The standard Encrypted SNI is implemented in Firefox Nightly
 Firefox was the first browser to implement TLS Server Name Indication (SNI) encryption. ESNI support was introduced into the latest version of Firefox Nightly, on which all innovations are run-in before being added to the mainline.
Firefox was the first browser to implement TLS Server Name Indication (SNI) encryption. ESNI support was introduced into the latest version of Firefox Nightly, on which all innovations are run-in before being added to the mainline.A month ago, CDfla provider Cloudflare told about the importance of this standard. In short, thanks to ESNI, information about which domain you are sending the request to is encrypted. In standard HTTPS, headers with domain names are not encrypted and are available for viewing by the provider or another “person in the middle”. Now he sees only the IP address. Since hundreds of domains can be located on the same IP address on the modern Internet, ESNI effectively hides information on which domain the user enters.
Thus, blocking by name stops working, and censorship on the Internet will become much more complicated. Censors will have to block IP addresses, and this is a dubious practice. Such blocking can affect uncomplicated sites, and the blocked service easily (automatically) switches to a different IP address.
Why do host names shine in normal TLS SNI? The fact is that before starting the encryption, the server needs to know which domain the client is accessing in order to present the necessary certificate. For this reason, the host name is in clear text (below the illustration from the Cloudflare blog ).
')
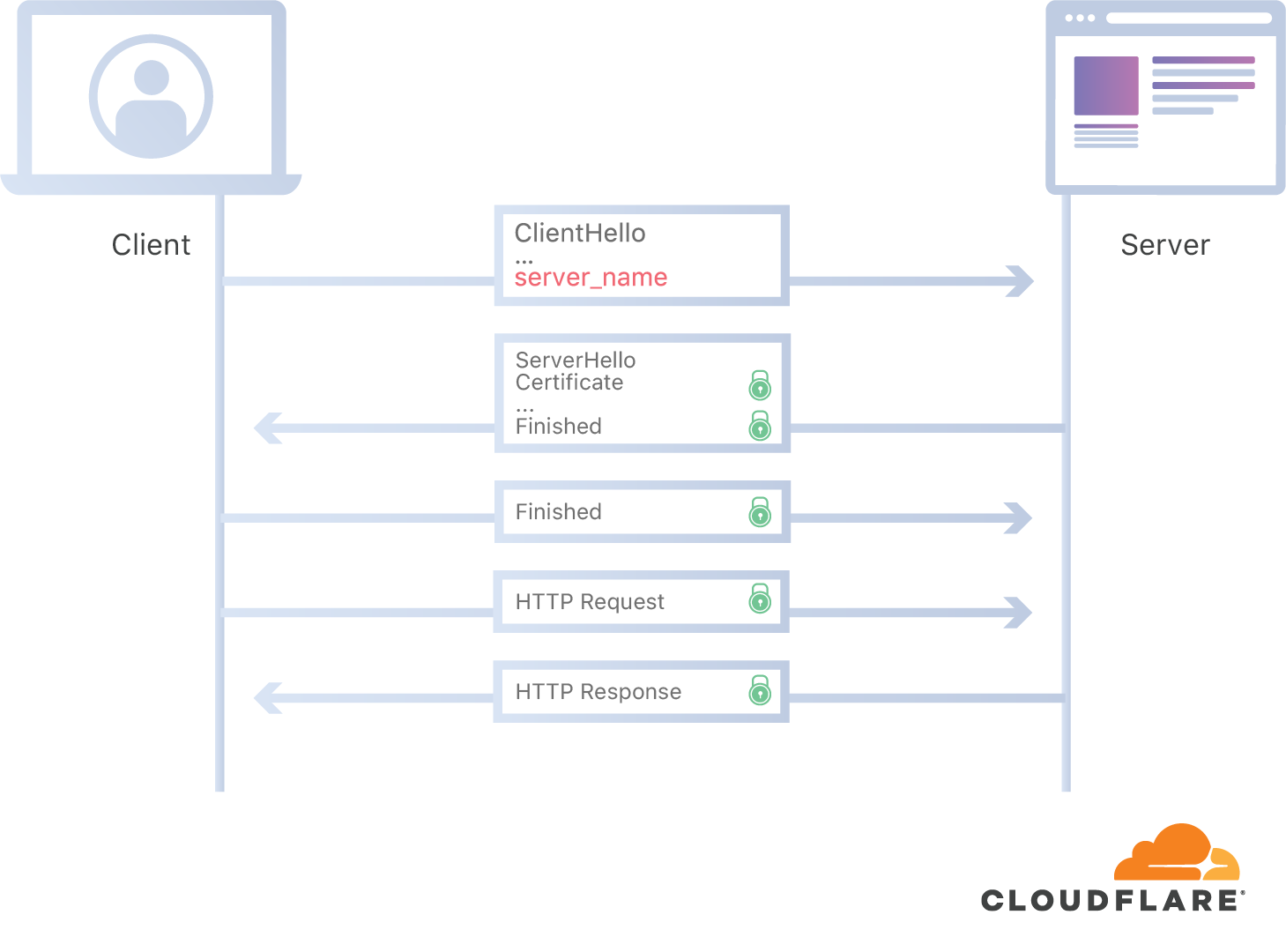
In encrypted SNI (ESNI), this problem is solved as follows: the client takes the server's public key from the DNS and encrypts all data with it before establishing a TLS session.

Browser support for Firefox Nightly means that ESNI will work with every website / provider that supports it.
Mozilla developers explain that there are four main ways to leak the history of visited pages:
- TLS certificate message,
- DNS name resolution
- Server ip address
- TLS Server Name Indication.
So far, they have made good progress in closing the first two leak channels: the new TLS 1.3 standard encrypts the default server certificate (channel 1), and over the past few months, Mozilla has been studying the use of DNS over HTTPS to protect DNS traffic (channel 2). The test results are not bad, and in the coming months, the function will be rolled out for all Firefox users. The IP address remains a problem, but in many cases several sites share the same IP address, so SNI is the main leak channel.
At one time, the Server Name Indication (SNI) technology began to be used precisely because there are several hosts on the same IP address. In this case, the SNI field tells the server which host you are trying to connect to, allowing it to choose the correct certificate. In other words, SNI helps to ensure the operation of large-scale TLS-hosting. That is, this function was introduced for the sake of security, and now we have to deal with it as a data leakage channel.
The SNI problem has been known for a long time, the Mozilla developers write, and it was clear that this field should be encrypted. But every design they tried included some sort of performance compromise. There was another important drawback: the fact that a particular site is switching to ESNI was a signal that “there is something to hide”, that is, the censors had the opportunity to trite the traffic by ESNI. In the end, it was decided to release the TLS 1.3 standard without ESNI.
Only in the beginning of 2018, developers realized that there is a pretty good option: large content distribution networks (CDN) host many sites on the same physical servers. If they agree to transfer all clients to ESNI at once , then suddenly ESNI ceases to be a useful signal for the attacker. Thus, it became possible to implement ESNI in TLS 1.3, through mass configuration of multiple sites on the existing set of servers.
ESNI is a completely new technology, and Firefox is the first browser to implement it. To activate it in Firefox Nightly, you should perform the following actions:
- Make sure you have DNS enabled over https (DoH):
about:config- set
network.trr.modeto 2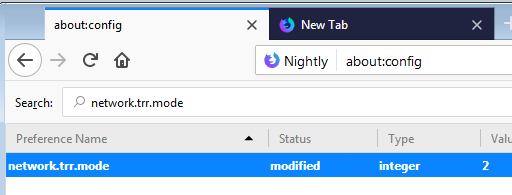
- set
network.trr.urito the DoH server (for example,https://mozilla.cloudflare-dns.com/dns-query).
about:config- set
network.security.esni.enabledtotrue
This should automatically enable ESNI for any site that supports it. At the moment, of the major hosters and CDNs, this is only Cloudflare, but the Firefox developers hope that other providers will be connected soon. Check the operation of encryption can be on this link .

In the coming months, Mozilla will check how ESNI interacts with different types of firewalls and other network devices. If you have enabled encryption and something is broken - please inform the developers via a bug tracker.

Source: https://habr.com/ru/post/427563/
All Articles