The highly secure Signal messenger "secretly" saves the history and encryption keys in plain text

Illustration of thehackernews.com
Signal gained popularity after it became known as the “favorite messenger” of Edward Snowden . In 2015, he said that he uses Signal daily to communicate with journalists.
The Signal messenger is positioned as a specially protected means of information exchange, which uses end-to-end encryption, which should exclude unauthorized access to the contents of the correspondence. However, as it turned out, there are situations where all efforts to encrypt Signal information are in vain.
')
Signal was initially available only as a mobile phone application, but convenience required a desktop version, which as a result appeared as an extension for Chrome. Since the end of October 2017 , a new version of the offline application, independent of the browser, has become available to users. Since that moment, the extension for Chrome has received the status of end-of-life , and at the time of publication of this article the period of its support expires in less than a month. This is where the sad story begins.
Do it once
Information security researcher Matthew Syush shared his discovery that one of the most secure crypto-messengers “planted” an impressive size to his users. The Signal messenger during the migration process from the Chrome extension to the full desktop client exports user messages to unencrypted text files.
Matthew Syush discovered this dangerous bug when working in macOS when updating Signal. The BleepingComputer journalists went further and found out that the exact same problem manifests itself in Linux Mint.
When exporting conversations to disk, Signal creates separate folders named by name and phone number of contacts. All dialog content is stored in plain text JSON. The program does not display any warnings that the information is decrypted and saved to disk. This moment is the key to the threat of leakage of confidential data.
The worst thing in this situation is that unencrypted messages remain on the disk even after the upgrade is completed, and you have to delete them manually, if, of course, the user guesses at all ...
Make two
But this was not enough! The second problem in Signal Desktop was revealed by another researcher, Nathan Shochy.
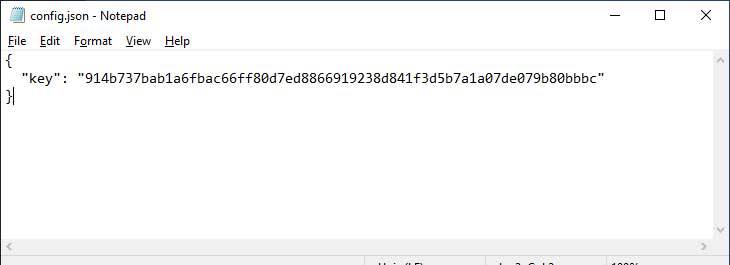
Nathan Shochy learned that during the installation of Signal Desktop an encrypted db.sqlite database with an archive of user messages is created. The encryption key for the database is generated by the messenger without user interaction and is used every time you need to read the database with a message archive. Who would have thought that the key is stored locally and in clear text? This key can be found on the PC in the % AppData% \ Signal \ config.json file and on the Mac in ~ / Library / Application Support / Signal / config.json .
Do three, Signal blue flame burn!
Apparently, the problems with Signal do not end there. For example, another expert, Keith McCammon, points out that Signal Desktop is not good at removing attachments from "disappearing" messages.
The function of the “disappearing” messages was conceived by the Signal developers as an additional security layer, but in fact it does not work very reliably. According to McCammon, all attachments remain on the Signal users disk even after they should be deleted.
Source: https://habr.com/ru/post/427637/
All Articles