it is proposed to use a third-party daemon, and direct the system resolver to localhost (127.0.0.1).
Setup on macOS
Let's analyze the DNS over TLS setting on the latest macOS version, using the knot resolver as an example.
Installation
brew install knot-resolverknot , dnsmasq.
nano /usr/local/etc/kresd/config:
policy.add(
policy.all(
policy.TLS_FORWARD({
{'8.8.8.8', hostname='8.8.8.8'},
{'8.8.4.4', hostname='8.8.4.4'}
})))
:
-- Config file example useable for personal resolver.
-- The goal is to have a validating resolver with tiny memory footprint,
-- while actively tracking and refreshing frequent records to lower user latency.
-- Refer to manual: https://knot-resolver.readthedocs.io/en/latest/daemon.html#configuration
-- Listen on localhost (default)
-- net = { '127.0.0.1', '::1' }
-- Drop root privileges
-- user('knot-resolver', 'knot-resolver')
-- Auto-maintain root TA
trust_anchors.file = 'root.keys'
-- Load Useful modules
modules = {
'policy', -- Block queries to local zones/bad sites
'hints', -- Load /etc/hosts and allow custom root hints
'stats', -- Track internal statistics
'predict', -- Prefetch expiring/frequent records
}
-- Smaller cache size
cache.size = 10 * MB
policy.add(
policy.all(
policy.TLS_FORWARD({
{'8.8.8.8', hostname='8.8.8.8'},
{'8.8.4.4', hostname='8.8.4.4'}
})))
hostname TLS-
SAN , 8.8.8.8:853
hostname. , X.509- IP-, hostname .
hostname — Common Name (CN) Subject Alt Name (SAN) . , , . .SAN , 8.8.8.8:853
dns.google
8888.google
8.8.4.4
8.8.8.8
2001:4860:4860:0:0:0:0:64
2001:4860:4860:0:0:0:0:6464
2001:4860:4860:0:0:0:0:8844
2001:4860:4860:0:0:0:0:8888
hostname. , X.509- IP-, hostname .
sudo brew services start knot-resolver, , :
sudo lsof -i -P -n | grep kresdkresd 53 localhost.
- , :
cat /usr/local/var/log/kresd.logdig @127.0.0.1 habr.com, .
, :
UPD
DNSCrypt, DNSSEC, DNS over TLS/HTTPS.
DNSCrypt UDP TCP. 443. , HTTPS. DPI. , DNS over TLS/HTTPS, RFC, . , , .
DNS over TLS (DoT) — TCP- 853, DNS-. , DNS . , DNS over TLS , over HTTPS.
DNS over HTTP (DoH) — TCP- 443, HTTPS. , HTTP-. HTTPS-. , , DNS- , . , .
, DNS over HTTPS over TLS — , . RFC. , .
DNSSEC — DNS-. , . DNS, UDP/TCP 53, DNS over TLS/HTTPS. DNSSEC DNS-. NS-. , DNS , , A- MX-, RRSIG, . DNSSEC , .
dnscrypt.info/faq ( Other protocols)
Source: https://habr.com/ru/post/427639/
All Articles