How is the security of your Windows operating system organized?

Are you sure you know what actions are performed by programs on your computers and other devices? For example, can games dig in your documents?
What does an application that is approved to run as administrator have, and why can't it run without issuing these rights?
Let's try to figure it out together.
Many people know that you should not download and run programs from unofficial sources, because can catch a virus. But there are those who sometimes neglect it.
')
In the article I share my personal opinion and experience . The purpose of this article is to figure out how to ensure safe operation in Windows.
UPD. Thank you for bathing in the minuses of the savvy inhabitants of Habr, who have forgotten that there are regular users of the OS , who are not obvious to many things!
UPD_2. It is a pity, I added not so much self-irony, so that it was more obvious, as here
I did not think that any program can perform almost any action, even under the supervision of antiviruses, until I reproduced it myself.
Even less obvious to a typical user:
" How to limit the permissible actions of the program if you want to have more reliable protection than the banal trust in the developer?"
First things first.
# Some lyrics. You can't do without a little background
Most recently, I decided to master python. Having learned the basics, I decided to write an application to automate my routine tasks. I am not a programmer, but PL / pgSQL knowledge helped me quickly.
1. Outline
I was surprised when the program compiled into .exe and .bin started from a flash drive on another computer without any questions, having done everything that is written in it:
- delete files from the folder "My Documents"
- read and replace the clipboard
- display information about files in other directories
- access the internet
- turn off the computer and other "pranks"
In fairness, I tried on Linux - the result is the same.
PS
On Linux, rarely anyone puts antivirus and other means of protection, because Linux users do not usually download any of the questionable sources. Usually everything is installed from trusted repositories. Probably why he is not covered with viruses.
But on Windows (8/10) I naively expected some kind of dialogue confirming the launch, the squeal of antivirus and other delights . I used to think that I am safe , because nothing really dangerous happened to my computer.
I tried to run the program on different computers of friends, using the guest record and the new simple user, put different means of protection - the effect is the same.
For some reason, I naively believed that the clipboard is something "holy" because it often flashes important information, and it seemed to me that I myself regulate the insertion of data.
However, as I understand it, for the OS it is just a program, like PuntoSwitcher, Teamviewer and others, who calmly perform all sorts of actions.
I wondered how to stop unwanted actions of my own program.
2. A little about the program
The console version of the program would be boring to run, so I decided to add an interface.
The main part of the console looked something like this:
While indulging with him - there was an uncomplicated game. I wanted to write a sapper, but # , import os import platform all_results = ['Start'] commands_dict = {'010 OS:': 'platform.system()', '050 :': 'platform.uname()', '060 !': "get_coffee('Cappuccino')", '150 - :': "None", '270 :': "os.listdir()" # # } def exec_in_results(command, note): try: note = note[3:] # 3 result = eval(command) # Eval is Evil? - Maybe if result is None: all_results.append('\n\n!! : {0} >>> {1}'.format(command, note)) else: all_results.append('\n' * 2 + '*' * 30 + note + '\n') # all_results.append(result) except Exception as err: all_results.append('\n\n!!! : {0} >>> {1} ERROR: {2}'.format(command, note, err)) for key_note in sorted(commands_dict.keys()): exec_in_results(commands_dict[key_note], key_note) print('\n'.join(str(x) for x in all_results)) Game menu when you first start

The program may seem to be a harmless game, but a few minutes after downloading the file (or another designated event), new functions are activated.
limited to the following list:
Program:
From decorations : the window is always centered, does not allow to collapse / move / close itself, because It does not have a header, it overlaps all windows. Does not respond to ALT + F4 (added button to exit).
Bonus: an optical illusion of shimmering circles between squares accidentally emerged.
The program weighs about 7 MB, although the code on lines 300 (including many empty ones), because the compiler I use (pyinstaller) even “Hello world” compiles to 5-MB exe.
- collects some data about the computer and shows it in notepad
- reads and replaces the clipboard
- accesses the Internet (just gets the main page of a famous search engine)
- opens the browser with the specified links
- is friends with antiviruses (so far, checked on virustotal.com). When downloading this program from the Internet, the only barrier I met is SmartScreen, which does not like applications from unknown manufacturers.
- can turn off the computer even faster than it does the button from the Start menu
- deletes files in a specific folder
From decorations : the window is always centered, does not allow to collapse / move / close itself, because It does not have a header, it overlaps all windows. Does not respond to ALT + F4 (added button to exit).
Bonus: an optical illusion of shimmering circles between squares accidentally emerged.
The program weighs about 7 MB, although the code on lines 300 (including many empty ones), because the compiler I use (pyinstaller) even “Hello world” compiles to 5-MB exe.
The menu of the game that we deserve

I made a video for those who are interested in the work of the program.
PS
If you want to download this file for the experiment, you can guess where to download the “more innocuous” version of the program (without deleting and turning off).
But I do not advise doing this, is there anything there :)

But I do not advise doing this, is there anything there :)

I think it makes no sense to throw the source, because The essence is not in this program, it is only as an example.
3. What confuses me?
" I know that I know nothing ."
I am a simple user, convinced that the antiviruses and the system itself will protect me from most of the dubious (in my opinion) program actions. It is unlikely that my application is considered a virus, but it can harm.
I have no complaints about antiviruses, they save from popular threats, phishing sites and other problems.
The main cause of the problems is the actions of the user himself.
Surely there are users who are unaware of how dangerous it can be to download unfamiliar / cracked applications from torrents, file sharing, and other sites.
Especially those that require administrative rights to run. The series "Black Mirror" hints . About Root firmware / phone applications - I will not say anything.
Not all people get along well with the computer, download what they offer, and trustfully click "Continue / Continue" with all installations. Therefore, when friends ask me to watch a computer that barely moves, I always see a lot of
Typical Expert Mode

I am a little annoyed by the “permissiveness” of programs , when they register themselves not only in autoload, but also take root in services, registry and task scheduler, slowing down the computer with their incomprehensible processes.
While I tried different antiviruses, one of them spoiled the driver for the network card when I deleted it, and I was left without internet. The system restore point helped.
I do not have paranoia, but I do not like that when the program is installed, only 2 options pop up:
-Set (* Install as administrator)
-Cancel
But what if I want (just in case) that the application only sees its folder, does not have access to the Internet, clipboard, etc.? Where should I click?
The benefit of the camera / microphone restrictions are in the privacy settings.
4. What do you want? It was always the same
Apparently, I have already got used to the fact that on the phone the applications are annoyingly requesting access to data and functions of the system (“allow access to Photo / Camera / Microphone / Geolocation”).
But!
Now I thought, is it permanent access at any time of the application? Or just when I click "Write / Photograph / Send File"?
I hope everything is all right there, but that's another topic ..
I hope everything is all right there, but that's another topic ..
But, it is not quite clear to me how it is possible to launch / install an application on a personal computer in a convenient way, setting the framework for what is permitted.
5. Search for a solution
The most important and obvious step will sound naive, because many people know about him, but often neglect it.
Most of the troubles (viruses, miners, crashes, etc.) of Windows due to the fact that many use the account with administrator rights created during installation, thereby launching all programs with redundant rights. I repent, I was one of them for a long time.
UPD. Just look at the result of the survey at the end of the article.
I do not know why so far in Windows this is not such an obvious point
like in linux

Brief instructions for those who understand what they mean, but do not dare to take this step:
Create a separate user, give him administrator rights, and remove yourself.
Only with passwords do not get confused.
When you start / install some programs and other changes in the system, the administrator password will be requested (and not just: Yes / No), you will have occasion to think about why the program requires such rights.
From accustomed applications will not help
Only with passwords do not get confused.
When you start / install some programs and other changes in the system, the administrator password will be requested (and not just: Yes / No), you will have occasion to think about why the program requires such rights.
From accustomed applications will not help
I noticed that some programs at startup want to get administrator rights , however, if they fail, they can offer an alternative:
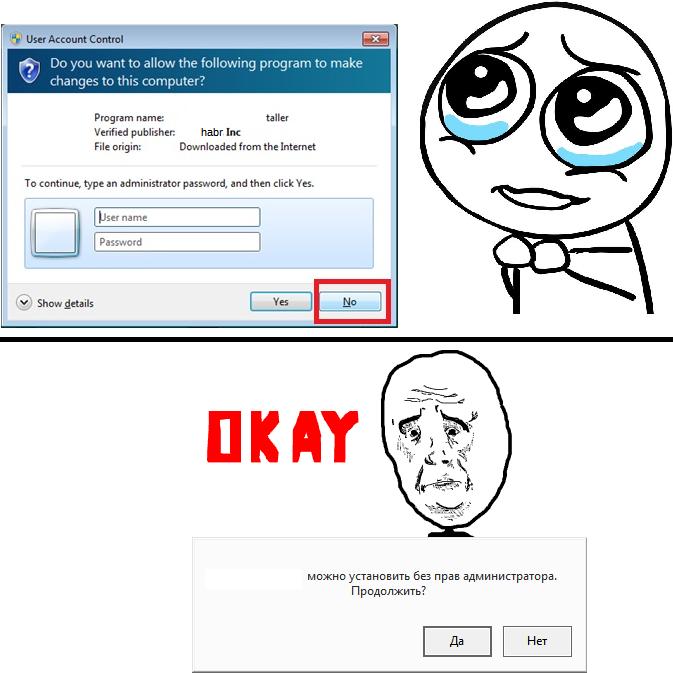
Now the system files were more secure, but my program continued to do treacherous things.
I went to the Internet with a similar question (+ IT chat rooms in messengers): “How can I run an EXE program safely / in isolation?”
Another surveyed friends close to IT.
Found the following options:
1) Use a virtual machine
A great option, but not for all occasions.
I think that some users may represent a virtual machine somehow.

2) System settings
- Set up security policies, rights to important folders, etc.
- Understand why the program asks for additional rights, and suppress the UAC request
Of course, Windows is quite flexible in configuration. I consider myself considered to be a fairly “advanced” user, but even I don’t want to bother with policy settings, additional software and other tricks.
PS While I was looking for information, I most often found articles on how to disable UAS so that it does not interfere with its warnings .
3) Do not download suspicious applications. The best way! .
I have doubts now, how can I know that any known application does / does not do what I don’t want?
Fragments of a typical license agreement
The user is notified and agrees to automatically update the Program without any additional notifications.
The license agreement may be changed unilaterally by the Copyright Holder. Changes to the terms of this License are published on the page: page_on_which you_requirer or go . These changes in the terms of the license agreement take effect from the date of their publication,or then when it will be convenient for us ..
The license agreement may be changed unilaterally by the Copyright Holder. Changes to the terms of this License are published on the page: page_on_which you_requirer or go . These changes in the terms of the license agreement take effect from the date of their publication,
I do not like it - do not use it, everything is fair.
I will not write that for the update I flew in this way, because I do not want to offend anyone in this publication.
4) Use the program " sandbox "
The most convenient option, in my opinion. I was able to suppress some of the dangerous operations of my program, which is not quite bad. However, this is a third-party and not always free software that requires configuration.
I want something similar built into the OS, with a clear interface.
Total
I do not blame anyone, I do not call for panic: I just wanted to share with you my thoughts about the security of our OS.
It surprises me that any application can be a “Pandora's box”, from which very few people know how to defend themselves (as I observed).
It seems to me very strange, at a time when everyone is trying to protect their information, they use two-factor authentication / SMS, encryption in instant messengers and other things.
If there is a simple full-time opportunity to organize a safer environment, I will be glad if you tell me how to do it!
Thanks for attention!
How is the security of your Windows operating system organized? What can you advise?
Source: https://habr.com/ru/post/426217/
All Articles